CISO Summary
It’s critical that anti-phishing programs reflect the latest threats. Cofense IntelligenceTM has recently observed a phishing campaign that illustrates why. It entices users to download a malicious document from a seemingly legitimate source, an insurance company whose roots go back to 1896. Through a complex chain of abuse, including the exploitation of a legit subdomain hosted by Microsoft, this threat is capable of tricking users unfamiliar with wrinkles like multiple links to the same source and malicious “unsubscribe” links. If successful, the attack activates the Loda Remote Access Trojan, underscoring the importance of educating users to stop phishing emails.
Full Details
Cofense Intelligence recently observed a campaign that used convincing emails to entice recipients into downloading a malicious document from a seemingly legitimate source. These attention-grabbing emails contained multiple links to the same source, which was hosted on a subdomain of the legitimate Microsoft-owned domain azurewebsites[.]net. This source URL downloaded a Microsoft Word document that abused an object relationship to then download and open an RTF document. The RTF document abused CVE-2017-11882 to download the multi-functional Loda Remote Access Trojan. By taking advantage of users’ assumption that unsubscribe links are legitimate, along with their trust in verification, threat actors were able to craft a campaign capable of fooling even users with basic security awareness training.
What a Deal…
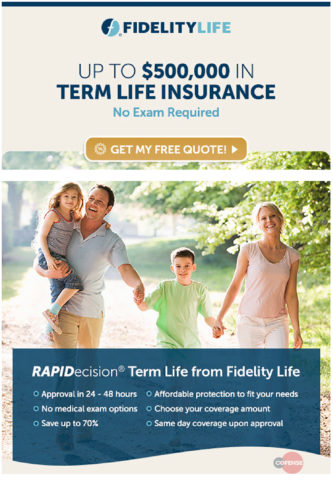
The emails used in this campaign have several attributes that give the appearance of legitimacy. The first email, the top of which is shown in Figure 1, impersonates Fidelity Life and claims to offer a good deal on life insurance.
Figure 1: Body of the email spoofing Fidelity
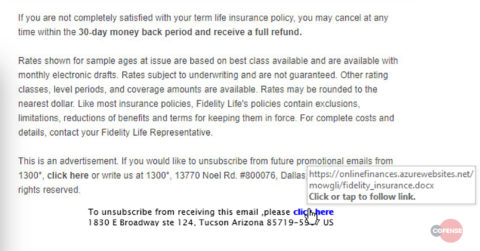
In this email, the only actual text present is the unsubscribe information at the bottom of the email shown in Figure 2.
Figure 2: Unsubscribe section of the email spoofing Fidelity
The top three paragraphs in Figure 2 are in fact an image, while the bottom paragraph (with a pointer hovering over it) is searchable text that appears to have been added by the threat actor. All of the image shown in Figure 1 is a clickable link leading to the same URL as the unsubscribe link, hxxps://onlinefinances[.]azurewebsites[.]net/mowgli/fidelity_insurance[.]docx.
Verification Passed
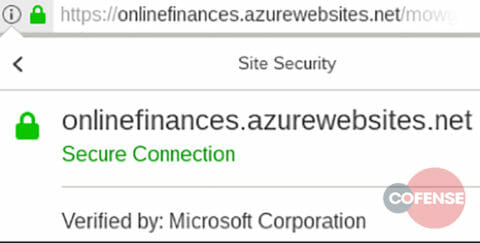
If users who have been trained to be suspicious of links were to first visit the website by typing the URL into an internet browser and looking at the webpage information, they would see the information shown in Figure 3.
If users are particularly security conscious, they might even look up the domain on a website with tools that check for legitimacy. However, this would likely give them the same information as what is shown in Figure 3, because most tools will check the root domain, in this case azurewebsites[.]net, which is a completely legitimate domain owned by Microsoft. The only easily recognized indicator of malicious content is the prompt when a file is downloaded from an unsubscribe link.
Double Interest
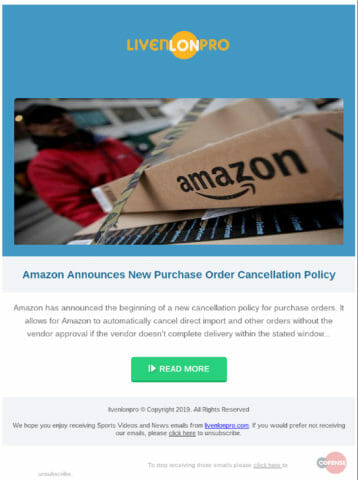
The second email, shown in Figure 4, pretends to be a relatively benign “news” email from the company Livenlonpro about a new Amazon policy.
Figure 4: Body of the email spoofing Livenlonpro
In this case all links and images download a file from hxxps://onlinefinances[.]azurewebsites[.]net/mowgli/Amazon_Cancelled_order[.]docx. With this approach, any user that attempts to unsubscribe from what appears to be a spam email will instead download malware. Although differently named, the downloaded file is the same for both emails.
Actual Goal
Once the file is downloaded and opened, it attempts to use an object relationship to download a document with CVE-2017-11882 which, in turn, downloads the multi-functional Loda malware. Loda is capable of acting stealthily to download additional malware or provide the threat actor with full remote access to the victim’s computer.
Direct Importance
Attacks such as this demonstrate threat actors ability to adapt to changing circumstances and training methods. Organizations often focus employee training on the philosophy “don’t click suspicious links or open attachments.” While usually effective, this method can fall prey to creative threat actors. Using a training method that encourages employees to think critically can help protect organizations by avoiding situations where employees make assumptions about the nature of a link and act accordingly.
To stay ahead of emerging phishing and malware trends, sign up for free Cofense™ Threat Alerts.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.