By: Adam Martin, Phishing Defense Center
As CapCut continues to dominate the short-form video editing scene, cybercriminals are seizing the opportunity to exploit its popularity. In a recent phishing campaign observed by the Cofense PDC team, threat actors have crafted convincing fake CapCut invoice lures (Figure 1) designed to harvest Apple ID credentials along with credit card information.
By leveraging the app's widespread appeal and mimicking its official branding, these attackers aim to deceive users into divulging sensitive information. This blog post delves into the mechanics of this phishing scheme, highlights the tactics used, and provides insights on how to recognize and avoid such threats.

Figure 1 - Email Body
Once clicked by a user, the “Cancel your subscription” button in Figure 1 will open a webpage in their default browser. The user is then redirected to an imitation Apple ID login page at the URL “Flashersofts[.]store/Applys/project/index[.]php,” which is a domain that is unrelated to Apple services. As seen in Figure 2, the victim is prompted to enter their Apple ID Credentials. The use of official branding further instils a sense of trust in the webpage.
Figure 2 - First Landing Page
When credentials are entered, as per Figure 3, they’ll be sent via an HTTP POST request to 104[.]21[.]33[.]45 to exfiltrate the credentials.
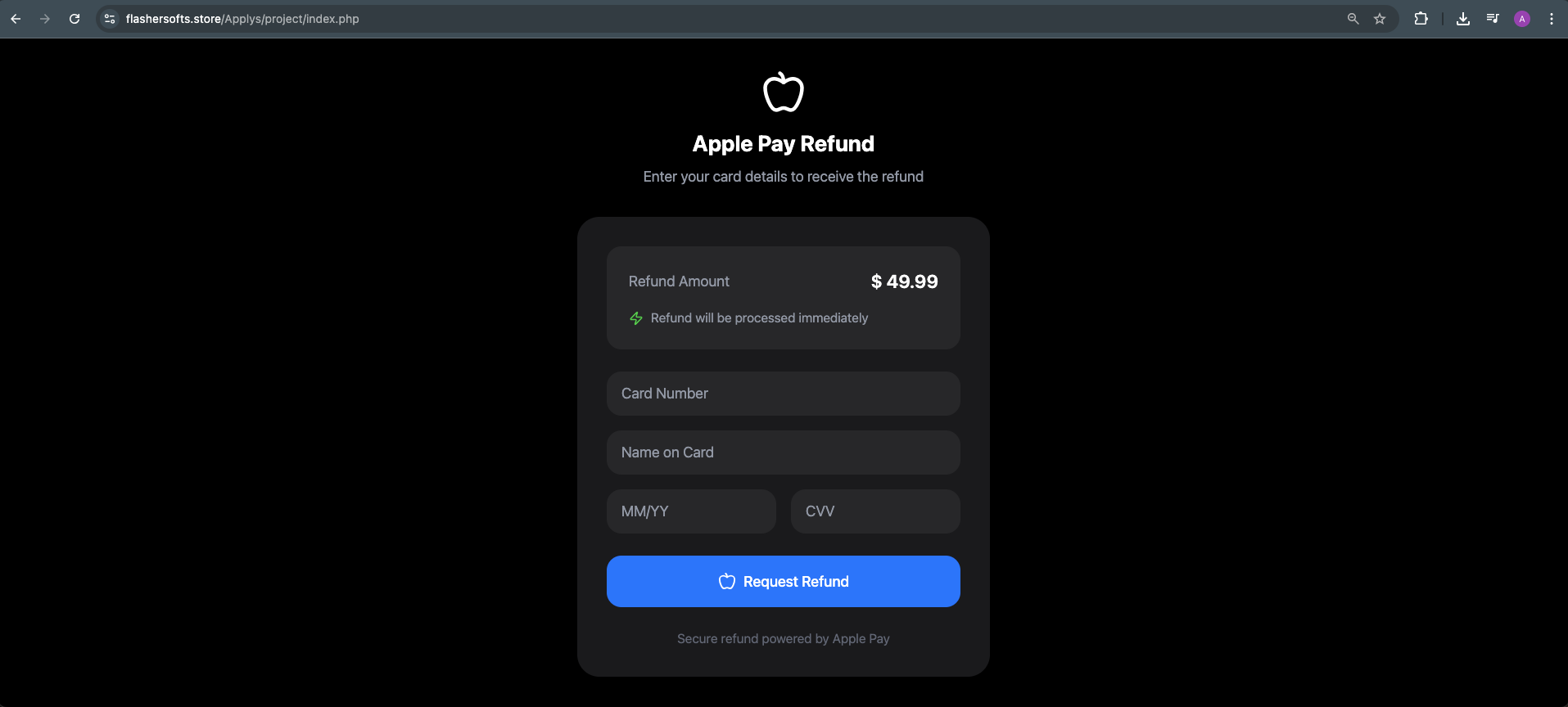
Figure 3 - Fake Credentials Posted
This is further evident in Figure 4, which depicts fake credentials input during the analysis of this campaign. These credentials were sent to the threat actor’s server as part of the analysis.
Figure 4 - Credentials Posted in Plaintext
After the user's credentials have been exfiltrated to the C2 server mentioned previously, the page is refreshed to reveal the second part of this double-barreled phishing attack. This method acts as the second prong in the phishing hook, with the financial incentive of the refund acting as the bait.
Figure 5 - Secondary Phishing Page
Mirroring its partner, this dialog box, shown in Figure 5, requests card information to refund money. Notably, this shares the same C2 and base address as previously mentioned above.
Figure 6 illustrates the same POST request, however, this time with credit card info being exfiltrated. A clever tactic is the input box not recognizing anything less than a standard amount of card number digits, i.e., if it’s missing 1 digit of the 15 required, an error will be returned, providing a form of input validation.
Figure 6 - Second set of credentials posted
Utilizing a dummy card generator, Figure 7 shows the given card info being exfiltrated in plain text.
Figure 7 - Exfiltrated Credentials in plain text
The last step in this attack chain is done to avoid arousing suspicion by the now duped user. A fake authentication code check box, shown in Figure 8, is presented. Regardless of how many times “send new code” is used, nothing will ever be sent. This step is likely done to increase the efficacy of the attack and to keep the user from reporting the event further, instead blaming some error with the authentication code.
Figure 8 - Fake Authentication code prompt
This phishing campaign highlights how easily trust can be manipulated through familiar branding and urgency. By imitating CapCut’s/Apple’s identity and dangling the threat of unwanted charges, attackers guide victims through a seamless two-stage credential theft process. The use of a fake verification step at the end is a subtle yet strategic move to delay suspicion and extend the attack window. As always, skepticism is a critical defense—check URLs carefully, question unexpected prompts for sensitive information, and report suspicious messages. The Cofense PDC team will continue tracking and exposing these evolving social engineering tactics.
Stage 1 - Observed Email Infection URL: | Infection URL IP(s): |
hXXps://yms1[.]ynotmail[.]io/clients/link[.]php?M=703770538&N=3194361&L=453538585&F=H | 99[.]192[.]255[.]26
|
Stage 2 - Observed Payload URL(s): | Payload IP(s): |
hXXps://flashersofts[.]store/Applys/project/index[.]php | 172[.]67[.]141[.]41 |
All third-party trademarks referenced by Cofense, whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and the use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of endpoint protections are based on observations at a point in time, based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.