By: Max Gannon, Intelligence Team
Cofense Intelligence relies on over 35 million trained employees from around the world, and a considerable number of analyzed campaigns are written in languages other than English. This report focuses on the URLs embedded in emails that bypassed email security controls like secure email gateways (SEGs) to deliver malware.
The URLs that are the focus of this report are commonly referred to as “infection URLs” as they are the source for an infection by malware. Infection URLs, especially the services hosting them, are important as they represent the first step in a chain of events that can be broken with proper preparations and tools.
This report is part of a series of reports covering different trends in phishing campaigns that are delivered by the top five non-English languages that Cofense sees. Other topics include the malware families and delivery mechanisms seen in different languages, as well as the themes seen in various languages.
Languages Chosen
Within the two-year time frame of this report, there were campaigns in 24 different languages that bypassed SEGs to deliver embedded URLs that led to malware. Unfortunately, covering all of them would require more space than is feasible. As a result, the top five by volume were chosen to be featured.
Those languages were Spanish, Thai, Chinese, Portuguese, and German. Although the volume of these five could be compared and used to make claims about the volume of phishing campaigns against a specific language, that would be inaccurate, as the individual shares of the whole are more likely to represent the distribution of customers reporting emails and a broad-scoped collection area bias rather than a pattern of activity.
As a result, the specific volumes of each language will not be compared, but several trends within each language will be examined. It is important to note that language can often be taken as an indicator of regionality. For example, the vast majority of German-language campaigns were received by individuals in Germany. Spanish and Portuguese-languages campaigns can be a bit more varied in terms of recipient location, but when it comes to this report, it is safe to assume that the majority of campaigns in those languages were focused on Latin America rather than Europe.
In other reports on non-English language campaigns, French or Italian qualified as being in the top five based on the volume of campaigns in the type specified by the report. When it comes to campaigns that make use of infection URLs rather than attachments, French and Italian do not place in the top five by volume. Instead, Thai-language campaigns are significantly more popular than French or Italian when it comes to utilizing infection URLs to deliver malware.
This may indicate that threat actors targeting Thai-language victims believe them to be more susceptible to embedded links than attachments.
Infection URLs
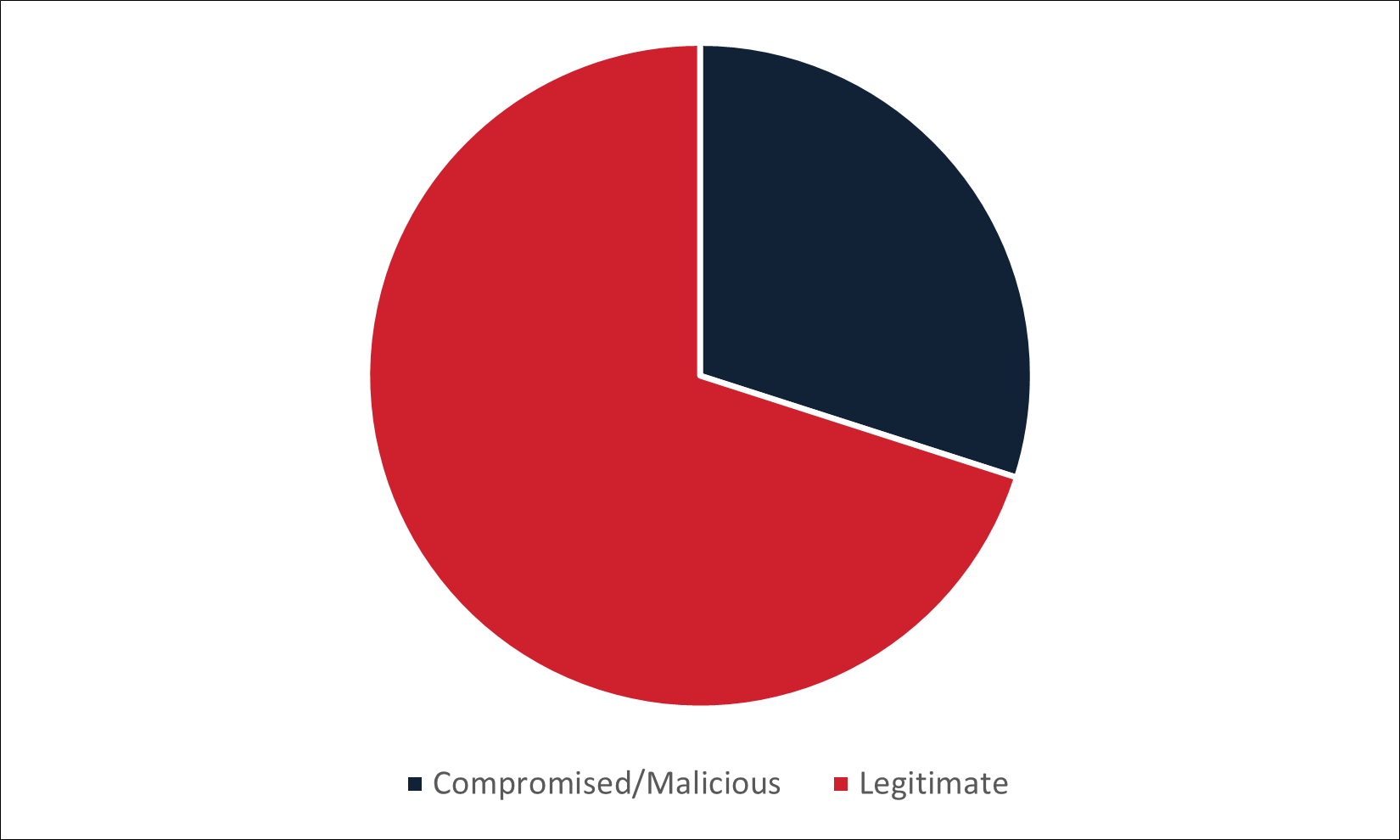
Figure 1: Type of infection URL used to deliver malware in the top five non-English email campaigns delivering malware via embedded URL.
Infection URLs are the first step in a chain of events leading to an infection by malware. They are embedded in emails and represent the first action that a victim must take to become infected. Infection URLs are distinct from URLs embedded in attachments, such as PDFs, because recipients must first interact with the attachment before clicking a link.
As seen in Figure 1, legitimate services account for the majority of infection URLs seen across the top five languages. Although these URLs often lead directly to a file download or intermediary service with a link to a file download, sometimes legitimate redirect services, such as bit[.]ly, are used. Additionally, legitimate services may also be used as an intermediate step to host documents with links to the next stage in the chain. Both redirection and intermediate services are also tracked as infection URLs, as they are part of a chain that leads to malware.
The malware files, intermediary steps, and redirects that are delivered by infection URLs are typically hosted on a source that is compromised, threat actor controlled, or on a legitimate service that is being abused. While the compromised hosts once dominated as a source of malware, this has become less common recently.
As threat actors have advanced their abilities to obfuscate whether a host is compromised or wholly owned by a threat actor, it has become increasingly difficult to differentiate between the two. One of the most historically useful tools for determining domain legitimacy, domain registration date, can no longer be considered as valid, as discussed in another Strategic Analysis Immunity Evasion: Defeating Security with Active Measures & Long-Lived Domains.
For the purposes of this report, the domains hosting the malware, redirecting to it, or serving as intermediary steps leading to it, will be considered to be an abused legitimate service or a compromised/malicious domain. The focus of this report will be on the domains and services that are part of an infection chain leading to malware.
Legitimate Services and Domains
The line between a legitimate service and a malicious one can sometimes be difficult to determine. For the purposes of this report, the general consensus of intelligence services and the service offered for each domain were considered rather than the domain age or other increasingly unreliable indicators, such as registrar or other WHOIS information.
Domains such as anonymfile[.]com were categorized as malicious because, although they claim to be legitimate, the anonymous nature of their service and their implementation of “Jurisdictional Restrictions”, which can be easily used to ensure law enforcement is unable to access content, indicate that the service is likely intended to be abused by threat actors or caters to an audience with significant overlap with threat actors.
Several of the more well-known legitimate services include OneDrive, Dropbox, MediaFire, Discord, Google services such as Docs and Drive, GitHub, and WeTransfer.
Compromised or Threat Actor Controlled Hosts
The most common hosts within this category are those that were created by threat actors. These are frequently designed to appear legitimate at first glance, such as nota-fiscal[.]org. In other cases, malicious subdomains were created on legitimate domains such as jusbrasil-combr[.]processos[.]site.
The base domain, processos[.]site, has been around for 4 years and appears legitimate, but the subdomain, jusbrasil-combr, is designed to appear as if it were jusbrasil[.]com[.]br, an often used and legitimate website. Spanish-language campaigns saw the most abuse of domains and subdomains designed to appear legitimate, but all featured languages were subject to some amount of domain impersonation.
Spanish-Language Email Campaigns Delivering Malware via Embedded URL
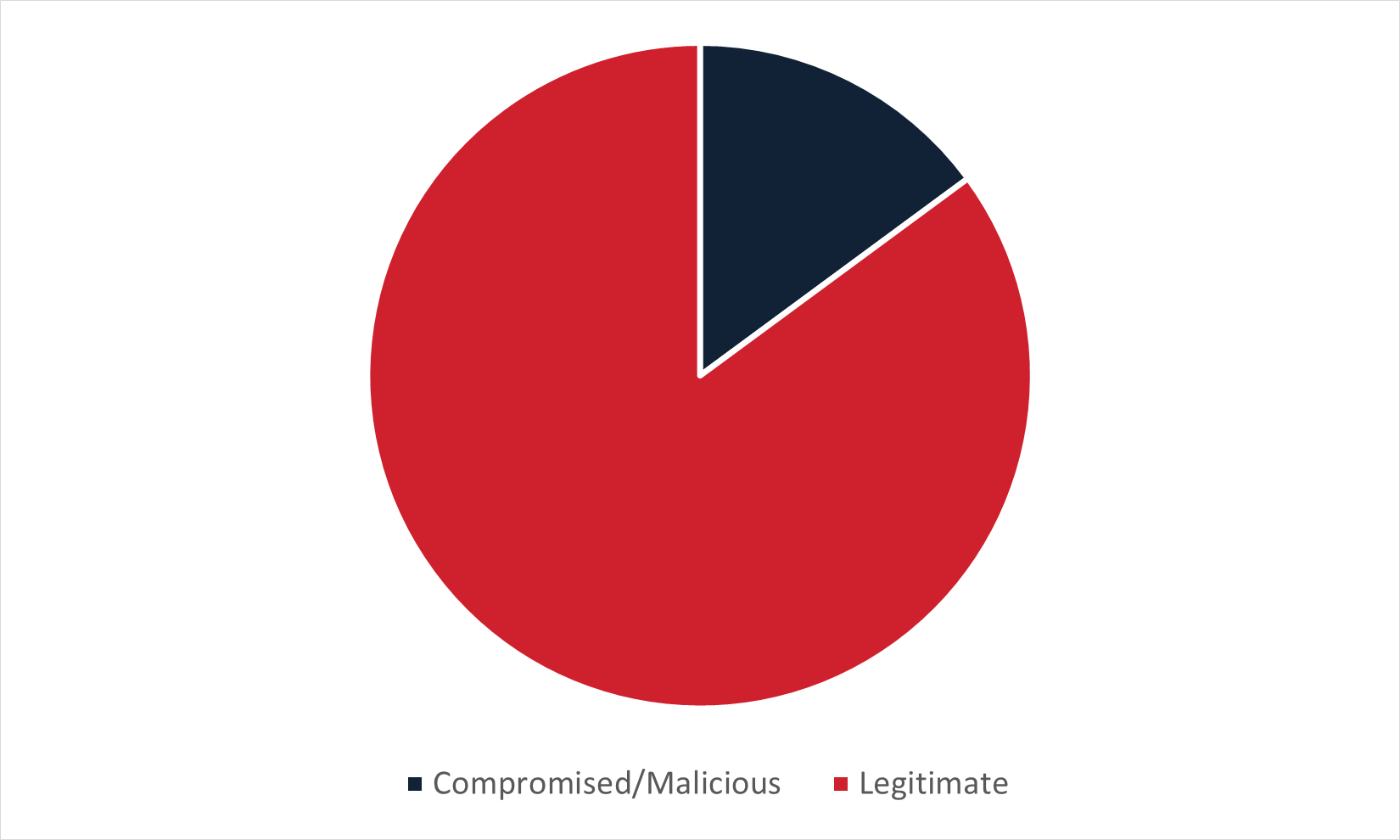
Figure 2: Type of infection URL used to deliver malware in Spanish-language email campaigns delivering malware via embedded URL.
Spanish-language email campaigns delivering malware stayed with the general trend of utilizing primarily legitimate domains and services. The most commonly abused domain was docs[.]google[.]com, followed closely by drive[.]google[.]com. Overall, 62% of the domain names delivering or leading to malware belonged to Google services.
Although there were a comparatively small number of compromised or created domains delivering malware, several domains that were carefully crafted to appear legitimate stuck out, including denunciadigital-gobmx[.]com and avisojudicial[.]org. The malware most commonly delivered in these campaigns was Remcos Remote Access Trojan (RAT).
In fact, Remcos RAT made up 42% of all malware families seen in these types of campaigns and was seen being delivered in all top five languages. The most common legitimate domain leading to malware that was seen in Spanish-language email campaigns is docs[.]google[.]com, and the most common malicious or compromised domain was ###[.]###].]###[.]host[.]secureserver[.]net (Where ###[.]###].]### is an IP address).
Thai-Language Email Campaigns Delivering Malware via Embedded URL
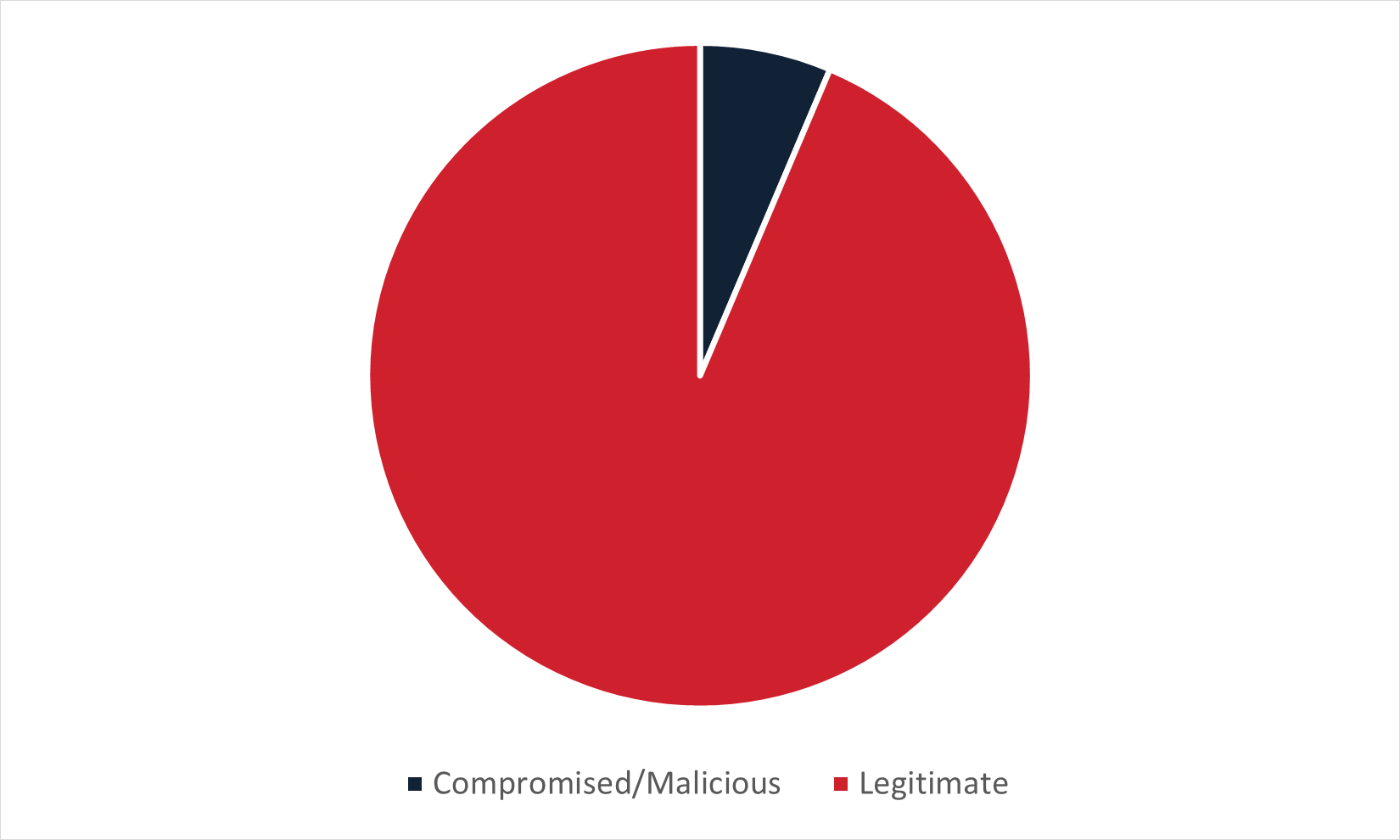
Figure 3: Type of infection URL used to deliver malware in Thai-language email campaigns delivering malware via embedded URL.
In line with overall trends, Thai-language campaigns typically made use of legitimate domains to deliver malware. The most commonly abused service in these campaigns is Dropbox, followed closely by MediaFire and Google. Much like Spanish-language emails, Remcos RAT was a popular malware delivered in these campaigns.
However, in this case, Loda was tied with Remcos RAT for first place, with each taking up roughly 29% of the delivered malware. Thai-language campaigns were, similarly to most non-English campaigns, primarily Finance-themed. However, most of the abuse of Dropbox occurred with Copyright-themed campaigns.
The most common legitimate domain leading to malware that was seen in Thai-language email campaigns is drive[.]google[.]com and the most common malicious or compromised domain was ccrhs[.]shop.
German-Language Email Campaigns Delivering Malware via Embedded URL
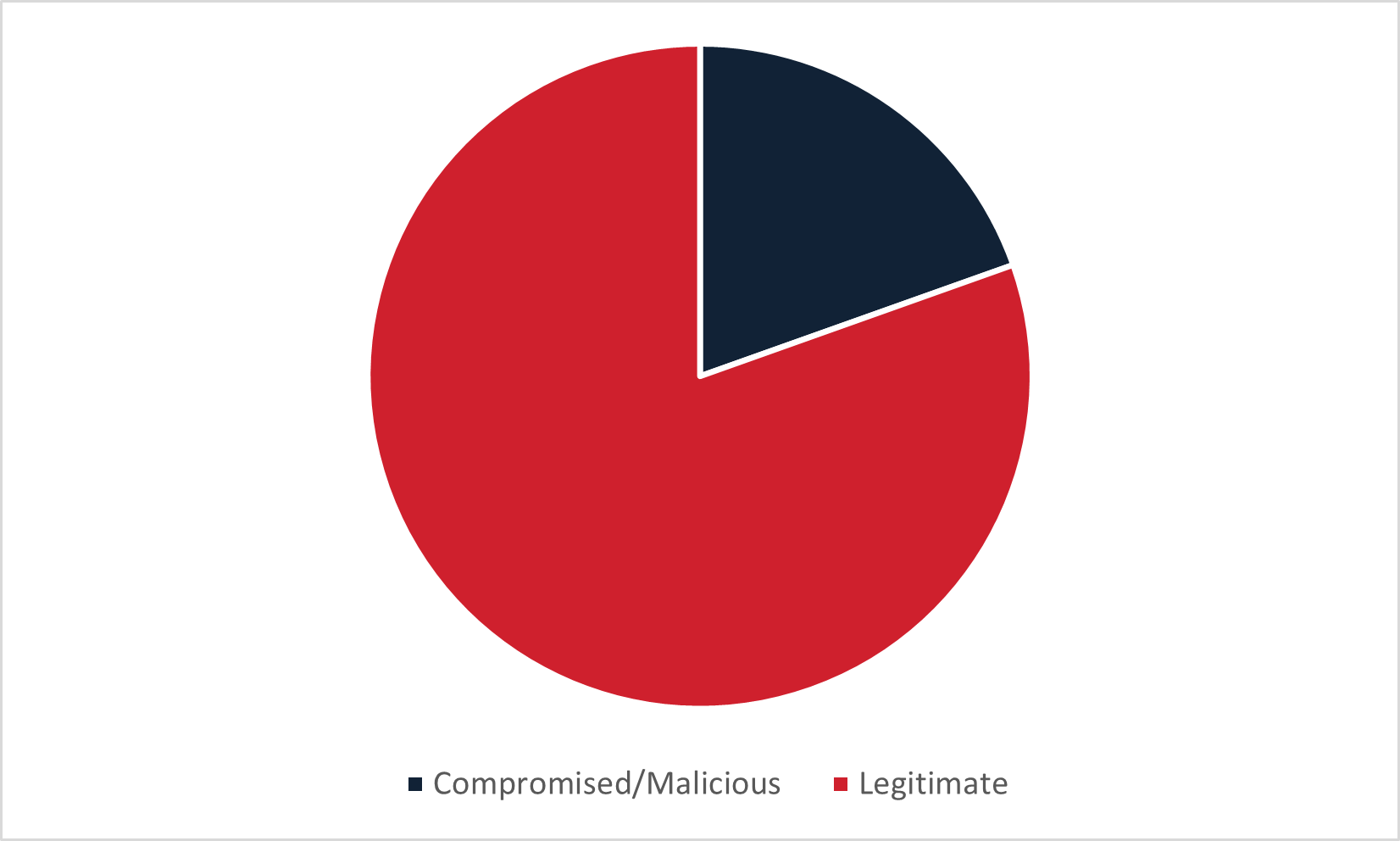
Figure 4: Type of infection URL used to deliver malware in German-language email campaigns delivering malware via embedded URL.
German-language campaigns delivering malware stayed with the general trend of utilizing primarily legitimate domains. The most commonly abused legitimate service was Dropbox. Overall, 68% of the domain names delivering malware belonged to Dropbox services. Unlike other languages, German did not have a single associated .de country code Top Level Domain (ccTLD) amongst the malicious or compromised domains used to deliver malware.
German-language emails primarily delivered RATs, in particular delivering up to four different malware families at a time. The most commonly delivered malware family was XWorm RAT, which accounted for 28% of all German-language infection URLs delivering malware. The most common theme among German-language campaigns was Finance with a correspondingly large amount of Dropbox abuse being used to deliver multiple RATs.
The most common legitimate domain leading to malware that was seen in German-language email campaigns is dropbox[.]com and the most common malicious or compromised domain was a tie between datei-online[.]geodezja[.]lublin[.]pl and datei[.]mylocoltd[.]co[.]ke.
Chinese-Language Email Campaigns Delivering Malware via Embedded URL
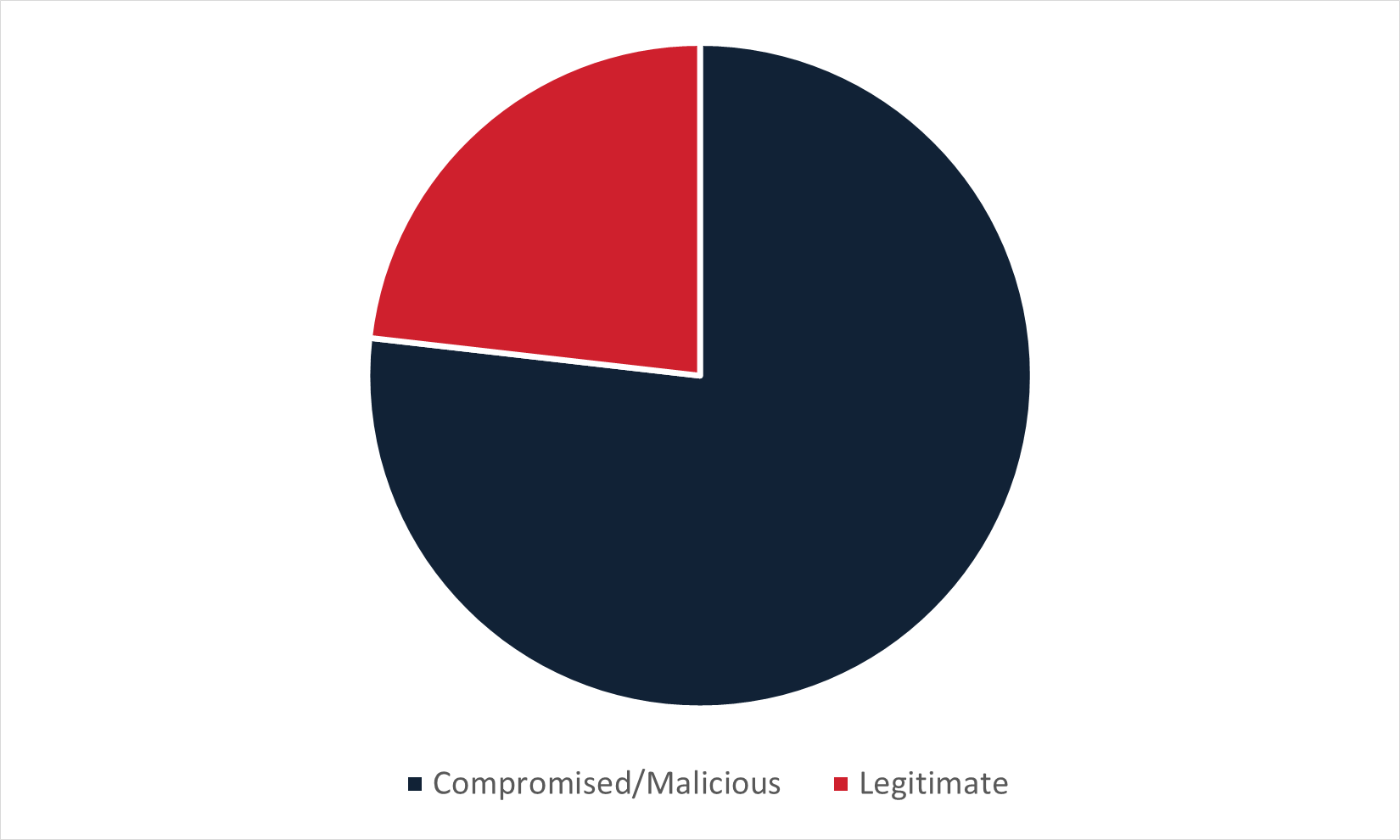
Figure 5: Type of infection URL used to deliver malware in Chinese-language email campaigns delivering malware via embedded URL.
Chinese-language campaigns were one of the outliers in that domains in these campaigns were far more often compromised or malicious rather than legitimate. Because the domains were more often compromised or malicious, Chinese-language campaigns also demonstrated an unusual trend in domain names: A large number of domains delivering malware made use of the ccTLD primarily associated with the Chinese-language, .cn. In fact, .cn ccTLD domains made up 32% of all malicious or compromised domains delivering malware in Chinese-language campaigns.
These campaigns also had a marked trend towards delivering the KrBanker malware family. This makes sense as KrBanker is known for targeting Chinese-language victims. In fact, KrBanker was delivered in Chinese-language campaigns 94% of the time, showing an extreme targeting preference only found in Portuguese-language campaigns.
Other malware that exclusively targeted Chinese-language victims include Ghost RAT, Gooxion RAT, HackBrowserData, NSecRTS, Rust Dog, and Yangtu RAT. The most common legitimate domain leading to malware that was seen in Chinese-language email campaigns is myqcloud[.]com and the most common malicious or compromised domain was luynhk[.]com.
Portuguese-Language Email Campaigns Delivering Malware via Embedded URL
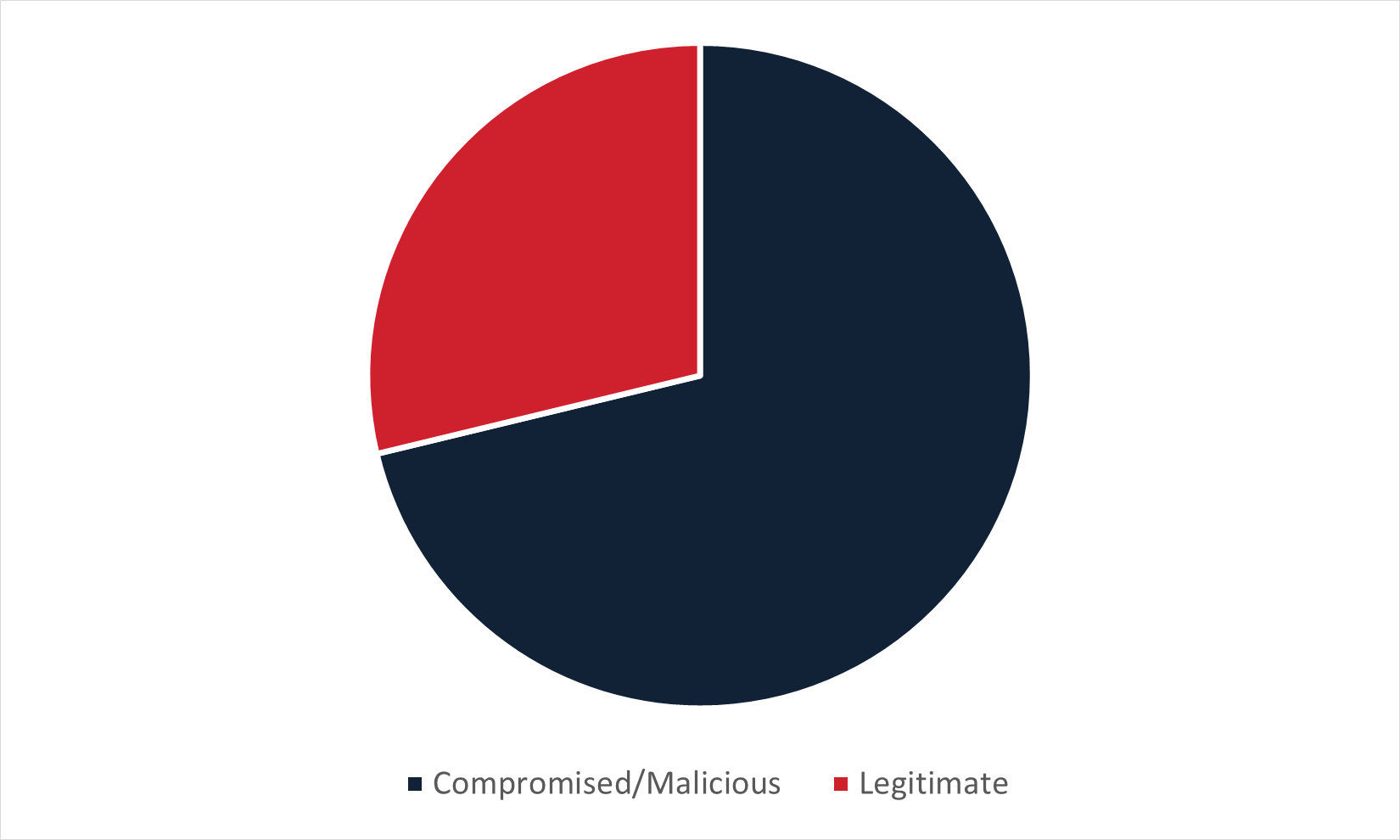
Figure 6: Type of infection URL used to deliver malware in Portuguese-language campaigns delivering malware via embedded URL.
Portuguese-language campaigns were the second outlier in that domains in these campaigns were far more often compromised or malicious than legitimate. Unlike Chinese-language campaigns, Portuguese-language campaigns did not have a high number of ccTLDs delivering malware.
In fact, the ccTLD most often associated with Portuguese (.com.br) made up only 6% of compromised or malicious domains delivering malware in these campaigns. Amongst the abused legitimate services, Amazon AWS made up 22% but it only made up 6% when looking at the language overall. What made Portuguese-language campaigns stand out, however, was the fact that they saw a high number of malware families delivered almost exclusively (95% or more) in Portuguese.
These families include: PeepingTile, N-Able, Lampion Banking Trojan, Atera, Janela RAT, Carnaval Heist, and Astaroth. Portuguese also saw an unusually large spread of malware delivered via an infection URL, with almost double the number of unique families seen in German-language campaigns delivering malware via infection URL.
The most common legitimate domain leading to malware that was seen in Portuguese-language email campaigns is amazonaws[.]com and the most common malicious or compromised domain was ###[.]###].]###[.]host[.]secureserver[.]net.
Conclusion
Phishing attacks aren’t just in English anymore. Cybercriminals now use multiple languages to lure people into clicking URLs or opening malicious attachments. Phishing attacks that deliver malware increasingly exploit multiple languages to broaden their reach. Cofense
Intelligence identified the top 5 high-volume languages used in such attacks: Spanish, Thai, German, Chinese, and Portuguese. By tailoring the phishing content to these languages, attackers increase the likelihood of deceiving users located internationally. These insights emphasize the need for multilingual cybersecurity measures, including user training, email filtering, and threat intelligence, to effectively mitigate phishing attacks.