By Alex Geoghagan, Cofense Phishing Defense Center
Many companies around the world have grown to rely on the Microsoft environment for their day-to-day workflow. However, this widespread adoption comes with risks, including the potential for spoofing attacks. The PDC has seen a campaign of phishing emails delivered to multiple customers, targeting Microsoft Copilot. This service functions as a type of Generative AI assistant, similar to many of the functions performed by OpenAI's ChatGPT.
With new services like this, employees may not be aware of what types of emails they should be receiving from the provider. They may not be accustomed to the formatting or appearance of these emails and so, it is easy to imagine a scenario where an employee uses this service for the first time and is sent this spoofed invoice for services, tricking them into clicking on a link.
.png)
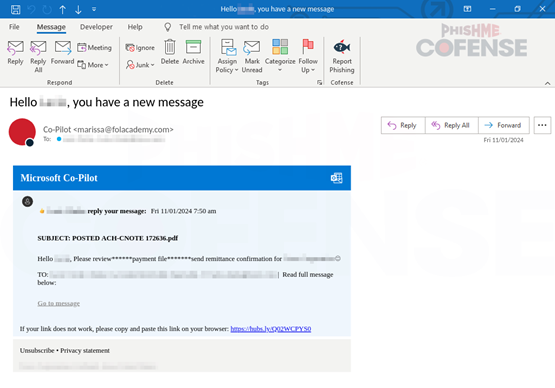
Figure 1: Email Body
Figure 1 shows the email body as it appears to the user. This spoofed email will appear to the user to have come from simply "Co-pilot." Users may have some familiarity with using Copilot to perform a myriad of tasks such as transcribing emails or drafting documents in Microsoft Word. However, Copilot is a relatively new product that launched in 2023. Because of this, users may be unaware of what financial obligations they have to pay for Copilot, and whether their company has provided it to them free of charge, which may lead them to interact with the spoofed invoice contained in this email.
Together with the overall appearance of the email, this may goad a user into clicking on the link and proceeding to the next steps of the phishing email. A particularly keen user may notice at this point that the from address is not an official Microsoft email address, which shouldn’t be included in official communication from Microsoft. Any users who do not notice the discrepancy will find themselves clicking the link and moving on to the next stage of the phishing attempt.
.png)
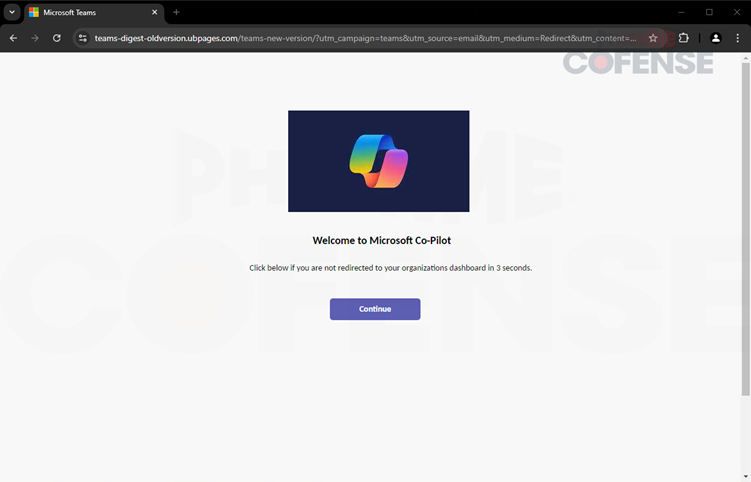
Figure 2: Welcome Page
When the user clicks the link, they will be met with what we see above in Figure 2. The page has been modeled to resemble a welcome page for signing in to Microsoft Copilot. The page leads the user to believe that they are continuing to a payment dashboard, which aligns with the context of the initial phishing email. This page may be convincing to those who have interacted with the product before, since the layout has been spoofed in a pretty accurate fashion. The largest tip that you are looking at an illegitimate page is going to be the URL. A legitimate Microsoft Copilot sign-in should be hosted on “microsoft.com” or a related domain, but this one is hosted on “ubpages.com”.
Figure 3: Phishing Page
Finally, the user will find themselves on a page crafted to look like a Microsoft Copilot login, that asks them for their login credentials (Figure 3). One thing to notice is that it does not provide a section for a forgotten password. This is a common theme in most credential phishing sites because the threat actor cannot facilitate a password reset because it is not a legitimate service, and the threat actor has nothing to steal if the user has forgotten their credentials.
This page makes heavy usage of Microsoft branding. You may notice in the wheel of various Microsoft logos to the left of the sign-in boxes that there is a large variety of Microsoft products here. Microsoft is a very widely used service provider, and this branding makes the spoof appear more legitimate and may lead the user to believe they have exceeded some trial date or otherwise incurred some fee from Microsoft.
.png)
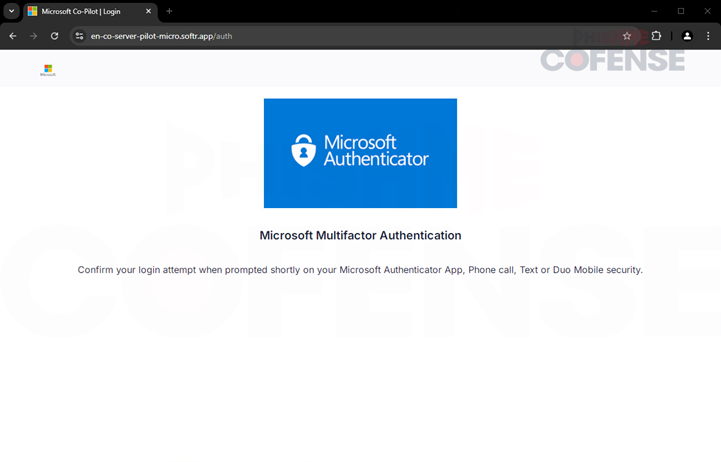
Figure 4: Authentication Page
In the last stage of the attack, we see that the user is redirected to a fake Microsoft Authenticator multi-factor authentication (MFA) page. This page may serve to give the threat actor more time to act on the new credentials they have just stolen. In theory, the user should see this page and think they will receive some type of multi-factor authentication prompt from Microsoft. This small window where the employee is waiting for an MFA prompt may be all the time they need to reliably change passwords or perform whatever tasks that the threat actor would like.
In conclusion, we see above that attackers have taken notice of which products are commonly used by employers across our digital landscape. These new products and services offer employees a new avenue to complete their work but also afford attackers a new vector of attack that needs to be considered. As we introduce new tools—such as Generative AI—it is paramount that we communicate with our various workforces what their obligations are to these services and whether they are provided to them free of charge or will be billed eventually for them. It is helpful for IT or other admins at a company to send out communications with visual representations of what their employees should expect to see and how their interactions with the service might look. By making sure employees are up to date on which products are used in the workplace and how they are being afforded by their employer we can make sure that spoofs like this do not slip through the cracks of our digital environment.
Indicators of Compromise | IP |
hXXp://url4221[.]folacademy[.]com/ls/click?upn=u001.fn1BsYIkFXRWxBLF12AvXicsM-2FsjE9RvnGDoSa-2FG6tyCnLQvgQnf124Cx5EuUZhhTfVR_3c33YtrYFIK9hyz-2F-2BlqzkU2qrdPYA98ZKUQyRf-2BQDoIUlTg3SwnirNuCRwkyv7A4R8qSErob6NGPIKBJj-2B9wc-2BBYea6dhPyUhsBBcVg20UepoQdPSsvQrB0AnxfK-2Bro-2BYxUlR1r8pzfLjpiDlWRXi6c8dnqSmoFoTE5te8qCvIU1M-2FjVV0h3yxBw50XHgm6nHpUeIMxud0B-2FuDgWjadZuyx2rapm5DFmD7tmScsM5YQ9c5klknWkOkAiCoklISM2poWD9GPFqk1QXmDMIz4rMlAxnnnPyURpR5olppJokC6BE4jmcWjYBsZAoCNbn0J14Eqm4igAWaWD2MI1UhY6BeUrHqJA7vXOB63Nr3e7QBW-2BiWRLpvDsQhOH8O3-2Fky-2B3bA-2B3dh-2FUIyzZwsTfw6LPDxVqp4HPNMAuRzric4Qhlg7Sk3RRNm2YOGOjkGmDmZai5rzIQpHiZeFE77SUw6zn6IAECEJl-2Fkx-2F0Ng8wbhp-2BJ43wzSZ2QiAyWwmui2IZy1lpm10XiPkp4Upb0ypkLHYvpF2LusNKpoiMytqgZRUCWMZEptEaH84SvxWcD9p5UKem9ZfLuYCy3usX-2FCRpWdHxwE5p1aKe-2BPZBHrMNpmXqYl-2FB4Tb2iJbzIaaJuu91Cl-2Fxznl5NeKlmdVa1ZyIQw0s38ZkFz4PDSfBFAL033pfldVMHEsPD9S7lK0W1ccfogOGWikeyh6iwQ74vIMpN-2FxSBfWf6gOKZjTRnd8fJniEfN-2BwKUODSDfZ3gxhogzgsTcn0dKGJtS-2BNVxPQszXFHuacWqUGSFD8RjbULqp-2Fho0Qf0HQDm6NuYMOixDA0a4CHAZRrlXokTNQ8Bffw6AtENqDVl7neMZMFQvHzkJ6oXhAcyNA1b7K4wjKJqfpmRNLFNXsp-2FF8-2F5R8AHMMVgEM-2FYjQ-3D-3D
| 167.89.118.95 |
hXXps://en-co-server-pilot-micro[.]softr[.]app/auth | 3.64.247.100 |
hXXps://teams-digest-oldversion[.]ubpages[.]com/teams-new-version/?utm_campaign=teams&utm_source=email&utm_medium=Redirect&utm_content=Co-pilot | 104.18.41.137 |
All third-party trademarks referenced by Cofense whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding the circumvention of end-point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog, are registered trademarks or trademarks of Cofense Inc.