By: Tej Tulachan, Cofense Phishing Defense Center
The Cofense Phishing Defense Center (PDC) recently uncovered another dose of credential phishing attacks on consumers, whereby threat actors lure their victims with known social engineering tactics. Thanks to the widespread use of Microsoft Single Sign On (SSO), such as OAuth2, threat actors can use this to their advantage as a powerful means of harvesting credentials to compromise important services.
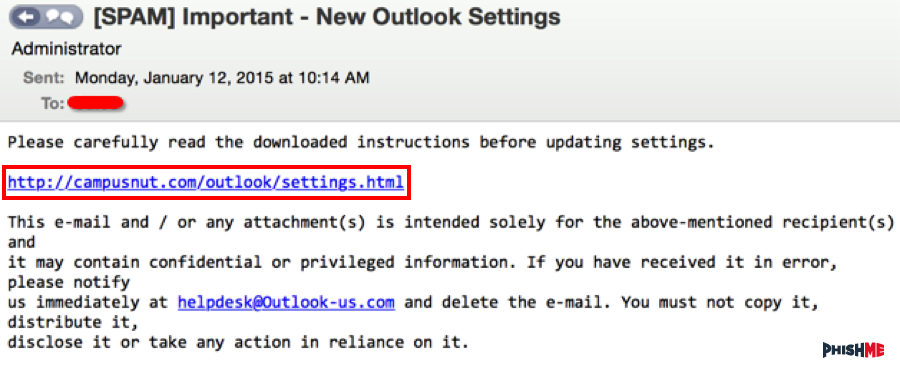
Figure 1: Email Body
The “From” address in Figure 2 uses a well-known fragrance company’s spoofed domain with an IP address of 40[.]107[.]220[.]139. Most likely for this reason, the email slipped past basic authentication checks, such as the sender policy framework (SPF). However, on further inspection, we see what is likely the actual sender’s address “Return-Path” from a compromised domain registered to a U.S. law firm, with an IP address of 10[.]217[.]135[.]43. Attributes such as email address can be unreliable as indicators of compromise (IOCs) when creating Yara rules. Why? Because they are often quickly changed and have very brief time-to-live (TTL) periods. Strong IOCs identify repetitions and meaningful patterns, resulting in higher quality Yara rules and a lengthier period for tagging threats. 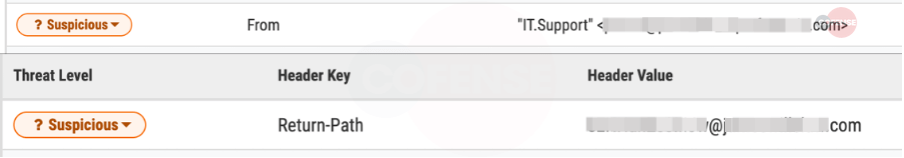
Figure 2: Header Analysis
Figure 1 shows the email body, which was found in environments protected by several secure email gateways (SEGs). We noted that the spoofed sender’s address remained static across the campaign, allowing for a high degree of signature-based detection efficacy. A bonus for defenders, this static sender address can be blocked by the endpoint detection team or even the SEG. Threat actors sometimes use legitimate but compromised domain names to send out such phishing emails. Pivoting the domain led us to a legitimate law firm based in the United States that was registered in February 2015. The longer a domain has been registered, the greater the chance the domain will be recognized as non-malicious. This may be a preferable approach for the adversary versus registering a new domain for the purpose of sending out credential phishing emails. That is not to say that the characteristic of being newly registered makes a malicious domain easily identifiable. Instead, it’s a combination of suspicious attributes that raises red flags.
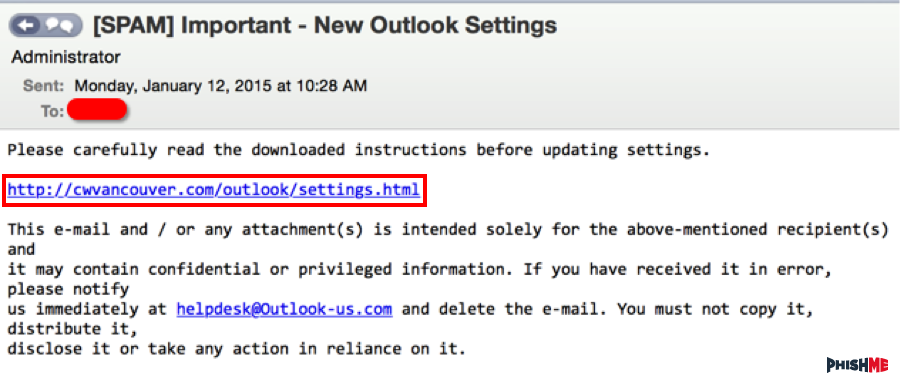
Figure 3: Phishing Landing Page
The image in Figure 3 is what the recipient would see. It looks perfectly legitimate with all functionalities a legitimate Microsoft login page would have. At this stage, we have high confidence to state that the threat actor’s objective was to gain as many users’ credentials as possible at a given period of time. Should the recipient provide their credentials, the web page would redirect seamlessly to the legitimate Microsoft login page, thereby deflecting suspicion.
How Cofense Can Help
Every day, the Cofense PDC analyzes phishing emails with credential phishing attacks and malware payloads that bypassed email gateways and were reported by well-conditioned users. Of the threats found, 100 percent were identified by the end user and mitigated by a human analyst. None were stopped by the endpoint detection technology. Thanks to phishing training, users have the know-how to look out for evolving phishing attacks. Using Cofense Reporter, they can forward threats to the Cofense PDC for analysis. Cofense Triage reduces real-time exposure to threats, and combines with Cofense Vision to quarantine them. Cofense Intelligence then protects your organization against emerging threats. Cofense Intelligence customers received additional information about this specific campaign in Active Threat Report (ATR) 222896.
Indicators of Compromise
| IOC | IP |
| hXXps://ww3sXUcRltmd[.]asesiklimlendirme[.]com[.]tr/ | 83[.]150[.]212[.]44 |
| hXXps://production[.]passwordupdate00- | 109[.]169[.]71[.]112 |
| microsoftpasswordupdate00-odragrant-tooth- | 104[.]21[.]75[.]60 |
| 3351[.]lllibby-webb6868[.]workers[.]dev | 172[.]67[.]214[.]249 |
| hXXps://smtpjs[.]com/v3/smtpjs.aspx |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.