By Schyler Gallant, Cofense Phishing Defense Center
Our analysts in the Cofense Phishing Defense Center (PDC) review thousands of phishing emails, all varying in degree of complexity. Recently, PDC analysts observed a simple Microsoft phish that was reported by several clients. One of these clients had Cofense Vision, which provided insight into how many emails from this campaign appeared in their email environment. Even with a Secure Email Gateway (SEG), there were over 130 emails from this phishing campaign. A vast majority of the emails were not reported to the PDC, however, with the power of Vision’s quarantine function, analysts were able to prevent these from being a potential threat to users.
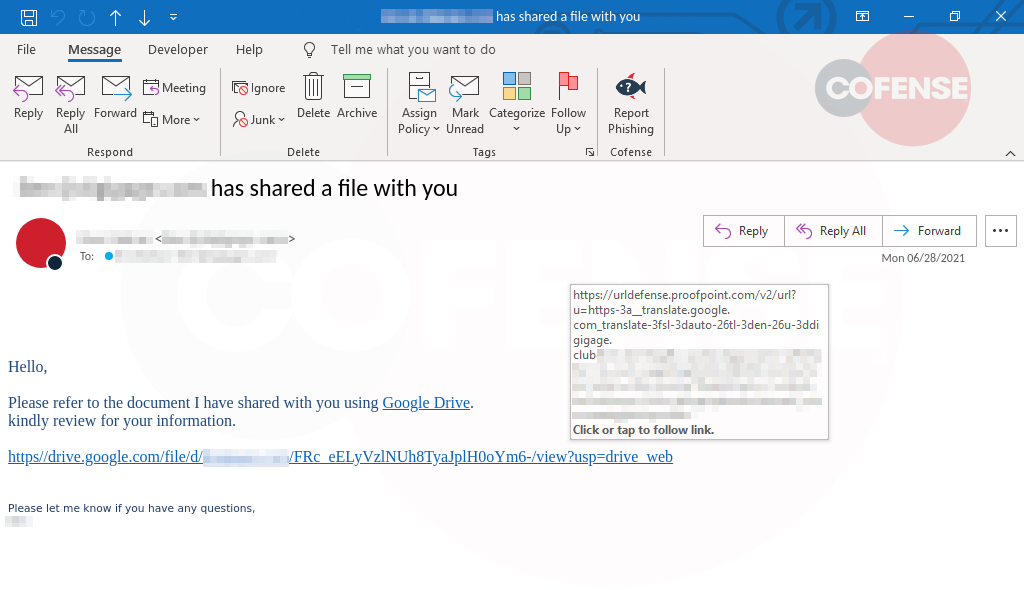
Figure 1: Email Body
The email appears with the subject, “Mail delivery failed: return message to sender,” seen in Figure 1. This alert is a common message someone would receive when their messages are kicked back because the person who they emailed has a full inbox or that email address does not exist. The first indicator of this phish is the email sender is genelle[@]sjvma[.]org while representing itself as Microsoft.
In Figure 1, the email body appears with a Microsoft logo, giving the user extremely specific information on when three messages became undeliverable. This is to convey to the user that these emails will need to be reviewed and released for them to come into their inbox. This is a common tactic for threat actors to leverage legitimate alerts common to Microsoft users. Once ’allow messages or ‘review messages’ is clicked, the user is directed to hxxp[:]//youdeh[.]co[.]za.
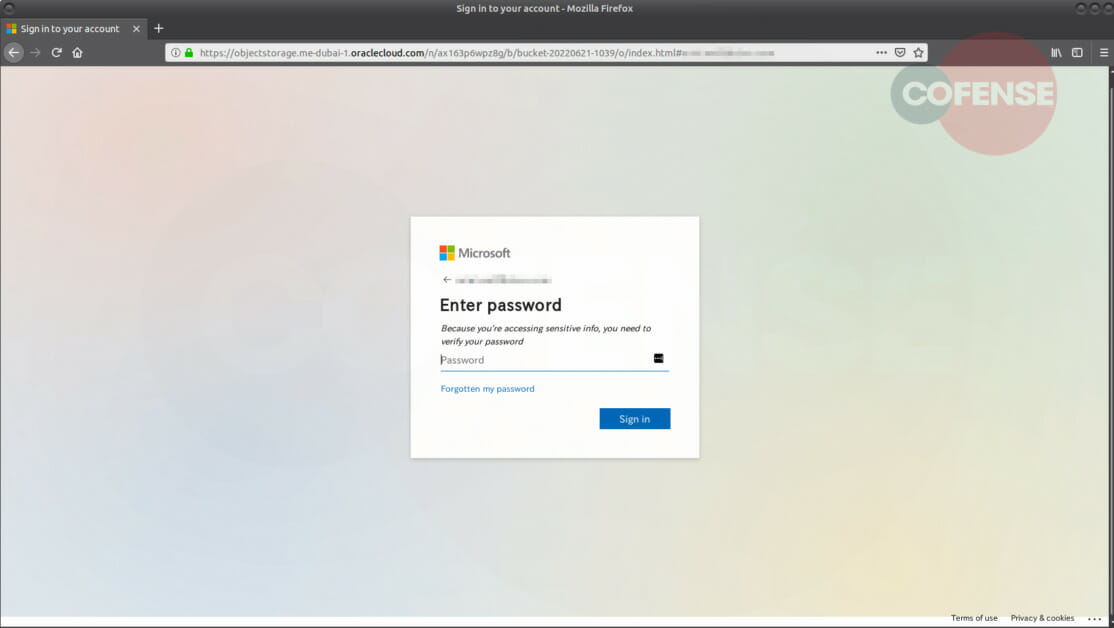
Figure 2: Phishing Page.
When the user clicks this link, they are redirected to a landing page that appears as the Microsoft login in Figure 2. While this appears as the actual Microsoft login page, looking at the address will show that the URL is actually hxxps[:]//objectstorage[.]me-dubai-1[.]oraclecloud[.]com/n/ax163p6wpz8g/b/bucket-20220621-1039/o/index[.]html. It’s common for Microsoft phish to have a page that closely resembles the real one. If the user did enter their credentials, they be redirected back to the Microsoft office page.
Even with common tactics used in this campaign, Cofense was able to quarantine and protect the client in an environment despite the presence of a Secure Email Gateway (SEG). That’s why Cofense is in a unique position behind SEGs. Vision paired with the PDC can protect against a campaign with numbers like this from causing a potential incident or data breach.
| Indicators of Compromise | IP |
| hXXp[:]//youdeh[.]co[.]za | 99[.]198[.]101[.]186 |