By: Don Santos, Cofense Phishing Defense Center
When it comes to personal and professional growth, online learning platforms have become a popular resource. Companies like Coursera and Udemy offer courses on a wide range of topics, which can be consumed at a time and pace that suits the user, and provide a recognized certificate upon completion. With the increasing popularity and credibility of online learning platforms, threat actors are exploiting this trend to lure victims into a deceptive phishing campaign.
The Cofense Phishing Defense Center (PDC) recently discovered a phishing campaign that tricks victims using an online course invitation. While most phishing attempts involve direct requests for your login credentials, this example provides a unique and clever method in which it spoofs the Coursera online platform first, but ultimately directs victims to a fake Meta login page.
.png)
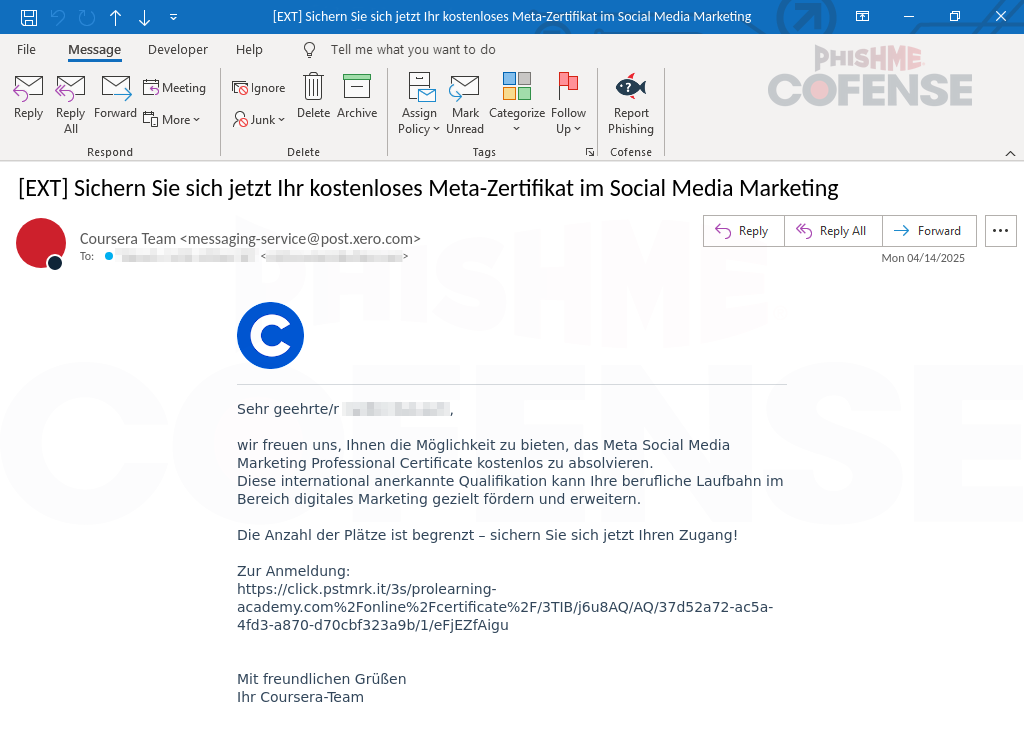
Figure 1: Email Body
The campaign starts with the message illustrated in Figure 1. The intended victim is greeted with an email coming from “Coursera Team” with a subject that translates to “Get your free Meta Certificate in Social Media Marketing now.” This initial lure is likely to have a high efficacy percentage, as most online learning platforms send out email invitations and updates about new courses to their registered users. However, the sender address, <messaging-service[@]post[.]xero[.].com>, is the first red flag as it doesn't match the official domain used by the company. Since online course prices can vary, offering a “FREE” course enrollment is a tactic the attacker can use to attract the attention of their intended target.
The email body translates to “We are pleased to offer you the opportunity to complete the Meta Social Media Marketing Professional Certificate free of charge. This internationally recognized qualification can specifically advance and expand your professional career in digital marketing. Places are limited – secure your access now!” Statements like “free of charge” and “internationally recognized qualification” make the offer sound exciting and rewarding to users. By suggesting that slots for this course are limited, it creates a sense of urgency, prompting victims to act quickly. A link is then provided to enroll in the course.
.png)
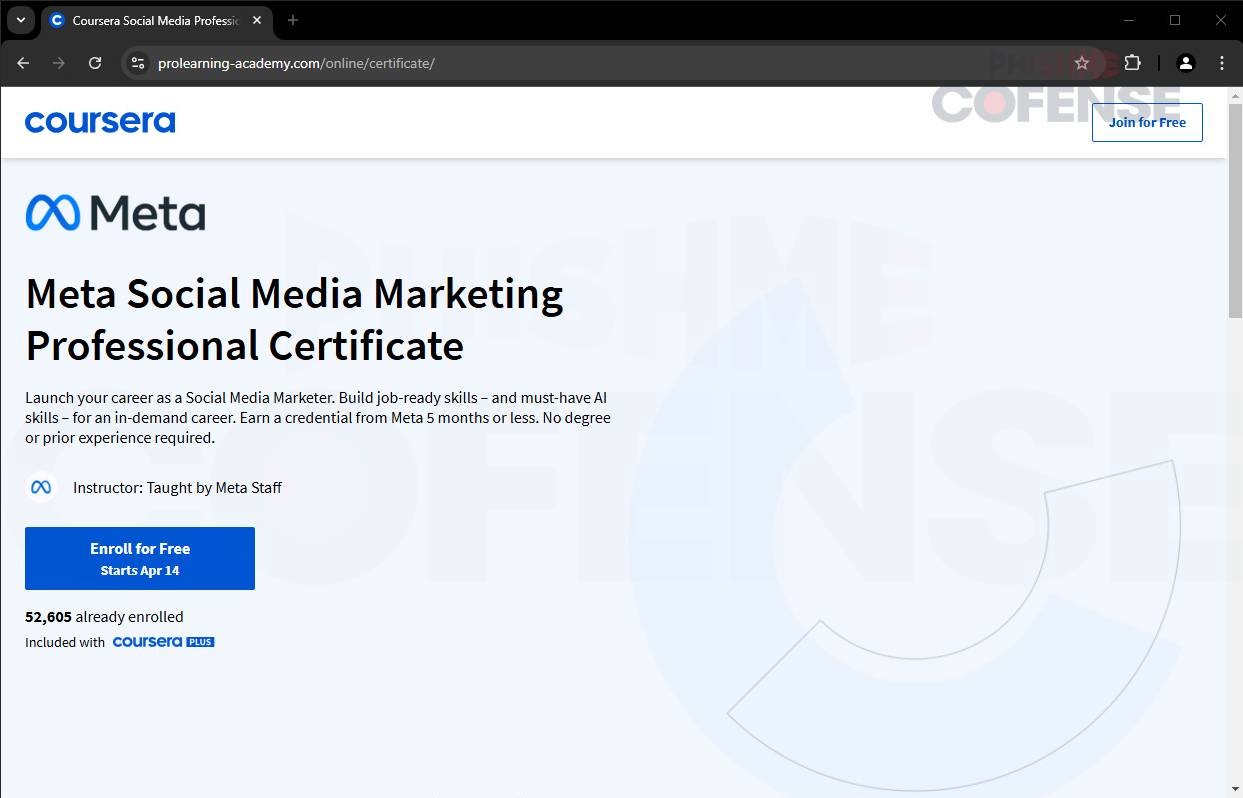
Figure 2: Enrollment Page
When the victim clicks on the link in the email, they are redirected to the course enrollment site, as portrayed in Figure 2. This landing page is almost a mirror image of the legitimate landing page displayed by Coursera. This is done by the attacker to further gain the victim’s confidence, duping them into “enrolling” for a Meta Social Media Marketing Professional Certificate. However, upon inspecting the URL in the address bar, one can spot a second red flag: the site displayed, (hXXps://prolearning-academy[.]com/online/certificate,) is a newly registered website, and is not the legitimate Coursera domain. An “Enroll for Free” button can be clicked to continue and finalize enrollment, mimicking how you enroll in courses on Coursera.
.png)
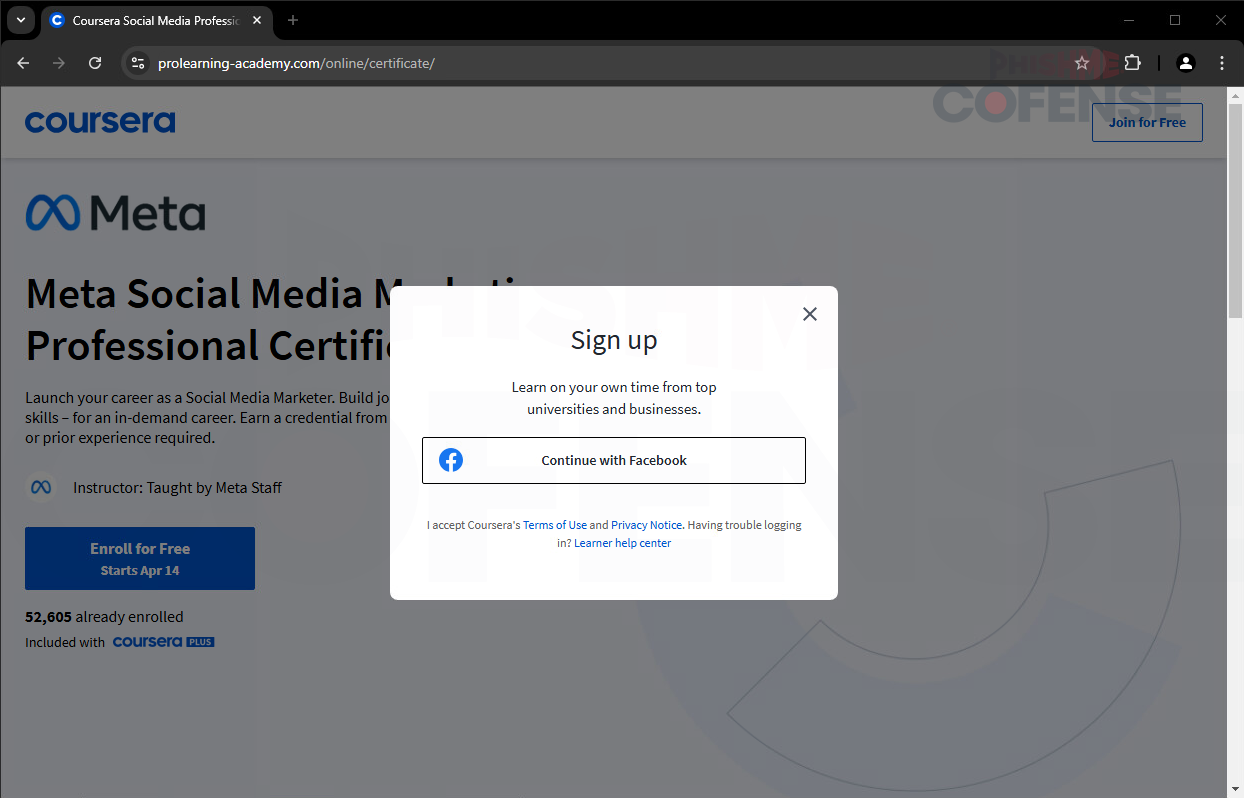
Figure 3: Enrollment Page
Clicking the Enroll button reveals a prompt to the victim, as displayed in Figure 3. A clickable button with the text “Continue with Facebook,” prompting the victim to log in to Coursera using their Facebook account. This clever use of the modern method of signing in via a social media platform/email account for ease of use has been employed with the goal of credential phishing.
.png)
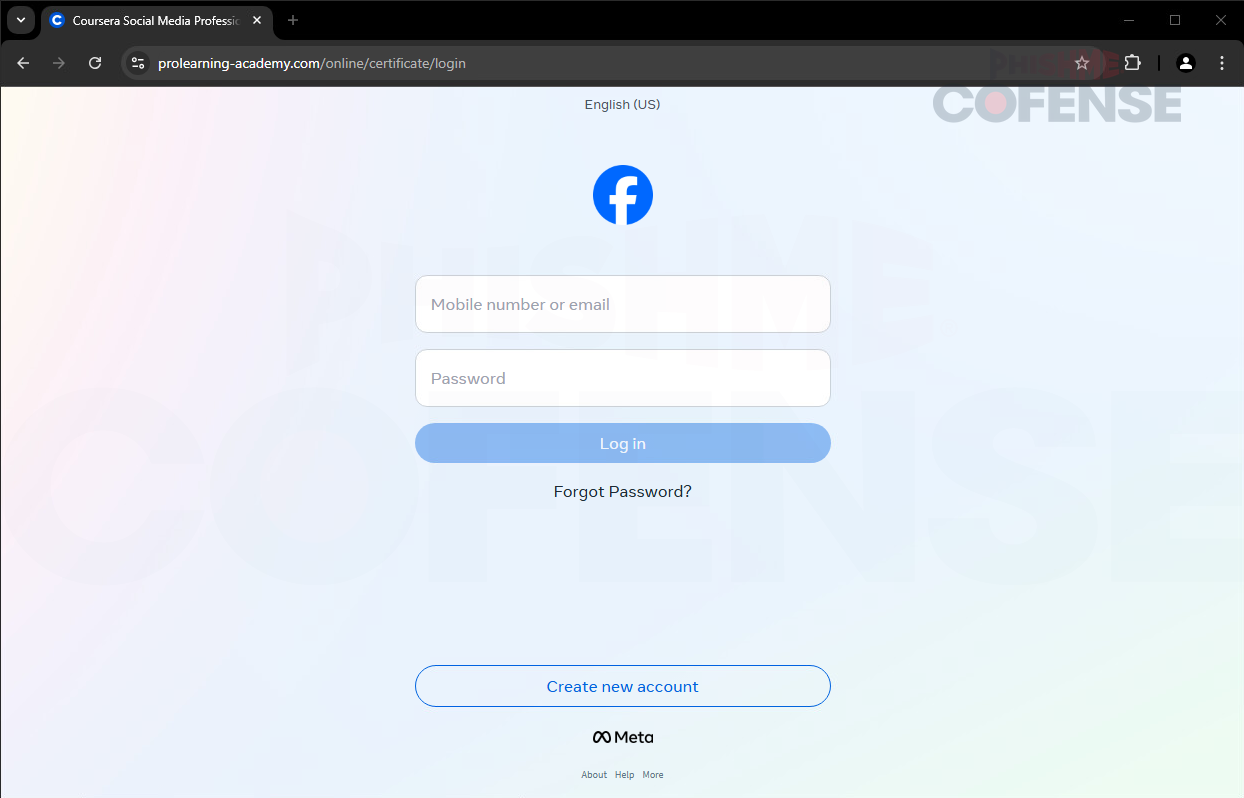
Figure 4: Phishing Page
In the final stage of the campaign, users are presented with a fake Facebook login page, shown in Figure 4. The login page contains a mobile number or email address field, a password field, and a login button. Similar to logging into their own Facebook account, the victim is expected to type their email and password in the fields below, and click log in, exfiltrating their credentials to the threat actors’ C2 server.
Phishing campaigns like this are examples of how threat actors deceive victims by spoofing multiple platforms and offering enticing rewards. This example leverages the popularity of online learning platforms and the allure of free courses to ultimately become an expensive lesson for its victims. Campaigns like this will become ever more common, aiming to steal victims' credentials and sensitive information. Users should always be alert and validate enticing emails, enable 2FA when possible, and even report to IT suspicious emails received. To learn more about our threat-based simulation training as well as our Managed Phishing Detection and Response (MPDR) platform, contact us today.
Stage 1 - Observed Email Infection URL: | Infection URL IP(s): |
|
52[.]38[.]173[.]188 |
Stage 2 - Observed Payload URL(s): | Payload IP(s): |
hXXps://six[.]anotherlevel[.]app/api/send_login/67fd232e7901ae64481ec04a/67fd232e7901ae64481ec049
|
146[.]70[.]81[.]214
|
All third-party trademarks referenced by Cofense, whether in logo form, name form, or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of endpoint protections are based on observations at a point in time, based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog, are registered trademarks or trademarks of Cofense Inc.