Found in Environments Protected By:
Microsoft, Cisco Ironport, Proofpoint, Trend Micro
By Brandon Cook, Cofense Phishing Defense Center
Threat actors are frequently trying to explore new ways they can take advantage of trusted services and organizations by using popular file-sharing services or abusing URL redirects for familiar websites. Recently, the Cofense Phishing Defense Center (PDC) has observed a phishing campaign, under the guise of a payment remittance, taking advantage of custom URLs from Atlassian to redirect users to their phish.
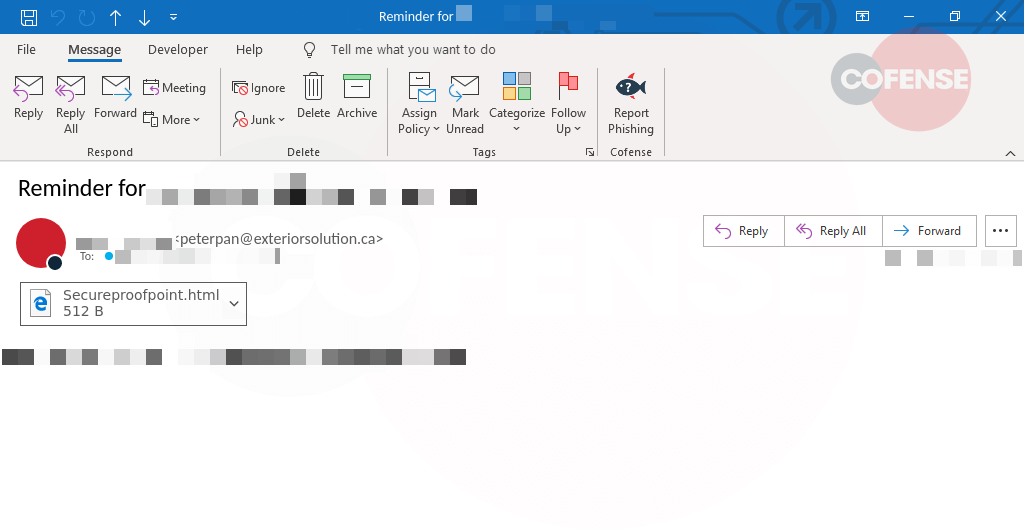
Figure 1: Email Body
In Figure 1, the threat actor uses the ‘SharePoint’ title to add confidence to the message with an attempt to make the body of this email appear to be more legitimate. By implying that a “Payment” is in progress, the recipient is more inclined to click on malicious URLs to investigate. Upon clicking the “Review Document” button, the recipient is directed to an Atlassian page, used by many organizations to collaborate, manage projects, share, etc.
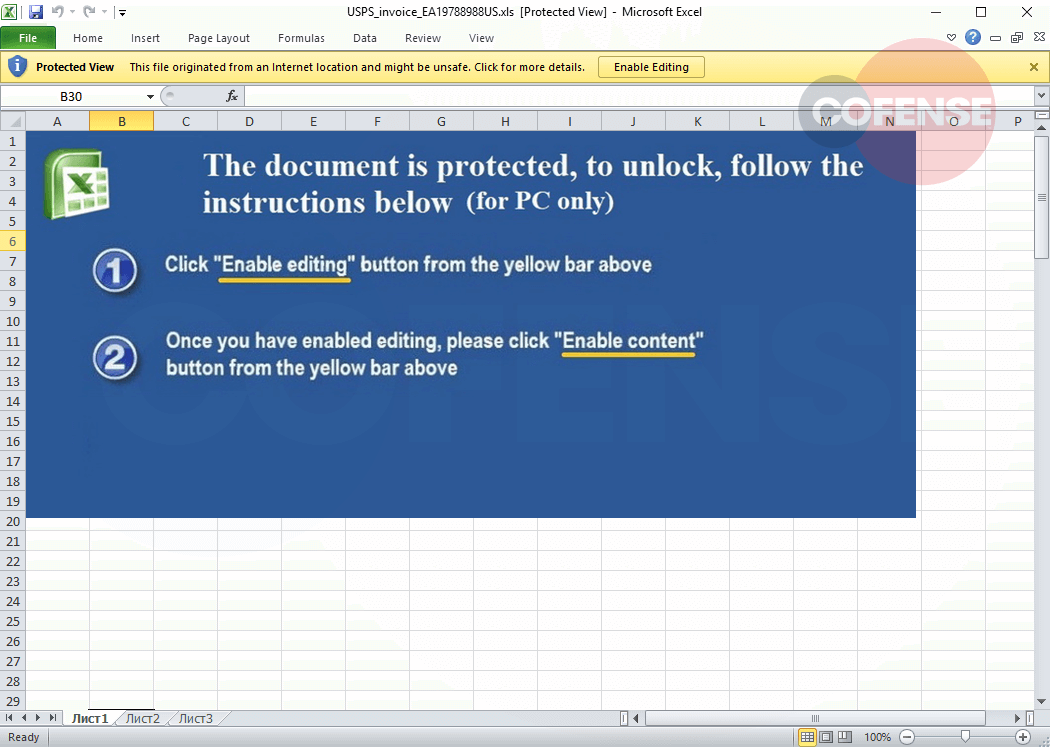
Figure 2: Phishing Page
After clicking the link, the recipient will be redirected to the page in Figure 2, hosted on Atlassian. On the landing page there are blurred documents when you hover over a “Preview Document Here” button, directing the recipient to the final page of the phish.
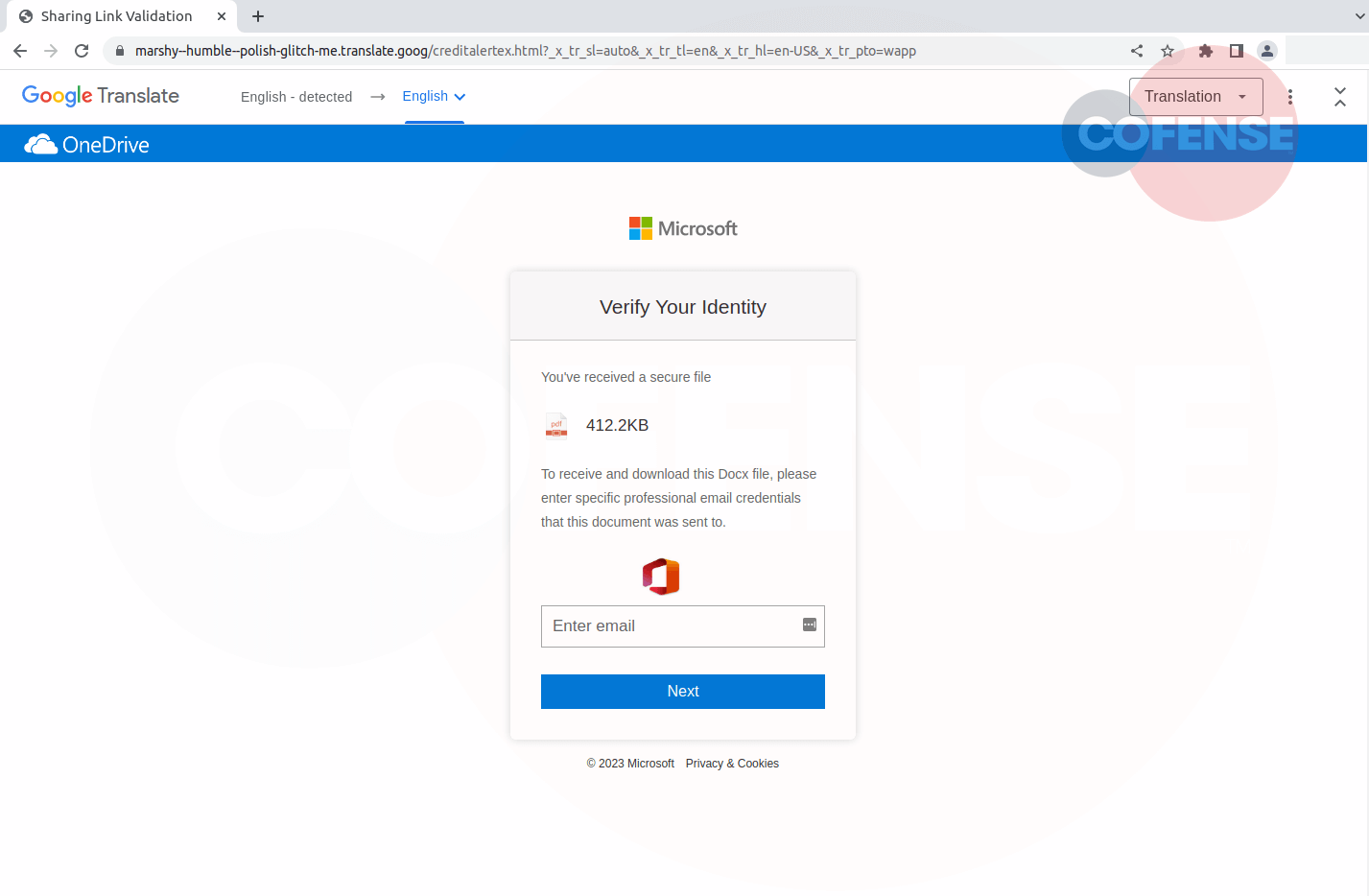
Figure 3: Phishing Page
Finally, the recipient has arrived at the landing page of the phish in Figure 3 where they are prompted to verify their identity by entering Microsoft credentials. This campaign uses a mixed bag of brands that don’t normally fit together, starting with SharePoint, Confluence, and now Microsoft and Google. After all the techniques used by the threat actor, this page is hosted on a Google Translate page.
Although this campaign may have seemed convincing at first by using popular logos and financial transactions it’s using a new, but quite familiar, organization to host their initial phishing page. The Cofense Phishing Defense Center (PDC) was able to detect the malicious intent and keep our clients secure from this attack. If you would like to learn more about the PDC, reach out to us
| Indicators of Compromise | IP |
|---|---|
| hxxps://remittancepaymentnotification[.]atlassian[.]net/l/cp/mTeibV2o | 104.192.142.18 |
| hxxps://csb--p44y4q-netlify-app[.]translate[.]goog/?_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=wapp | 142.251.163.132 |
| hxxps://prism--thin--fear-glitch-me[.]translate[.]goog/remittanceex[.]html | 172.253.122.132 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.