Email Gateways Bypassed: Microsoft
By Amy Griffiths, Cofense Phishing Defense Center
The Cofense Phishing Defense Center (PDC) has analyzed a phishing campaign that is aimed to harvest an employee’s Microsoft credentials via a malicious HTML attachment. The attached file includes spliced code when it’s executed, it scrapes for the employee’s credentials.
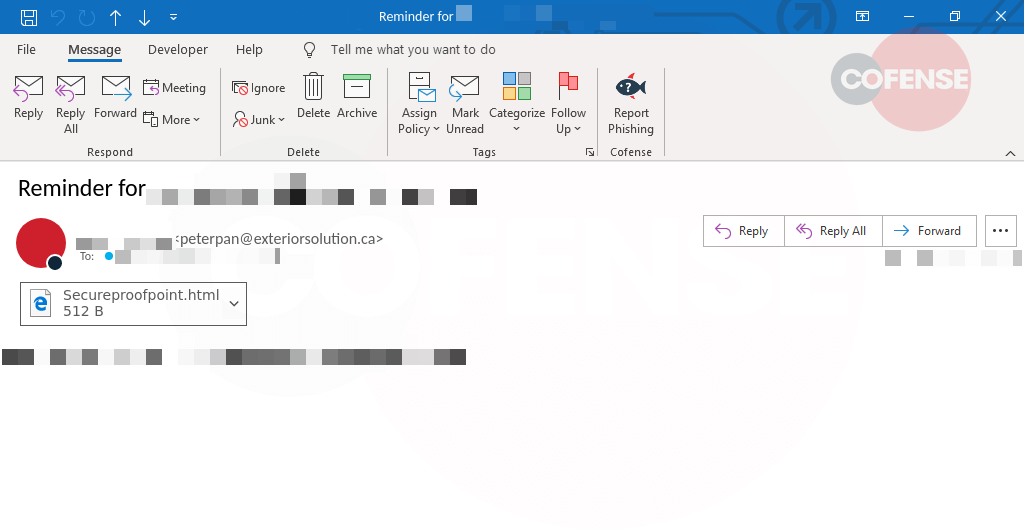 Figure 1: Email Body
Figure 1: Email Body
As seen in Figure 1, the subject of the email “Reminder for…” gives the employee a sense of urgency, something they may have missed or overlooked previously. Perhaps not so urgent, but does have an interesting object within the body, an attached HTML file named “Secureproofpoint[.]html[.]”
The attachment name could refer to the trusted vendor Proofpoint Secure Share a cloud-based solution that enables enterprise users to exchange large files in a secure and compliant manner to enterprise policies.
 Figure 2: Malicious code
Figure 2: Malicious code
The several lines of code seen in Figure 2 can be found within the HTML file and are used to run JavaScript code to decode strings and a malicious URL. To summarize the code, the 'encdStr' string is the encoded subdomain 'primeaco[.]com[.]br' which is followed by the targeted users email address that is stored as the string named 'emma'. The function 'atob(encdStr)' is followed by a linked set of variables that sets the URL to "hxxp://SILENTCODERSLIMAHURUF[.]primeaco[.]com[.]br/<recipient name or identifiable information>". Finally, the last line of code calls the function 'window[.]location[.]href'. This function returns a string containing the whole URL and allows the hyperlink reference to be updated. At this point, the browser is updated from the HTML file to the malicious URL.
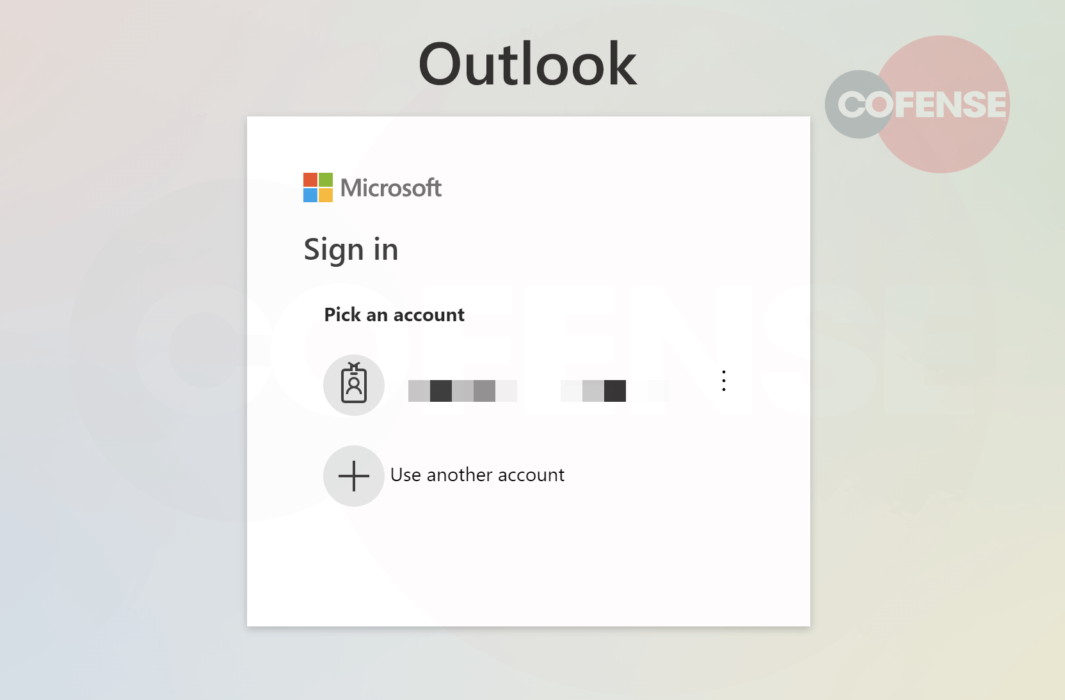 Figure 3: Pick an Account
Figure 3: Pick an Account
Once the completed URL is executed in the browser the user is presented with the page seen in Figure 3. This gives the user a false sense of security by masquerading as a trusted brand, Microsoft. It fools the user into thinking they can pick the account; however, we know from analyzing the code the user’s details are already set as a variable.
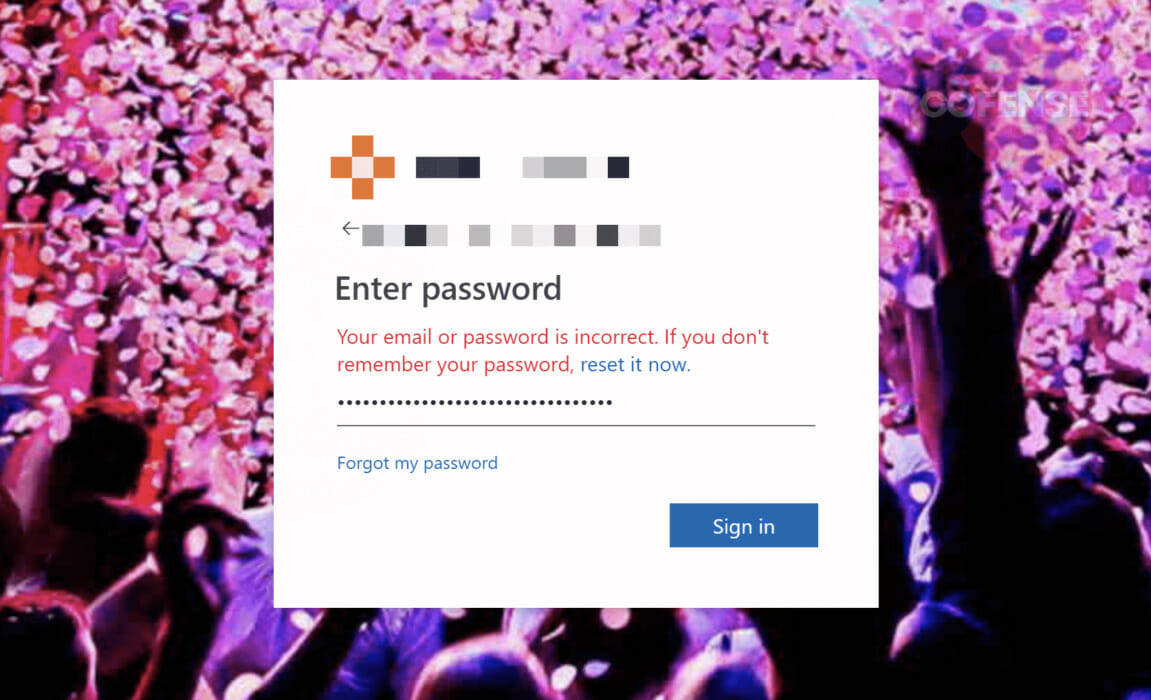 Figure 4: Phishing Page
Figure 4: Phishing Page
Once the employee clicks on their user account, they are then presented with the phishing page seen in Figure 4, where they are prompted to enter their credentials which are finally scraped by the threat actors.
| IOC(s) | Description |
|---|---|
| PM_Intel_CredPhish_283847 | Cofense Triage YARA Rule |
| hxxp://silentcoderslimahuruf[.]primeaco[.]com[.]br/ | Phishing URL |
| 216[.]172[.]172[.]168 | IP Address for shared hosting node |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.