At PhishMe we talk frequently about a familiar concept that cyber attacks and phishing emails are very rarely sent to only one organization. While security teams tend to focus on threats to your organization, PhishMe Intelligence is watching for email-based threats for EVERY organization. As we were gathering information about tax-related phishing scams this year, we noticed that institutes of higher learning were being hit quite broadly by this year’s W2 related scams.
While many businesses also receive these scams, universities are a great place to gather information about such targeted attacks because so many post warnings about cyber attacks on public facing websites.
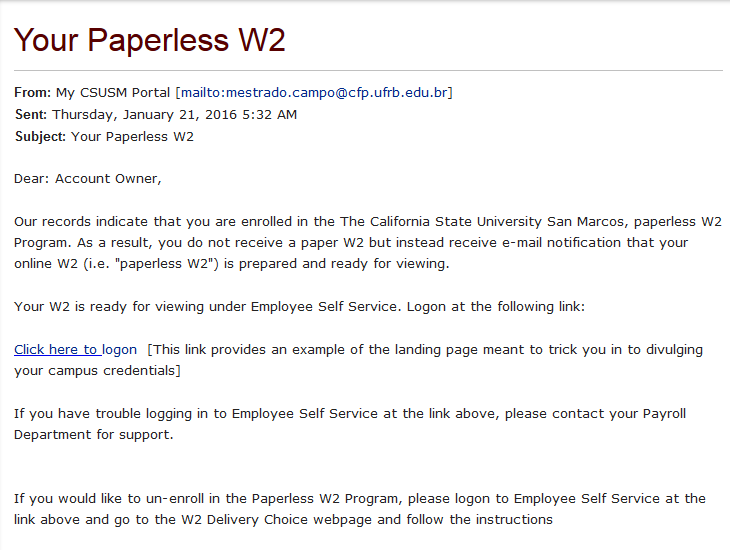
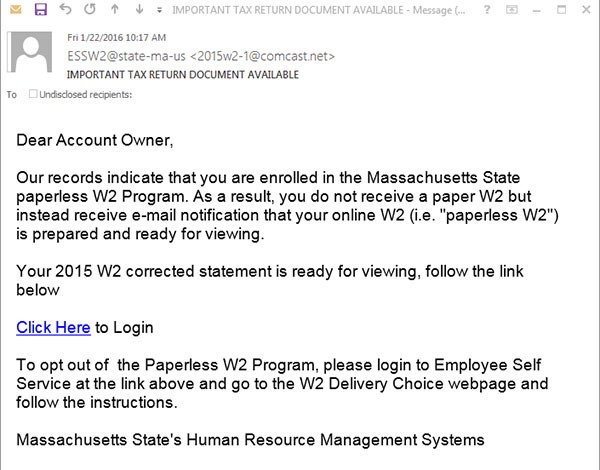
“Paperless W2” Phishing
These two example phishing emails will serve to illustrate a common W2 Phishing attack that has targeted more than twenty universities all across the country:
 |
 |
The Auburn University version of this scam also used the “My (school-here) Portal” in the username, and was also from [email protected]. This is unlikely to be the criminal’s true email, however, as many of the emails are being sent from other universities where the phisher has already stolen user IDs and passwords that allow them access to the email accounts of students, staff, and faculty in those locations.
All of the universities and colleges in the table below have published warnings regarding this same scam after seeing it show up at their universities. For those who are in this space, clicking each university name will take you to their published warning about this scam.
In many cases, while the language is almost identical in each, other characteristics of the attack match as well.
Many of the phishing emails use the trick of having an email address listed as the name for the email user, knowing that many clients display the human readable name instead of the email address. For example, the sample email shared by the University of Chicago was really from an email address at ualberta.ca, but the name, which would normally be “John Smith” or “Amy Jones” in this case is [email protected]. The Berkeley example email used the name [email protected] even though the from address was really a k12 educator in Georgia. Colorado came from “ESSW2@colorado-edu” and Williams was from [email protected]. Clemson was “from” [email protected] and University of Florida also had the extra “S” in [email protected].
Where does the “Click Here” go?
“Paperless W2” phishing sites imitating Auburn University, Clemson, Kansas State, Ole Miss, and University of California – San Diego all went to “kaizenkz.org” with each school having a customized phishing site in a different subdirectory there:
- /k-state/K-StateSign-In.htm
- /wp-includes/theme-compat/all/ucsd/login.htm
- /wp-includes/theme-compat/5050/o/olemiss/irj/portal
- /wp-includes/theme-compat/admin/clemsons/Clemson/Oracle.htm.
- (Auburn did not specify the path, but did confirm the kaizenkz.org site)
Chicago = www[.]flirtingvision[.]co[.]nz / css/50/chicago/weblogin.htm
Cornell = haksuara[.]com/web4_login_cornell_edu/index.html
Austin CC = perfect[.]com/eapps-austincc-edu/w2/
In order to address cyber attackers such as these it is imperative that investigators understand the relationships between all of these various attacks. If you have information about new phishing attacks, please send them to us! We love to receive your emails containing suspicious URLs at [email protected] — not just university phish, but ANY type of phish!
CEO/President Impersonations to Get ALL the W2s
More than just a phishing URL, some employees are receiving very targeted spear-phishing attacks that attempt to convince the recipient that their CEO or other high-ranking officer needs them to email everyone’s W2 information to some outside address. This is what happened at the University of California – Irvine, where former DHS Secretary Janet Napolitano is now president.
Here’s the email they shared about the incident:
From: Janet Napolitano <[email protected]>
Date: Mon, Feb 22, 2016 at 8:17 AM
Subject: 2015 W-2 statement
To:
I need all our employee's reference copies of 2015 W-2 wages and tax statement, i am working on a review and if you can work on the W2's and have it sent to me as an attachment this morning that will be splendid. Via email would be appropriate.
Regards.
Janet Napolitano.
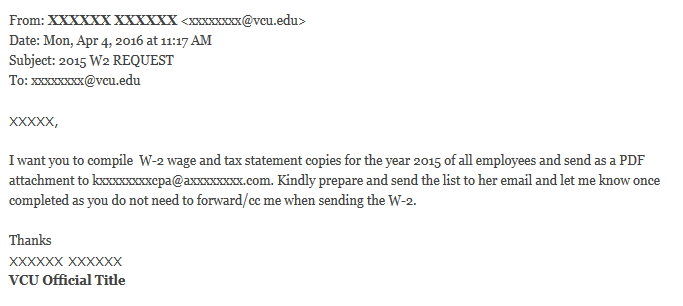
The same attempt was made at Virginia Commonwealth University, according to the post they made here, on April 4, 2016: https://phishing.vcu.edu/2016/04/04/w2-request-phishing-scam-4416/
Although the wording is slightly different, these seem very similar to the warning that security journalist Brian Krebs shared in his recent article “Phishers Spoof CEO Request W2 Forms.” Scammy emails impersonating business executives for the purpose of moving money is referred to by the FBI as a “Business Email Compromise” and has been documented to have cost more than 17,000 victim companies over $2.3 Billion in related scams! (See “FBI Warns of Rise in Schemes Targeting Businesses and Online Fraud of Financial Officers and Individuals” March 29, 2016)
Conclusion
The bottom line is that criminals will keep coming after our tax information because it can be used for so many types of fraud, beginning with fraudulent tax returns, but also to establish new lines of credit in your name. Our average employees need to be aware of the common phishing scams like the “Paperless W2” or “Electronic W2” scam hitting so many universities. More importantly, each organization should be asking the question “Do my employees know what to do if they receive an email like this?”
For employees in our payroll and human resources departments, as well as anyone with financial responsibilities in our organizations, we need to be warning them about the “CEO Impersonation” version of this scam.
Lastly, the only way to know if you are the victim of a “targeted attack” is to be exchanging information with someone who knows what OTHER organizations are facing. Each of these universities certainly thought they were being targeted, but knowing that they were just one of many victims should help them to understand their attack more thoroughly.