By Jake Longden, Cofense Phishing Defense Center
Microsoft Power BI, a popular data-visualization tool, is designed to help users wrangle their data in multiple and more human-friendly formats. As a recognizable application from a commonly used and trusted vendor, Power BI is also a prime target for threat actors to spoof and abuse it for phishing attacks.
The Cofense Phishing Defense Center (PDC) has observed a new phishing campaign that harvests Microsoft credentials by impersonating Power BI emails.
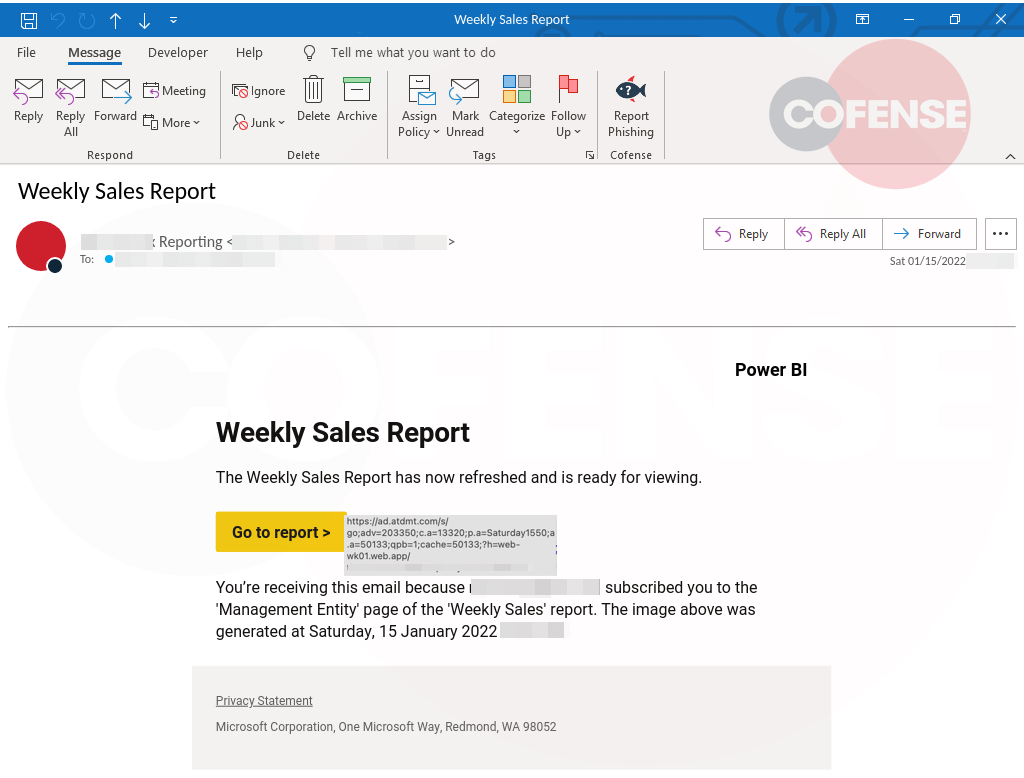
Figure 1: Email Body
As seen in Figure 1, the email resembles a legitimate Microsoft notification. There are a couple of reasons how this happens. Threat actors have become comfortable adapting legitimate MS notifications in their phishing templates. We also observe them leveraging stolen credentials to create a legitimate looking notification from a legitimate MS instance. We see that the threat actor in this email used a common theme to try to get the recipient to interact with the links – Weekly Sales Report.

Figure 2: Phishing Page
Once the user has clicked the link in the email, they are presented with a page seen in Figure 2, designed to look like a legitimate Microsoft log-in page. The first indicator that something’s not right with the page, beyond the missing standard imagery, is that the URL doesn’t look anything close to what’s indicated in the email or associated with Microsoft services.
Figure 3: Phishing Final Page
Subsequent to the recipient providing their credentials, the final step of the attack is an error message indicating that there was an issue with the account verification. This is another Microsoft spoof the threat actor employed to distract the recipient from the fact that they have not been redirected to the Power BI report they expected to see. This discourages the recipient from suspecting that they have just given away their credentials.
Cofense continues to observe credential phishing as a major threat to organizations. This is why it’s critical to condition users to identify and report suspicious messages to the security operations team. This recipient was well-conditioned to identify something wasn’t adding up with this email and landing page, and used Cofense Reporter to send this off to the Cofense Phishing Defense Center. Cofense can help you, too. Attacks such as this one are effective at eluding common email security controls, and are – by design -- overlooked by end users. Cofense can help.
| Network IOC | IP |
| hXXps://ad[.]atdmt[.]com/s/go;adv=203350; c.a=13320;p.a=Saturday1550;a.a=50133;qpb=1;cache=50133;?h=web-wk01[.]web[.]app | |
| hXXps://web-wk01[.]web[.]app | |
| hXXps://l-formula[.]com/wp-reporting.php | 202.254.234.76 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.