Author: Max Gannon, Intelligence Team
Cofense Intelligence tracks advanced Tactics, Techniques, and Procedures (TTPs) in credential phishing and malware reporting. These tracked advanced TTPs consist of individual techniques such as steganography or reversing a filename and file extension with a special character. They also include overall campaign characteristics, such as Spanish language emails delivering Remote Access Trojans (RATs) via embedded links to password protected archive files hosted on Google Drive or Google Docs. Luckily, advanced TTPs such as these are not as common and only account for a small fraction of the campaigns observed by Cofense. This report will cover the individual TTPs that account for over 5% of all tracked TTPs in 2024.
Key Points
- 28% of campaigns with advanced TTPs saw the inclusion of Personally Identifiable Information (PII) within the subject, which required redaction.
- 3% of campaigns in 2024 exhibited advanced TTPs.
- The most common advanced TTP was the usage of QR codes which accounted for 57% of campaigns with advanced TTPs in 2024.
- The use of password-protected archives increased across 2024 but seems to be decreasing slightly in 2025.
- Legitimate file usage increased in 2025, with almost as many usages in the first quarter as compared to all of 2024.
PII in Subjects
Inclusion of PII within the email subject, a TTP applied by threat actors of moderate to high sophistication, was unsurprisingly relatively common in campaigns with advanced TTPs. 28% of campaigns with advanced TTPs saw the inclusion of PII within the subject, which required redaction. The majority of these subjects were also Benefits themed, referencing topics such as 401(k) plans, “Company Guidelines”, and payroll.
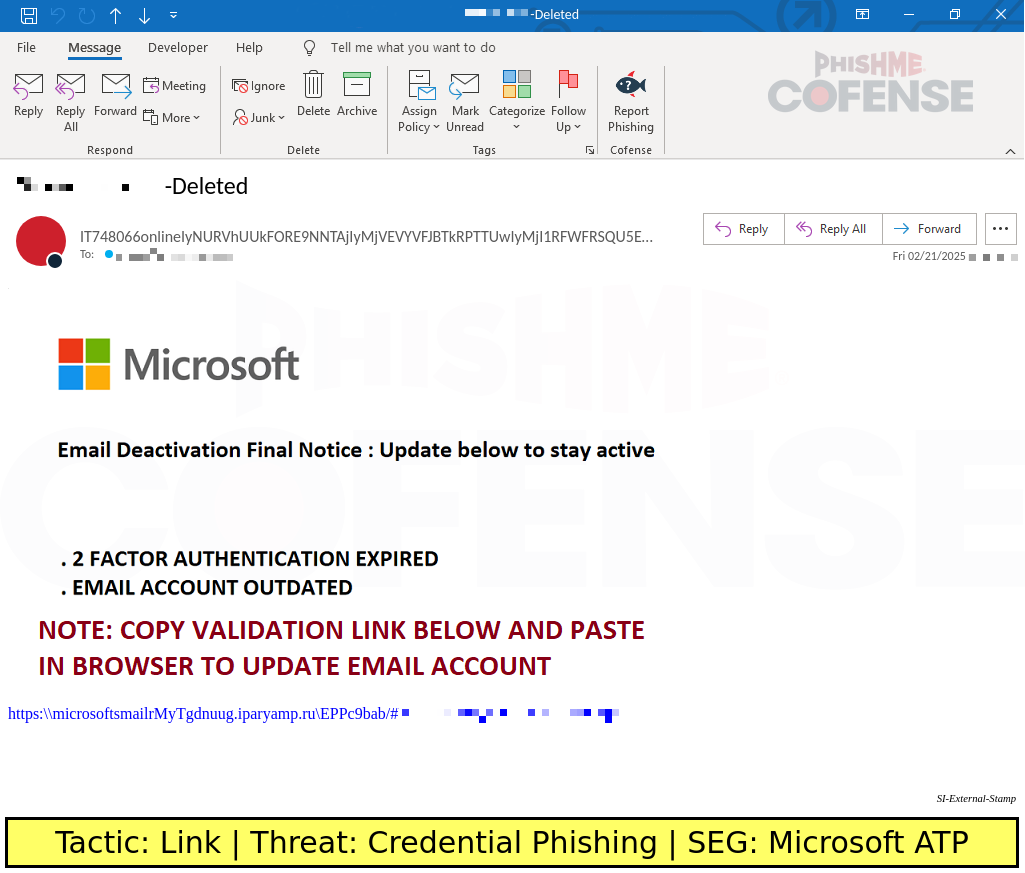
Figure 1: An email with a customized subject requiring redaction.
URL Shortcut File to WebDAV Server
URL shortcut files were not particularly common as a delivery mechanism. There are different methods of abusing URL shortcut files to deliver malware, but this method involved opening File Explorer to a remote server and demonstrated an advanced skill level. Threat actors only used this TTP in 5% of campaigns, but when they did it, it was typically in concert with abuse of Cloudflare’s free hosting services on trycloudflare.com and was used to deliver multiple RATs at one time, including XWorm RAT, DcRAT, Venom RAT, and Anarchy RAT.
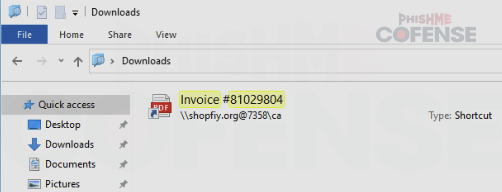
Figure 2: File Explorer is used to open up WebDAV on a remote server.
Reverse Character Used to Disguise a File Extension
One of the easiest ways to prevent victims from running .exe files is simply making file extensions visible. When file extensions are enabled, it becomes immediately obvious if a file is an executable or a script, as long as threat actors have not applied special TTPs. One of the ways that threat actors bypass this preventative method is by using a special character that reverses the characters in a file name. This makes it so that a file with the name “malware.fdp.exe” will instead appear as “malware.exe.pdf”. This method was used in 6% of the advanced TTPs seen in 2024.
Steganography
Steganography could be defined as “the practice of representing information within another message or physical object, in such a manner that the presence of the concealed information would not be evident”. In terms of threat actors using steganography as a TTP, threat actors typically download an image such as the one in Figure 3, which contains an embedded DotNET Loader .dll that is extracted and run. Campaigns making use of this TTP accounted for 9% of all advanced TTPs seen in 2024.

Figure 3: Image with embedded DLL extracted via steganography.
Legitimate Files Abused to Launch Malware
An advanced TTP utilized by threat actors to both obfuscate their activities and frustrate analysis is abusing legitimate files, most commonly legitimate executables, to run malware. Threat actors typically use a known legitimate executable such as Haihaisoft’s PDF Reader and accompany it with a malicious .dll with a specific name. When the legitimate executable is run, it automatically loads the named .dll and runs it. This accounted for approximately 10% of advanced TTPs seen in 2024. This TTP is problematic because it increases the likelihood that an analyst will report a legitimate system executable that, if blocked or deleted, has the potential to crash the computer.
Spanish Language Campaign Utilizing Google to Deliver Password Protected Archives Containing RATs
This set of tactics represented a sustained trend, likely by one threat actor or group of threat actors, where a series of tactics were combined to create emails that were likely to bypass SEGs and deliver a RAT such as Async RAT, Remcos RAT, DcRAT, or njRAT. This TTP accounted for 13% of advanced TTPs seen in 2024. This TTP is also notable, as the trend continued into January of 2025.
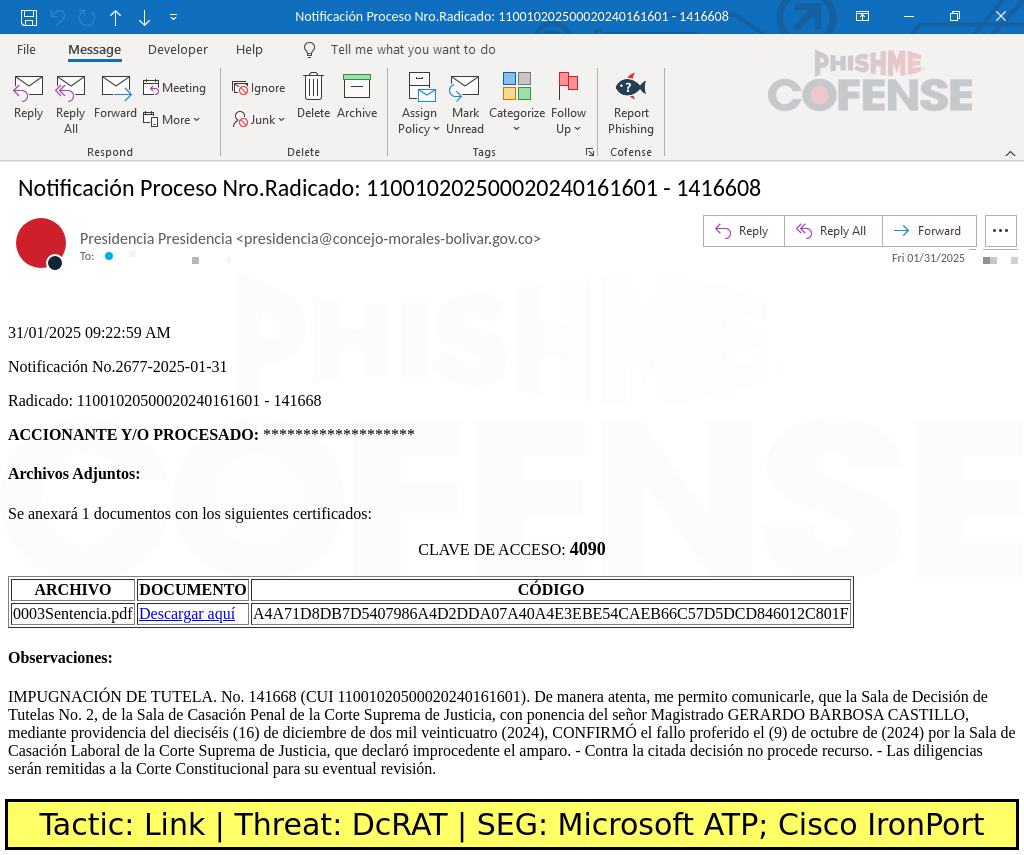
Figure 4: A Spanish language campaign delivering an embedded link to Google Drive, which hosts a password-protected archive.
A Password Protected Archive is Used to Deliver Malware
A TTP that is known to bypass many SEGs is delivering an attached archive or a link to download an archive that is password protected. The password is typically in the body of the email but is sometimes listed in the attachments, such as in an attached PDF. By password-protecting the archive, threat actors prevent SEGs and other methods from scanning its contents and detecting what is typically a clearly malicious file. This TTP is not the most advanced but still indicates threat actors willing to go a step beyond the usual methods and accounts for 22% of all advanced TTPs seen in 2024.
A QR Code is Used to Deliver Credential Phishing or Malware
Although they are increasingly more common now, QR Codes still represent a TTP that requires the threat actor to take an additional step of creating a QR code that leads to a credential phishing site. Many threat actors take one extra step and ensure that the credential phishing page only functions for those using a mobile browser. Campaigns using QR codes to deliver credential phishing or malware accounted for 57% of advanced TTPs observed in 2024.