By Cole Adkins, Cofense Phishing Defense Center
Hook, Line, & Tax Sink: Dodging the Phishing Nets This Tax Season
Tax season has officially arrived, and with it comes an increased need for vigilance when handling emails or documents related to personal tax information. During this time of year, cybercriminals are particularly active, finding new ways to target individuals and compromise sensitive data. In fact, threat actors have been deploying sophisticated, tailored phishing schemes based on tax returns for some time now. Fortunately, there are ways to protect yourself from these malicious attacks. In this blog, we'll share one of the many encounters the Cofense Phishing Defense Center (PDC) has come across and provide key indicators to help you spot these threats and safeguard your personal information.
The Cofense PDC has observed a new phishing campaign that targets employee credentials by exploiting their anticipation of tax return notifications during tax season. The main objective of this phishing campaign is to deceive recipients into interacting with emails disguised as tax return notifications in order to harvest their Microsoft login credentials. 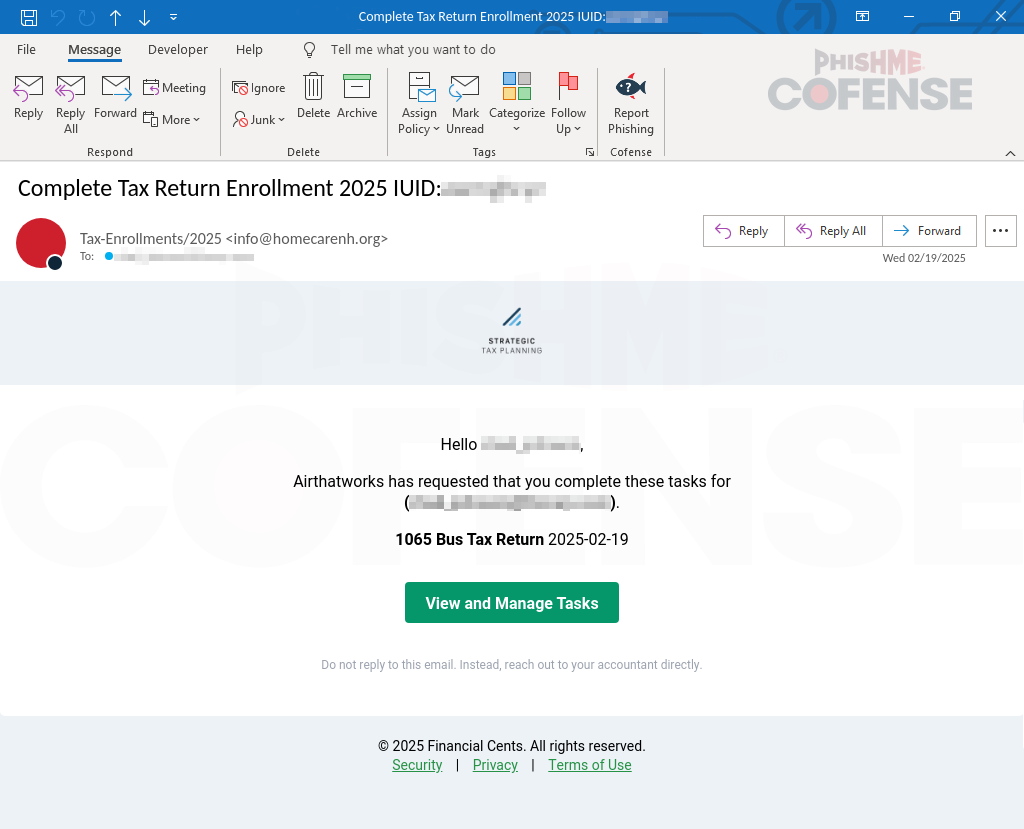
Figure 1: Email Body
The email in Figure 1 is meant to appear as though it came from “Strategic Tax Planning.” However, if you look closely, you will notice that the from address is “info[.]homecarenh[.]org.” Most employees scanning through their emails might only notice the “Tax Enrollment” subject and see the body of the email indicating they have tax enrollment tasks to complete. This would likely lead to the employee clicking the “View and Manage Tasks” button found in the body of the email. Branding this phish as a tax return helps ease the suspicion of unsuspecting employees who are eager to get their taxes filed so they can get their returns. The body of the email shows the employee has outstanding tasks that need to be taken care of, which creates a sense of urgency that something may be incorrect with their taxes.
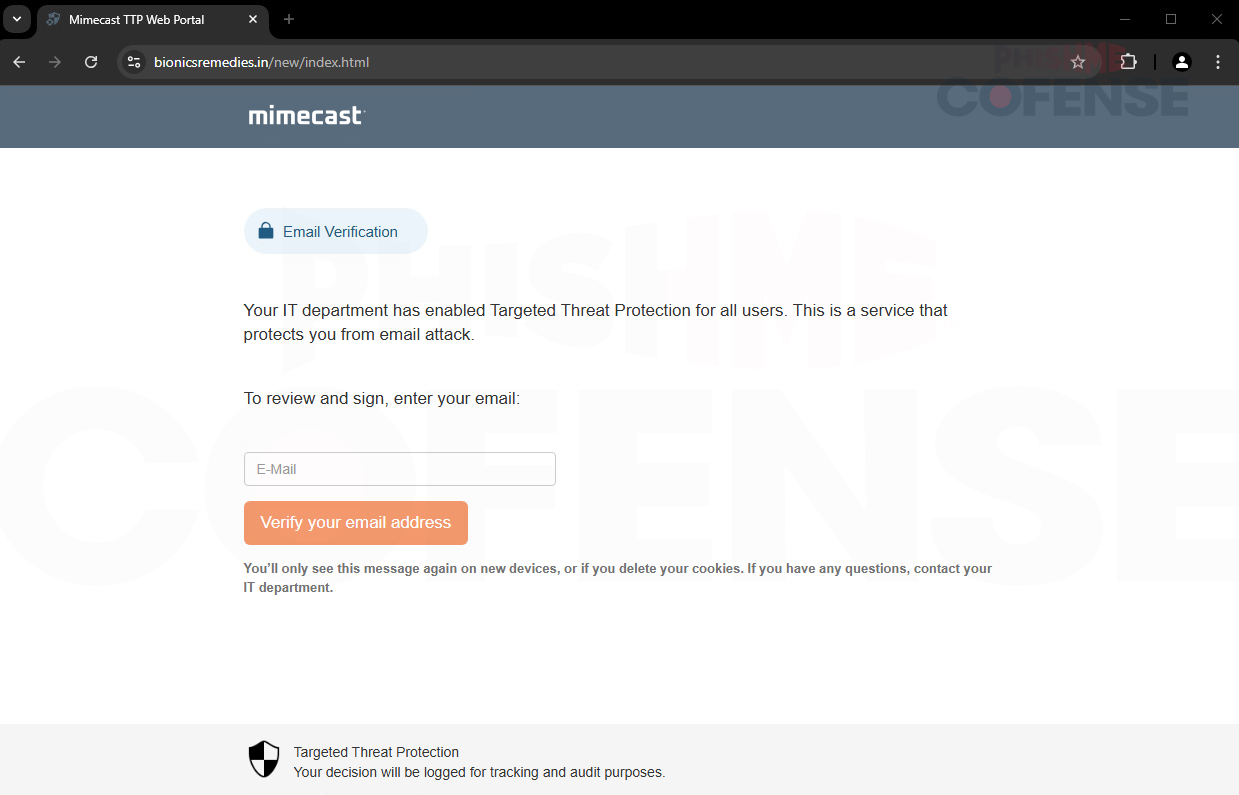
Figure 2: Phishing Redirect Page
Figure 2 shows the threat actor spoofing a Mimecast URL protection page, which is commonly used by many companies to check for malicious links. This gives the user the illusion that this redirect is safe and has been vetted. Upon clicking the “View and Manage Tasks” button found in the body of the email, the employee is redirected to this site. The employee will then enter their work email and click the “Verify your email address button.” This will prompt the next step in this phishing attempt process. Something to note here is that the URL address at the top of the webpage does not match with Mimecast branding at all, as it is bionicsremedies[.]in.
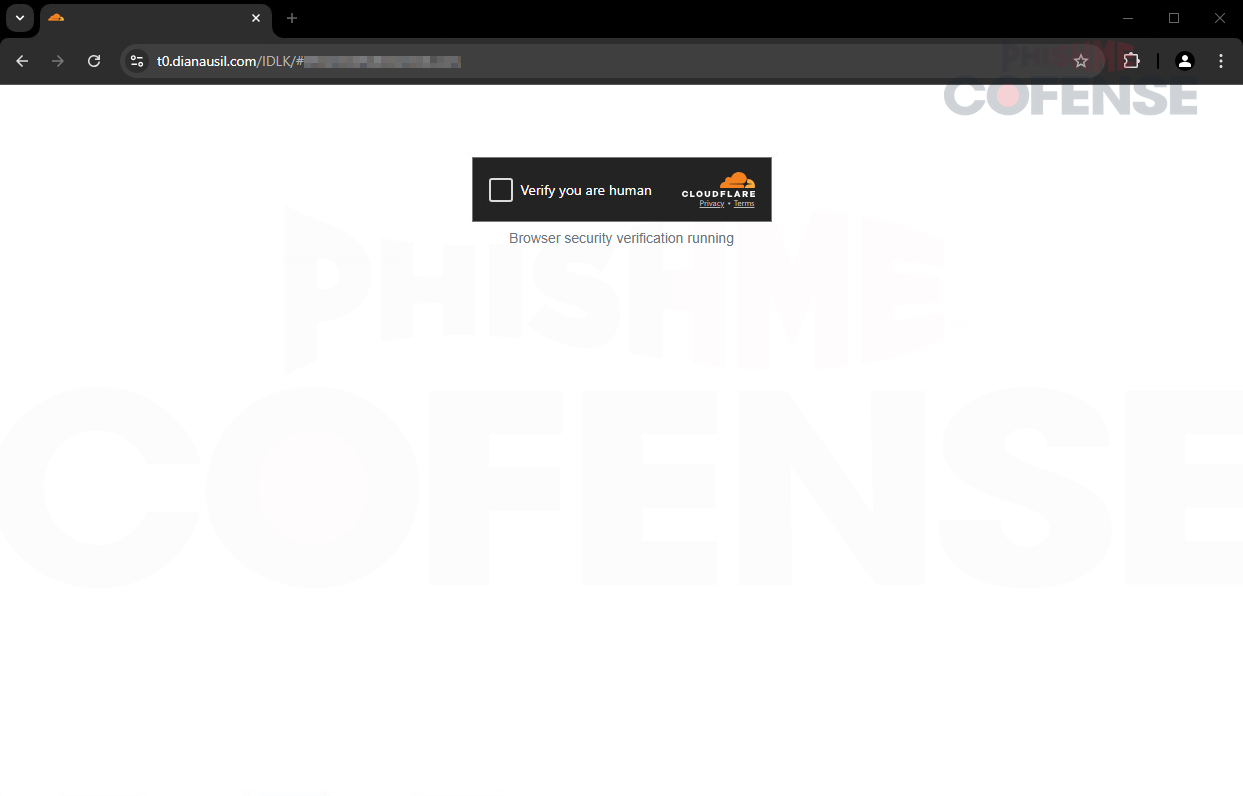
Figure 3: Phishing Redirect #2: CAPTCHA
Figure 3 displays the second redirect, which leads to a CAPTCHA page. The employee will interact with the CAPTCHA, which will verify they are indeed human before redirecting again. This further adds to the legitimacy of the redirect, which in turn is building the trust of the employee in hopes that once they land on the final phishing page, they will enter their credentials.
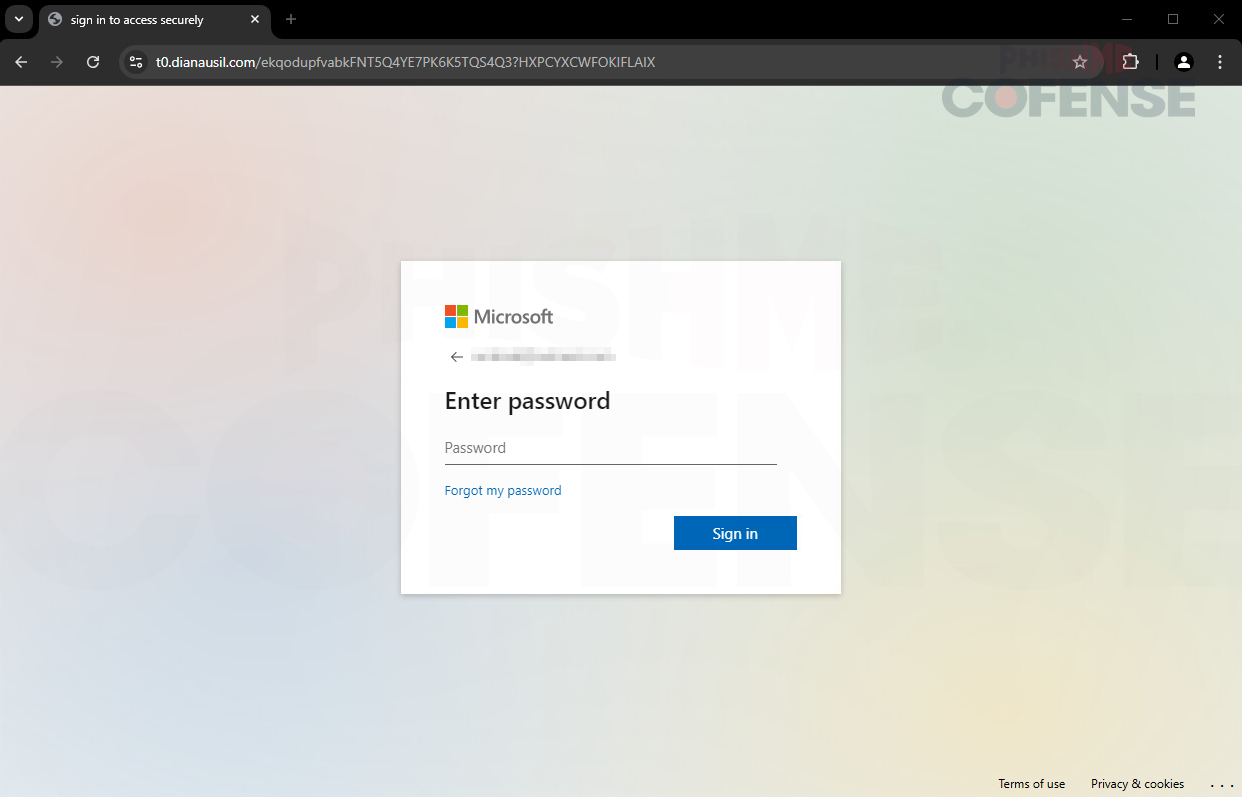
Figure 4: Final Phishing Page
The final stage of the phishing campaign is the Microsoft landing page, as shown in Figure 4. This is typical formatting across all Microsoft credential phishing emails. Again, the obvious way to tell is through the URL, “t0[.]dianausil[.]com,” which is not an official Microsoft-owned domain. Once the employee enters their email and password, their account will be compromised.
This campaign demonstrates how fast tactics evolve and the ways in which threat actors can tailor credential phishing emails for things such as tax returns. This is why recipients must stay vigilant and informed on common phishing threats in order to protect their credentials and other sensitive information. COFENSE Managed Phishing Threat Detection and Response (MPDR) solutions can help identify threats such as these and bolster your company defenses against phishing attacks and other threats that may arise. By partnering with the Cofense Phishing Defense Center (PDC), your organization can stay ahead of evolving phishing campaigns and ensure the security of employee personal information.
Indicators of Compromise | IP |
hXXps://us[.]content[.]exclaimer[.]net/?url=hXXps%3A%2F%2Ftyw55uhbb[.]cc[.]rs6[.]net%2Ftn[.]jsp%3Ff%3D001fCpcrsdCunDl9WbCgL4s4_o7lCCfUKc-_Gmf-2cXeijC-QKy_ucQ9LejFsbdTaFAvBz_nxFbwCfNtoM1Af8klzhr7zZOKphrQx_9JsP8DewIoRHg2VdAc4g2AxqajGop-1ifXj9HmKvWRoBhknfNQBI8o4n2cwX-CLK4bRH9lRrUGAGr7wn5G1Bibl6hpKXXjDK3g2KlsSDuKynCxiaA86VvfZR39dJxAjDGvh-sJhpA9epEpC8m9dhh5PzK3j7as6LLgG-A1NbcKqc04qDomvMgDhn-QyMeL04oB1ANtUTLvDT-85v7leQ7huAokR7mPCVsIXcTY5xnqWhwzfthx1rvMi2o-x8bpigtWnxBpH-tmGOxSQfsmaiDoHR6zqw%26c%3DY272-Avpc5qqPlnjOZoqo_oia-5xa5wnDaOSxv_2DGBiHZyf9qN05Q%3D%3D%26ch%3DuJWmSxOzt0iwKlMeXQwAoyrz079N2hzyEBuPTGlJ_NM9ODKGQwtJFQ%3D%3D&tenantid=ky73-4KEe-QywAiSCk5gQ&templateid=cb0b228ec9eeef1190cb002248293981&excomponentid=nFEX-f7jNWeTfOzn2CEZDBNyzTqFqptsBHQZrvkNPgE&excomponenttype=Link&signature=sEERLmKwG_ch5xjxBK8TizNVcH13klI3oQD_EpRI0vd-FUv00yRBYB7MDvPdStSuYXIsXxQZcn4YVazADwZuTc7BfPkmbMPL4khk1gt5nuNc5pRUMlSHCyVZXL_9_K-T6Dl9yGTsXnaGPlQWybwKCpKN1UgFDPN71-3RsewLvATu118H3noHegsza6gxTxKFBxdXxpgxEQ8M2_NOdj3fUpbExbXa4IkMwPlqdQo0US0D0oCzQ8xeS1u0FHCaJlcaFwumNEPVs9Jdnj0ufqyILHmol9_JZedWObkiG6ouqtKKV71DrDVUT-RmvM3gJWlZZX89tunoICt293rdOH2DeQ&v=1&imprintMessageId=ca7502cf-82a7-4210-81de-d97312a43ba2 | 172.64.152.78 |
hXXps://tyw55uhbb[.]cc[.]rs6[.]net/tn[.]jsp?f=001fCpcrsdCunDl9WbCgL4s4_o7lCCfUKc-_Gmf-2cXeijC-QKy_ucQ9LejFsbdTaFAvBz_nxFbwCfNtoM1Af8klzhr7zZOKphrQx_9JsP8DewIoRHg2VdAc4g2AxqajGop-1ifXj9HmKvWRoBhknfNQBI8o4n2cwX-CLK4bRH9lRrUGAGr7wn5G1Bibl6hpKXXjDK3g2KlsSDuKynCxiaA86VvfZR39dJxAjDGvh-sJhpA9epEpC8m9dhh5PzK3j7as6LLgG-A1NbcKqc04qDomvMgDhn-_QyMeL04oB1ANtUTLvDT-85v7leQ7huAokR7mPCVsIXcTY5xnqWhwzfthx1rvMi2o-x8bpigtWnxBpH-tmGOxSQfsmaiDoHR6zqw&c=Y272-Avpc5qqPlnjOZoqo_oia-5xa5wnDaOSxv_2DGBiHZyf9qN05Q==&ch=uJWmSxOzt0iwKlMeXQwAoyrz079N2hzyEBuPTGlJ_NM9ODKGQwtJFQ== | 104.21.23.248 68.178.226.214 172.67.214.184 208.75.122.11 |
All third-party trademarks referenced by Cofense whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of ed point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
Typically these are more often used just to block some VPNs and locked down browsers for malware sandboxes. Not really sure if this angle of making it seem more legitimate is true for most people maybe use "phishing campaign" or just "phish" for this