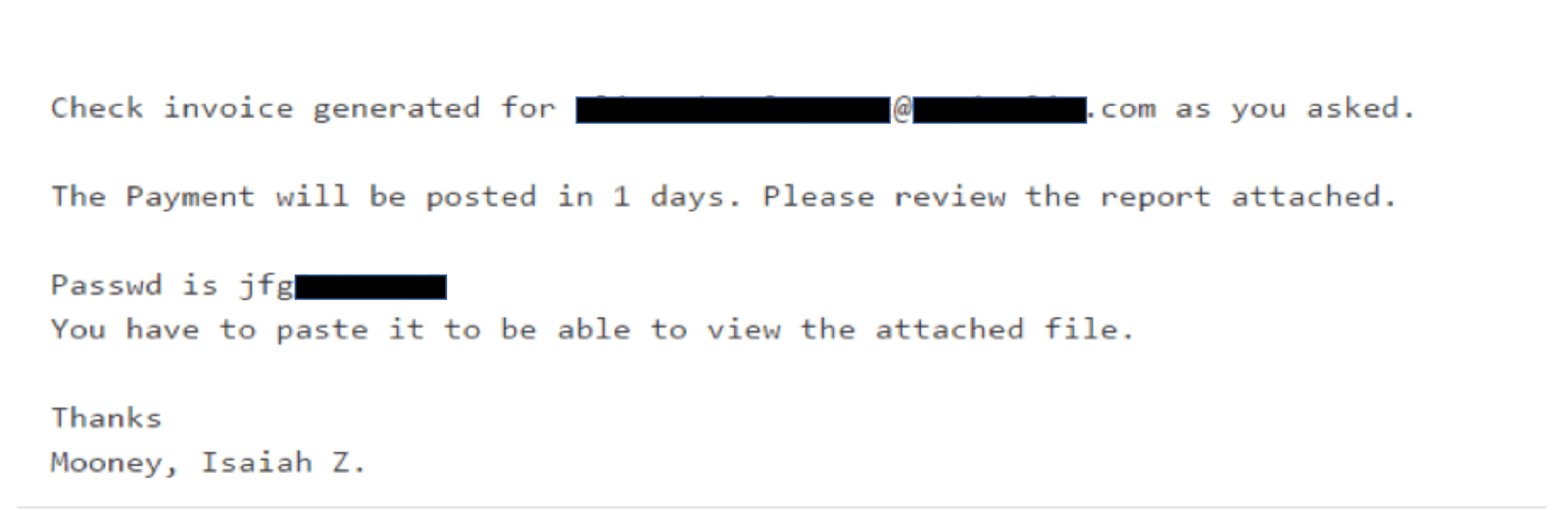
On April 5th, our Phishing Defense Center received a flurry of emails with subject line following a pattern of Lastname, firstname. Attached to each email was a password-protected .docx Word document with an embedded OLE package. In all cases the attachments were password protected to decrease the likelihood of detection by automated analysis tools. A password was provided to the victim in the body of the email which attempts to lure the victim into opening the malicious attachment and to increase the apparent legitimacy of the message.
An example of a phishing email for this attack is shown below:
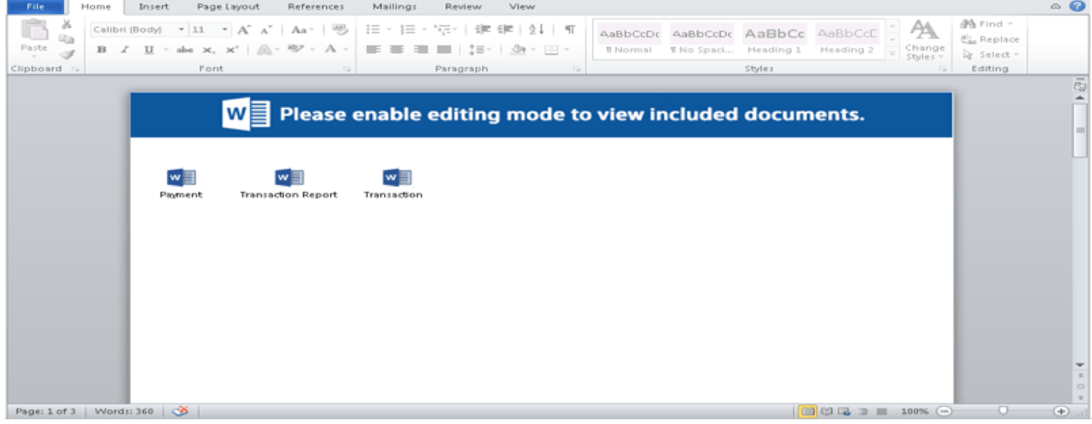
If a victim attempts to open the attachment they will be presented with a window to enter the password found in the message body. Upon entering the password correctly, it then presents a Microsoft Word document with embedded links to open an OLE object. This OLE object is designed to write to disk a malware payload and execute it.
Below is an example of a document with embedded OLE objects.
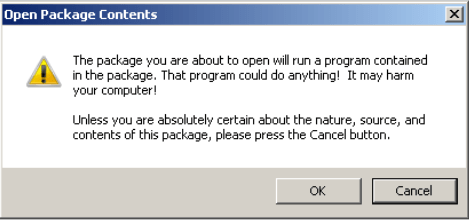
Upon double clicking to open an embedded OLE objects the victim is presented with a dialogue box warning that clicking OK will run a program contained in the package.
If the victim clicks OK to continue, the following malicious payload is placed on victim’s computer under Local Temp folder “C:UsersusernameAppdataLocal Temp”
File: MS Office Word MultiPart.vbs
MD5 Hash: 510aff28e3f912f984544cd27843c606
This technique is distinct from the prolific use of macros embedded in the MS Office document, but still writes a Visual Basic script application to disk to facilitate the download and execution of malware binaries. When the victim double clicks the OLE package this script application is run by a wscript.exe process.
Payload IOCs:
URL : hxxp://185.195.24.196/agt.dgd
The malware can detect the presence of analysis tools and checks for virtualization to detect if it is being analyzed in a virtual environment like VMware or VirtualBox. The Visual Basic downloader application is used to create a file with the arbitrary .OjM and .gAV extensionsin the C:UsersusernameAppdataLocal directory. It also downloads one or more executables from the above payload location.
The dropped files are the Ursnif botnet trojan malware. The Ursnif samples identified in our analysis are below:
Ursnif Operation:
The Ursnif trojan and the many variants thereof represent a category of multipurpose trojan malware capable of conducting a wide variety of hostile activities. These variants are used to carry out attacks against browsers using man-in-the-middle techniques as well as information-stealing attacks in which private data is collected from victims’ machines and sent to a command and control server infrastructure.
Most Ursnif variants rely on a core set of command and control servers to maintain cohesion of their botnets. These locations are used by botnet operators to support Ursnif infections by delivering configuration data containing targeting information for web inject or credential stealing functionality or even delivering additional malware binaries to infected machines.
Observed Files:
File: 404017.OjM
File: 33.gAV
File: 55.7.646397626463.1.docx
File: 307
Observed Hashes:
MD5:275b5d49485d599d84f94eadedd2780b
MD5: 2d4ec600fb64dddfd1b8a9386de7e216
MD5: cb661f43181f67cc0b4e8dc271736b4a
MD5: 7efd5d0693157767a392830fcf5b5c03
MD5: c0c22384cf3440b937d40c18c818ee9a
Observed command and control.
hxxp://www[.]dorure-palomares[.]com/sd.bks
hxxp://monsteradds[.]at/key/x32.bin
hxxp://aaxvkah7dudzoloq[.]onion/images/
PhishMe cautions its customers to be wary of emails containing suspicious links or attachments. Specific to this sample, we recommend that customers be observant for unexpected emails with a password protected attachment and the password within the body of the email.
PhishMe Simulator may consider launching simulations that follow this style of attack to further train their users to detect and report suspicious emails.
The Phishing Defense Center is the hub for our remotely managed PhishMe Triage services. The fully staffed center manages all internal reported emails for a number of organizations. All information shared has been cleansed of any identifiable data.
Want to be notified of the latest malware strains and phishing threats? – sign up for our complimentary PhishMe Threat Alerts service, delivered straight to your inbox.