Found in Environments Protected By:
Microsoft, Proofpoint
By Brooke McLain, Cofense Phishing Defense Center
Analysts at the Cofense Phishing Defense Center (PDC) see all sorts of tactics being used by threat actors to make their phishing campaigns more effective. Recently the PDC has observed phishing campaigns abusing Microsoft Customer Voice URLs, similar to the campaign reported in August. While Microsoft Customer Voice is a customer engagement/survey service that is used for plenty of benign and useful reasons, threat actors are always trying to abuse such avenues. Figure 1 is an example of such an attempt.
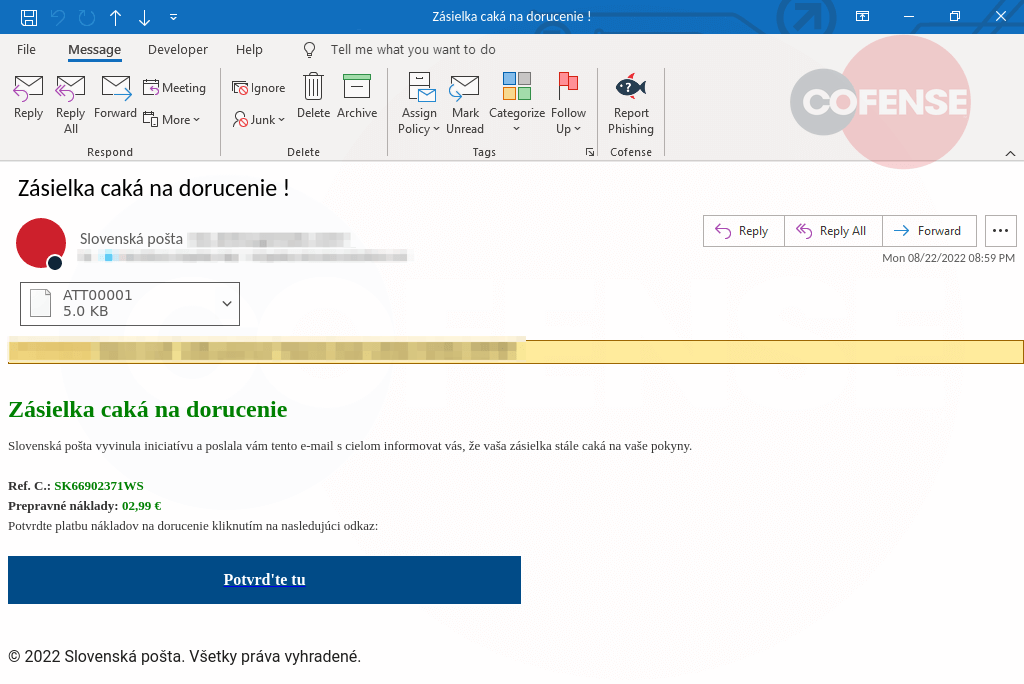 Figure 1: Email Body
Figure 1: Email Body
As seen in Figure 1, the body of this email attempts to appear legitimate due to the use of the Microsoft SharePoint logo, as well as the simple formatting of the body, which convinces the user receiving the email that this is an authentic document being delivered through SharePoint. In the message itself, the threat actor is trying to persuade the recipient to click “Go To Document >>,” leading to the first page of the phishing attack at a Microsoft Customer Voice URL. By using such a Microsoft URL, the user can be tricked into believing this is a legitimate email.
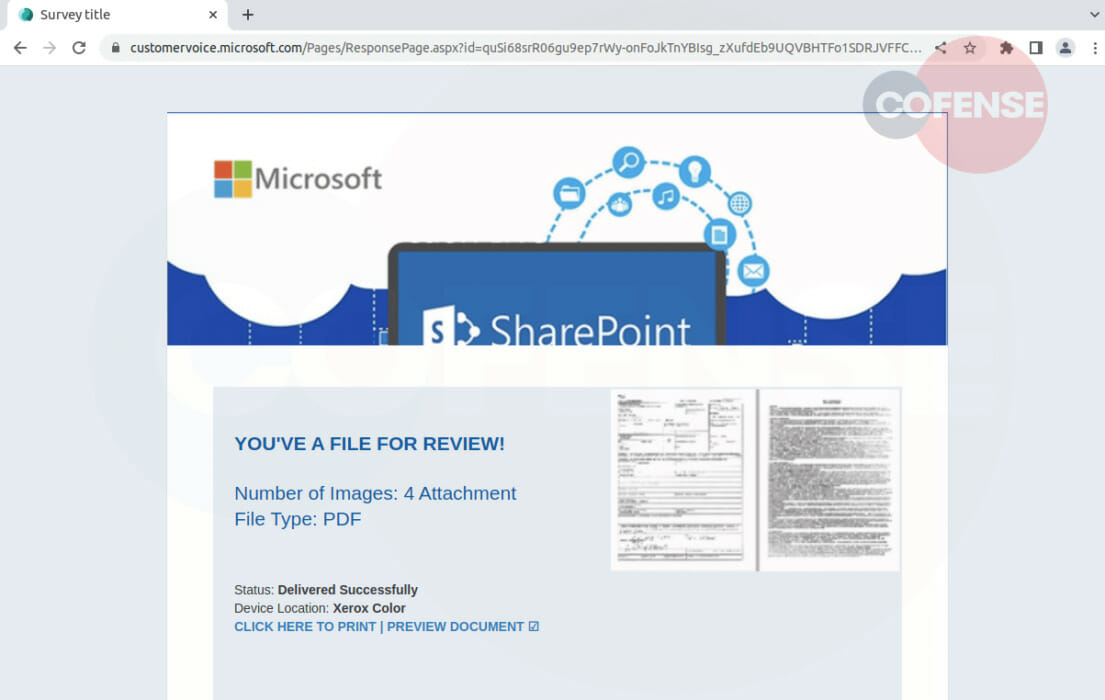 Figure 2: Phishing Page
Figure 2: Phishing Page
Once at the Microsoft Customer Voice page seen in Figure 2, the user is informed that they have to “preview” the document. This is an example of threat actors using stolen credentials to build a page that the user wouldn’t know exists and is difficult for the recipient to know. Once opening the hyperlink nested in the “CLICK HERE TO PRINT | PREVIEW DOCUMENT” section of the page, the user is redirected to the final phishing page.
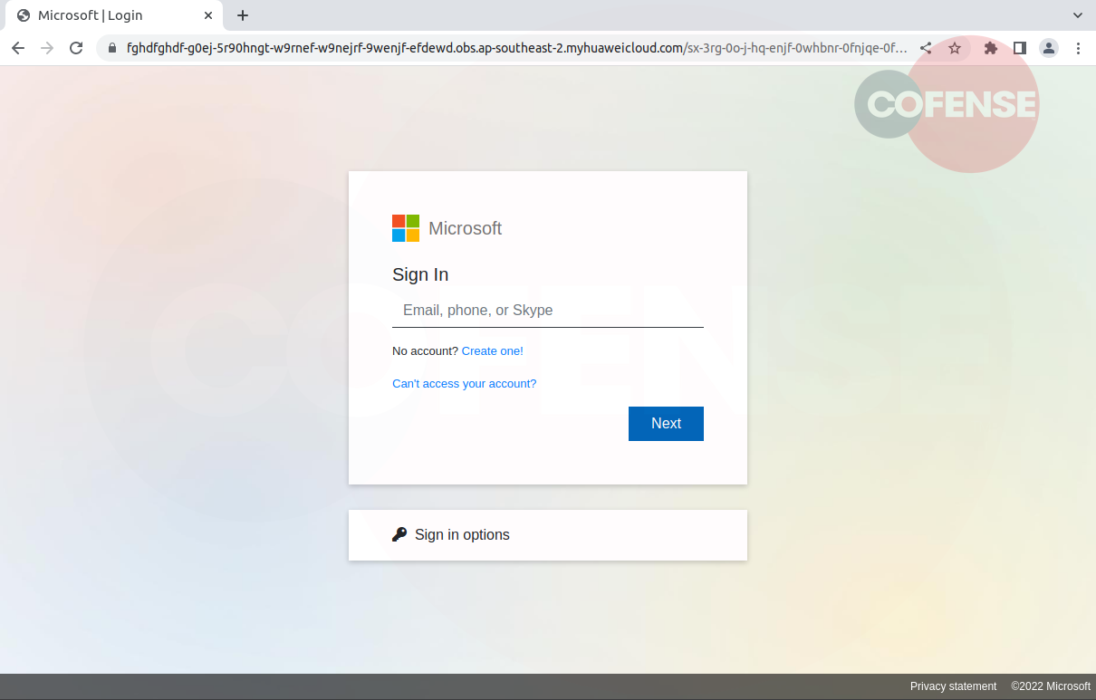 Figure 3: Phishing Page
Figure 3: Phishing Page
The second malicious URL, hxxps://fghdfghdf-g0ej-5r90hngt-w9rnef-w9nejrf-9wenjf-efdewd[.]obs[.]ap-southeast-2[.]myhuaweicloud[.]com/sx-3rg-0o-j-hq-enjf-0whbnr-0fnjqe-0fcdhnwq-enc-0enf[.]htm, seen in Figure 3, takes the recipient to the landing page of the phish where they are prompted to enter their Microsoft login credentials. The appearance of the page closely resembles that of a legitimate Microsoft login page.
In the end, this campaign used to abuse Microsoft Customer Voice services by threat actors has given them another way to get their phishing landing pages to users. Luckily for the client in this example, they had Cofense Vision, so any other instances of this specific campaign in their email environment can be quarantined. Couple that with the knowledge of the PDC analyst, and enterprises can enjoy adaptive and responsive protection. Contact us to learn more.
| Indicators of Compromise | IP |
| hxxps://customervoice[.]Microsoft[.]com/Pages/ResponsePage[.]aspx?id=qu Si68srR06gu9ep7rWy-onFoJkTnYBIsg_zXufdEb9UQVBHTFo1SDRJVF FCWDM5VzAzQTlSSk1MWS4u | 13[.]107[.]21 3[.]41 |
| hxxps://fghdfghdf-g0ej-5r90hngt-w9rnef-w9nejrf-9wenjf-efdewd[.]obs[.]ap-sou theast-2[.]myhuaweicloud[.]com/sx-3rg-0o-j-hq-enjf-0whbnr-0fnjqe-0fc hnwq-enc-0enf[.]htm | 110[.]238[.]1 27[.]235 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.