Author: Kahng An
Cofense Intelligence has recently identified a series of end-of-year and holiday bonus-themed credential phishing emails. These are notable because of their topical seasonal lure and for spoofing the recipient’s company. The victim organizations targeted in this campaign are mostly in the Mining, Quarrying, and Oil and Gas Extraction sectors. The most sophisticated iteration of this campaign, which this article will focus on, is also notable for using a QR code in an attached Microsoft Word document to deliver the credential phishing link. Threat actors sometimes use QR codes to bypass Secure Email Gateways (SEGs) and increase the odds of a target following a link without knowing where it will take them.
Campaign Structure
The emails for this campaign are tailored to spoof the victim’s organization, and the more sophisticated examples use brand assets to appear legitimate. The lures are generally structured around the HR team thanking the recipient for their hard work over the past year and providing an end-of-year bonus. Toward the end, the lure prompts the recipient to open the attached Microsoft Word document for additional details. The following figure shows the email, though highly redacted due to the sensitive nature of the spoof.
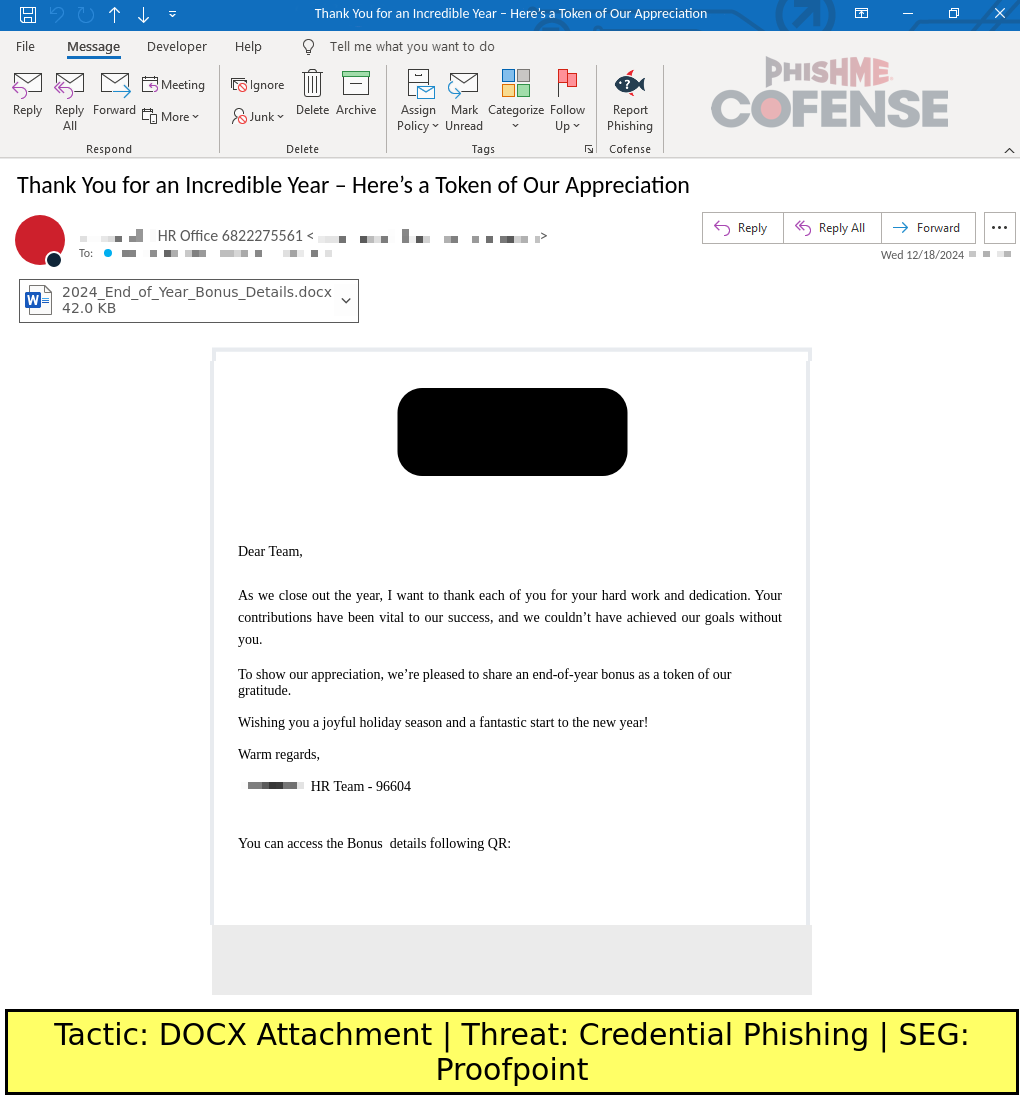
Figure 1: An example of the credential phishing email.
The attached document contains a QR code that purports to be a link to SharePoint but actually leads to the credential phishing page, as seen in Figure 2. The document is notable for addressing the recipient directly and claims that the document is confidential in an attempt to make the recipient feel like they received a unique offer.
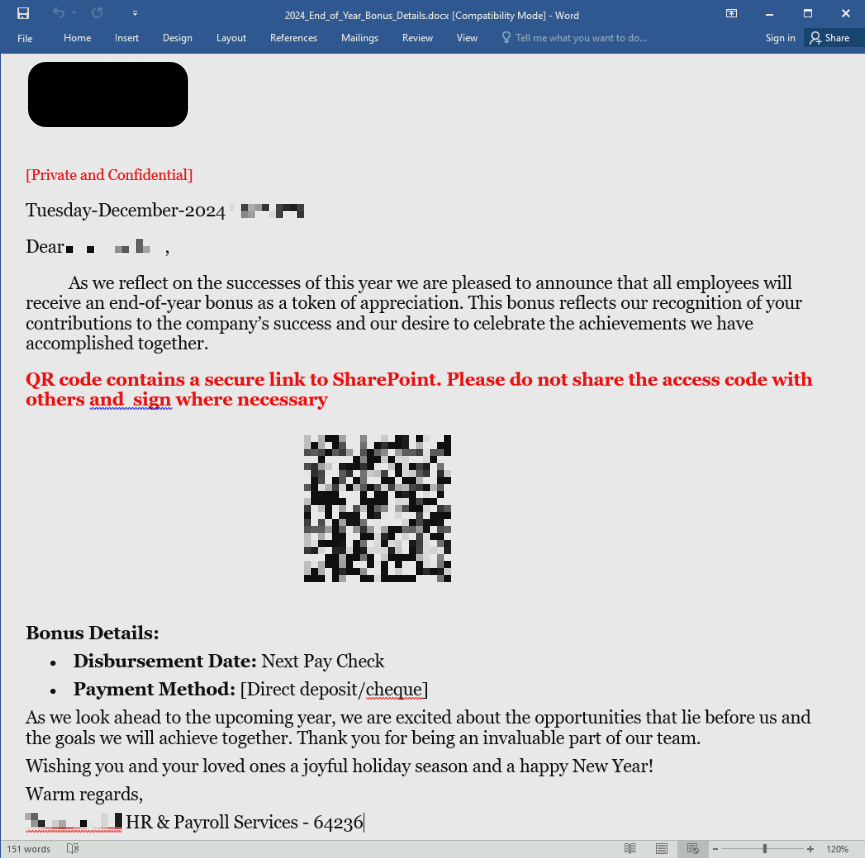
Figure 2: The attached Microsoft Word document containing the phishing QR code.
When accessing the QR code, the victim is directed to a credential phishing page that mimics a Microsoft login page viewed in Figure 3.
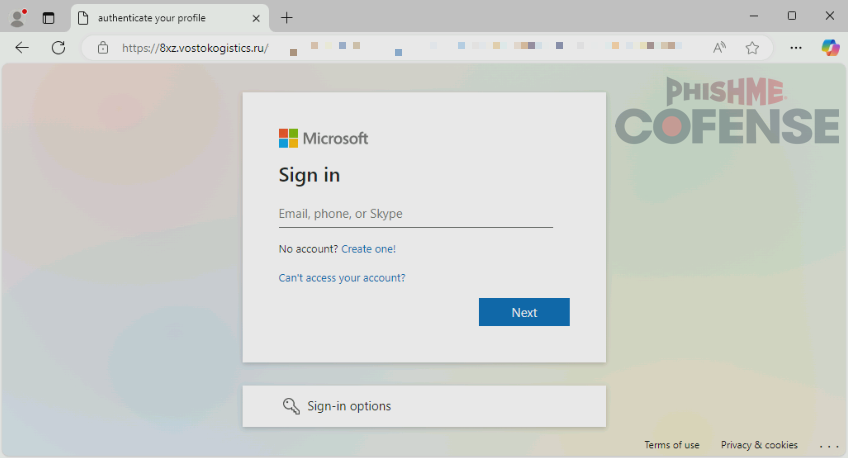
Figure 3: The credential phishing page embedded within the QR code.
After inputting an email address from the victim’s organization, the credential phishing page prompts for a password and displays the organization’s brand assets to make the login seem more believable, as seen in Figure 4.
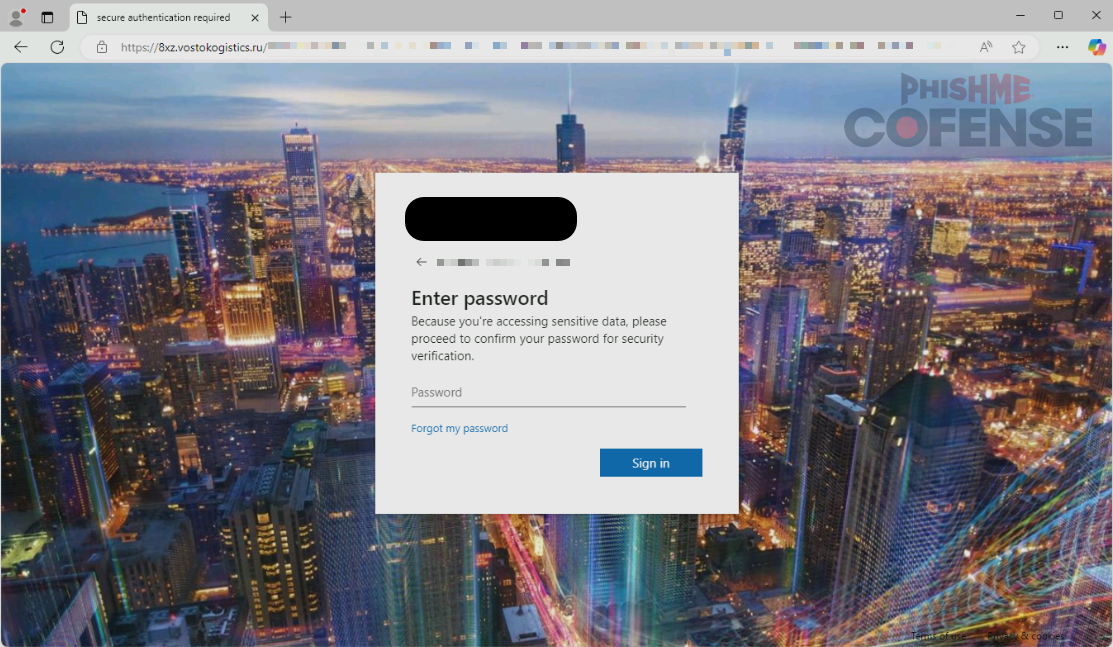
Figure 4: The credential phishing page prompts for a password and displays the victim’s organization logo to make it seem like a legitimate login screen.