Cofense recently identified and named a new malware called Poco RAT, which is a simple Remote Access Trojan that targets Spanish language victims. It was first observed in early 2024, primarily focusing on companies in the Mining sector and initially was delivered via embedded links to 7zip archives containing executables that were hosted on Google Drive.
The campaigns are ongoing and continue to exhibit the same TTPs. The majority of the custom code in the malware appears to be focused on anti-analysis, communicating with its Command and Control center (C2), and downloading and running files with a limited focus on monitoring or harvesting credentials.
First Seen and Categorized
Poco RAT was first identified and assigned a malware family on 2024-02-07. The strings were used to label the malware as “Poco RAT”. It had all the hallmarks of the campaigns that will be described in this report.
Observed Targeted Sectors
While Poco RAT first targeted customers in the Mining sector, over time this has spread to incorporate four sectors in total as of Q2 2024. A breakdown of the sectors targeted over the course of the campaigns can be seen in Figure 1. It is notable that while there are four total targeted sectors, Mining still makes up the majority of the targets at the time of this report.
Despite the spread of industries, it is important to note that one company was the most targeted, being responsible for 67% of the total volume of these Poco RAT campaigns.
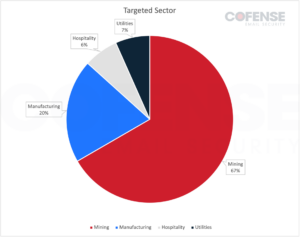
Figure 1: Sectors targeted by email volume in Poco RAT campaigns.
Email Features
The emails campaigns have several consistent features which made identification very straightforward.
- The emails were finance themed, having both a subject and message body indicating as such.
- The language of both the email subject and message body was Spanish.
- The emails either contained a link to a 7zip archive hosted on Google Drive or delivered a file with a link embedded inside the file to download a 7zip archive hosted on Google Drive.
A sample of what most of the emails look like can be seen in Figure 2.
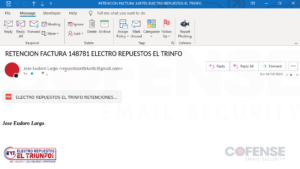
Figure 2: Email seen delivering Poco RAT via a Google Drive link embedded within image in the email body.
Delivery Methods
The file eventually delivered by each of the emails is a 7zip archive containing an executable. The archive could be delivered in three different ways. The first, and most common, way is via a Google Drive URL that is embedded directly in the email. As seen in Figure 3, this accounted for 53% of the emails.
The second most common way was via a link embedded in an HTML file which was observed 40% of the time. The HTML file could be either attached or downloaded via another embedded link which was also hosted on Google Drive. Finally, an attached PDF could contain a link to download the archive from Google Drive.
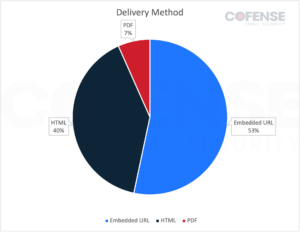
Figure 3: Delivery method of 7zip archives by email volume in Poco RAT campaigns.
URL Embedded in Email Body
The most commonly seen method of delivery was a Google Drive URL embedded in the email body which downloaded a 7zip archive containing an executable. An example of an email with this tactic can be seen in Figure 2. Threat actors often use legitimate file hosting services such as Google Drive to bypass Secure Email Gateways (SEGs) and this tactic has been seen in use by many different threat actors and APT groups over the years.
Downloaded HTML
The second most commonly seen method of delivering Poco RAT was HTML files with a 40% share. Specifically, emails would have a Google Drive link embedded in them which would lead to downloading an HTML file. The HTML file, shown in Figure 4, would then provide a link that would then download a 7zip archive containing the Poco RAT executable.
This tactic would likely be more effective than simply providing a URL to directly download the malware as any SEGs that would explore the embedded URL would only download and check the HTML file, which would appear to be legitimate.

Figure 4: Contents of a downloaded HTML file with an embedded Google Drive link to download Poco RAT.
Attached PDF
The final, and most rare, method of delivering Poco RAT was via an attached PDF file at only 7% of all emails. An example of one of these PDFs can be seen in Figure 5. The PDF file contained an embedded Google Drive link which would, as usual in this campaign, download a 7zip archive containing the Poco RAT executable.
Despite being the rarest form of delivery, using an attached PDF with an embedded link rather than a link embedded directly in an email is actually the most successful method of bypassing a SEG based on analysis of similar campaigns. This is because SEGs typically consider PDF files to be non-malicious and, if properly managed, a PDF file can have embedded URLs hidden from scanning methods.
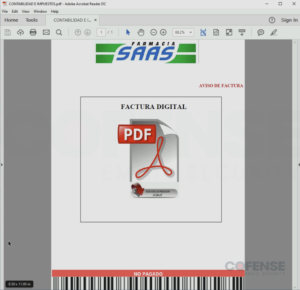
Figure 5: Attached PDF file with an embedded Google Drive link to download Poco RAT.
Malware Features
Detection Rates
The use of extensive metadata is likely in an attempt to bypass Anti-Virus (AV), however, with an average detection rate of 38% for the executables, it is unlikely to have succeeded. The detection rate for the archives is lower but still substantial at an average of 29% while none of the delivery mechanisms used were detected by any AV when they were first submitted to VirusTotal.
Not only did the executables face significant detection rates but their suspicious behavior, such as checking for a debug environment, checking for user input, and having long sleeps was also detected in almost every case.
POCO C++ Libraries
Poco RAT makes use of, and derives its name from, the POCO C++ libraries. These libraries are quite popular cross-platform open-source libraries used for adding network functionality to desktop and mobile apps. This makes malware using them less likely to be detected than if the malware were to use its own custom code or a less widely used library.
Executable Specifics
Poco RAT is delivered as an executable with the .exe file extension. It is written in Delphi, sometimes UPX packed, and has an unusual amount of Exif metadata included in each executable. The metadata typically includes a random Company Name, Internal Name, Original File Name, Product Name, Legal Copyrights and Trademarks, and various version numbers.
Behavior
Poco RAT is consistent in its behavior. When the executable is run it establishes persistence, typically via a registry key. It then launches the legitimate process grpconv.exe, which has very few opportunities to run legitimately on modern Windows OS. Poco RAT then injects into grpconv.exe and connects to its Command and Control (C2) location.
This C2 is always hosted on 94[.]131[.]119[.]126 and is connected to at least one of 3 ports: 6541, 6542, or 6543. Unless the infected computer has a geo location in Latin America, the attempts to communicate are not responded to by the C2. If the infected computer appears to be coming from Latin America, then a very small conversation takes place over an extended period of time.
Aside from being able to communicate basic information about the environment, Poco RAT also appears to be able to download and execute files making it capable of delivering other malware more specialized for information stealing or even ransomware.