By Matthew Dortch, Cofense Phishing Defense Center
Commonly used, yet still effective tactics, are being exploited by threat actors to get phish into user’s email inboxes. The Cofense Phishing Defense Center (PDC) has observed a phishing campaign targeting energy/infrastructure companies by utilizing HTML attachments containing credential stealing forms. This is another example of how Cofense observes phishing campaigns across various customers and industries.
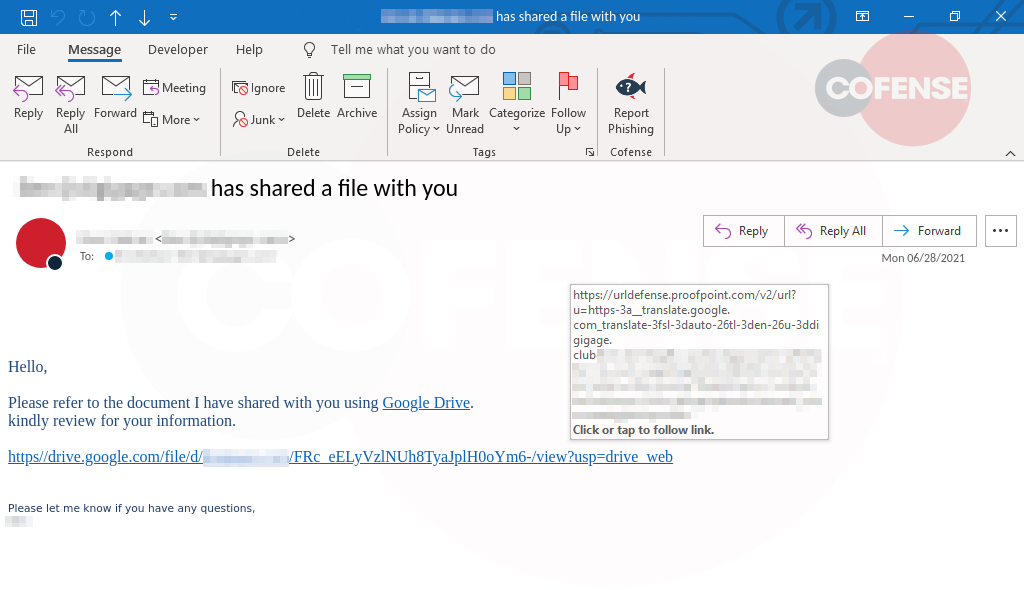 Figure 1: Email Body
Figure 1: Email Body
The email shown in Figure 1, poses as a notification of a legitimately received file presented as a transcript. The threat actor leveraged a simple transcript alert theme. Specific details added in the email such as the date and time the attachment was received may boost the authenticity of the phish. To portray as being from an internal source, the threat actor spoofed the organization by using “Shared-Files via ”, however, the email address, with a Japanese domain, is still clearly displayed.
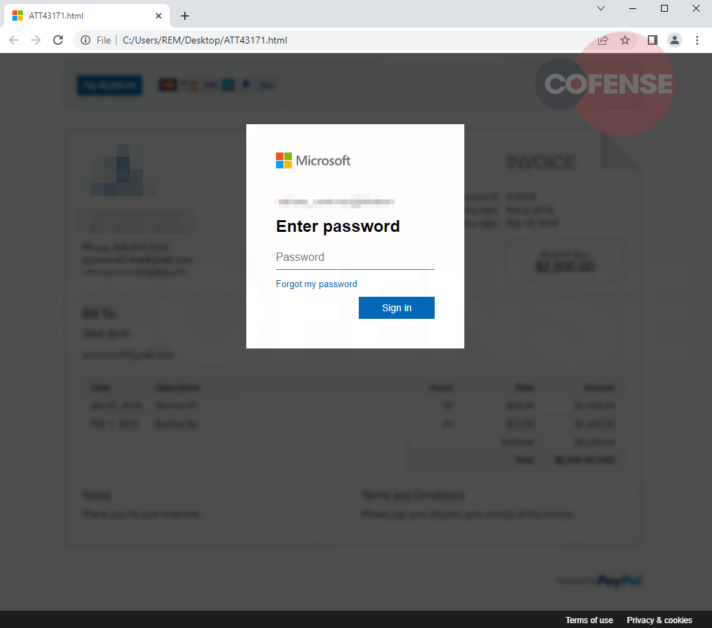
After downloading and opening the HTML file, users are shown a Microsoft login form with some type of document masqueraded behind, shown in Figure 2. The document behind appears to be an invoice with financial information on it that can only be accessed by logging in with a Microsoft account. This tactic alone was most likely an indicator to the recipient that the email content didn’t align with what was being presented on the landing page, leading them to quickly report the suspicious email. The recipient’s email address is automatically displayed with just the password field empty, as the threat actor scripted the HTML file to have to pass the recipient’s email address.
Since one of these customers hit by this campaign leverages Cofense Vision to automatically quarantine emails, the customer was able to mitigate the email from 40 unique inboxes, reducing the risk of user interaction to give away credentials.
Cofense continues to observe HTML / HTM attachments as the top attachment type making it to the inbox, leading to credential theft. Cofense Vision sits post SEGs and offers an effective and unique phishing defense by using a network of people reporting suspicious emails that allows one email to be used to mitigate an attack across an entire organization. Reach out to learn more.
| Indicators of Compromise | IP |
| hXXps://warrenlawomaha[.]com/scn/hope.php | 103.125.218.44 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.