By Nathaniel Sagibanda, Cofense Phishing Defense Center
Customer feedback is always important for organizations of all sizes. There are several well-known companies that offer different kinds of feedback tools. But what if, however, those customer feedback systems were utilized to launch Phishing attacks? The Phishing Defense Center (PDC) has observed an interesting technique in which a threat actor sends a spoofed eFax notification using a compromised Dynamic 365 Customer Voice business account to lure the recipient into credential phishing.
These credential phishing emails have been broadly disseminated, with no specific industry targeted. The campaign has hit dozens of companies in multiple sectors, including energy, financial services, commercial real estate, food manufacturing, furniture, data analytics, and professional services."
The phishing email, as seen in figure 1, claims the recipient has received a “10-page corporate eFax”, which is a familiar tactic to lure interaction with the email. There are several interesting clues in this email that most likely encourage the recipient to report quickly. Starting at the top of the email with the subject, which doesn’t seem to align with the rest of the email. The recipient most likely opened the message expecting to see a message related to a document signature need. However, that isn’t what we see as you read the message body. It leads the recipient to believe they received the file attached via the ‘Attachment File Type: pdf’, without an actual file name, delivered from the fax. Continuing further down the email, we see a footer that indicates this email was generated from a survey site.
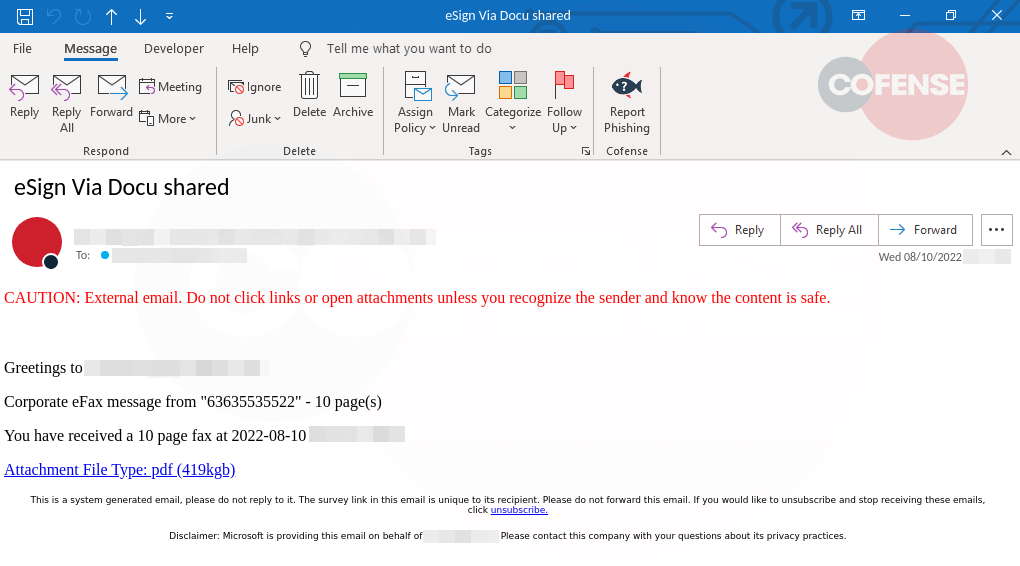 Figure 1: Phishing Email
Figure 1: Phishing Email
When the user clicks the link, they are directed to the Customer Voice survey made to look like an eFax solution page with a reasonable layout, as seen in Figure 2. The URL confirms this is a Microsoft Dynamics 365 webpage (Figure 3). In an effort to further establish the credibility of the page, the threat actor uses the words "dynamic365" and “eFaxdynamic365”.
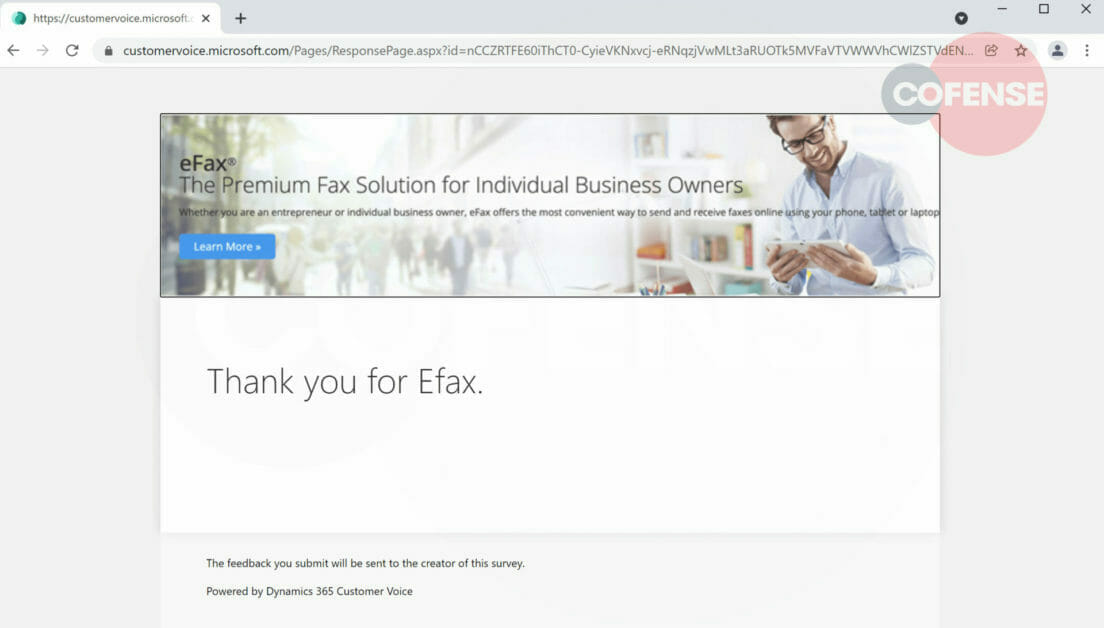 Figure 2: Phishing page
Figure 2: Phishing page
Noticeably, the threat actor embeds a video of eFax solutions for spoofed service details, instructing the user to contact “@eFaxdynamic365” with any inquiries. The “Submit” button at the bottom of the page serves as additional confirmation that the threat actor used a real Microsoft Customer Voice feedback form template and modified it with spurious eFax information to entice the recipient into clicking the link (Figure 2), leading them to a Microsoft Login page (Figure 5) which then exfiltrates their credentials to an external URL.

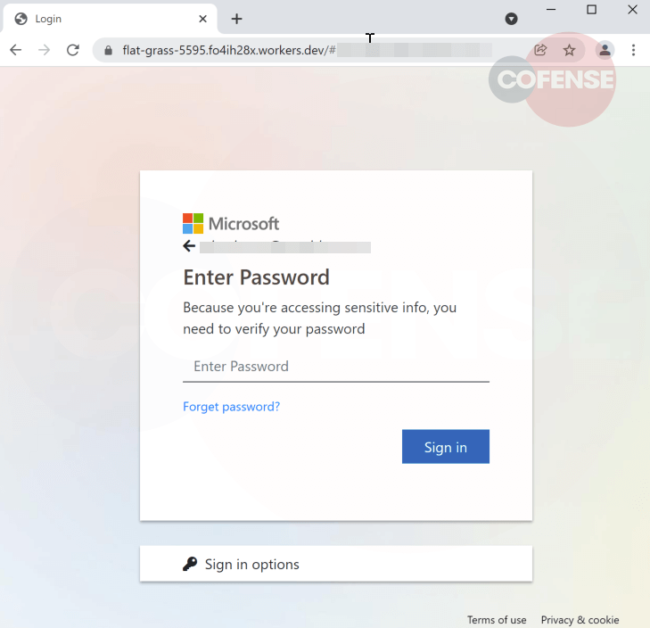
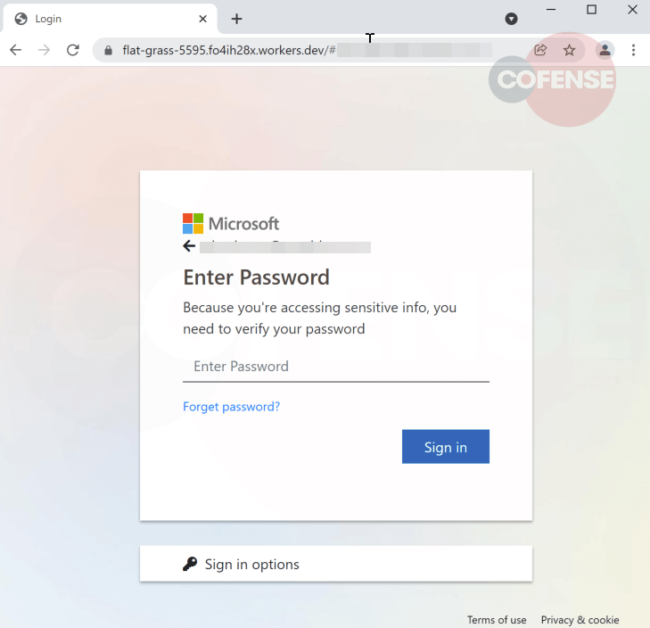
The above phishing campaign may follow a well-known pattern, sent using a compromised account, for a well-known customer feedback platform, making it difficult to block and simpler to bypass the SEGs to reach users' inboxes. By reporting these types of emails to the Cofense PDC, we can help our customers to identify new phishing email patterns and techniques.
| Indicators of Compromise | IP |
| hXXps[:]//ncv[.]microsoft[.]com/Om5CjXwiLj | 13[.]107[.]213[.]40 13[.]107[.]246[.]40 |
| hXXps[:]//flat[-]grass-5595[.]fo4ih28x[.]workers[.]dev/ | 172[.]67[.]223[.]76 104[.]21[.]86[.]177 |
| hXXps://customervoice[.]microsoft[.]com/Pages/ResponsePage.aspx?id=nCCZRTFE60iThCT 0-CyieVKNxvcj-eRNqzjVwMLt3aRUOTk5MVFaVTVWWVhCWlZSTVdENFcwUTFXRS4u&vt =4599209c-4431-48eb-9384-24f4f82ca279_f3160b43-dee8-41a8-baa7-ee24dfe7d977_637957430290000000_NAM_Hash_VhCr4kw%2bu%2b9Bs4OXTHvEBa9jcvcs 3Iiq4GIiWXPncAI%3d&lang=en-us | 13[.]107[.]246.69 13[.]107[.]246.70 13[.]107[.]227.40 13[.]107[.]219.40 13[.]107[.]213.51 13[.]107[.]213.70 13[.]107[.]246.57 13[.]107[.]246.18 |
| hXXps://jaqeuhyimhbi[.]diskstation[.]org/mintreurple/libscoreassets.php | 103[.]187[.]146.165 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.