By: Nathaniel Raymond
An evolving set of credential phishing activity targeting Microsoft Office 365 credentials has been observed reaching enterprise email inboxes. This activity is categorized by several key components that make it stand out from other campaigns. Key components include:
- Over 120 unique phishing domains created using the “bulletproof” registrar R01-RU, hosting thousands of phishing URLs.
- Abuse of Cloudflare CAPTCHA and IP proxying services for efficacy and anti-analysis
- The use of phishing services attributable to the seemingly defunct Phishing-as-a-Service operation called “Caffeine”, which was created by the kit maker “MRxC0DER” and features an API for email validation
Emails within this activity set are designed simply, using an embedded link (usually an open redirect) to redirect the user to the credential harvesting page. URLs of these credential harvesting page have followed certain patterns within the past year. These patterns often change after a period of time, with the most recent and biggest change occurring in April 2023. Email subjects range from notifications about passwords or messages to tax themes.
Who RU? “Bulletproof” Russian Registrar Used to Protect Threat Actor Identity and Infrastructure
The phishing activity set addressed in this report exclusively uses the domain registrar R01-RU. R01-RU is identified in various hacking forums as a “bulletproof” Russian registrar where threat actors can create and host a domain securely for malicious purposes, without having to worry about losing registered domains to fraud reports and shouldering the sunk cost that comes with it. This makes registering and hosting domains attractive to adversaries. It may also mean that even if the phishing content is removed, the adversary still controls the domain and can reuse it in future campaigns.
Cloudy with a Chance of Phish: Cloudflare Services Abused to Streamline and Protect Phishing Operations
Cloudflare is a legitimate domain security service for everyday users to keep their website(s) secure. However, this makes Cloudflare services such as CAPTCHAs, IP proxying, and other Cloudflare security services attractive to threat actors as well. Abuse of Cloudflare services enables threat actors to secure their own operations and infrastructure in several ways:
- CAPTCHA services ensure that the visiting client is an actual user from the targeted country through IP filtering
- CAPTCHA services also ensure that phishing content cannot be investigated by automated security services
- IP proxying services allow the threat actor to hide the domain’s original hosting provider to slow down the takedown process.
The activity set discussed in this report makes use of both CAPTCHAs and IP proxying for every credential phishing domain created through R01-RU.
Figure 1: An example of abused Cloudflare CAPTCHA services
It’s just a PHaaS Mom: URLs Use Consistent Patterns at Domains Likely Belonging to “Caffeine” Phishing-as-a-Service Provider “MRxC0DER”
Phishing-as-a-Service is nothing new, granting adversaries with little-to-no technical knowledge access to phishing tools such as phishing kits, email templates, emailer scripts, domains to host credential phishing pages, and much more for a price. The threat actor “MRxCODER is a prolific phish kit maker who offered such phishing services and sold the services through his now seemingly defunct shop “Caffeine”. His brand and logo spoof the legitimate live streaming service Caffeine TV. Although the Caffeine phishing services appear to be no longer used or updated, this campaign shows that the kits it sold are still in use. In Figure 2, we show one domain (netsn[.]ru) that MRxC0DER specifically identified as owned by his phishing service. 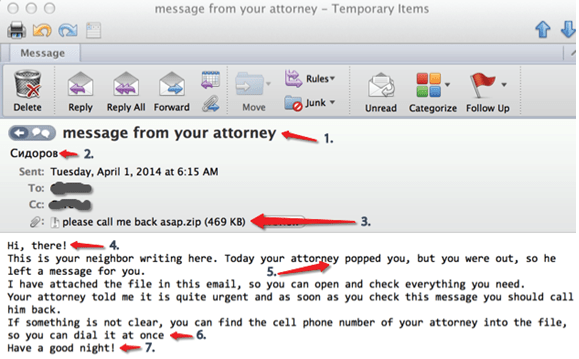
Figure 2:MRxC0DER Malicious Domain Link
This domain (netsn[.]ru) and its URLs have shared distinct patterns with the other domains in a larger activity set over the majority of the past year:
- Each domain is within the .ru TLD
- Each domain is registered through R01-RU
- Each URL found at these domains has a path containing alphanumeric strings of specific lengths, accompanied by one of several designated prefixes or suffixes
The Caffeine store on Telegram was created in September of 2021, advertising Version 8 of a Microsoft Office 365 credential phishing kit, as shown in Figure 3. The website caffeines[.]store goes further back, with its creation on May 1st, 2021. Although the Caffeine shop is no longer maintained on either Telegram or the main website, phishing emails that reflect these particular patterns have been observed reaching user’s inboxes since Q3 of 2022.
Figure 3: Caffeine Telegram Shop Advertises CAPTCHA Services In September 2021
Several iterations of the phish kit have been seen throughout the life span of the Caffeine service, demonstrating MRxC0DER’s flexibility and adaptation. For instance, as shown in Figure 3, the Caffeine shop previously advertised the use of Google CAPTCHA, but appears to have since switched to Cloudflare CAPTCHA. This flexibility may also extend to branding, and the Caffeine store may have been rebranded and/or moved while maintaining the same essential services. Cofense has not yet found evidence of a new brand or location at this point. However, given the maintenance of Caffeine-related domains, we surmise that MrXC0DER remains active, even if he is no longer selling his services at the Caffeine store. It is also important to note that skilled threat actors can modify and deploy phishing kits they have found, or previously purchased, to fit their own needs.
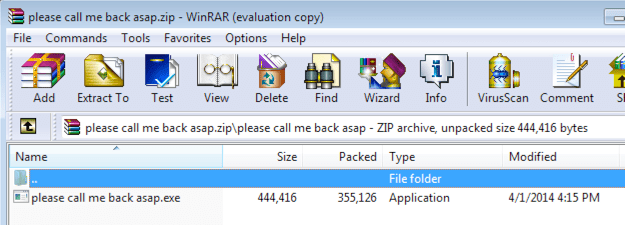
Figure 4: Email and Phishing Page Example
The emails and the hosted phishing pages within this activity set were designed with simplicity in mind. Figure 5 shows an example of an email with an embedded redirect link that takes the user to the credential phish, also in Figure 5. The links embedded in these emails generally abuse open redirects at both well-known and little-known legitimate websites, making defense via automated IOC recognition at this stage difficult. However, users should receive consistent phishing awareness training in order to recognize suspicious emails based on other components, such as grammatical errors and URLs that do not correlate with the email body and anchor text or with the user’s expected destination. Once the user lands on the credential harvesting page, a legitimate-looking prompt will ask the user for their email address. These phishing kits conduct a request to an API that validates the email. If the email is valid, the phish will prompt for a password on the credential harvesting page. The credential-harvesting URLs (unlike the redirect URLs embedded in the emails) are easily identifiable by the URL patterns shown earlier in Table 1, and security teams can attempt to block this traffic.
Outlook
Although Cofense Intelligence has identified patterns and characteristics that lead us to categorize these phishing threats as an “activity set”, it remains unclear whether this activity is being conducted by several threat actors (possibly current or former “Caffeine” customers) using the same tools or by a single actor (possibly MRxC0DER himself). What is clear, however, is that the phishing emails within this activity set are regularly reaching the inboxes of enterprise email users, and that patterns within the set often change, making continuous tracking more difficult. Activity following observed patterns peaked in March 2023, and fell over the course of April and May, in concert with the adoption of the newest pattern (involving “LOG” strings). The use of all other patterns was simultaneously discontinued, providing limited indication that the activity is conducted by a single actor or coordinated group. However, these observations may not represent the full extent of the activity, as there may be other new, unobserved patterns replacing the old activity.
Figure 5: Volume of Unique Phishing URLs Following “Caffeine” Domain Patterns and Observed Reaching Enterprise Inboxes