Cofense Intelligence has recently issued a Flash Alert regarding a Social Security Administration-spoofing campaign that delivers ConnectWise RAT. In short, an email claiming to be from the United States Social Security Administration delivered an embedded link that downloaded a ConnectWise RAT installer. This campaign is particularly notable for beginning several weeks before the 2024 United States presidential election and ramping up in frequency leading up to Election Day. However, the campaign’s emails have evolved since then and now feature more deceptive email spoofing techniques, evasion tactics, and credential phishing attempts. This intelligence report serves to provide updates on the changing tactics, techniques, and procedures (TTPs) used by this campaign and provide additional in-depth analysis on this threat’s relevance in the current political climate.
Campaign Overview
As previously covered in our Flash Alert, this campaign spoofs the United States Social Security Administration and claims to be an updated benefits statement. While the exact structure of the email changes from sample to sample, the campaign consistently delivers an embedded link to a ConnectWise RAT installer. The embedded link is typically a mismatching link that does not go to the site that is displayed in plain text, and some instances of campaign emails embed the link with a “View Statement” button. Early iterations of this campaign used relay servers hosted on ConnectWise infrastructure for its C2, but later samples use dynamic DNS services or various threat actor-hosted domains.
Cofense Intelligence first observed this Social Security Administration-spoofing campaign on September 16, 2024, but this sample was an isolated instance until another one was seen on October 15, 2024. Shortly afterwards, additional emails were delivered, increasing in frequency throughout early to mid-November. While additional emails were seen in late November, this campaign reached peak volume on November 11th and 12th, a week after Election Day.
Evolution in Tactics
While early iterations of these email campaigns featured basic and naïve emails, the tactics used have evolved over time to make the emails far more deceptive.
Brand Spoofing Emails
Many emails in these campaigns use various Social Security Administration-branded image assets such as logos to make the email appear to be legitimate. By combining these recognizable assets with mismatching links that appear to be directing to official government webpages, a threat actor can make emails that look to be from the spoofed brand.
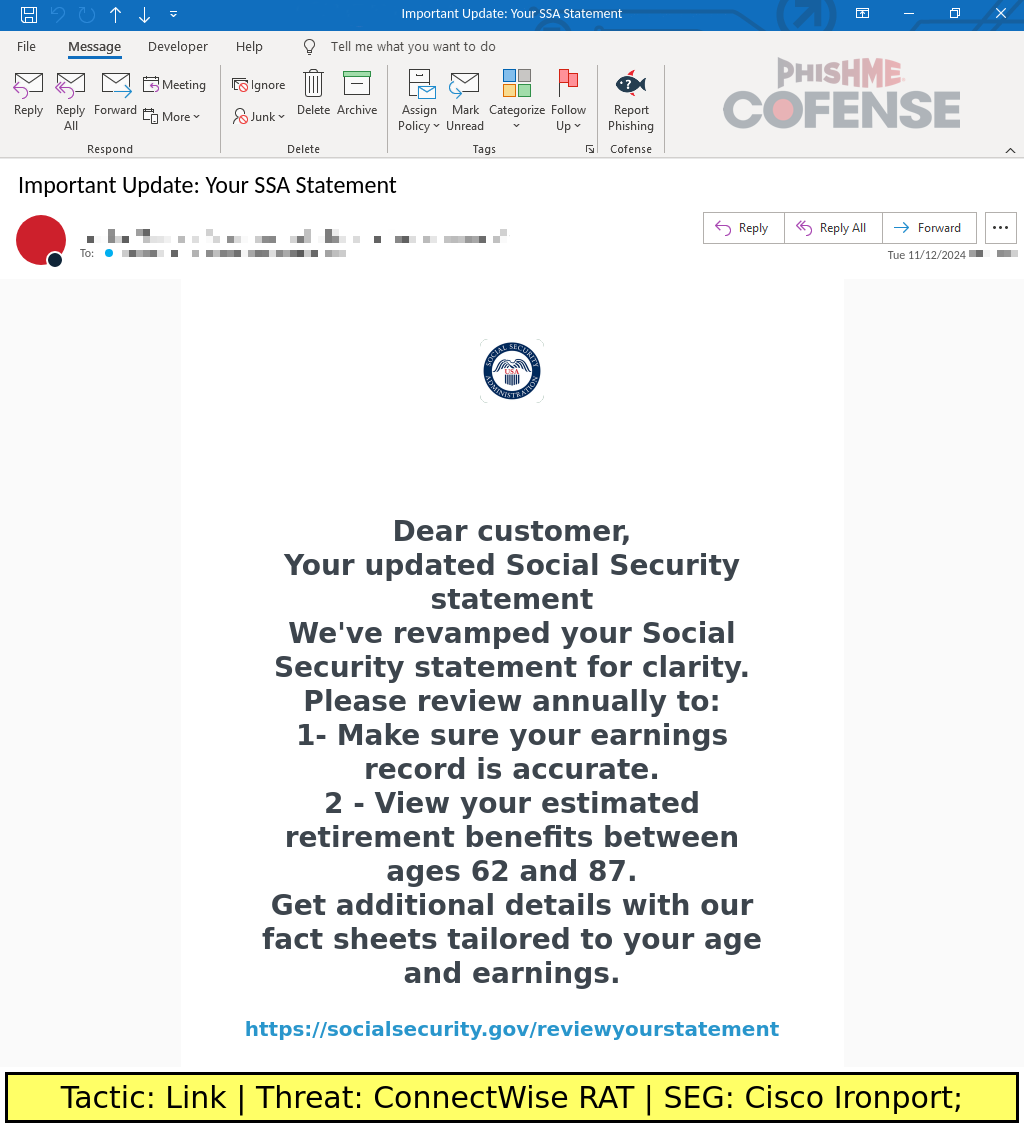
Figure 1: A sample Social Security Administration-spoofing email using branded image assets. Note the inclusion of a mismatching link that appears to go to an official Social Security Administration webpage.
Evasive, One-Time Use Payloads
Some embedded link payloads appear to only redirect to the ConnectWise RAT payload one time, and subsequent attempts to access the link redirect the potential victim to a legitimate Social Security Administration website. This mechanism appears to be using web browser cookies to detect whether a victim has visited the malicious site before.
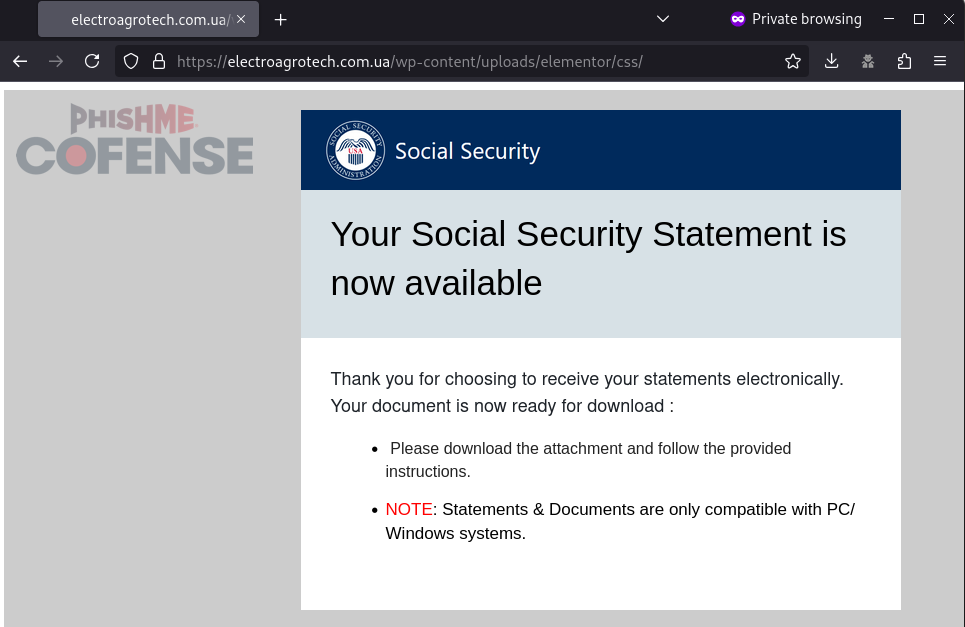
Figure 2: A sample embedded link to a ConnectWise RAT installer when accessing the URL for the first time.
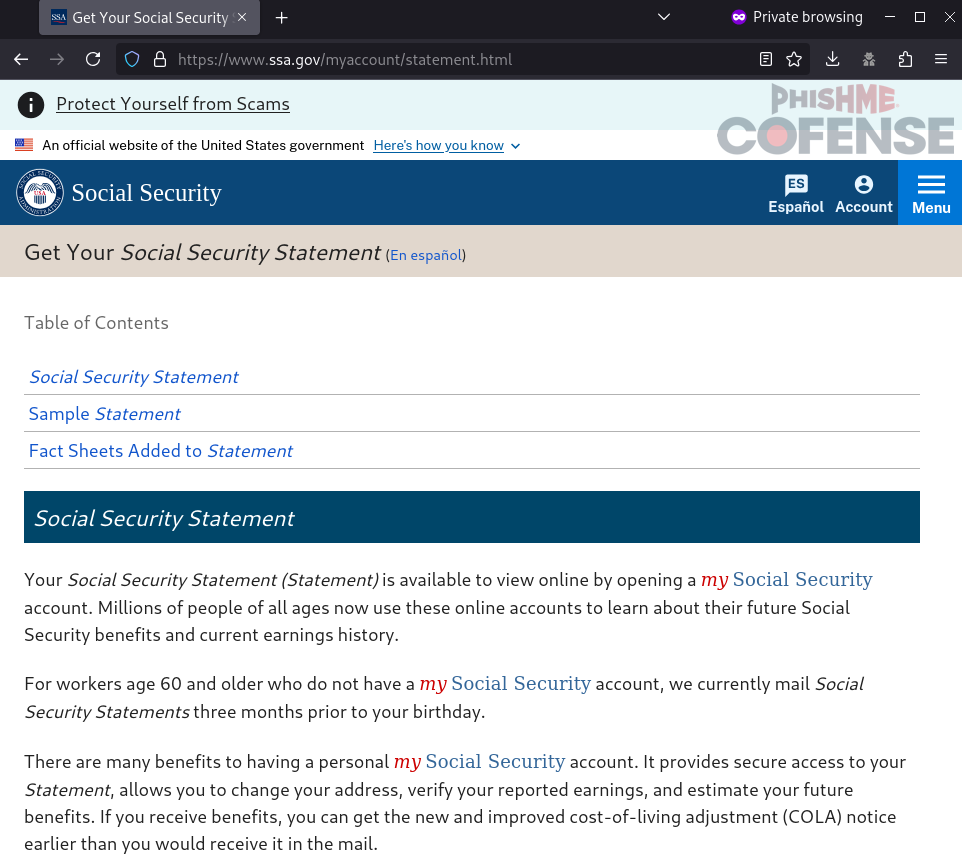
Figure 3: When accessing the link on subsequent attempts, the site redirects to an official Social Security site.
Credential Phishing Forms
- First name
- Last name
- Email address
- Phone number
- Residential address
- ZIP code
- Social Security Number
- Date of Birth
- Mother’s maiden name
- Phone carrier PIN
- Credit card number
- Credit card expiration date
- CVV
- ATM PIN
By requesting this information, the threat actors can commit identity fraud themselves or sell the information for other threat actors to use. While asking for sensitive financial information like credit card info is a common tactic for threat actors, asking for the mother’s maiden name and phone carrier PIN are slightly more novel. These two fields are likely used by the threat actor to perform account takeovers. Many websites use a person’s mother’s maiden name for password recovery security questions. Similarly, many websites offer SMS-based multi-factor authentication (MFA). By asking for a phone carrier PIN, a threat actor could request to transfer the phone number to a threat actor-controlled device. After securing these two potential account takeover methods, a threat actor could perform reconnaissance on popular websites to see if the victim’s email address has a registered account to takeover.
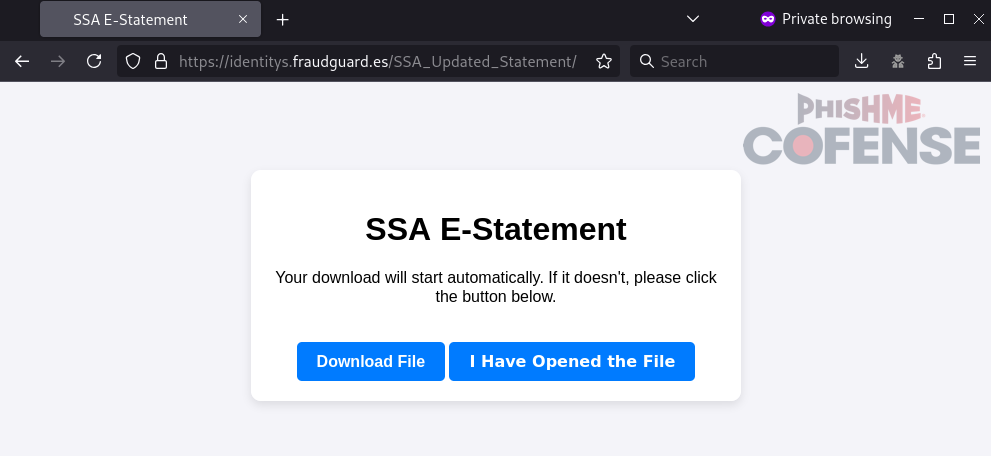
Figure 4: A sample embedded link to a ConnectWise RAT installer. Note the inclusion of an additional “I Have Opened the File” button which prompts the user to perform follow-up tasks after installing the RAT.
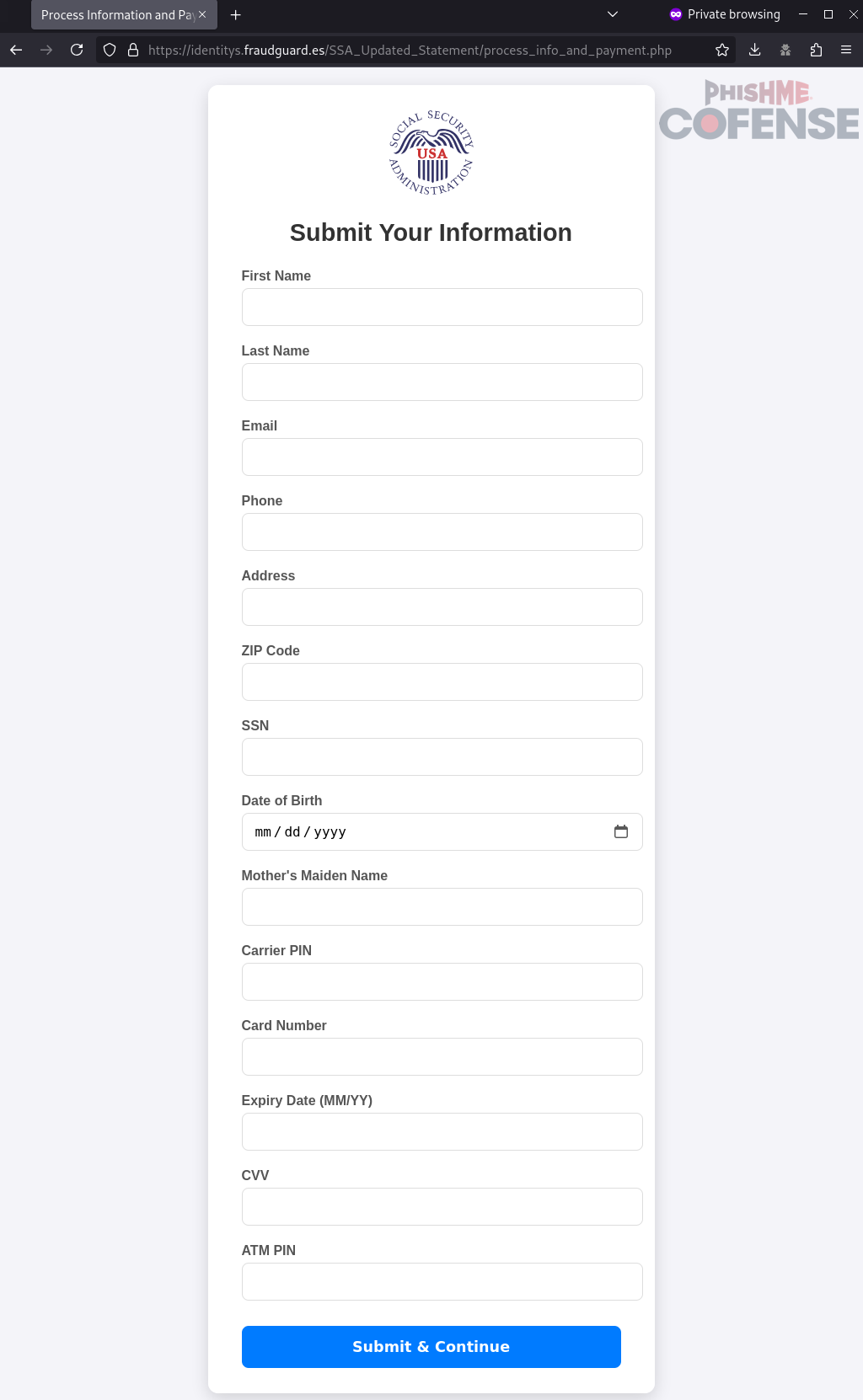
Figure 5: When clicking the “I Have Opened the File” button, the victim is redirected to a credential phishing page.