By Jer O’Donovan, Cofense Phishing Defense Center
COVID-19 has become an ever-present topic in our lives since the start of 2020. With this we’ve seen threat actors leveraging the pandemic with themes related to remote working, vaccination status, and back to the office surveys or general updates. This is on top of their usual business communications such as Microsoft Teams messages, deadline reminders, internal policy updates and more. The Cofense Phishing Defense Center (PDC) has observed a phishing campaign whereby threat actors impersonate companies to send out fake COVID-19 forms. In Figure 1 we see a phish masquerading as a general office wide email claiming someone in the building has been infected with COVID-19 and asking to review the company policy. Threat actors sometimes use legitimate but compromised email addresses to send out such phishing emails. In this case, searching the sender domain led us to a real German furniture store. They’ve spoofed the display name, “Human Resources” as the sender so the recipient will assume its legitimate.
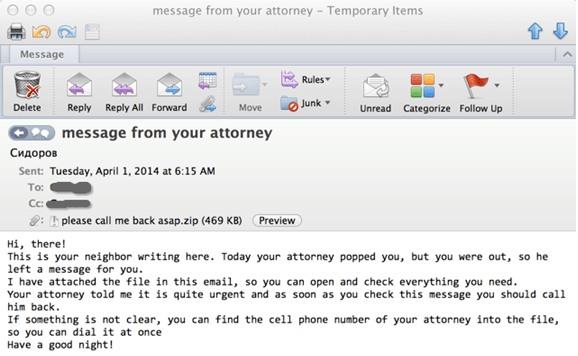
Figure 1: Initial Email
When we read the content in the email it is professionally presented. The threat actor has purposely used generic language across the mail such as “Dear Colleagues” “Human Resources” and a lack of company logos. They also used “COVID-19 Positive Case-IMPORTANT” as the subject to grab attention. All these tactics are used to convince the employee it’s a legitimate mail. This also indicates it is a mass email campaign sent to various companies as with generic language it doesn’t need to be tailored to each company. Once you click the link, you’re taken to a Typeform page that prompt’s the user for their email as seen in figure 2. Typeform is used for online form building and surveys. Threat actors use these sites a lot as they can easily setup a phishing form quickly.
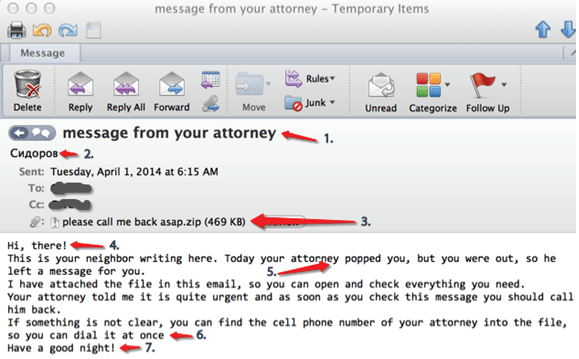
Figure 2: Initial Phishing Landing Page
Once their email address is submitted, they’re then prompted for their password as seen in figure 3. 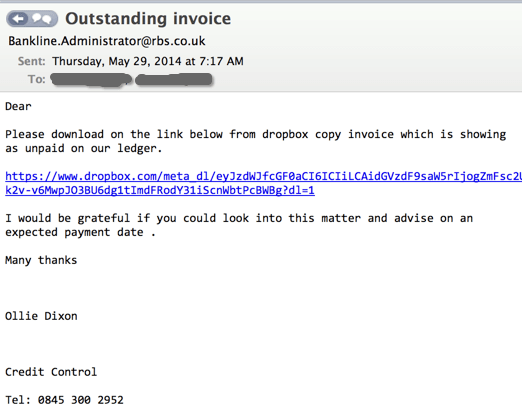
Figure 3: Password Entry Form
The PDC also observed another COVID-19 related phishing campaign from the same sender asking the user to update their vaccination status. Instead of Typeform, the threat actor used Wufoo, another online form builder to phish the user’s information as seen in figure 4. However, this has been taken down. 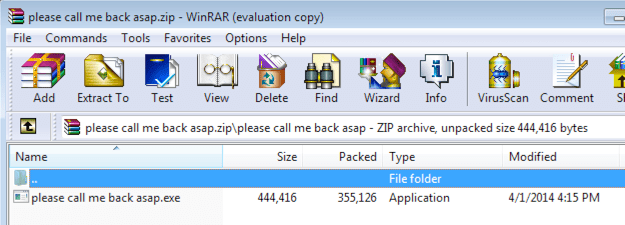
Figure 4: Second Phishing Campaign
Figure 5: Fake Covid-19 Policy
If an employee was to fall for this phish the web page would redirect seamlessly to a compromised SharePoint hosting a fake COVID-19 policy as seen in figure 5, thereby deflecting suspicion. We’ve noticed with various types of phishing attempts that threat actors will redirect to seemingly non-malicious pages after the user has entered their details, sometimes the redirect pages are legitimate sites such as Microsoft’s. For end-point teams under certain specific circumstances the blocking of a malicious sender address may be void. This would be the case with this sender address as the sender has been compromised and will need continued communication once their account has been secured.
| Indicators of Compromise (IOCs) | IP |
| hXXps://5g3poiiecwg[.]typeform[.]com/acknowledgement | 104.18.26.71 104.18.27.71 |
| hXXps://andy11[.]wufoo[.]com/forms/z1mh5ftj1a0115p/ | 18.67.65.39 18.67.65.38 |
Malicious emails like this are on the rise it’s imperative that businesses are made aware of these so that they can put a procedure in place to stop these kinds of threats. With Cofense tools and services, malicious emails can be identified, and indicators of compromise (IOC)’s given and shared. Find out what we can do for your enterprise. All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results. The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.