By Adam Martin, Cofense Phishing Defense Center
The Phishing Defense Center (PDC) observes a large variety of phishing techniques and lures throughout our customer base. Some of those techniques are quite unique methods of getting the end user to interact with the message. As illustrated below in Figure 1, the recipient is advised about a suspicious login, alluding to login location issues, and is offered a solution in the form of email verification. The name of the proposed security software company “DNS Domain Name Server” is vague enough but “tech” sounding enough to convince the unsuspecting recipient that this could indeed be their native security service. 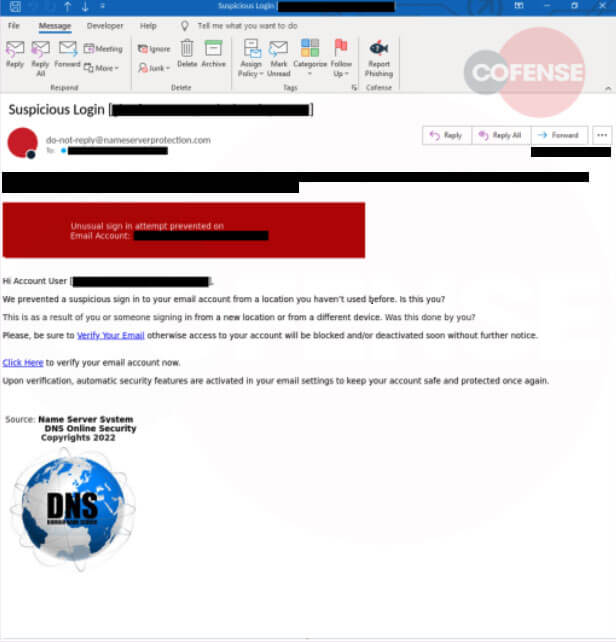
Figure 1 Initial Email
What sets this phish apart from other campaigns is the graphic displayed to the recipient once the malicious link is accessed. For the purposes of this example, fake information has been provided to the hosting server. 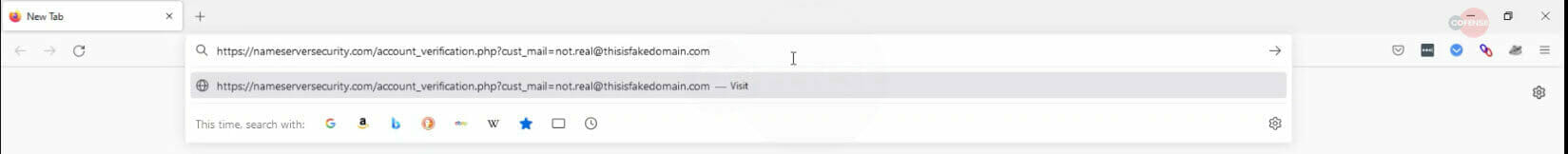
Figure 2 Example Email Address
Once accessed, the page shown in Figure 3 is displayed. The page runs in a loop with randomly generated names assigned to the domain based on the target company’s domain. Sharing some similarities with ransomware, the target company is faced with a countdown timer and the choice of stopping the deletion of potentially companywide email access or entering their credentials. The timer also shares ransomware-type panic creation all designed to push the recipient into entering their credentials without second guessing. These details aren’t deleted and a merely randomly generated as part of the scare tactic. Much the same as a ransomware “timer” for permanent file deletion should the ransom not be paid. 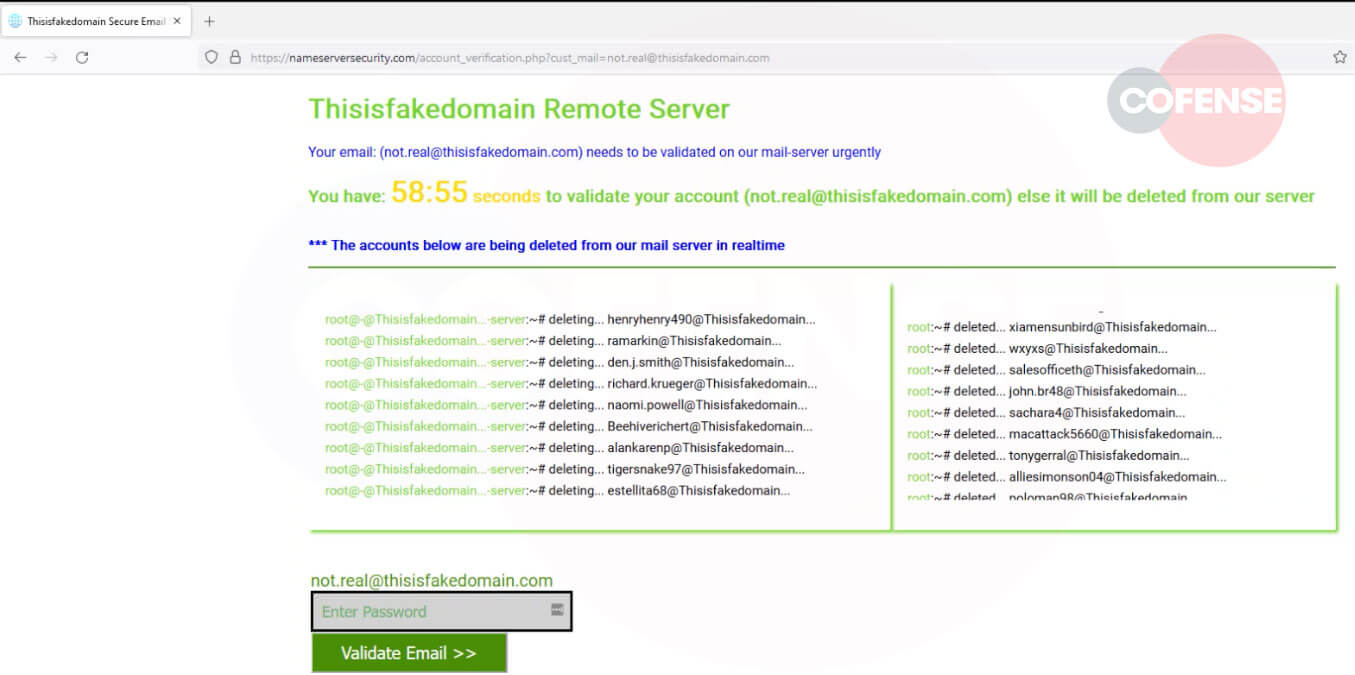
Figure 3 Ransomware style note displayed
As is the normal case with phishing incidents, once credentials have been provided by the recipient, one of two actions generally takes place. The password “input” box will return “wrong password” with the details posted to the C2 address. Alternatively, you’ll be redirected to a new page along the lines of “validating” the account, which will eventually revert to the homepage of the target organization, as seen in Figure 4. In this case, after several different variations of “validating, checking, confirming” the user was ultimately redirected back to their own company’s home page. 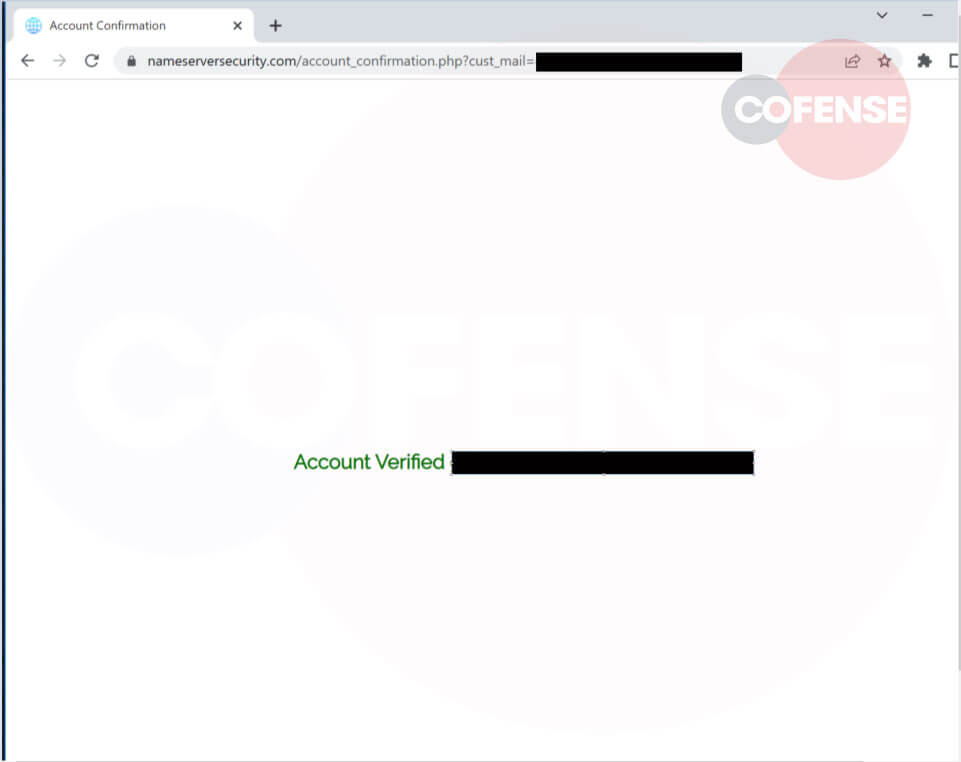
Figure 4 Validation loop
| Indicators of Compromise | IP |
| hXXp[:]//nameserversecurity[.]com/[account]_[verification.php]?cust_mail | 199[.]188[.]205[.]252 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results. The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.