By Dave Alison, VP Product, Cofense
Cofense has focused on the human side of email security for over a decade. This focus requires that we look at the threat landscape through a unique lens – not just the conditioning of employees to spot suspicious emails but to leverage our intelligence to eliminate threats other employees in other organizations around the world have just reported.
What does that mean? At a high level, it means that crowdsourced human intelligence is stopping attacks BEFORE it happens.
Every day, thousands of novel attacks are launched via email against organizations large and small. These bypass perimeter security technology and land in unsuspecting employee inboxes, potentially causing millions of dollars in damages as threat actors trick unsuspecting employees into activating these payloads or handing over their credentials.
How It Works
Cofense has millions of trained human sensors deployed across organizations and sectors around the world actively reporting those attacks to us as these campaigns hit their inboxes. These emails, combined with other proprietary collections, are analyzed by our Cofense Intelligence team, which examines these threats in close to real-time, and quickly provides intelligence derived from these verified attacks to our customers.
This intelligence subsequently feeds an Auto-Quarantine capability, which removes malicious emails from an inbox in minutes, often before users see or have a chance to open the email.
As this rich intelligence is disseminated via our Intelligence API feed, these Indicators of Compromise (IOCs) are deployed to any instance where our customers have Auto-Quarantine fully enabled. Here’s how this unfolds:
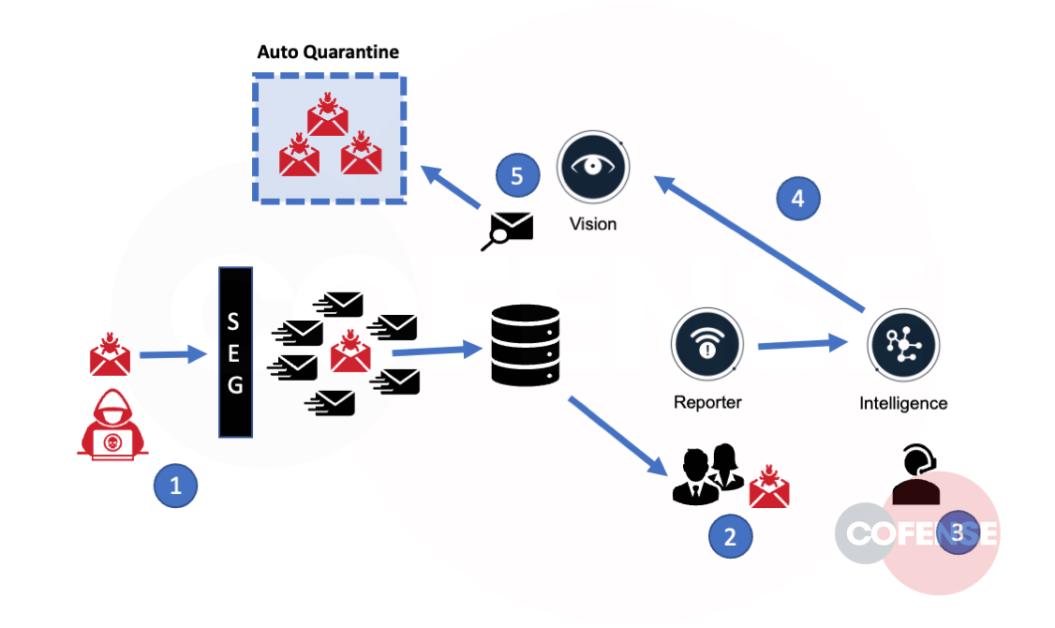
- A new attack that evades the secure email gateway (SEG) reaches one or multiple employee inboxes.
- An employee receives the malicious email and believes it is suspicious. They use the Cofense Reporter to notify their security team or our Cofense Phishing Defense Center (PDC).
- A Cofense Intelligence Analyst performs a review of malicious reported emails, building out an Active Threat Report (ATR) and extracting the Indicators of Compromise (IOC). There are over 50K of these IOCs generated every month.
- The IOCs are then sent to the Cofense Vision customers, with a 5-minute check-in schedule for any new ATRs added or updated.
- Vision Auto-Quarantine examines incoming and existing email for the new IOCs and, if found, automatically moves the emails into quarantine.
What We’ve Found
The results are shown in the following graph, which charts the number of emails our system identified as malicious after these got through the SEGs, or other various email controls, that protect it.
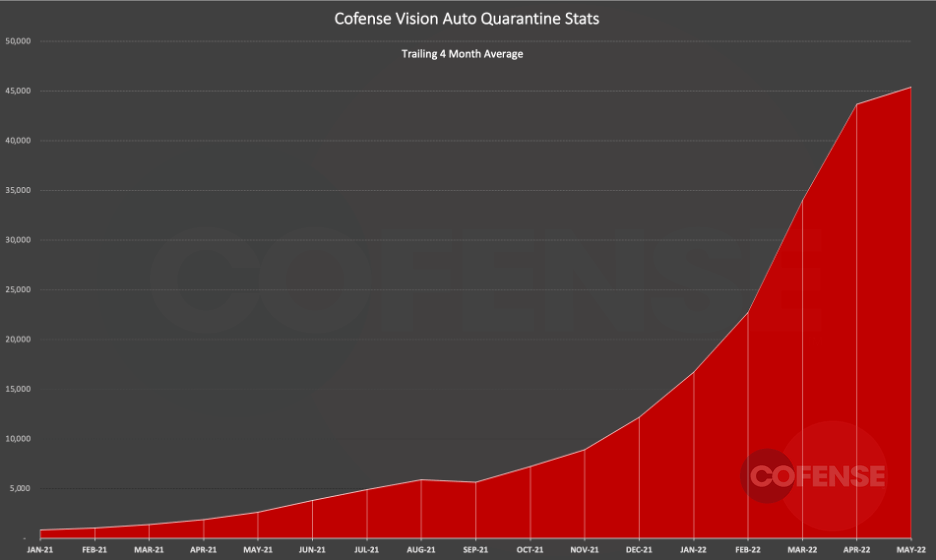
As you can see, this complete loop is having a powerful impact on the threat landscape. Cofense has operationalized the human security layer, addressing the threats that inevitably make it through the technology layer.
It’s important to note that while each SEG available on the market has varying degrees of effectiveness in identifying these threats, we observe thousands of attacks that have evaded every SEG available. This includes large, well-configured customer environments protected by Microsoft, Proofpoint, Cisco IronPort, Mimecast, etc. The actual attack types we see also run a broad range: malware leading to ransomware, credential phish, business email compromise, targeted attacks against VIPs, etc.
Cofense continues to make great strides in increasing the speed of that loop, getting the IOCs into the email stream quickly. Now, more than ever, Vision with Auto-Quarantine provides the best defense against the attacks that are continuing to make an impact.