By Alex Geoghagan, Cofense Phishing Defense Center
Impersonating a government entity is a relatively common practice for threat actors to attempt. Through this impersonation a threat actor seeks to gain trust or authority in an interaction with a potential victim. Recently, the Cofense Phishing Defense Center (PDC) has analyzed a phishing campaign that impersonates the United States Department of Labor. In this specific campaign, the threat actor also tries to push a financial incentive with the lure of an “INVITATION FOR BID” through the Department of Labor.

Figure 1: Email Body
Seen in Figure 1, the threat actor was able to spoof the dol.gov from address to increase the level of authenticity. Seen in the body, the email itself is structured to look like an RFP for “ongoing government projects.” The recipient is prompted to open a PDF attachment for information and directions for the bid invitation. A recipient who opens the attachment without realizing that this is not a legitimate government communication will be presented with a PDF document that contains a link to the phishing website.

Figure 2: PDF Attachment
The PDF, shown in Figure 2, is carefully crafted to lend credence to the scam, as well as to apply pressure with time sensitivity by reminding them of a “10:00 A.M.” deadline. It contains a list of instructions for filling out information that will allegedly be used to apply for the bid, however, this is simply done to make the phish appear to be more legitimate. The “BID” button contained within the PDF is the true goal of the threat actor, as clicking on it will direct the recipient to a fraudulent Department of Labor site.
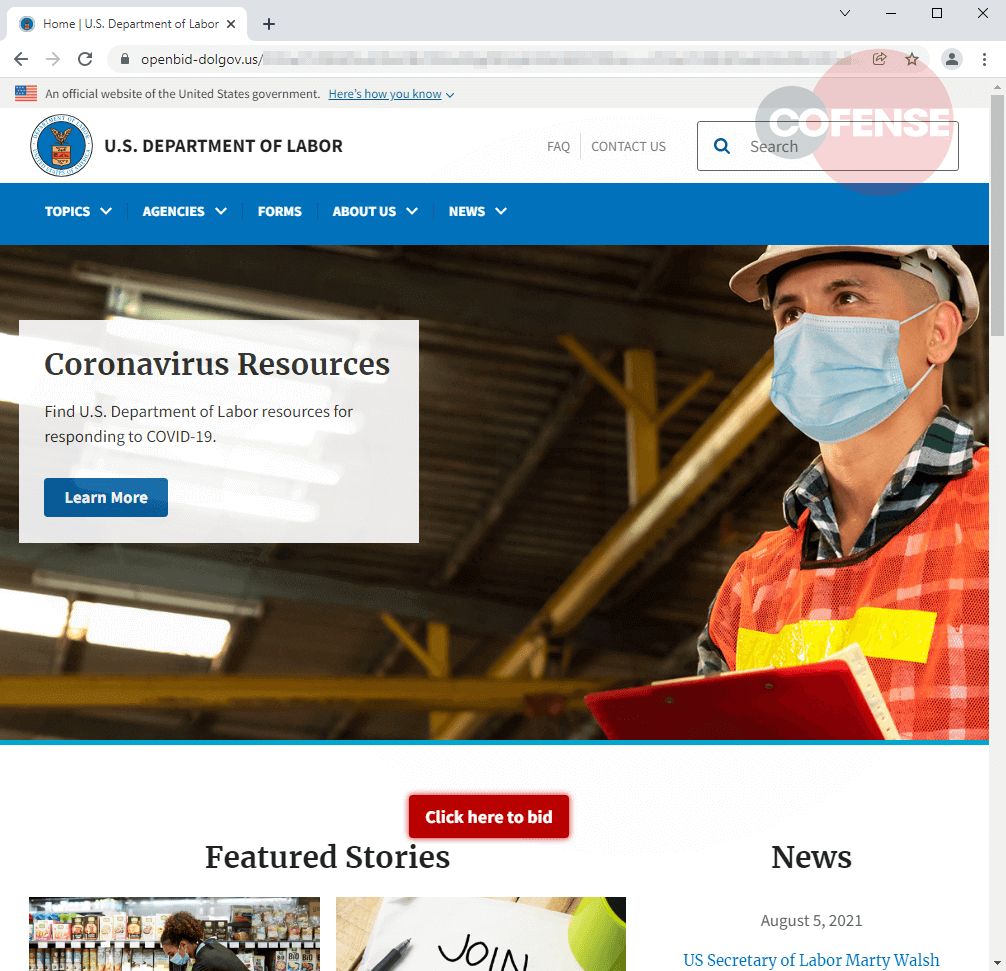
Figure 3: Phishing Page
The fraudulent page, Figure 3, is almost a 1:1 of the legitimate Department of Labor’website at dol.gov. Even with the domain, openbid-dolgov[.]us, the threat actor crafted it to be believable to the untrained eye. Upon reaching this page there will be a small popup that reiterates the instructions that are contained in the PDF. This page also contains a “Click here to bid” button that takes the recipient to the phishing page requesting their credentials, as seen in Figure 4.
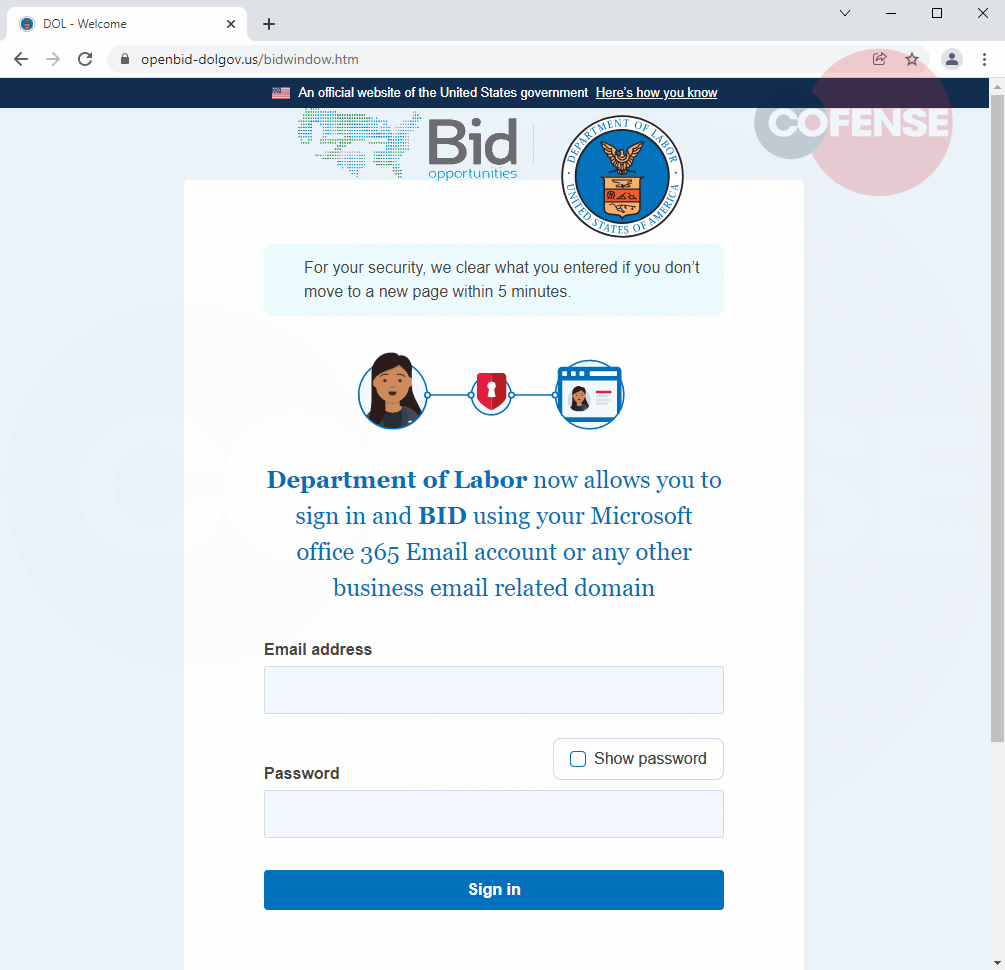
Figure 4: Phishing Page
Oddly enough, the threat actor has specifically asked for either their Microsoft Office 365 credentials OR their business email credentials (widening the net to collect anything the user might be willing to divulge). Once the credentials are submitted, the user is redirected to practically the exact same page, but it is asking the user to solve a captcha instead of signing in. An interesting note added to the page is reassuring the recipient their data will be cleared within five minutes, most likely mimicking the legitimate bidding site. A communication appearing to come from a government source may also be seen as more official, especially if the attacker is able to spoof a .gov email address. With how carefully crafted it is, this phish can pose a threat to any email environment, even ones protected by a secure email gateway (SEG). With the help of watchful users reporting suspicious email, analysts at the PDC can quickly identify threats like this one, and enterprises can benefit from our entire view of the threat.
| Indicators of Compromise | IP |
| hXXps://openbid-dolgov[.]us | 199.231.162.106 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.