Found in environments protected by: Microsoft
By Adam Martin & Janos Torok, Cofense Phishing Defense Centre
The Phishing Defense Center (PDC) recently detected a campaign leveraging the theme of income tax refund, a topic anyone would be intrigued to engage. As illustrated below, the initial email is mirroring an email notification from the German federal government, shown in Figure 1.
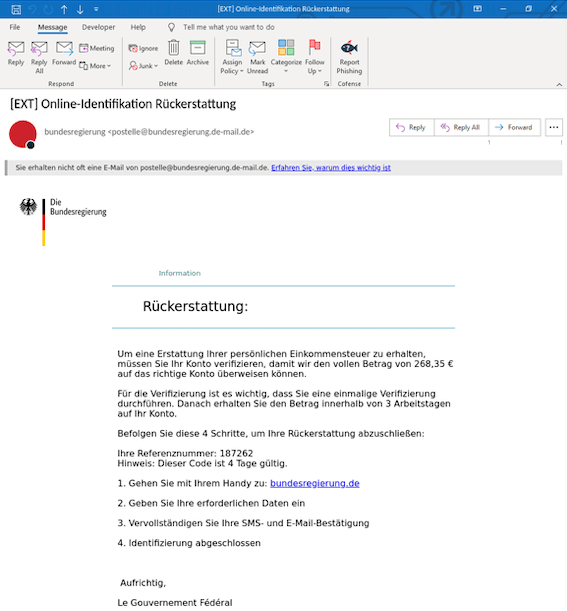
Figure 1 Initial Email Body
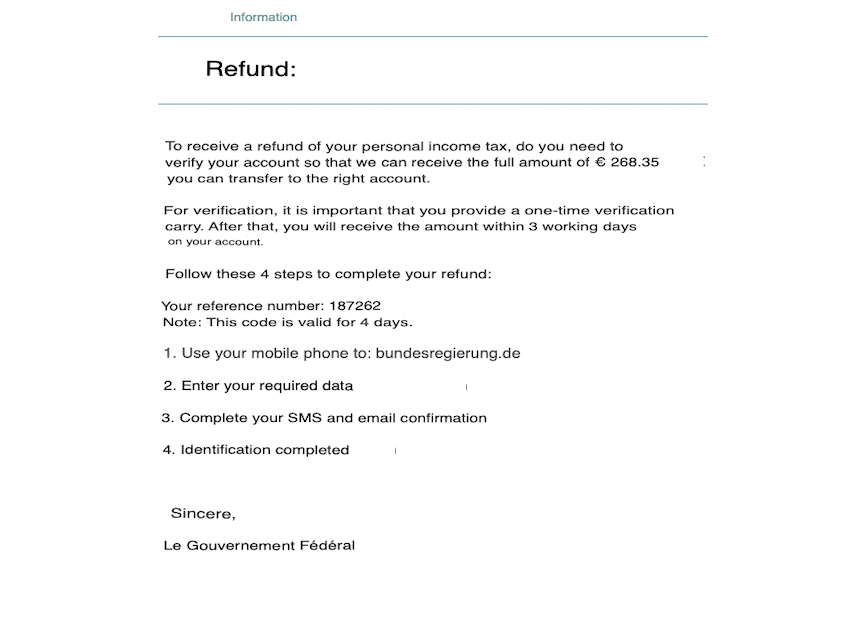
Figure 2: English Translation
This campaign is an income tax refund of 268.85 euros, with instructions given to the recipient on how to claim this rebate. The typical trope of a time limit is used with a 4-day timer placed; the recipient is redirected to a spoofed page that redirects to a malicious page once accessed. It’s recommended the recipient access the site via their mobile phone under the guise a further layer of confirmation will be given via SMS.
The initial landing page, in Figure 3, is quite well put together with a host of different banking institutions listed: PostBank, ING, Volksbank & Deutsche Bank, amongst others. What’s clever about this landing page is the fact that all the “clickable” brand logos redirect back to the official Bundesegierung page. Adding a confidence boost of legitimacy is given to the user with the mention of further verification methods mentioned in the below paragraph.

Figure 3 First Landing Page
What makes this Phishing attempt very convincing, is the absence of a generic, “please input details here” box that tends to be paired with typical attempts at credential theft. Instead, each banking institution listed has its own customized landing page accompanied by logos, banners & replicated login information input boxes.
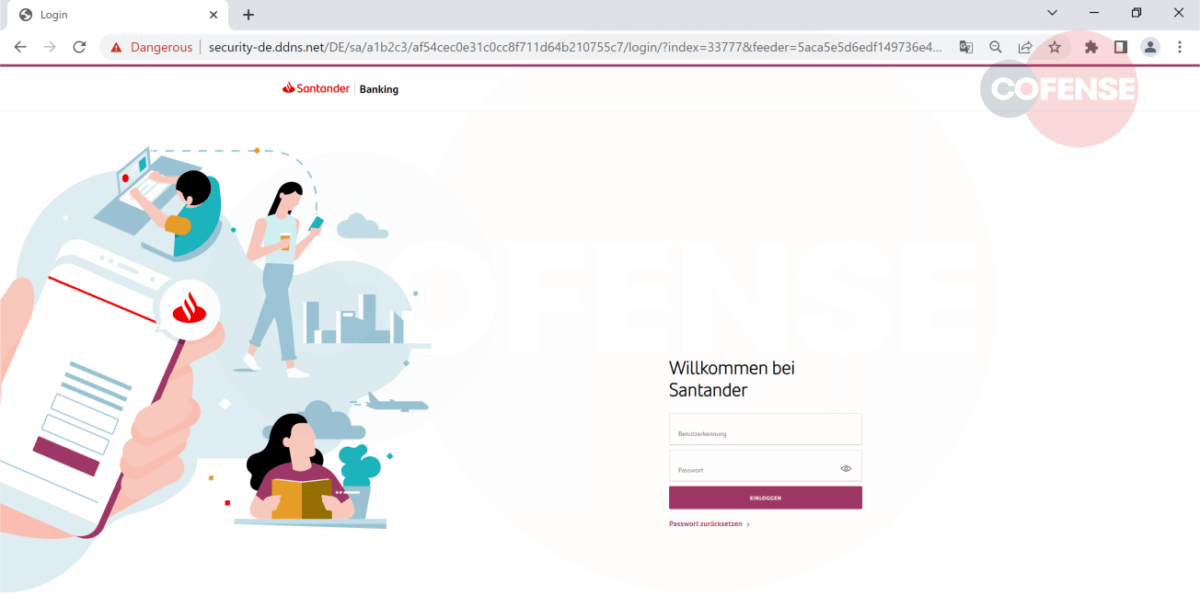
Figure 4Fake Santander Page
Figure 4 is an example of a crafted Santander Bank login page asking for account details to access online banking. While the overall looks of the page might be convincing, there is an obvious indicator that this is a spoofed page. The URL, which is a generic hosted domain, not mentioning Santander anywhere. This indicates that the domain is not owned or associated with Santander. The sole purpose of this site is to get the user’s online bank credentials.
 Figure 5 Fake Deutsche Bank Page
Figure 5 Fake Deutsche Bank Page
In Figure 5 we see another example, a spoofed page for the Deutsche Bank online banking page. This is again a well-crafted site mirroring the exact login steps of the real login page.
Again, we see It is clearly visible that the URL is the same generic host, which is not linked to Deutsche Bank, with the intent to steal banking credentials.
Overall, this example of credential phishing is building on two main principles which make it dangerous to inexperienced eyes. The first is creating a false sense of excitement about unexpected funds, with reasonable, realistic amounts, that gives the impression that it can be true. It also builds a feeling of urgency, so that the recipient acts quickly not to miss out on the free money. This is only meant to lower the victim’s guard and blind them with false hope.
The second is the quality of these crafted sites, which look legitimate at first, therefore reinforcing a sense of false security and convincing the user to go through with the attack.
As phishing attempts are becoming more sophisticated, potential victims need to be more vigilant and look for the signs that indicate this might be.
| Indicators of Compromise | IP |
| hXXps://security-de[.]ddns[.]net/root/index[.]php | 91[.]218[.]67[.]101 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.