By: Kian Maher
The Cofense Phishing Defense Center (PDC) has observed an uptick in malicious emails attempting to take advantage of the recent uncertainty and confusion surrounding immigration services in the United States of America.
The malicious emails pose as notifications from US Customs and Border Protection. They warn users about the need to submit a new application for the Electronic System for Travel Authorization (ESTA), attempting to instill a level of panic or fear that the loss or misplacement of this documentation may hinder travel or immigration plans, exploiting the complicated process that the application can entail.
Figure 1: USA Travel Support Email
The email is well crafted and very subtle with its use of formal and concise language that is free of obvious errors to convincingly represent a legitimate government email. It goes a step further by stating the user can disregard the message if a new application has been made recently, adding a layer of legitimacy. However, the email is sent through Brevo, an email marketing distribution service that would not be used by a legitimate US government agency for sending emails.
The sender address is a convincing facsimile of the legitimate ESTA address:
@esta-cbp-gov[.]org - Illegitimate
@cbp[.]dhs[.]gov – Legitimate
Making use of known legitimate emails, it attempts to masquerade as a perfect copy of an ESTA email.
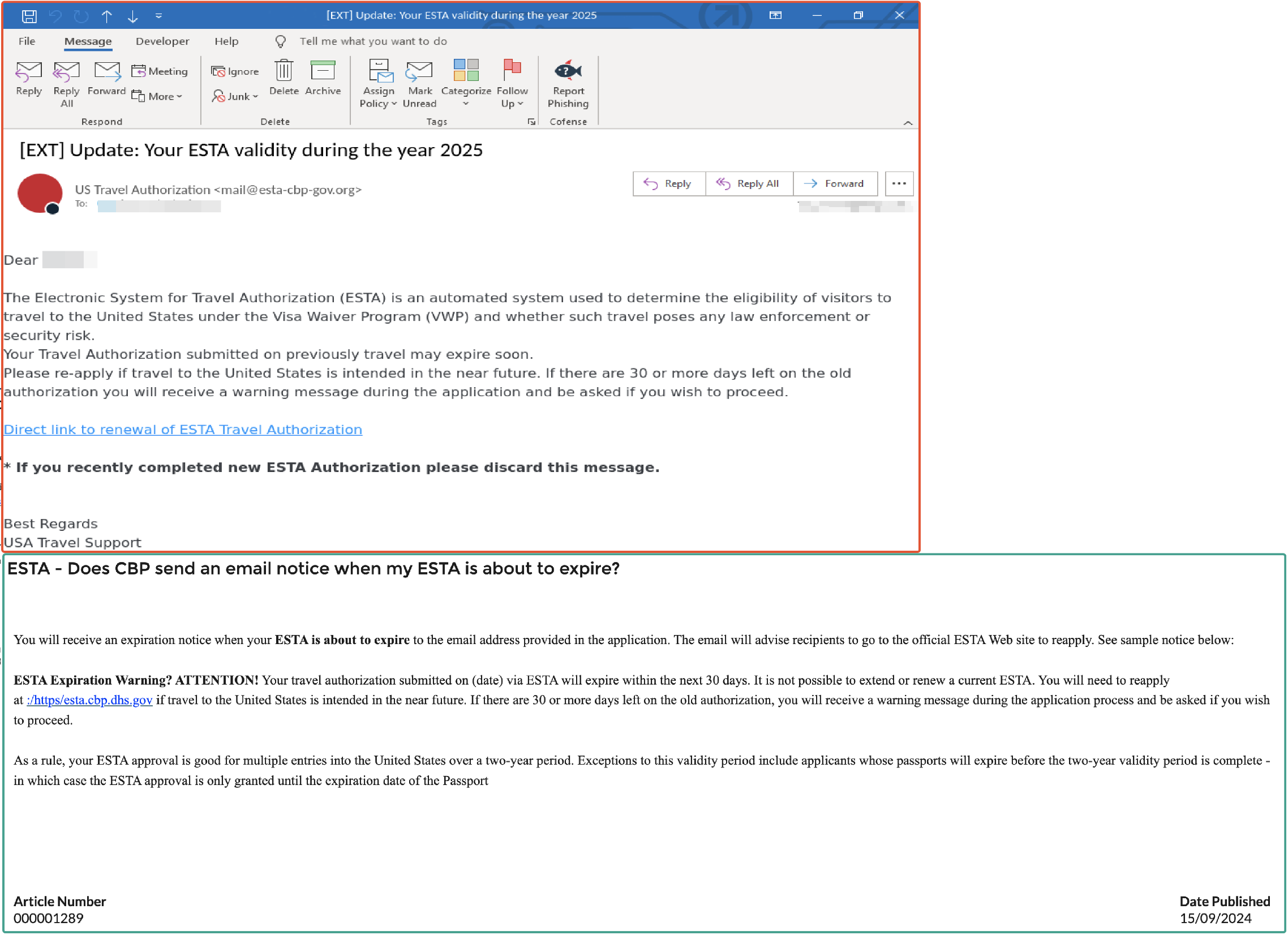
Figure 2: Legitimate ESTA Email vs Fake ESTA Email (Source https://www.help.cbp.gov/s/article/Article-1289?language=en_US#:~:text=Home-,ESTA%20%2D%20Does%20CBP%20send%20an%20email%20notice%20when%20my%20ESTA,ESTA%20Web%20site%20to%20reapply.)
After clicking the link contained within the email the user is redirected to a webpage containing a solid impersonation of the legitimate ESTA application portal. Inspecting the URL within the email shows that the Brevo marketing distribution service has been used something that would not appear within a legitimate government email:
hXXps://a40hk[.]r[.]a[.]d[.]sendibm1[.]com/
Figure 3: Fake ESTA application site.
After redirection, the URL presented is almost identical to the one used by the legitimate ESTA service:
hXXps://esta-cbp-gov[.]com/application/-Illegitimate
hXXps://esta[.]cbp[.]dhs[.]gov/-Legitimate
The similarity is close enough to mislead a user into believing they have arrived on the real ESTA application portal.
Figure 4: Legitimate ESTA Website
On the illegitimate portal, clicking on the new application link will send the user into a lengthy process that involves handing over a large amount of personally identifiable information.
Figure 5: Passport Information Gathering
Initially the user is asked to hand over passport information seen in Figure 5.
Figure 6: Personal Contact Information/ Employment Information
In addition, the user must provide information regarding their personal address, social media presence, and employment information. All the information provided to this fake service could be used to carry out malicious acts such as identity theft, blackmail, phishing attempts, business email compromises, and more.
Figure 7: Application Confirmation Screen
Once completed, the user is presented with the application finalization screen which presents some of the information input above along with a section that requests the final four digits of the user's credit card number.
Figure 8: Finalization Screen
The users are then redirected to a JCC Gateway payment portal. In this section, the user is requested to provide all credit card information to pay the fee of $88 to complete the application. This is a legitimate JCC payment system, any CC credentials input will result in the above amount being removed from the related account.
Figure 9: Payment Screen
A legitimate ESTA application should only cost $21, as seen on the actual ESTA application site.
Figure 10: Legitimate ESTA Fee
Third-party sites such as this tack on an additional fee to the process which in some cases can be 4 to 5 times more expensive than going through the legitimate portal, preying on peoples’ fears that their entry into the US may be hindered in some way, lining their own pockets with this deception. There is also no guarantee that the information will be sent to the correct authorities leaving affected users without an ESTA.
We recommend inspecting emails appearing to be from US Immigration services for unusual URLs, sender addresses, and false aliases. You should navigate to the ESTA application website independent from the email itself to check the claims being made.
US Customs and Border Protection - https://esta.cbp.dhs.gov/
With the Cofense Managed Phishing Threat Detection and Response (MPDR) solution, provided through our Phishing Defense Center (PDC), organizations gain an essential layer of protection, helping employees recognize and report suspicious emails. Our comprehensive, human-centric approach enables us to catch threats that automated systems often miss, ensuring your enterprise is protected from modern phishing and scam attacks.
| IOC | Associated IP(s) |
|---|---|
| hXXps://a40hk[.]r[.]a[.]d[.]sendibm1[.]com/mk/cl/f/sh/SMK1E8tHeFuBncRiLhXHFKsvruJJ/4Hh7ZuCCe-HU |
|
| hXXps://esta-cbp-gov[.]com/application/ | 138.68.89.147 |
| hXXps://fs6[.]formsite[.]com/ESTAdansk/kqk9cbcu9a/index[.]html |
|