Author: Kahng An, Cofense Intelligence
The Cofense Phishing Defense Center (PDC) and Cofense Intelligence recently identified a LinkedIn-spoofing malware campaign delivering ConnectWise RAT. The email purports to be a notification for a LinkedIn InMail message, a feature for messaging LinkedIn members who are not connected to the sender. While not entirely accurate to current legitimate LinkedIn emails, the spoofed email from this campaign features heavy use of LinkedIn brand assets to make the email seem legitimate.
Key Takeaways
- While LinkedIn is a commonly spoofed brand for credential phishing emails, this campaign delivered ConnectWise RAT instead of credential phishing or BEC.
- This sample was found on an environment protected by Microsoft Defender for Endpoint (formerly known as Microsoft Defender ATP).
- The “Read More” and “Reply To” buttons featured in the email deliver an embedded link to the ConnectWise RAT installer.
Campaign Structure
The email for this campaign is tailored to spoof a LinkedIn InMail email notification from a sales director asking for a quote on a product or service. The email itself is notable for mimicking LinkedIn emails well, though it uses an older email template style that was used prior to LinkedIn’s new UI and branding updates in 2020. At a glance, the email is convincing for those who used LinkedIn prior to the UI refresh.
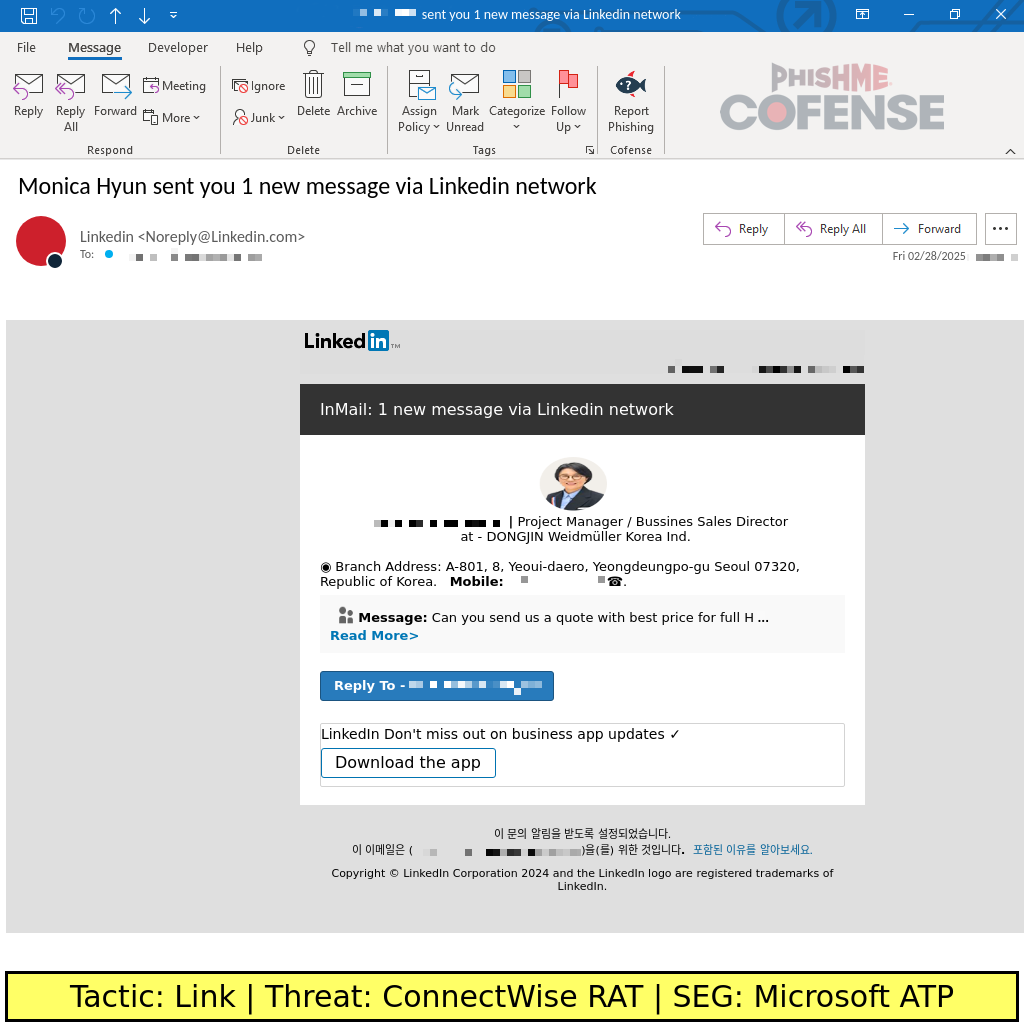
Figure 1 - The campaign email: For recipients who used LinkedIn prior to its rebranding in 2020, this email would look convincing.
Notably, the supposed project manager/sales director who sent the message does not seem to be a real person, and the attached photo is simply named “executive16.png”. The photo belongs to a real individual, Cho So-young, who is the President of the Korean Society of Civil Engineering Law. The purported company “DONGJIN Weidmüller Korea Ind.” does not seem to be a real company either, though it combines the names of two legitimate corporations. The listed address points to a real corporate office building, though the purported company does not exist.
By sending the email from a supposed business director and asking for a sales quote, the threat actors attempt to create a sense of urgency to quickly respond to the email. However, clicking on the “Read More” or “Reply To” buttons will download a ConnectWise RAT installer. Notably, the “Download the app” button on the email does not lead to any embedded links. Typically, threat actors would use embedded links with text prompting users to “download” or “run” a file, though this sample does not use this tactic. The threat actors do not prompt the user to run a program in the email, and well-trained users should be suspicious of running a downloaded file when they would normally expect to be directed to a LinkedIn webpage.
When looking at the email security headers for this sample, SPF (Sender Policy Framework) was marked as a softfail because the sender’s IP address is not permitted to send emails using the Linkedin.com domain.
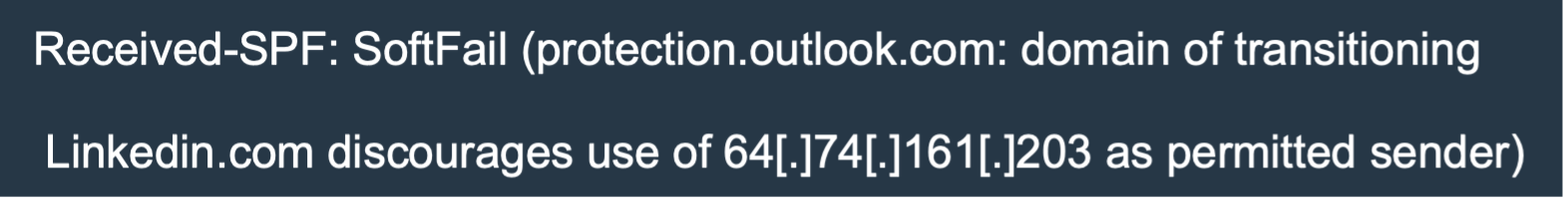
Additionally, the email was not signed with DKIM (DomainKeys Identified Mail) when legitimate LinkedIn emails are signed with DKIM for email authentication purposes.
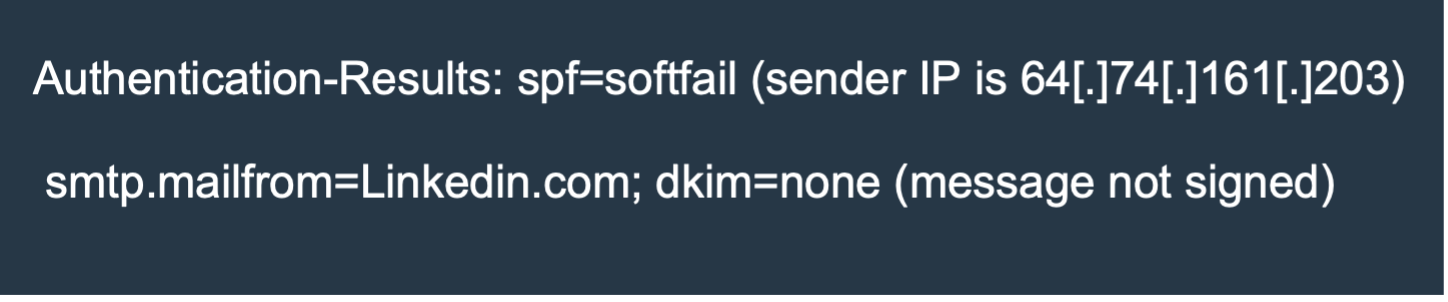
Despite these security measures flagging the email as a likely spoofed email, the email was able to bypass existing security measures and the Microsoft ATP secure email gateway (SEG) likely because the configured DMARC action was set to “oreject” which will mark the email as spam and let it reach the recipient’s mailbox.
While researching this sample, this campaign was found to exist in the wild as far back as May 2024. While the email template has not changed since then, Cofense Intelligence was unable to confirm whether this campaign was used to deliver ConnectWise RAT in prior samples that were found via open-source intelligence.