Is phishing still keeping you up at night? Do disparate systems and switching screens to analyze and respond to phishing frustrate you? Or, what about excessive phishing alerts that could be better solved through automation? Over a year ago, Cofense built an integration with ServiceNow® Security Incident Response (SIR). The purpose: integrate Cofense Triage™ and ServiceNow SIR to create security incidents in SIR and allow an analyst to analyze and investigate employee-reported suspicious emails in either platform. The integration was well-received for the first version, and since then, Cofense Triage has added new capabilities that have been extended to ServiceNow SIR. Creating a security incident at the cluster-level, responding to reporters, and downloading email artifacts, are just a few features that have been added to the next version of the integration, and then some! Mutual customers operating Cofense Triage 1.24 can integrate with ServiceNow’s Quebec, Rome, or San Diego releases. The foundation of the integration is still the same.
- Configure authentication (Triage Host, Client ID, Client Secret, and MID Server (optional)
- Define incident criteria that creates an SIR entry in ServiceNow.
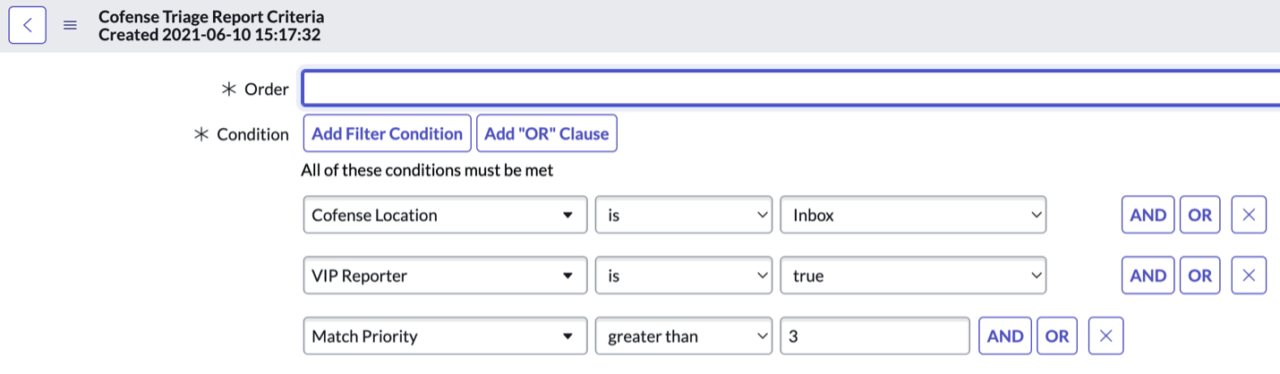
Incident Criteria Configuration to Create Entries in SIR
Let’s look at the 10 enhancements built into this integration.
1. Clusters: Create security incidents based on cluster criteria
Cofense Triage clusters multiple reported emails. ServiceNow can then ingest Clusters based on criteria and create one security incident. For example, 5 reported emails bound to one Cofense Triage cluster, can create one security incident in ServiceNow SIR.
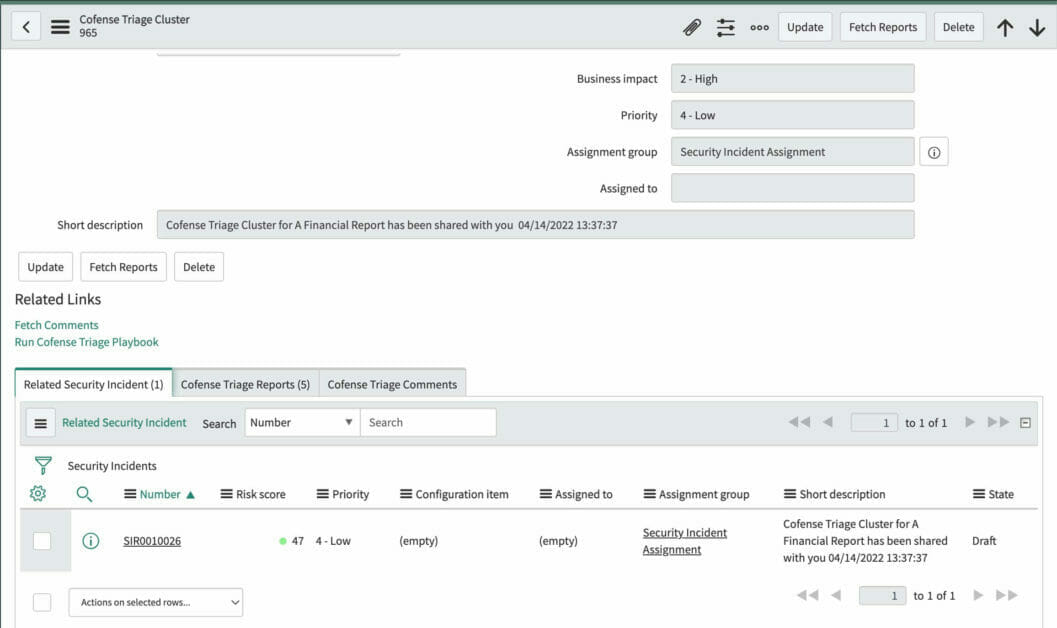 Security Incident Created from a Cluster
Security Incident Created from a Cluster
2. Reports: Ingest reports associated with clusters
When multiple reports are present in a cluster, analysts can choose to fetch all the reports from the cluster if they choose. Each report carries the relationship with the cluster and SIR record.
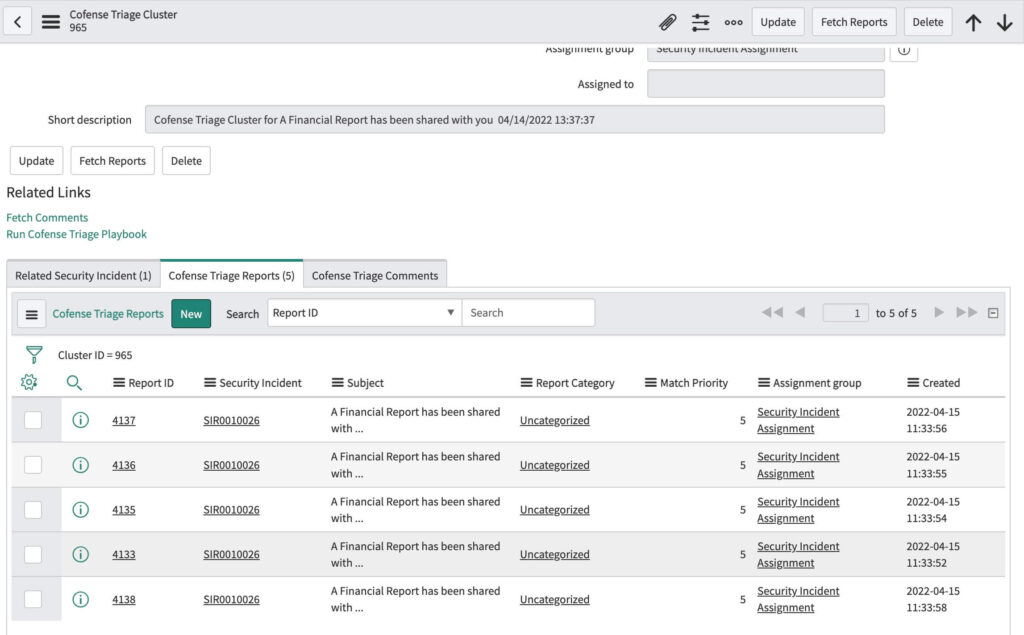 Fetched Reports Associated with a Cluster and Linking to SIR
Fetched Reports Associated with a Cluster and Linking to SIR
3. Fetched Reports Associated with a Cluster and Linking to SIR
Want to add the original email to the SIR? ServiceNow can download the full email(s) as .eml
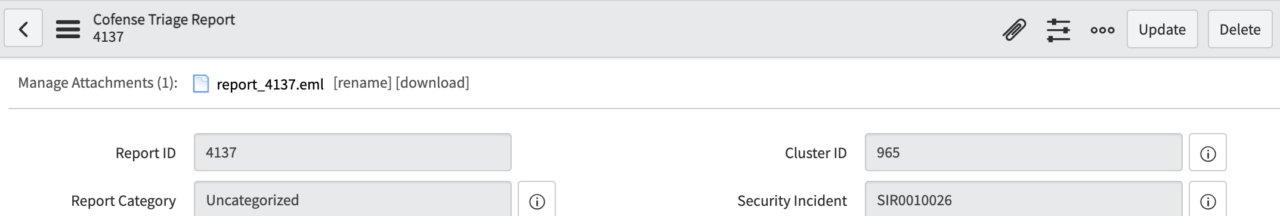 Report Downloaded as .eml File
Report Downloaded as .eml File
4. Attachments: Download attachments from reported emails
Attachments can be downloaded on demand and packaged into the SIR for additional analysis and research.
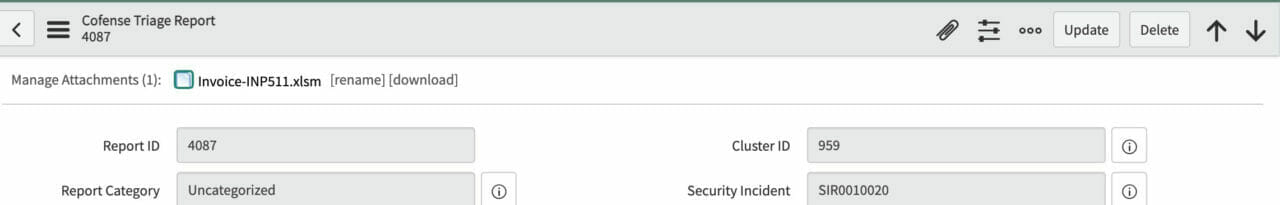 Download Attachment Capability for Additional Analysis
Download Attachment Capability for Additional Analysis
5. Relationships: Links between security incident and other reports
In addition to getting all reports, SIR will link and show the relationship between a cluster and reports.
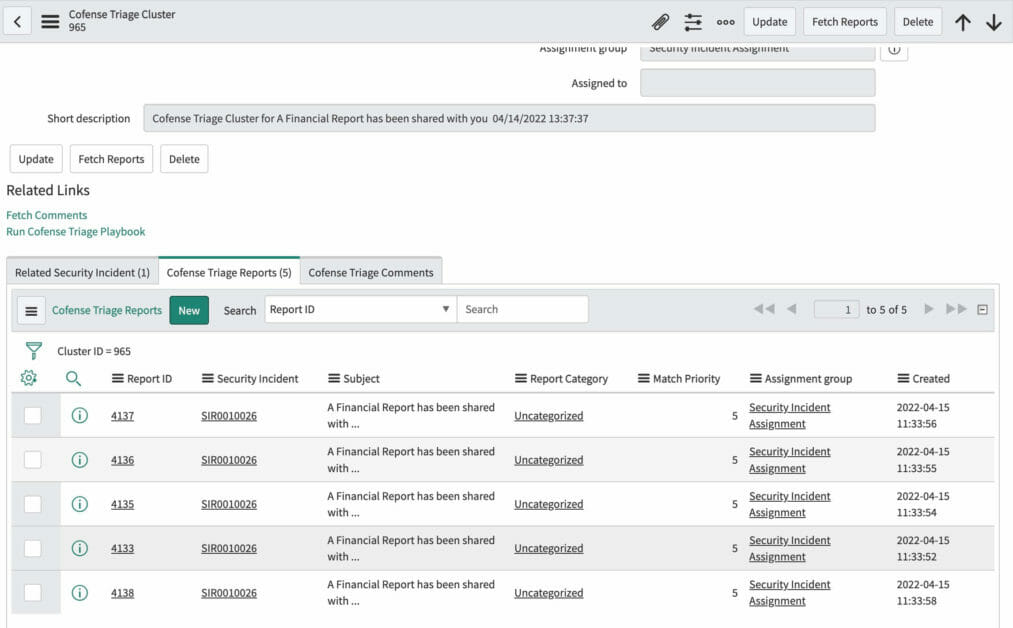 Fetched Reports Linking to SIR
Fetched Reports Linking to SIR
6. Fetched Reports Linking to SIR
Execute a playbook to categorize reports, single or multiple, from a cluster within ServiceNow SIR.
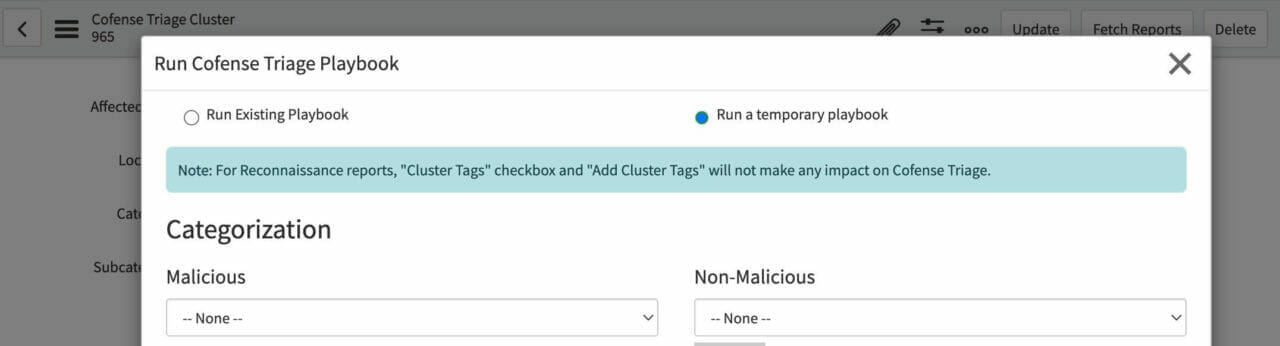
Categorize Reports as Malicious or Non-Malicious
7. Execute Playbooks to: Respond to Reporters and teams/groups
It’s important to keep reporters informed so that they continue to report suspicious emails that evade SEGs. Choose from various notification templates ingested from Cofense Triage into SIR so that specific responses can be sent to reporters and cybersecurity and IT team members.
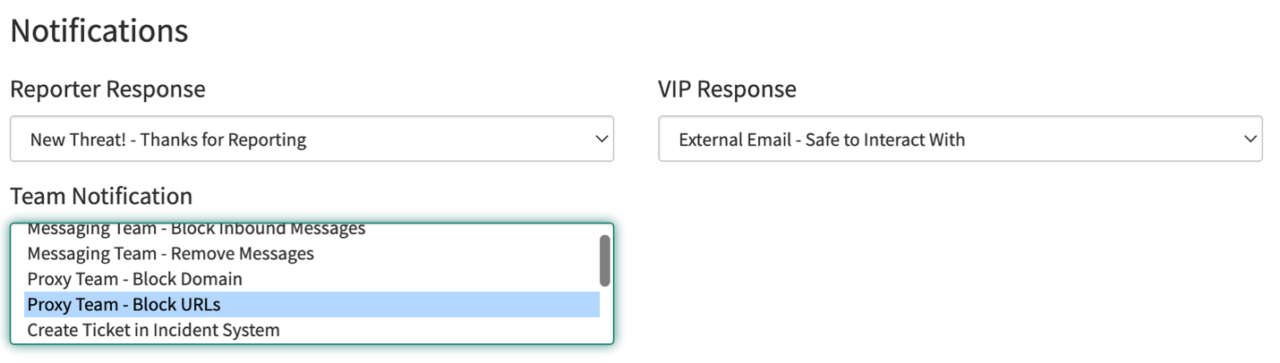 Response to Reporters and Team Members
Response to Reporters and Team Members
8. Execute Playbooks to: Apply tags to reports
When executing a playbook, tag reports in Triage to help security analysts keep track of various reports and workflow being conducted.
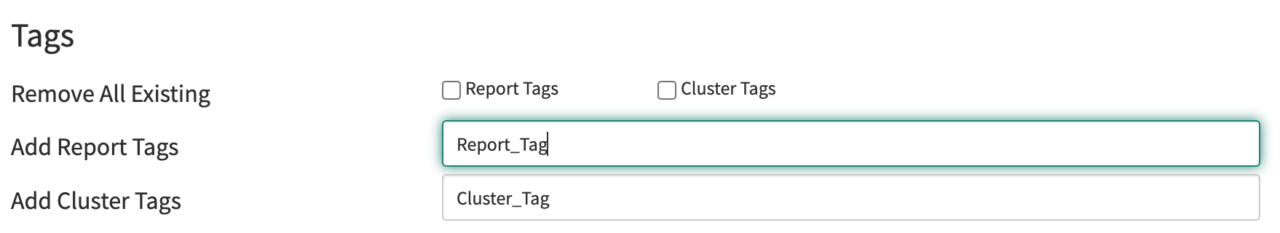 Add Tags When Processing and Executing Playbooks
Add Tags When Processing and Executing Playbooks
9. Comments: Get comments from reports
Cofense’s Managed Phishing Detection and Response service uses report comments that provide clients with other threat indicators associated with a reported email. These are typically indicators that are not visible in the email, but if clicked, redirect to other nefarious sites or link to more malware.
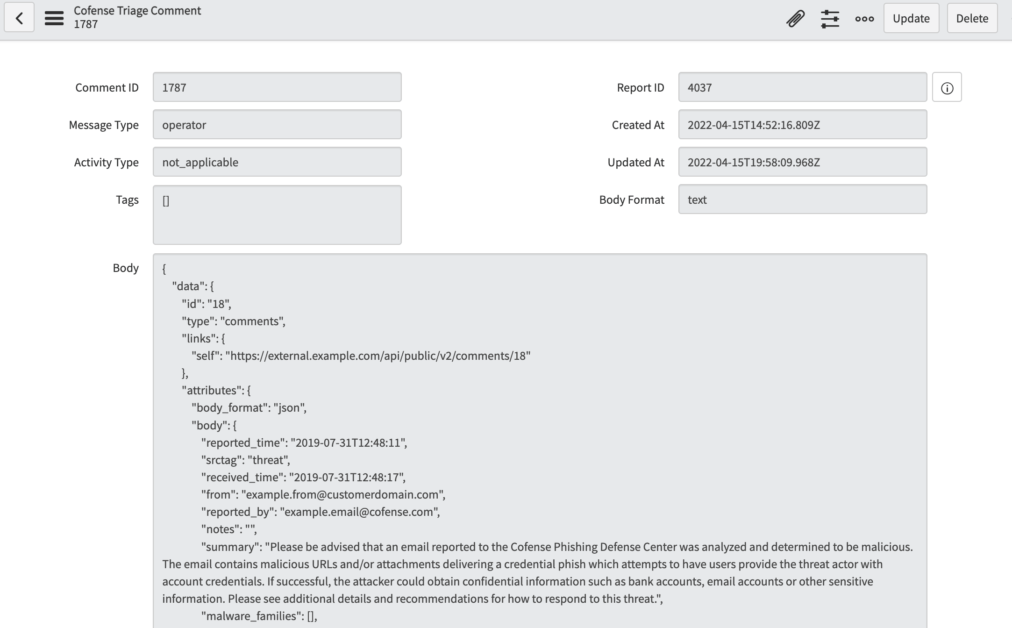 Sample Comments with Other Indicators From Reported Email
Sample Comments with Other Indicators From Reported Email
10. Threat Indicators: Get more threat indicators from reports
Analysts designating threat indicators across URLs, domains, and attachments in Cofense Triage, can set them to Malicious, Suspicious, or Benign. ServiceNow will ingest these indicators to be used in additional operational workflow. Additionally, other observables in Cofense Triage, such as headers, are populating SIR’s observable table, too.
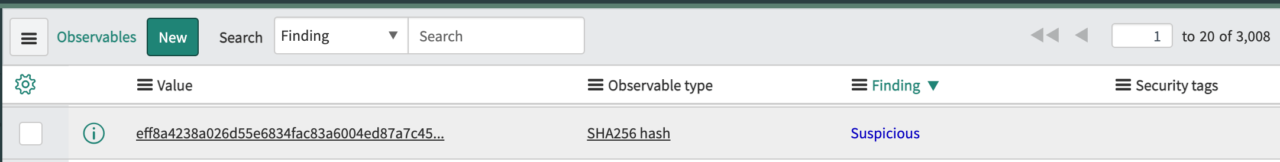 Suspicious Hash Threat Indicator Finding
Suspicious Hash Threat Indicator Finding
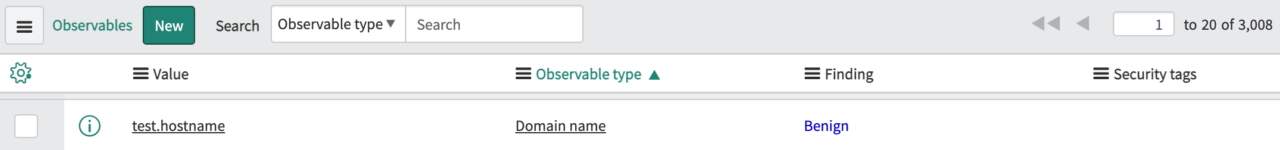 Benign Domain Threat Indicator Finding
Benign Domain Threat Indicator Finding
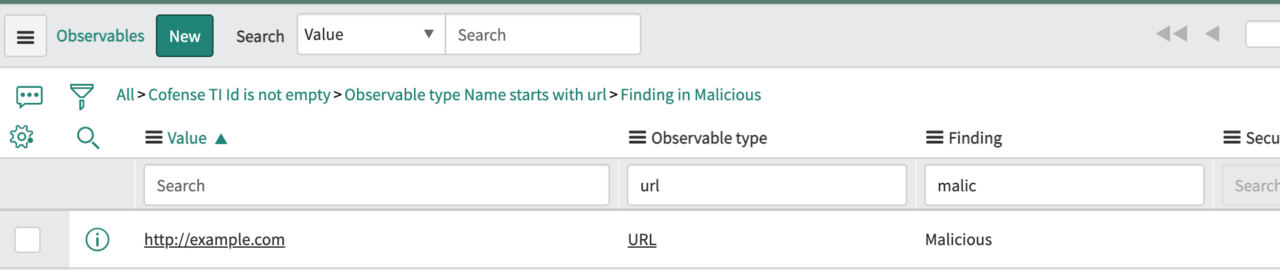 Malicious URL Threat Indicator Finding
Malicious URL Threat Indicator Finding
Cofense Triage and ServiceNow SIR are more tightly integrated to allow security teams to create a unified workflow that leverages the power of both platforms. By determining criteria to create an incident, security teams can ingest, prioritize, and close security incidents without flipping back and forth between screens.