By Iris Suaner, Cofense Phishing Defense Center
Found in Environments Protected By:
[SEGs Bypassed: Microsoft EOP, Microsoft ATP, Cisco Ironport, and Proofpoint]
The Cofense Phishing Defense Center (PDC) has discovered a new wave of sophisticated attacks that leverage judicial receipts for legal processes with multiple-layer techniques to distribute and execute SapphireRAT. The threat is particularly focused on organizations across Latin America, where threat actors are targeting industries with valuable data or critical infrastructure. The attack’s complexity lies in its ability to bypass traditional security measures, including email filtering and antivirus solutions, by disguising itself as legitimate communication related to legal matters.
This attack enables threat actors to gain unauthorized access to targeted systems. By embedding the SapphireRAT within seemingly official legal documents, the attackers use social engineering tactics to deceive recipients into executing malicious payloads. Once executed, the SapphireRAT allows the threat actors to conduct a wide range of malicious activities. This advanced persistent threat underscores the need for heightened vigilance, robust security protocols, and awareness within affected sectors.
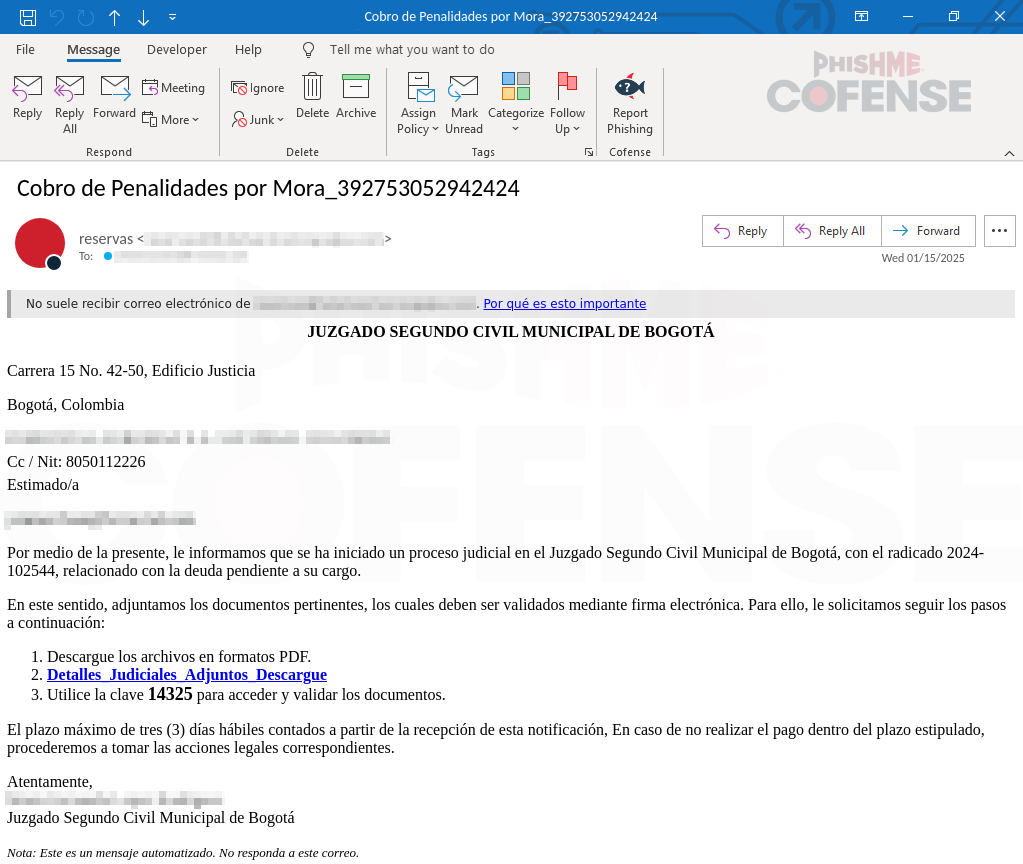
Figure 1: Email body seen during this campaign.
As shown in Figure 1, the email features the subject line “Cobro de Penalidades por Mora,” which translates from Spanish to “Collection of Late Fees,” designed to create a sense of urgency for the recipient. The email body includes details about the impersonated legal office, identified as “Juzgado Segundo Civil Municipal de Bogotá,” or “Second Municipal Civil Court of Bogotá.” It further claims that the court has initiated legal proceedings regarding an outstanding debt owed by the recipient. Additionally, the email instructs the recipient to review and sign the attached documents, reinforcing the fraudulent narrative.
Figure 2: The initial threat vector.
As shown in Figure 2, the threat actor provides detailed instructions on how to review and sign the relevant document which also includes the password to the document, attempting to add legitimacy to the email. However, these instructions include a URL that redirects the recipient to a malicious domain. This domain is specifically designed to host and deliver the malware, furthering the attacker's objective of compromising the recipient's system as shown in Figure 3.
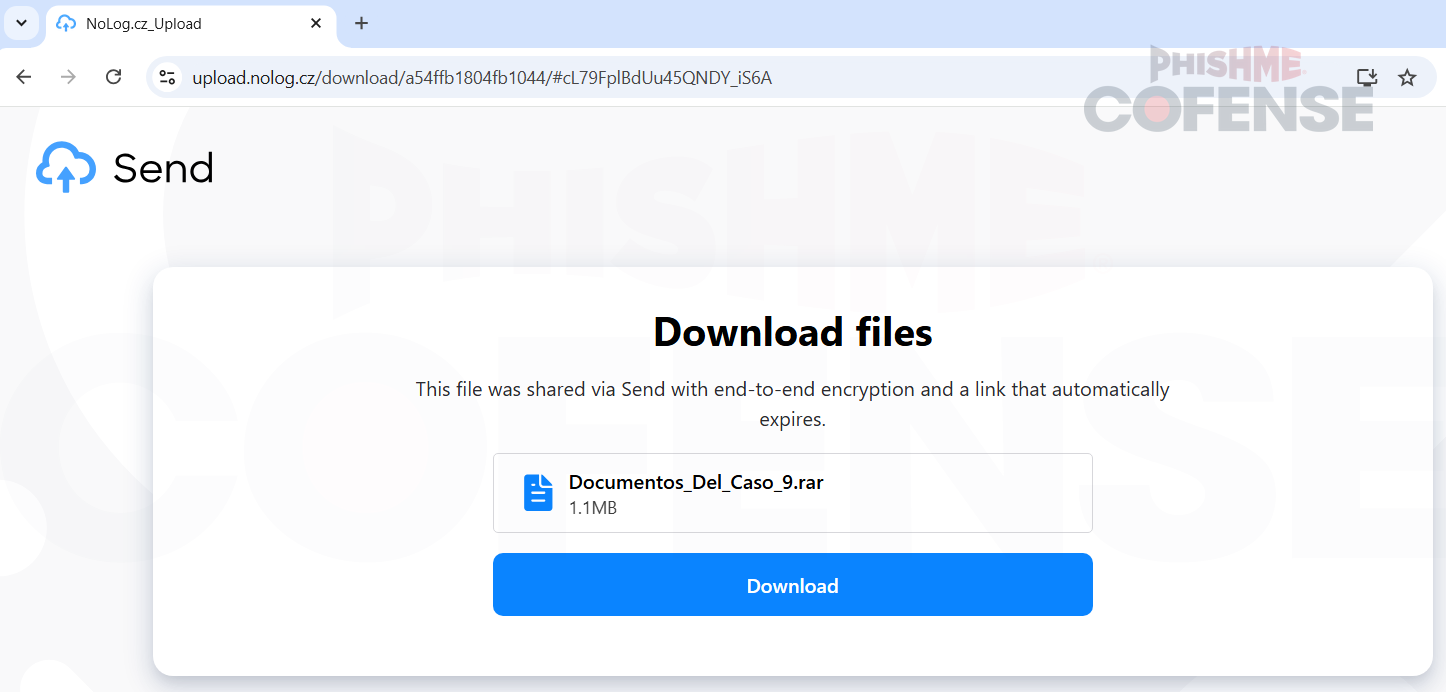
Figure 3: Landing page of the hyperlink to download the payload.
When the recipient clicks on the malicious link, they are redirected to a webpage containing a prominent button labeled as a download. Clicking this button initiates the download of a compressed .rar file, which is automatically saved in the system's default downloads directory. The exact layout of the webpage and the appearance of the download button can be seen in Figure 3, illustrating how the attackers have designed the interface to appear legitimate and entice the recipient to proceed with the download.
Initial Download:
When the button on the webpage is clicked, the download process for a .rar file is triggered. Figure 4 shows the file being downloaded, highlighting the seamless and potentially deceptive nature of the process. The design and behavior of the download button may give the impression of legitimacy, thereby increasing the likelihood of the recipient proceeding without suspicion.
Figure 4: .rar file downloaded to default download directory
As shown in Figure 5, after extracting the .rar file using the password mentioned in the email body, two additional .rar files are revealed.
Figure 5: Extracted payload from the .rar file.
Once the two-part .rar file is extracted, each part contains the same executable file shown in Figure 6. However, if either of the two .rar files is missing, the .exe file cannot be extracted from either of the files.
Figure 6: Executable file payload extracted from the .rar file.
Technical Analysis:
As illustrated in Figure 7, when the SapphireRAT malware is executed, it initiates by performing initial setup tasks. These tasks include unpacking itself and identifying a suitable target process for code injection. Following this, SapphireRAT spawns the legitimate Windows process regsvr32.exe and injects it with a portion of its malicious code. This technique allows the malware to evade detection by disguising its activities within a trusted system process. It will then spawn additional legitimate Windows child processes, powershell.exe and conhost.exe to download and execute additional payloads.
Figure 7: Execution of the file.
Figure 8: Extracted strings in the legitimate Windows process.
Figure 9: Remote connection location of this campaign, located in the strings.
Figures 8 and 9 present the strings extracted from the regsvr32.exe process, revealing key indicators of the malware's activity. These strings provide insights into the behavior and operations of the malware, particularly during the stage where it injects its malicious code into the regsvr32.exe process.
Figure 10: Remote address establishing the connection.
Figure 10 shows the network connection established by the malware, providing details about the endpoint it communicates with, such as the state of the connection and the port it is contacting the address on. The endpoint represents the target server or system that the malware uses for data exchange, command reception, or other malicious activities. This connection serves as a critical link in the malware's operation, enabling it to interact with its command-and-control infrastructure or other external resources.
Figure 11: Additional payload seen in the campaign after initial execution.
As shown in Figures 11 and 12, the malware creates an automated task in Windows Task Schedule that immediately starts a program located in the AppData\Roaming folder. This task is set to run at one-minute intervals indefinitely. Simultaneously, the malware also drops a .drv file in the AppData location to gain elevated privileges and achieve persistence, making it an effective method for conducting long-term and stealthy attacks.
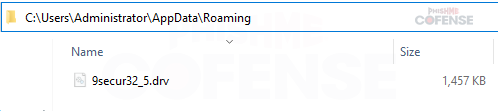
Figure 12: Location of the .drv file being found in the AppData folder.
Conclusion
In conclusion, the threat actor’s use of detailed instructions and a legitimate-looking landing page demonstrates the sophistication of the attack, leading recipients to a malicious domain to deliver malware. This highlights the need for vigilance against phishing attempts, verification of email content and links, and strong cybersecurity practices. Additionally, SapphireRAT poses a significant threat due to its stealth, versatility, and ability to maintain persistent access to compromised systems. Its modular design enables tailored attacks, making it a serious risk. This emphasizes the importance of proactive security measures, including threat detection, system updates, and employee awareness to mitigate such threats.
IOCs
Type | Information |
File Name: MD5: SHA256: Size: | Documentos_Del_Caso_9.rar ddc37a23988a9c86cd4bb0f85a667396 582ca9b2b5b8f8e5f79185f60a6893ec782527e464f037360678fc61e513dcd2 1,104,216 bytes |
File Name: MD5: SHA256: Size: | ad48273605918347192073865182749015637294826479518002.part1.rar 68eacfa360f5936cc121ea64cbafa6d9 d2fbc247f3f5e8bec0f7a282b6ea1a0d650cb86de337a7bd8a4be292f9a7e959 1,000,000 bytes |
File Name: MD5: SHA256: Size: | ad48273605918347192073865182749015637294826479518002.part2.rar 63d7ff161cf9fb13c69e73d95b5f6d32 06c1d2ea250d4c6453675091b1064154068c69ed6f01de7d00f5851d7ac66ba1 101,457 bytes |
File Name: MD5: SHA256: Size: | ad48273605918347192073865182749015637294826479518002.exe e2909ce9f9acf027481cba55c71f8253 da32159b27065337a699264da4778b7c99f8fbb4f00617061b9a5b5397bd5973 1,224,306 bytes |
URL | IP |
hXXps://upload[.]nolog[.]cz/download/a54ffb1804fb1044/#cL79FplBdUu45QNDY_iS6A | 93[.]185[.]97[.]211 |
Kzh83hfm0eovz7acsnioz[.]duckdns[.]org | 66[.]94[.]121[.]207 |
All third-party trademarks referenced by Cofense whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding the circumvention of end-point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog, are registered trademarks or trademarks of Cofense Inc.