Author: Max Gannon, Intelligence Team
A Qantas-spoofing email campaign claiming to have various rewards bypassed multiple secure email gateways (SEGs) to deliver credential phishing pages that targeted credit cards. This campaign primarily targeted Australian employees and used convincing emails templated from Qantas’ legitimate marketing emails. The credential phishing pages were fully developed and featured convincing components, such as terms of service acceptance and multi-factor authentication.
Key Points
- This campaign mimics legitimate Qantas emails with appropriate branding and functional links.
- The credential phishing forms, while not identical to legitimate Qantas websites, are well-crafted and initially appear legitimate with no glaring mistakes.
- This campaign bypassed multiple SEGs, including Microsoft ATP, Proofpoint, and Mimecast.
- The main target of this campaign was victim credit card details, but additional harvested data could be used in follow-up attacks.
Campaign Characteristics
This email campaign started in early February 2025 and appears to have reduced in volume in mid-March 2025. The emails in this campaign convincingly spoof Qantas, copying standard marketing email templates and colors. The targets included both United States and Australian employees; however, the majority of targets were Australian, the listing of coupons and gift card amounts was in Australian dollars (AUD), and Qantas is based in Australia, indicating a target preference. The most common email, seen in Figure 1, copies the format of a standard Qantas marketing email. The emails also included a “List-Unsubscribe” header, which is typically used by mail clients to allow one-click unsubscribe from marketing emails, as required by the FTC. The threat actors seem to have added the header for an increased sense of legitimacy. However, the unsubscribe URLs used are hosted on subscriptions[.]pstmrk[.]it while modern Qantas emails use an unsubscribe link hosted on qantas[.]com. The threat actors may be using the customized unsubscribe links to track active email accounts and recipients who received the emails but simply clicked unsubscribe.
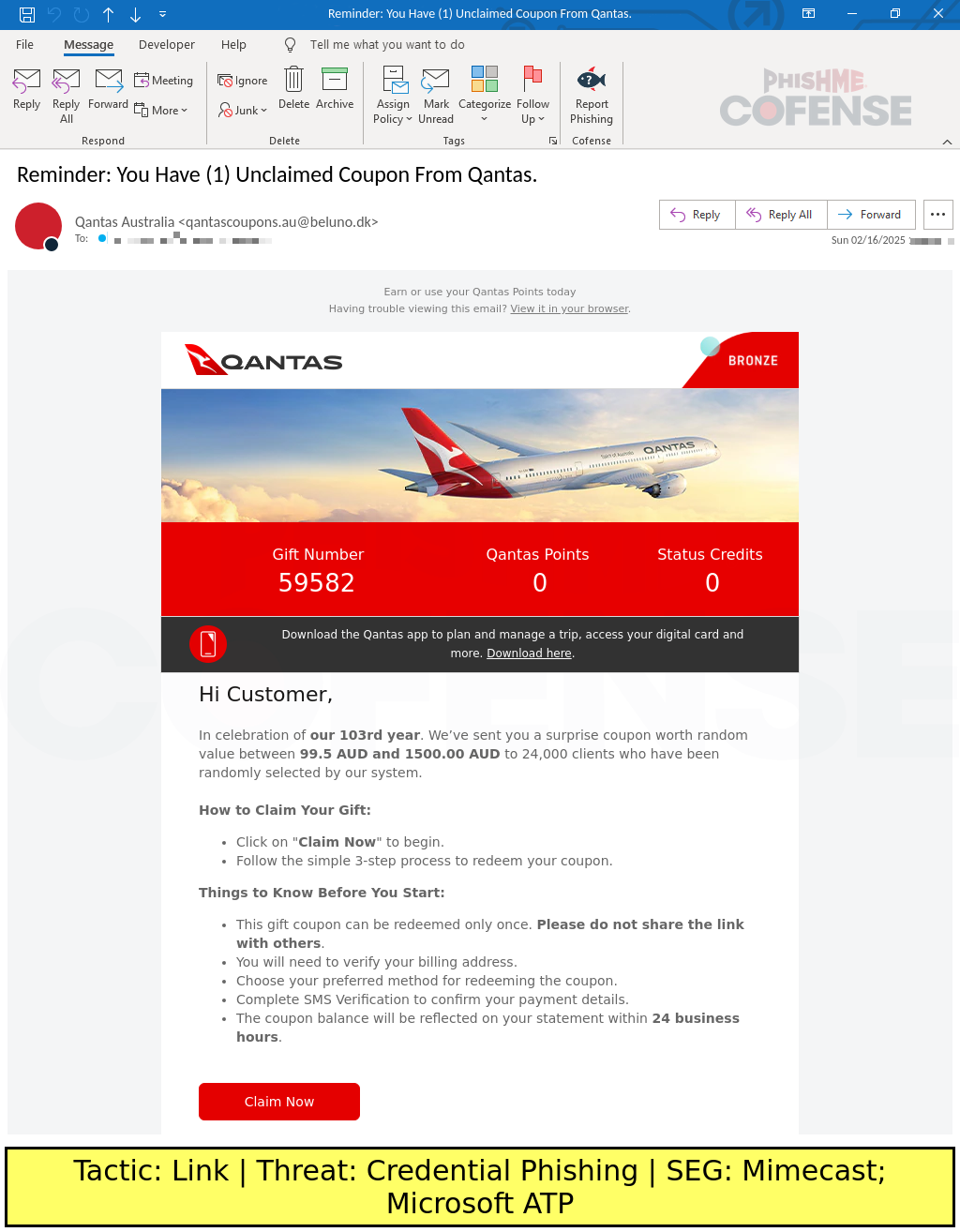
Figure 1: An excerpt of one of the most fully featured emails in this campaign.
Although less frequent, there were also simpler emails such as the one seen in Figure 2. However, even these emails were carefully designed to follow Qantas designs, and the HTML code of the email in Figure 2 reveals that the colors in the email are the exact same as Qantas branding. All emails seen in this campaign also include an unsubscribe link, further enhancing the appearance of legitimacy.

Figure 2: One of the less fully featured emails in this campaign that nonetheless is carefully adjusted to match Qantas branding.
The only area where this email campaign falls short of its impersonation of Qantas is that it states the emails are celebrating Qantas’ 103-year anniversary; however, that anniversary was in 2023.
URL Characteristics
All of the URLs embedded in the emails for this campaign use a shared “auth/auhs1” URL endpoint. The URL path before that is more randomized with references to Qantas, coupons, or other relevant terms. Moreover, each of the credential phishing sites was only available for a short time—less than 24 hours in one case.
Credential Phishing Page
Once victims visit the credential phishing page, they initiate a 7-step process. The first several steps appear to be simple confirmation steps requesting the user’s contact information, including cell phone, email address, and shipping address, as seen in Figure 3.

Figure 3: Step 3 of the credential phish, which asks for information that could be used in a follow-up attack.
Although the only security question available to answer is date of birth, all of the contact information gathered with the date of birth can be used in follow-up attacks or as part of password guessing attempts. By threat actors collecting this sensitive data, they can craft a more targeted attack, gain more trust and make the spear phishing attempt more likely to be successful. The real target of this attack is a credit card number which is requested in step 6, shown in Figure 4.
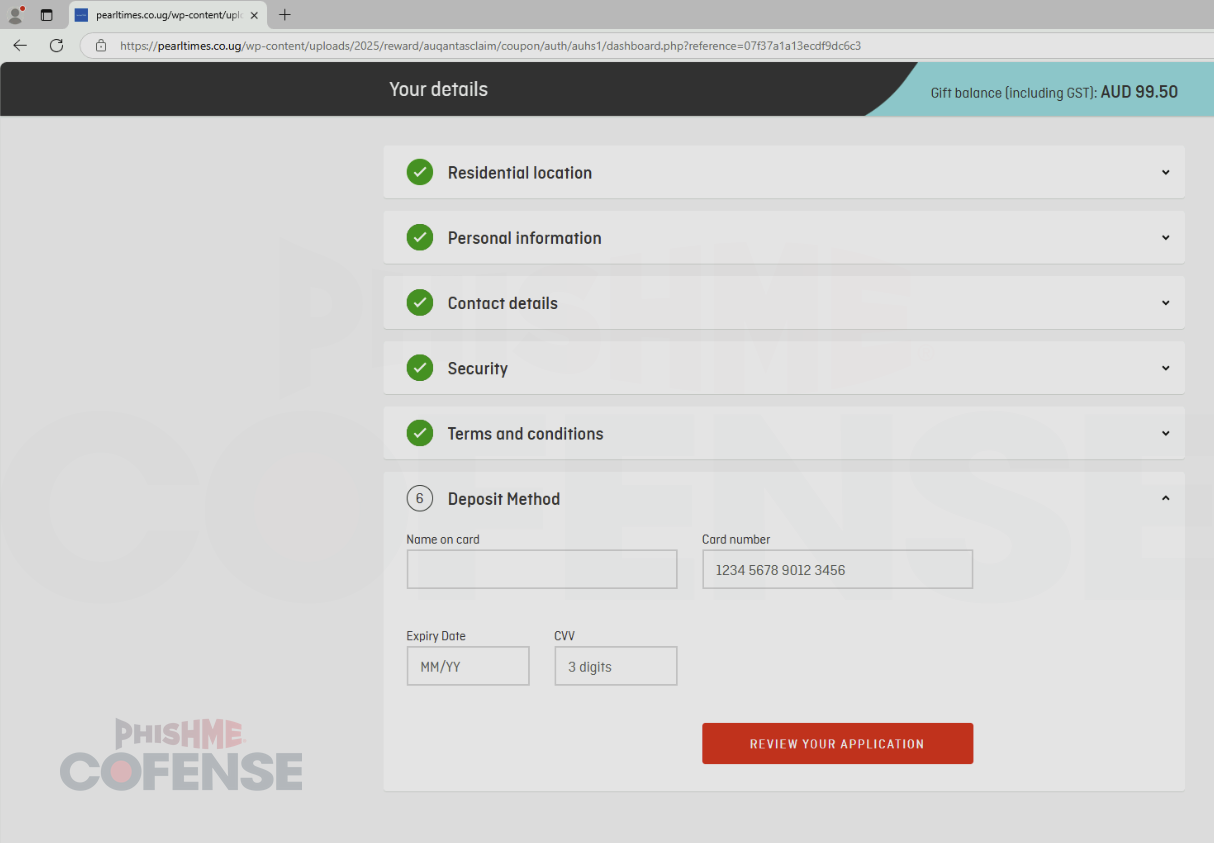
Figure 4: Step 6 in the credential phishing process is the only one that provides an immediate profit to the threat actors.
After personally identifiable information (PII), contact details, and credit card information are entered, the page claims to initiate a multi-factor authentication attempt with the phone number listed by the victim. Although the attempt does not work, it is likely intended to make victims think there is an issue on their end rather than being suspicious of the phishing page.