Found in Environments Protected By: Microsoft, Fortimail
By Kurtis Nicks, Cofense Phishing Defense Center
Phishing attacks continue to evolve, with threat actors becoming increasingly clever in their attempts to deceive their targets. The Cofense Phishing Defense Center (PDC) has recently observed a sophisticated phishing campaign targeting EPOS Net customers, a large Japanese credit card company. The campaign is notable for its meticulously crafted emails and cloned website, as well as its use of official customer service numbers to establish an illusion of legitimacy.
In the past, we have observed similar schemes employing social engineering techniques and exploiting popular platforms to establish trust. This particular phishing campaign stands out for the lengths to which the attackers have gone to create a sense of urgency and authenticity.
Figure 1: Email Body
The phishing email begins by thanking the receiver for their continued patronage of EPOS cards and mentions that EPOS Net monitors card usage to prevent unauthorized use. This seemingly benign introduction helps establish an air of legitimacy. The email then takes a more urgent tone, claiming that the receiver's credit card might have been used fraudulently and urging them to check the details via a provided link.
The threat actors have gone to great lengths to make the email appear legitimate. They have spoofed the "from" address to resemble an official EPOS Net email, and the layout of the email mimics that of a genuine communication from the company. The email's intention is to create a sense of urgency and fear, motivating the victim to click the link and provide their sensitive information.
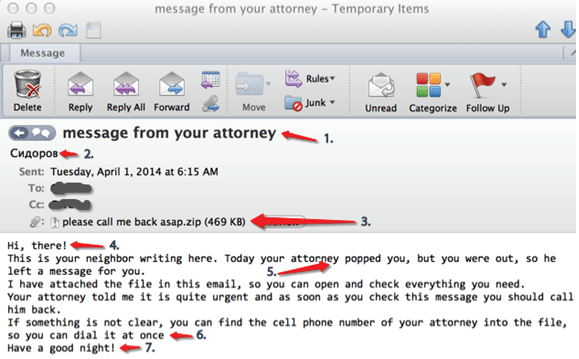
Figure 2: Phishing Page
Upon clicking the link provided in the email, recipients are directed to an exact replica of the official EPOS Net website. The threat actor has cloned the website to capture banking information from users. The phishing site requests the user's username and password and then leads them to a second page that asks for their EPOS card details, including the card number, date of expiry, security code, and the telephone number used when applying for the card.
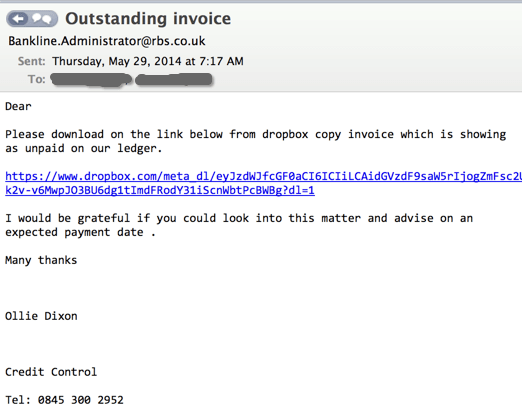
Figure 3: Phishing Page (Post login)
The attackers cleverly establish trust by including the official EPOS customer centre numbers at the bottom of the page. While some phishing schemes use fake numbers and call centres to assist in the deception, this campaign employs the actual customer service numbers. If victims were to call these numbers, they would quickly realize the scam.
Figure 4: One-time Password page
The threat actor continues to build on this false sense of security by asking for a one-time password after the recipient enters their credit card information. Threat actors have the potential to utilize a script, which can attempt to log in using the information provided, prompting EPOS to send a legitimate SMS code to the victim's mobile phone. Once the one-time password is entered on the phishing site, the victim is redirected to the official EPOS login page, further reinforcing the illusion of legitimacy.
In conclusion, this phishing campaign highlights the evolving tactics of threat actors and the importance of remaining vigilant when dealing with emails requesting sensitive information. Always verify the authenticity of emails and websites, and never provide personal or financial information without being certain of the recipient's legitimacy. This campaign illustrates how automated systems - such as those identified at the top of this article - fail to outperform humans, and the network effect of people as sensors, spotting and reporting suspicious email With Cofense Managed Phishing and Defense, provided through our Phishing Defense Center (PDC), enterprises benefit from our complete view of real phishing threats.
| Indicators of Compromise | IP |
|---|---|
| hXXps://eposcp-net[.]3utilities[.]com | 216.144.226.73 |
| hXXp://ww16[.]eipos[.]caneo[.]info/ | 64.190.63.136 |

*Figure 1 English Translation