By: Don Santos and Harsh Patel, Cofense Phishing Defense Center
Social media is widely used in marketing, helping businesses to generate ads that attract potential customers. But what if you received an email stating, "YOUR ADS ARE TEMPORARILY SUSPENDED"? What steps would you take? The urgency of the email instantly grabs your attention, and your first thought might be to click and investigate, hoping to get it fixed promptly. However, instead of fixing things, you could end up with your business account getting hacked. The Cofense Phishing Defense Center (PDC) has discovered a new phishing campaign that tricks users into giving out access to their Meta Business accounts. While social media phishing attempts are prevalent, this one went above and beyond by employing fake chat support, providing detailed instructions, and attempting to add itself as a secure login method.
Figure 1: Malicious Email
The phishing campaign starts with the victim receiving a fake Instagram alert with the theme of “Support ID: #xxxx - Critical Advertising Restrictions on Your Account,” as shown in Figure 1. It states the user has violated advertising laws, mentioning Instagram's policies, as well as the EU GDPR, and that the ads are suspended as a result. This is a common theme observed with these Instagram/Meta spoofing credential phishing emails. The user is asked to click the “Check more Details” button to resolve this concern. It is easy to see how this could trick users, especially with more businesses relying on social media platforms for advertisements. This poses a serious and urgent concern, as it can disrupt daily business operations and cause these businesses to lose out on potential customers. However, it is important to note that the from address is not coming from Instagram's official support email (support@instagram[.]com) but rather (noreply@salesforce[.]com). When clicking the "Check more details" hyperlink in the email, users are redirected to a fraudulent page that informs them their account is at risk of suspension and termination, as shown in Figure 2 below. Comparing this to a legitimate Meta Business page, most people will think that there isn’t anything out of the ordinary. But further checking the URL on the browser’s address bar reveals that they are not on a legitimate Meta domain, instead shows (businesshelp-manager[.]com).
Figure 2: Initial Infection URL Landing Page
Upon clicking the “Request review” button, the user is asked to input their name & business email to proceed to a chat support agent, as shown in Figures 3 & 4 below. This will continue to a different page where the rest of the phishing attempt is performed. Based on our analysis, the attacker aims to hijack Business Meta accounts by registering themselves as a “Secure Login” via the Authenticator App feature of Meta. The attacker does this in two different ways: a fake tech support chatbot or a supposed “setup guide” with step-by-step instructions.
Figure 3: Landing Page - Chatbot Information Form
Figure 4: Chatbot – Initial Conversation Part 1
The Threat Actor (TA) also provides an instructional guide for adding Two-Factor Authentication (2FA) to the user’s business account, as shown in Figure 5 below. This is a secondary account takeover method used by the TA if the chatbot phishing attempt is unsuccessful. This method mimics a do-it-yourself way to "fix" the user's account. To access this, a visible “View Account Status” can be clicked (on the right middle side of the page), revealing detailed instructions on how to start a “System Check” and fix the problem yourself. From the user's perspective, they are fixing their account faster instead of dealing with a support chatbot. But when emulating the steps given, it gives the attacker another way to log in to the Business Meta account via the hacker's Authenticator app named "SYSTEM CHECK", giving the Threat Actor multiple ways to hijack the account.
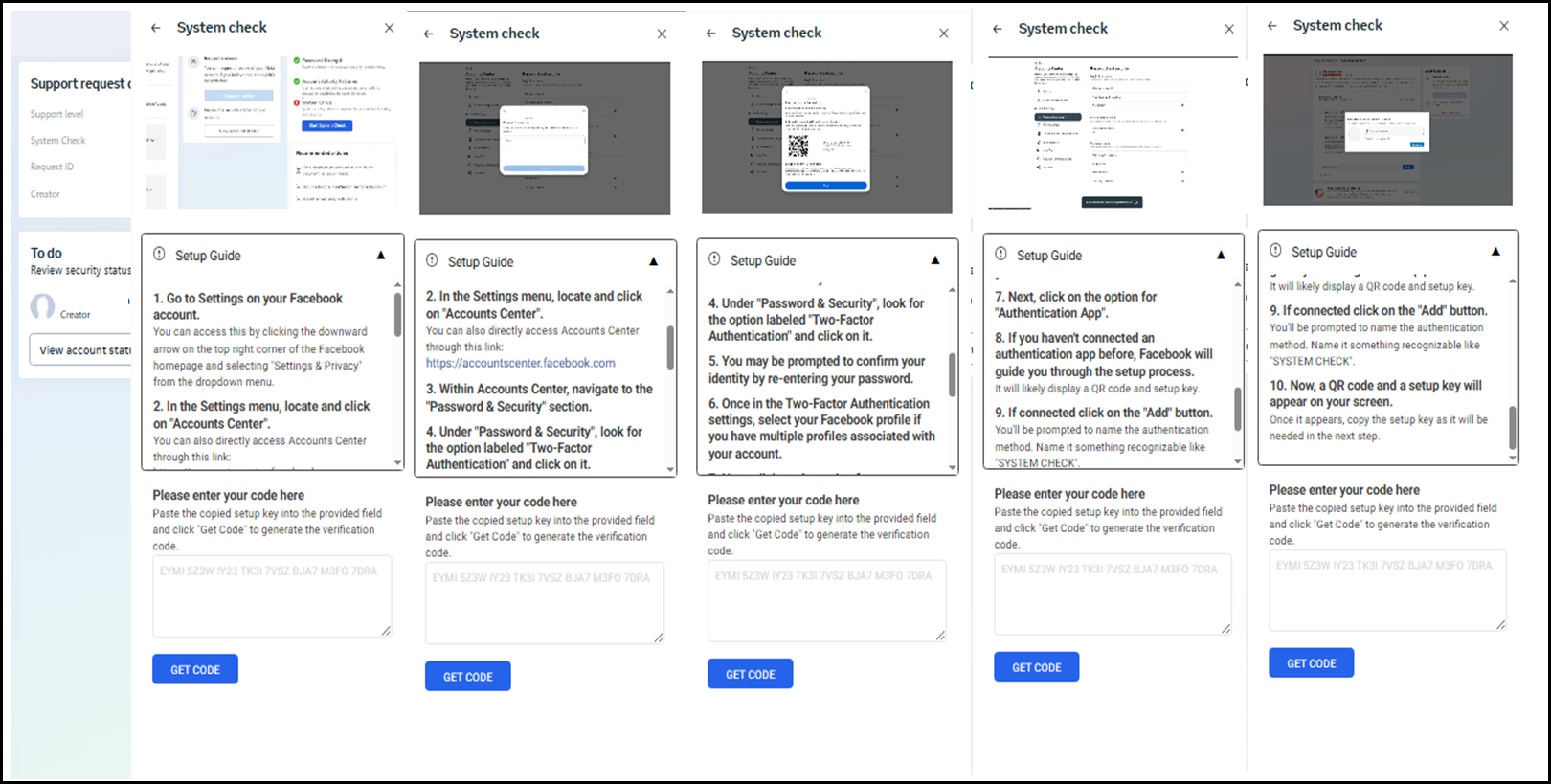
Figure 5: Step by Step Instruction to Adding Two-factor authentication (2FA)
During our testing, we were able to get a copy of the hacker's video instruction, detailing how it tricks the user into adding them as a Two-Factor Authentication (2FA), shown in the video below.
The main tactic this phishing campaign uses to steal from users is through a fake support chatbot. If the victims choose to chat with the fake support client, they are first asked about their business accounts. The attacker even asks for screenshots of the users' business accounts, perhaps as a way of screening victims. If they see fit, they proceed to instruct the victim how to perform a “SYSTEM CHECK.” Initial dialogue from the support chat can be seen in Figure 6 below. As a failsafe, the agent also asks for a contact number in case communication gets cut. If the victim continues with the fake chat support, they are asked to navigate to their business page settings on Facebook and provide a screenshot. The chat agent then explains that the user has violated certain advertising standards and is due for suspension. The TA then asks to confirm the user's private information asking to provide screenshots of their personal information page. We can see how a typical chat goes in Figures 7 & 8 shown below.
Figure 6: Chatbot - Initial Conversation Part 2
Figure 7: Chatbot - Business Page Screenshot
Figure 8: Chatbot – Flag Reason & Personal Info Screenshot
After following all instructions from the chat support, the user is then asked to click "Activate System Check.” Upon clicking the button, the page reloads and asks the user to enter their Facebook password, as shown in Figure 9 & 10 below.
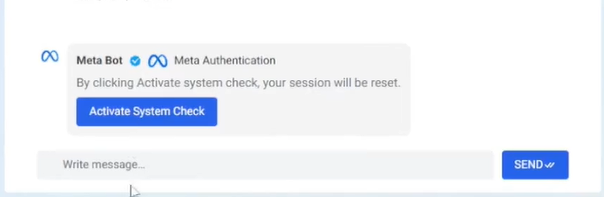
Figure 9: Chatbot – Activate System Check
Figure 10: Meta Phishing Page
This phishing campaign serves as a stark reminder of the evolving threats businesses face in securing their social media credentials. Users should try to actively remain cautious and verify all communications before responding. The campaign demonstrates a high level of attention to detail, with emails and landing pages that closely resemble legitimate communications. Furthermore, the inclusion of live agent support adds an additional layer of deception, making users believe they are interacting with Meta's official support team. Always take the time to verify the sender and carefully examine the URL before taking any action. As phishing tactics continue to evolve, it is crucial for users to stay alert and report suspicious activity promptly to prevent potential damage.
| Indicators of Compromise | IP |
|---|---|
| hXXps://link[.]engagezc[.]com/b/DthfdUh51xpmxoZc44di0w~~[.]PZmcCYg1oTEvcB_7uzh1T49cj3sB[.]gAE5JmtFTr7FkJogNps2nA~~?q=hXXps%3A%2F%2Fbusinesshelp-manager[.]com%2F#user_email= | 44[.]238[.]235[.]140 44[.]239[.]125.[1]15 52[.]35[.]19[.]120 34[.]213[.]244[.]139 |
| hXXps://businesshelp-manager[.]com/chat[.]php?id= | 104[.]21[.]66[.]161 172[.]67[.]205[.]110 |
All third-party trademarks referenced by Cofense whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding the circumvention of end-point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog, are registered trademarks or trademarks of Cofense Inc.