By: Max Gannon
Through the first six months of 2023, our Intelligence team has seen alarming changes in the email security and phishing landscape. Most notably, compared to both Q1 and Q2 of the previous two years, HTML attachments used in malicious phishing campaigns have increased dramatically, 168% and 450%, respectively. This report will focus on some of the significant changes in tactics in email security, compared to what we observed in 2022, and includes insights on:
- Web3 Services Abused in Credential Phishing
- Emotet and QakBot Updates
- Predictions for the rest of 2023
HTML Attachments Used in Malicious Email Campaigns
The high volume of HTML attachments observed in malicious email campaigns towards the end of 2022 continued in the first several months of 2023. The volume peaked in February 2023 with an 11% increase over the next highest volume seen in 2022.
Thanks to this dramatic increase, the first 6 months of 2023 had 168% higher volume than the first 6 months of 2022, and a 450% higher volume than 2021.
Over the next four months, the volume of HTML attachments seen in malicious email campaigns continued to decrease to the levels seen in 2022 and 2021. During this time, several campaigns with a small number of sophisticated HTML attachments that were good at avoiding detection and resistant to automated analysis were seen in the wild.
Although the decreasing volume mid-year may be part of the same trend seen in 2021 and 2022, part of it is likely due to the small number of campaigns with more sophisticated HTML attachments taking the place of multiple low sophistication campaigns seen in the past.
Figure 1: Use of HTML Attachments in Malicious Email Campaigns for the First 6 Months from 2021-2023
Figure 2: HTML attachment files seen in malicious email campaigns from 2021 to mid 2023.
Web3 Services Abused in Credential Phishing Campaigns
Amongst the changes to the top Web3 services abused in credential phishing, the biggest changes are the abandonment of fleek[.]co and siasky[.]net as abused Web3 services. In a December 2022 post, fleek[.]co said they were decommissioning storage APIs, which includes the domain “storageapi2[.]fleek[.]co”.
This domain was responsible for most of the fleek[.]co domains seen in credential phishing leading to the significant (37%) drop off in usage. This took fleek[.]co from the top Web3 service abused in phishing to the 3rd. In August 2022, the closure of Skynet Labs was announced leading to the shutdown of siasky[.]net, which depended on Skynet Labs leading to no usage of siasky[.]net in 2023. With the first and second place Web3 abused services of 2022 gone, the third place ipfs[.]io took over to become the top Web3 service abused in phishing with a 33% lead over second place.
This demonstrates how volatile hosting services can be and why takedowns of credential phishing resources can be ineffective as the threat actors simply switched to ipfs[.]io and did not appear to scale back operations.

Figure 3: All of 2022 top Web3 services abused in phishing.
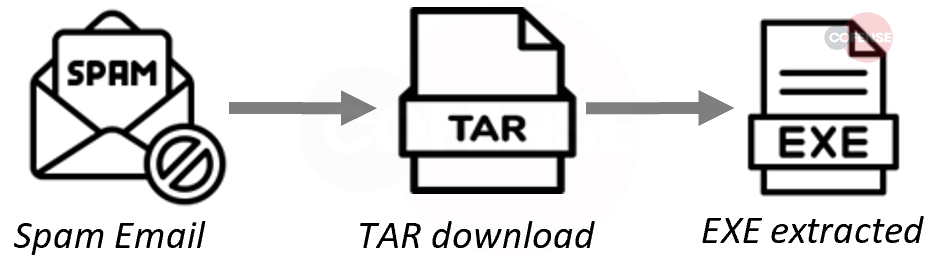
Figure 4: First 6 months of 2023 top Web3 services abused in phishing.
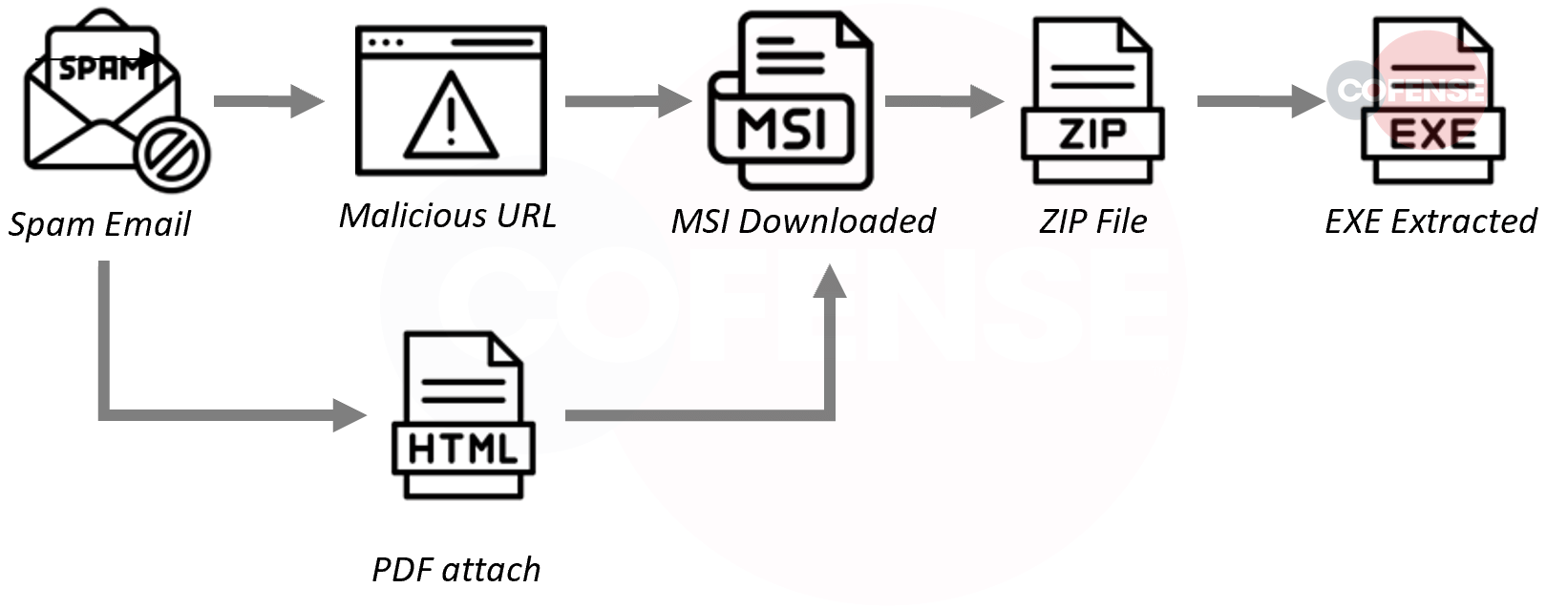
Figure 5: Change in Web3 domains abused in credential phishing from 2022 to the first 6 months of 2023
Emotet and QakBot
Although the top Web3 services abused in credential phishing and the use of HTML attachments for malicious email campaigns were major changes, there were also more minor changes driven by Emotet. Included in the minor changes was a decrease in the previously popular Office macros and LNK downloaders due to Emotet delivery via said mechanisms dropping off.
In place of Office macros and LNK downloaders, WSF downloaders and OLE package objects (taking the form of .one files) became popular as they were used to deliver large amounts of QakBot and most of the Emotet seen in 2023.
Predictions for the rest of the Year
Tailored Content Makes Phishing Emails More Effective At Scale
This year we have seen remarkable developments in phishing emails tailored specifically for targeted users or organizations. The operators responsible for the prolific SuperMailer-generated credential phishing campaigns used the software’s template features to automatically craft emails featuring users’ email addresses and organization names.
Other threat actors generated unique images in each email, with similar user details rendered within the image. As threat actors hone their techniques, expect a greater level of detail in tailored phishing emails, even in high-volume campaigns.
Phishing Services Struggle to Maintain Momentum Under LE Pressure, Some Succeed
Individuals or small-scale operations dealing in credential phishing may be under increasing pressure from law enforcement and market forces. Authorities dismantled several notable threat actor marketplaces recently, including the Genesis Market in April and Breach Forums in late March. Without them, small operations will have a harder time connecting with customers. At the same time, certain prominent credential phishing services remain operational.
Our recent Strategic Analysis highlighted the Caffeine service still running, although they no longer maintain a public website. Another service we’ve investigated, BulletProftLink, continues to run openly, apparently unconcerned with potential exposure to authorities.
Smaller operators may also have trouble matching the features offered by established credential phishing services, including tailored email content, bulletproof hosting, multi-factor authentication capture, and easy-to-use management of campaigns. In the long term, the legal risks and barriers to entry could drive credential phishing operators into more centralized, organized teams akin to the Conti ransomware organization.
Use of Malicious PDF Attachments to Continue Growth
The past two years have seen growth in the number of PDF files among malicious file attachments, from 15% in Q2 2021 to over 40% every quarter since Q2 2022. PDF documents have several features that make them attractive as a delivery mechanism for malware or malicious links:
- PDFs can include images and formatting to make them appear more legitimate, which can be difficult to accomplish with content embedded directly in emails.
- Automated analysis of PDF files is more complicated than analysis of raw email content. Obfuscation, password protection, and other measures can further thwart defenses.
- In a business setting, legitimate PDF attachments are common, making malicious ones more likely to avoid detection.
The operators of QakBot have been quick to experiment with and adopt different delivery mechanisms in the past several months. Going forward, look for other threat actors to follow their lead.