By: Kahng An, Intelligence Team
While virtual hard drive files like .vhd and .vhdx are typically used for virtual machines, they can also be opened in Windows to mount the virtual image as if it were a physical volume. Recently, threat actors appear to be avoiding detection from Secure Email Gateways (SEGs) and commercial antivirus (AV) by embedding malicious content within virtual hard drive files.
The threat actors send emails with .zip archive attachments containing virtual hard drive files or embedded links to downloads that contain a virtual hard drive file that can be mounted and browsed through by a victim. From there, a victim can be misled to running a malicious payload.
Even worse, the virtual hard drive can be configured to automatically execute the malicious payload in versions of Windows prior to Windows Vista via AutoRun, a component of Windows that allows the operating system to automatically perform an action when the volume is mounted. When SEGs and antivirus scanners analyze virtual hard drive files, they struggle to detect malicious content contained within the hard drive image.
Campaign Trends
Throughout 2024, mountable virtual hard drive files have been utilized as a delivery mechanism across multiple distinct email campaigns delivering various malware families. While the email themes may differ from campaign to campaign, they all appear to be delivering Remcos Remote Access Trojan (RAT) and/or XWorm RAT.
These RATs have recently been featured in Cofense Intelligence’s Executive Phishing Summaries for being some of the most common RATs in SEG protected environments.
Tax-Themed May 2024 Campaign Using Embedded Links
This campaign targeted victims with an embedded download link to a virtual hard drive file purporting to be the sender’s tax documents. Upon downloading the virtual hard drive file, a potential victim would run the main payload, Tax_Organizer.exe, which delivers Remcos RAT by loading a malicious DLL. Figure 1 is a sample of one of the emails within this campaign.
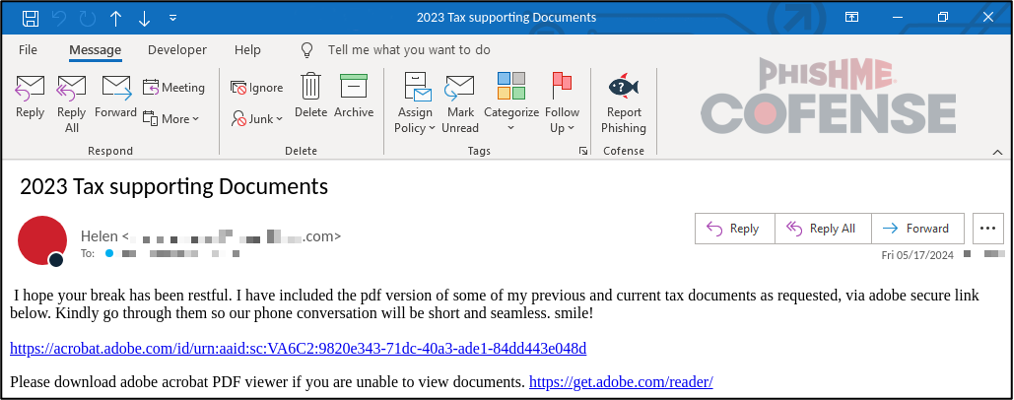
Figure 1: Sample email for a tax-themed campaign from May 2024 that utilized legitimate embedded URLs to bypass SEGs.
Notably, the virtual hard drive files in all the emails within this campaign contain the same Tax_Organizer.exe payload that delivers Remcos RAT, but the virtual hard drive files themselves have varying file hashes because their size and contents can be easily manipulated by threat actors.
Shipping-Themed June and July of 2024 Campaign Using VHDX in Attached ZIP Archives
This campaign spoofed Canada Post and other postal services to deliver attached .zip archives containing a virtual hard drive file purporting to be a package label photo. The threat actors targeted victims with emails claiming that a package was not delivered and that the postal service requires the victim to review their address and contact information on an attached photo of the package label.
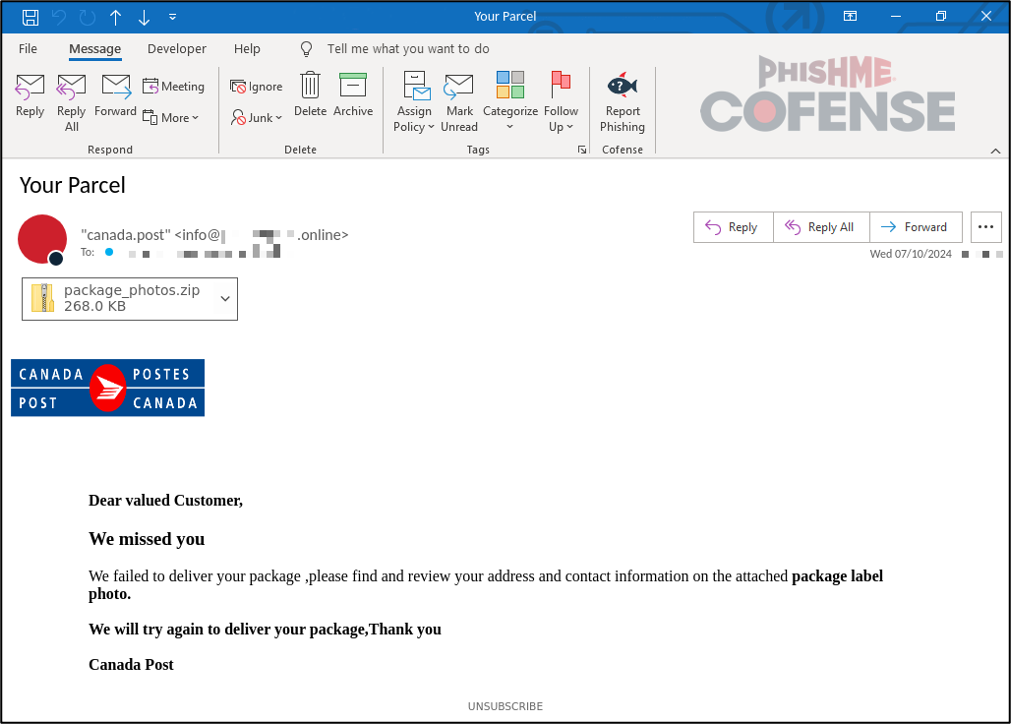
Figure 2: Sample Canada Post-spoofing email for a shipping-themed campaign from July 2024.
After opening the virtual hard drive file, a potential victim would open a malicious LNK file named package_photo.lnk which subsequently executes malicious a Visual Basic Script file stored within a folder named faq. The Visual Basic Script is used to deliver a DotNETLoader and XWorm RAT which is in turn used to deliver Remcos RAT.
Resume Themed August 2024 Campaign Using VHDX in Attached ZIP Archives
This campaign targeted Spanish speaking victims with attached .zip archive files that were purported to be a curriculum vitae for review by the recipient. Notably, the emails have several copies of the same file archive attached with each one delivering the same .vhdx file. Each attached virtual hard drive file contains a Visual Basic Script file that runs Remcos RAT in memory.
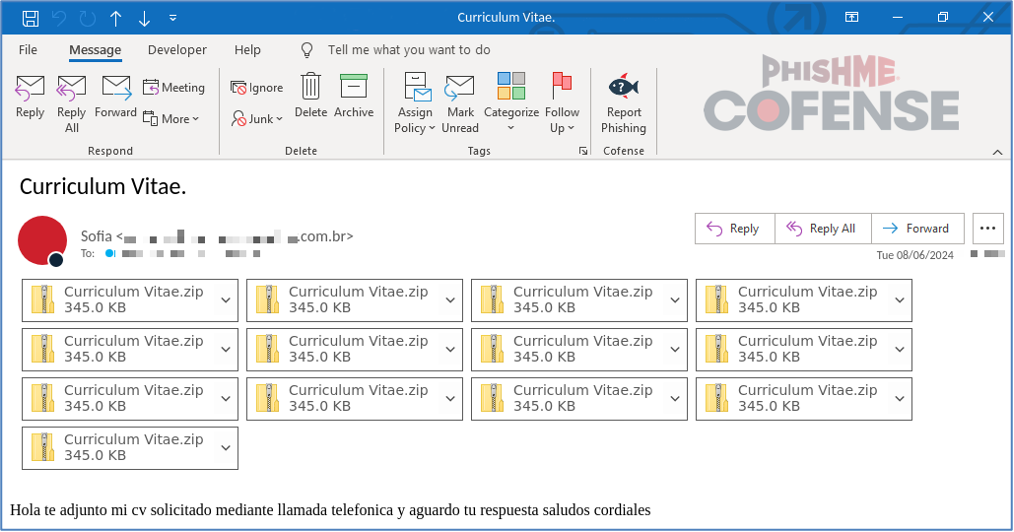
Figure 3: Sample email for a resume themed campaign from August 2024.
Notably, this campaign included autorun.inf files within the attached virtual hard drive files. This is a configuration file that was used by previous versions of Windows to define actions that can be automatically performed when the volume is mounted. On older versions of Windows, autorun.inf files can be abused to prompt users to run malware or even silently run malware without the user ever being aware. Autorun will be discussed in further detail in a later section.
Bypassing SEGs
While virtual hard drive files can be delivered through links to legitimate cloud-based file sharing services to bypass SEGs, they appear to also be able to bypass SEGs on their own. This is likely because many SEGs do not handle scanning virtual hard drive files, and the ones that do rely upon antivirus solutions that struggle to detect malicious content within the hard drive images.
Within the resume-themed campaign noted above, threat actors were able to bypass the following SEGs and related components by simply attaching virtual hard drive files within archive files:
- Cisco Secure Email Gateway
- Cisco ThreatScanner
- Cisco AMP
- Cisco IronPort
- Proofpoint Messaging Security Gateway
- FireEye Email Security
Cisco Secure Email Gateway
Cisco SEG headers were found in three email samples. These headers span three separate components: ThreatScanner, AMP, and IronPort.
When analyzing the email, ThreatScanner simply provided a negative verdict when scanning emails with attached virtual hard drive files. This is focused on HTML-based threats and not attached files. However, one email sample from the tax-themed campaign also provided a negative verdict from ThreatScanner even though the tax-themed campaign used embedded links to deliver the virtual hard drive files.
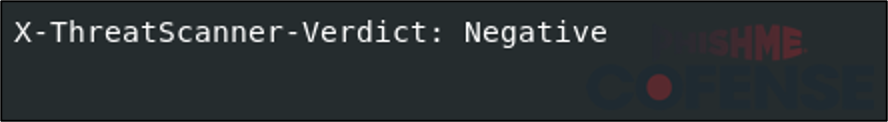
Figure 4: Sample result of a ThreatScanner scan of an email with an attached virtual hard drive file.
Even though ThreatScanner was unable to detect the malicious threat in the email, ThreatScanner was at least able to scan the attached virtual hard drive file. However, AMP was unable to scan the attached file even once across three emails that included AMP headers. AMP noted that the attached files were unscannable, and files were not uploaded. However, it is unclear if this result is because the files were virtual hard drive files within archives files or if because multiple of the same files were uploaded.
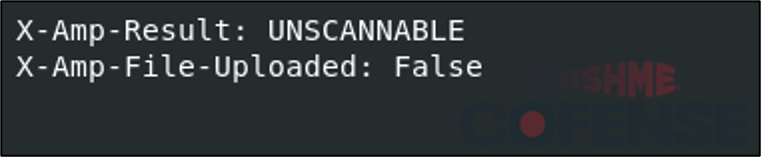
Figure 5: Sample result of an AMP scan of an email with an attached virtual hard drive file.
While ThreatScanner and AMP provide simple positive or negative verdicts for whether an email is malicious, IronPort provides more detailed antivirus scan information. Sophos, the underlying antivirus solution used for this scan, was able to scan the attached file and successfully identify that the archive file contained a .vhdx file, but it did not flag it as malicious.
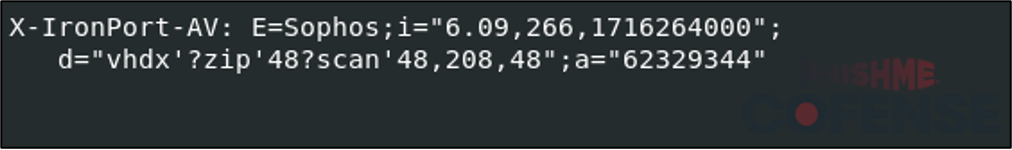
Figure 6: Sample result of an IronPort scan of an email with an attached virtual hard drive file.
Proofpoint Messaging Security Gateway
Proofpoint SEG headers were found in one email sample. The notable header that contains the results of the email scan is displayed below. Notably, the email has a malware score of zero and was determined to not be spam.
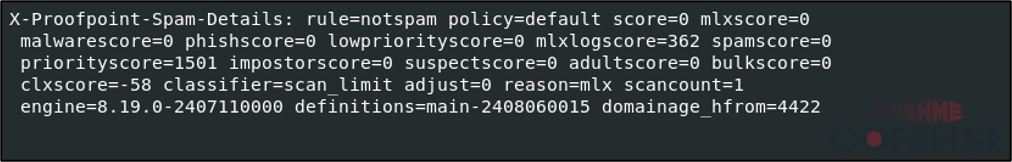
Figure 7: Sample result of a Proofpoint scan of an email with an attached virtual hard drive file.
FireEye Email Security
A FireEye SEG header was found in one email sample. The header simply notes that the email was scanned and determined to be clean.
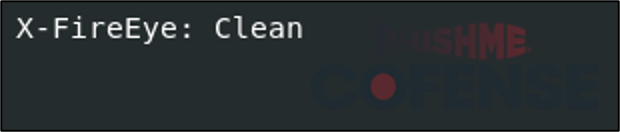
Figure 8: Sample result of a FireEye scan of an email with an attached virtual hard drive file.
Evading AV Detection
Virtual hard drive files also seem to be effective at evading antivirus detection depending on vendor choice with most vendors failing to detect malicious content within .vhd files. One method of validating antivirus detection is by using the EICAR test file which is used to test antivirus detections without needing to use actual malware.
For example, compare the following detection rates on VirusTotal as of October 2024 for an EICAR test file compared to an EICAR test file delivered within a .vhd file and .vhdx file respectively.
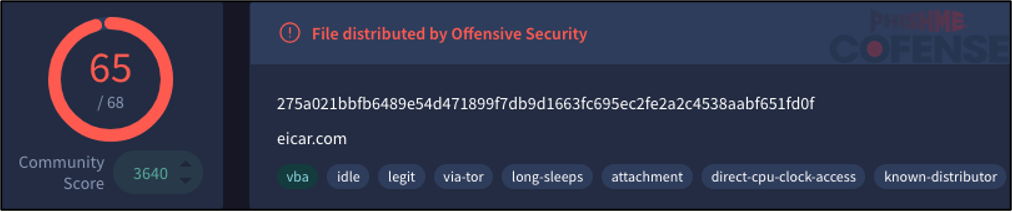
Figure 9: 65 out of 68 detections on VirusTotal for an EICAR test file.
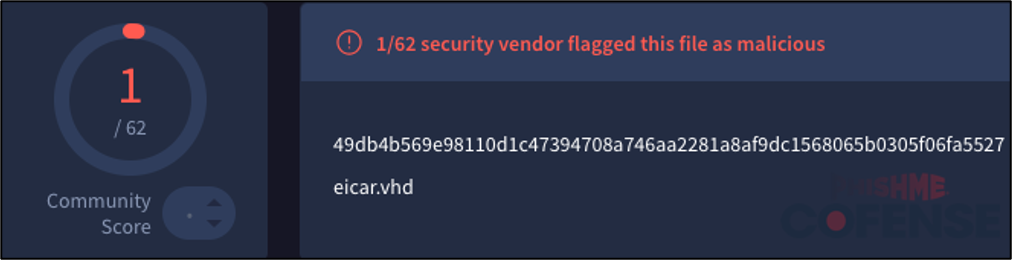
Figure 10: 1 out of 62 detections on VirusTotal for an EICAR test file within a .vhd file.
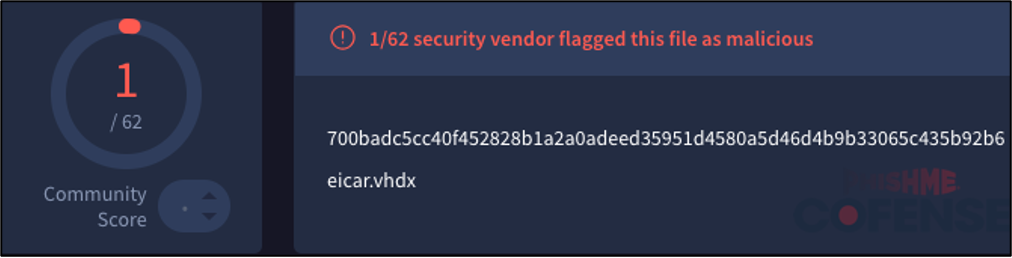
Figure 11: 1 out of 62 detections on VirusTotal for an EICAR test file within a .vhdx file.
While these results are indicative of fresh samples that have not yet been analyzed by any antivirus software, older samples do not necessarily receive substantially better detection rates. Consider the following eicar.vhd sample provided by Will Dormann in August 2019 as described in The Dangers of VHD and VHDX Files:
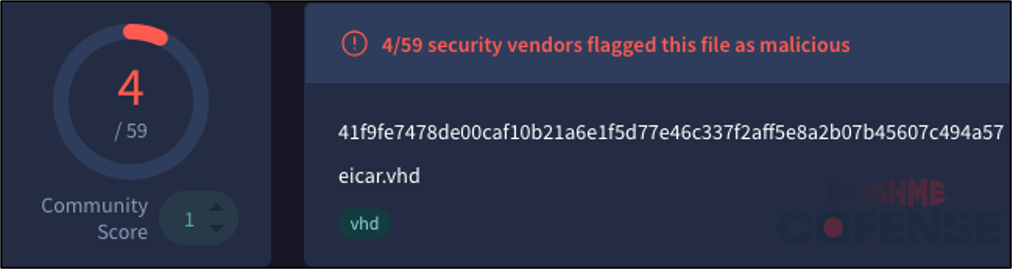
Figure 12: 4 out of 59 detections on VirusTotal for an EICAR test file within a .vhd file uploaded in 2019.
Despite being a much older sample with more time for potential detection, the sample went from zero detections to four detections in total over the course of multiple years of reanalysis.
While antivirus software should be expected to be capable of detecting EICAR test samples, proper detection of an obfuscated EICAR sample is unimportant compared to the detection of actual malware. Unfortunately, real virtual hard drive malware samples are still detected at a lower rate compared to the embedded malicious files.
For the samples found within the resume-themed campaign from August 2024 Curriculum Vitae.vbs is detected at a far greater rate compared to the virtual hard drive file that was used to deliver it.
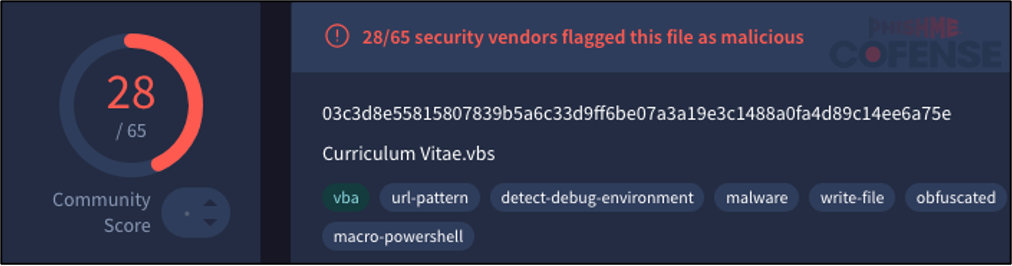
Figure 13: 28 out of 65 detections on VirusTotal for Curriculum Vitae.vbs.
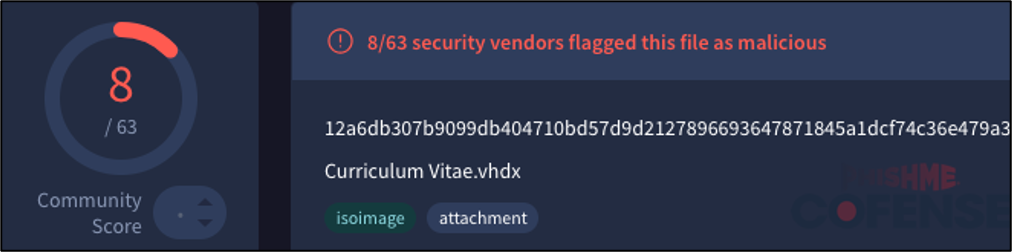
Figure 14: 8 out of 63 detections on VirusTotal for Curriculum Vitae.vhdx which contains Curriculum Vitae.vbs.
To add one more challenge to detecting malicious virtual hard drive files, threat actors can easily manipulate the file hash for virtual hard drive files by adding unnecessary filler files along with the malicious payload, similar to how the file hash for archive files can be manipulated.
However, threat actors can additionally manipulate the file hash for virtual hard drive files by changing the file format in which the hard drive file is stored or changing the amount of storage space that is allocated. Referring back to Figures 10 and 11, note how the same EICAR test file produces two different file hashes when placed in a .vhd file versus a .vhdx file.
Both of these virtual hard drive files were created with 100MB of storage space allocated. However, when creating a similar .vhd file containing the EICAR test file but with 20MB of storage space allocated, the resulting .vhd file produces a different file hash as noted in Figure 15.
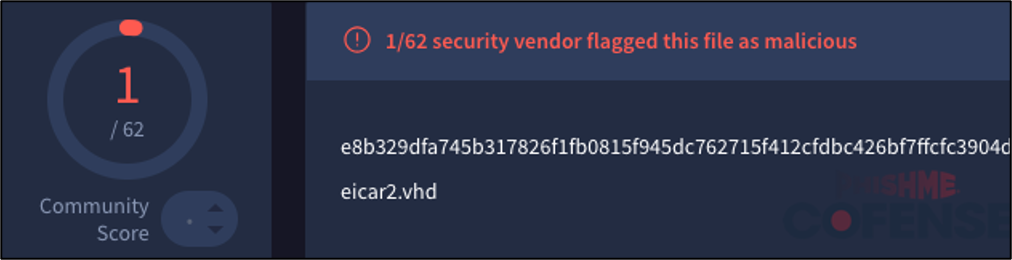
Figure 15: 1 out of 62 detections on VirusTotal for an EICAR test file within a 20MB .vhd file.
Execution via AutoRun and AutoPlay
AutoRun is a Windows functionality that allows for mounted volumes to automatically take actions when mounted, though its malicious capabilities are heavily mitigated in modern versions of Windows. Assuming Windows Registry settings are set to enable AutoRun, the autorun.inf file in the root of a mounted volume lists tasks to perform automatically.
While many of the abusive capabilities such as silently executing malicious programs without user interaction are removed in Windows Vista and above, older versions of Windows are still susceptible to malicious AutoRun tasks.
Additionally, versions of Windows up to Windows Vista can still prompt users to manually run a specified malicious payload via a popup handled through AutoPlay, a similar system that gives user-selectable actions to take on a mounted volume.
In the case of these virtual hard drive files, the autorun.inf configuration file attempts to run the malicious script or executable contained within the virtual hard drive. However, if AutoRun is not enabled or if the victim is using a relatively modern version of Windows where AutoRun is not able to automatically execute programs for virtual hard drives, the victim will still be able to browse through the mounted virtual hard drive and run the payload manually.
Figure 16 shows the contents of the autorun.inf contained within Curriculum Vitae.vhdx. In older versions of Windows this configuration will automatically execute SpecificationRequirement.vbs with wscript.exe or prompt the victim to “Run VBScript” via an AutoPlay popup. However, the sample does not provide a SpecificationRequirement.vbs file.
This was likely a leftover from a previous campaign that was not updated.
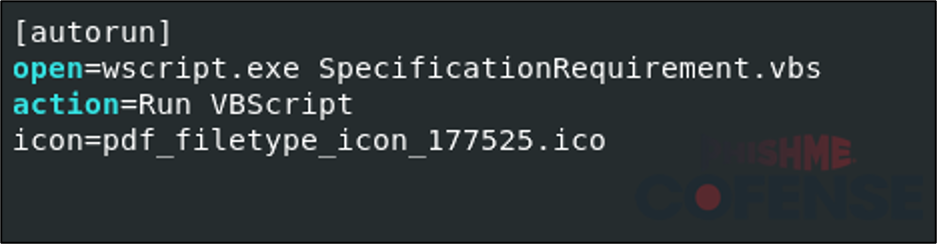
Figure 16: autorun.inf found within Curriculum Vitae.vhdx.