Found in Environments Protected By: Microsoft
By: Justin Rudd, Cofense Phishing Defense Center
In recent weeks, the Cofense Phish Defense Center (PDC) observed an evolution of a commonly seen scam tactic known as “sextortion” scams. These scams are prevalent across different sectors and industries and are difficult to stop due to the general lack of malicious URLs or attachments within the email, randomized sending addresses, and each scam being tailored to the target in question. These factors make it difficult for traditional security suites to detect and neutralize the threat.
Figure 1: Email Body
Though blurred in Figure1, the threat actor lists the target’s supposed address and phone number in the email body to grab the target’s initial attention. While the usual sextortion scam email will originate from random or spoofed email addresses, the trend with this version is that the emails originate from Gmail accounts that appear randomly chosen. Previous scam emails are also simpler in that everything is contained within the email body and rarely come with URLs or attachments. In the case of these email bodies, they only contain unique individual information: the name, address, and contact information of the potential target.
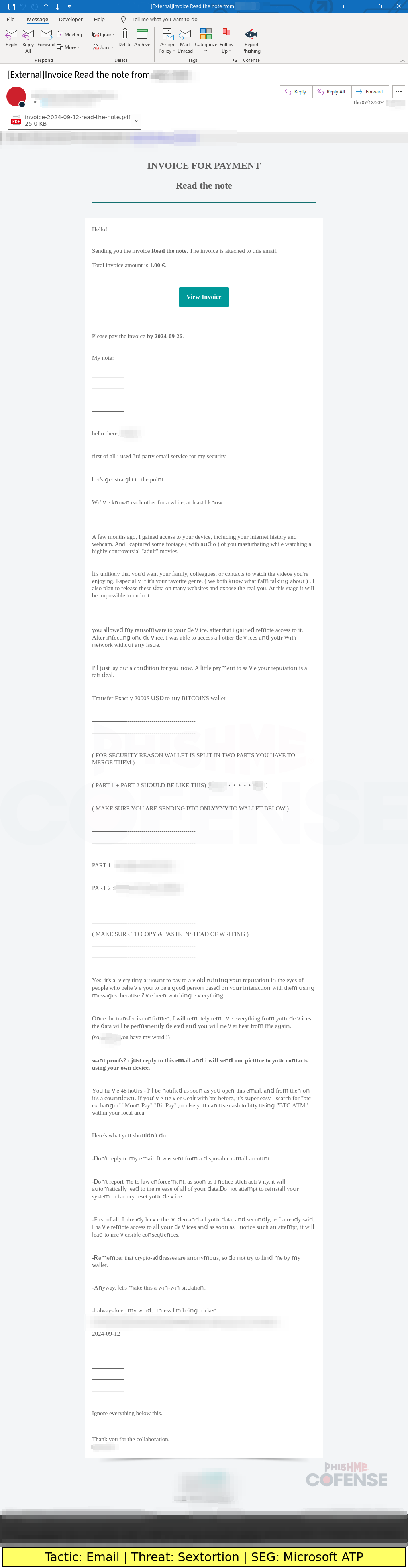
Figure 2: Attached PDF File
Attached to these emails are PDF documents containing the language expected from sextortion emails with the twist of including an image of the target’s supposed home or place of work. The images used are not always of their residence; instead, they might just be pictures of the street or the environment around it. This suggests that they are likely auto-generating the images they are using in the email instead of grabbing them manually. The document starts by addressing the target by their first and last name along with their street address and an image of the address. The threat actor has likely made use of mapping services such as Google Street View to obtain an image of the target’s residency or place of work and threatens to visit them if they don’t respond to the email.
The threat actor will assert that they compromised the target’s system using “Pegasus” spyware and will use additional technical verbiage to prey on the target’s potential lack of knowledge. They will claim that they’ve been watching the target for an extended period, amassing a large amount of information. To bolster their credibility, the threat actor will use casual language and slang, expressing confidence while suggesting they have recorded the target, even complementing their surroundings.
The threat actor presents two options to the target. The first is to ignore the email, which would result in the sender threatening to release the supposed videos to the target’s contacts. In the second choice, the threat actor claims that they will delete the videos and disappear if the target pays them a certain amount in the cryptocurrency “Bitcoin”. They will then list their bitcoin wallet address, along with the requested amount, and include a QR code containing the same listed bitcoin address.
The way this has evolved from previously observed scams of this type comes in the form of consistently using random Gmail addresses and the inclusion of the target’s residency or place of work as well as potential photos of it. While previous versions of sextortion scams would sometimes make use of spoofed email addresses as an intimidation tactic, it seems that threat actors are beginning to shift their focus towards the more direct and more easily intimidating approach of threatening the target in a much more personal way.
In the same period Cofense has also observed a secondary, smaller, deviation from your typical sextortion campaigns: invoicing services. In the figure below we see a threat actor using Deepfin, a Lithuanian free-to-use invoice generation platform tailored to those who are self-employed. Threat actors will utilize services such as these to assist in bypassing security measures as in most cases the invoicing service will send the email on behalf of the threat actor. This ensures that most of the information that would normally be visible to any security is in some way covered by the service's own header information or email content.
While the use of invoicing services is helpful in getting the email to a user's inbox, the content within is still very much the usual sextortion language where the threat actor claims to have compromised a user's computer and will accept cryptocurrency payments in exchange for not leaking content to said user's contacts. As an added layer of security circumvention, these threat actors have opted to split the wallet address included in two. Since cryptocurrency wallet addresses are a consistent addition to these types of scams, splitting the address helps to avoid any detection methods in place that recognize those signatures.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of endpoint protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.