By: Tej Tulachan, Cofense Phishing Defense Center
The Cofense Phishing Defense Center (PDC) has recently observed a new wave of credential harvesting attacks involving phishing emails sent via SendGrid. The campaign exploits the trusted reputation of SendGrid, a legitimate cloud-based email service used by businesses to send transactional and marketing emails. By impersonating SendGrid’s platform, attackers can deliver phishing emails that appear authentic and bypass common email security gateways. The campaign delivers the attack through three differently themed emails, each crafted to create a sense of urgency in both the subject line and body. The emails also use spoofed sender addresses, making them appear as if they genuinely originated from SendGrid.
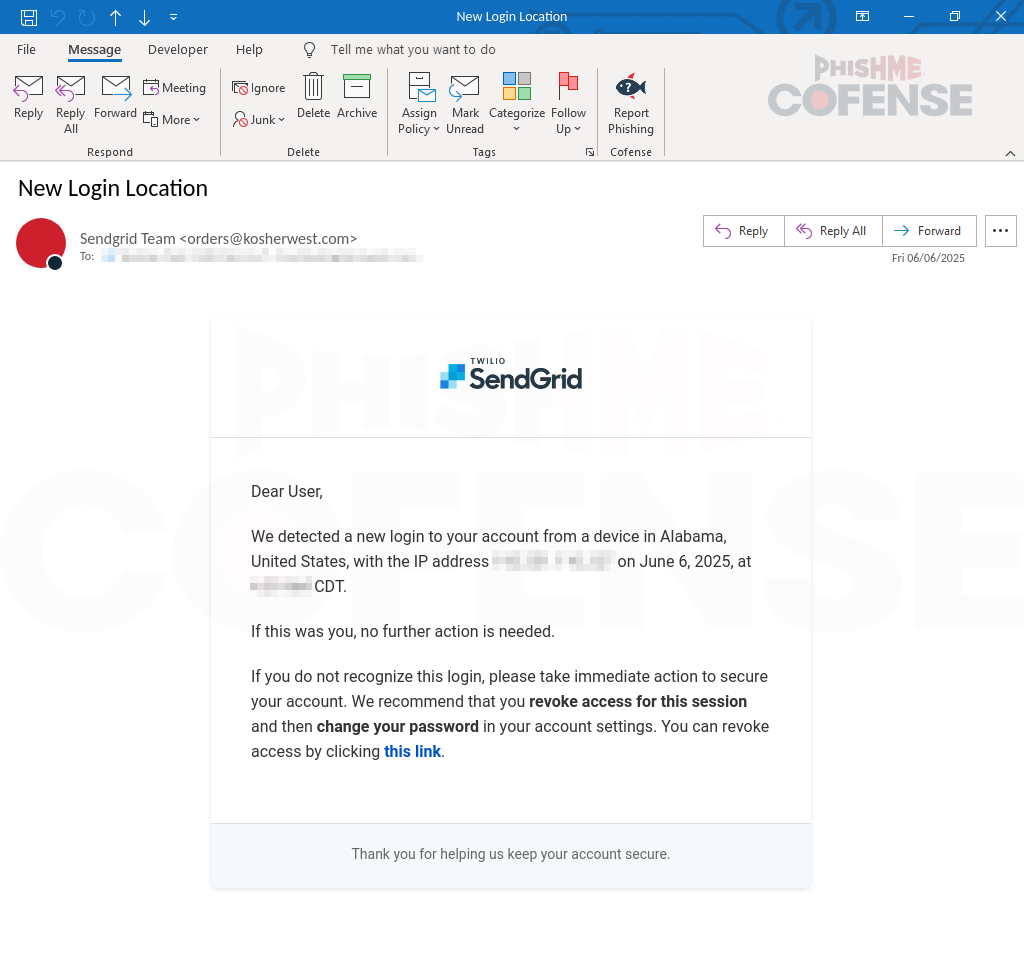 Figure 1: Email Body
Figure 1: Email Body
Let’s begin by reviewing the first email, illustrated in Figure 1. The subject line “New Login Location” is designed to grab the user’s attention. At first glance, the email appears legitimate, featuring correctly sized logos and polished formatting. A commonly seen tactic in these phishing emails is mentioning a suspicious login attempt from a fake IP address and location, followed by reassuring language such as “If this was you, no further action is needed” to lower the user’s guard. Furthermore, the threat actor uses an email alias modification spoof to make the email appear as if it originated from SendGrid. Finally, the primary tactic to trick users into revealing their passwords is the malicious link embedded with the prompt “access by clicking this link.” This appeal to human curiosity encourages users to click the link without hesitation.
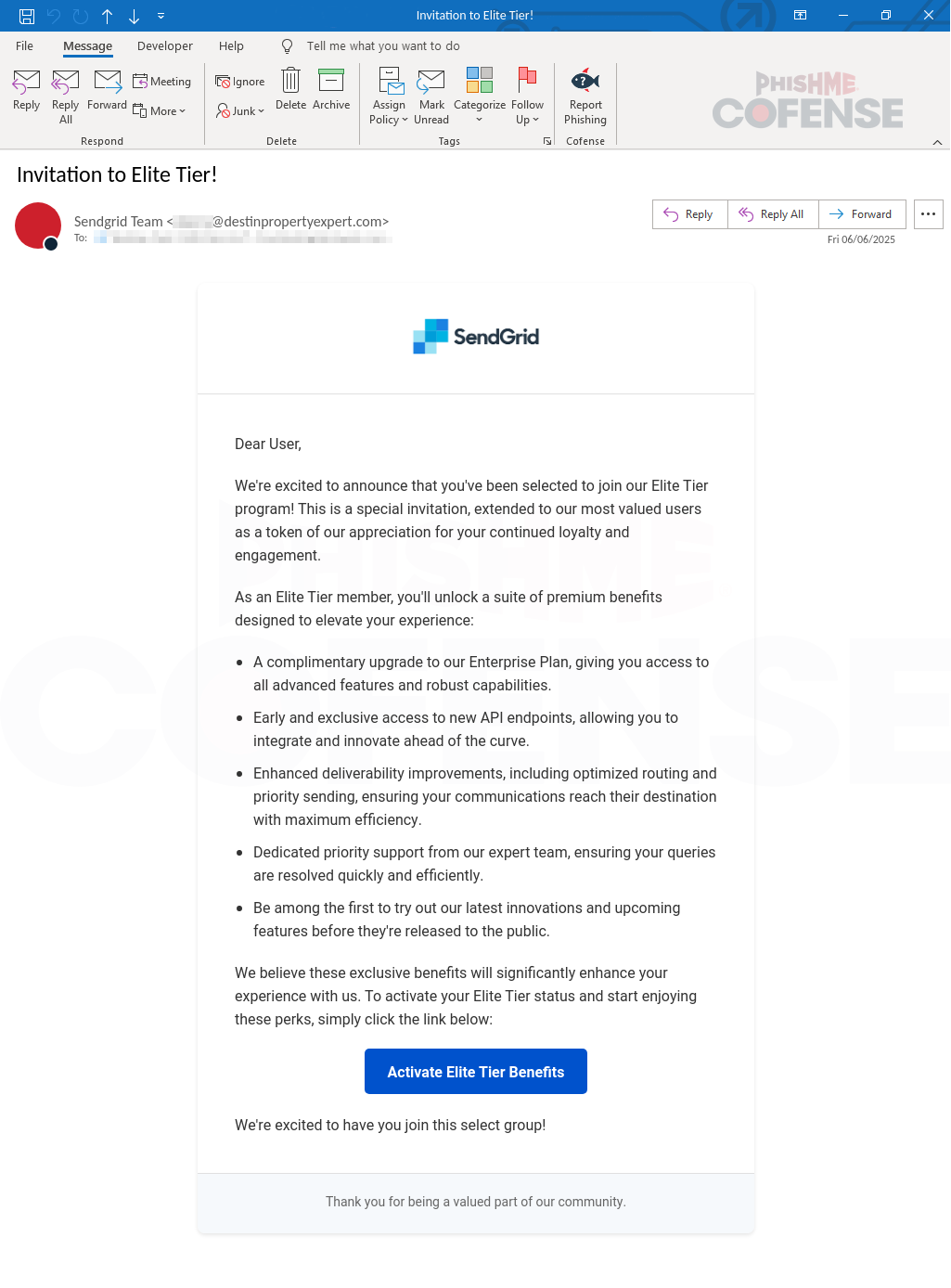
Figure 2: Email Body
The second phishing email, like the first one, employs spoofing techniques to closely replicate a legitimate message. However, the email body entices users by offering a free promotion to an “Elite Tier” with premium benefits. This tactic plays on users’ emotions—after all, who doesn’t like free perks? At the end of the email, there is an embedded prompt, “Activate Elite Tier Benefits,” which contains a malicious link designed to capture credentials.
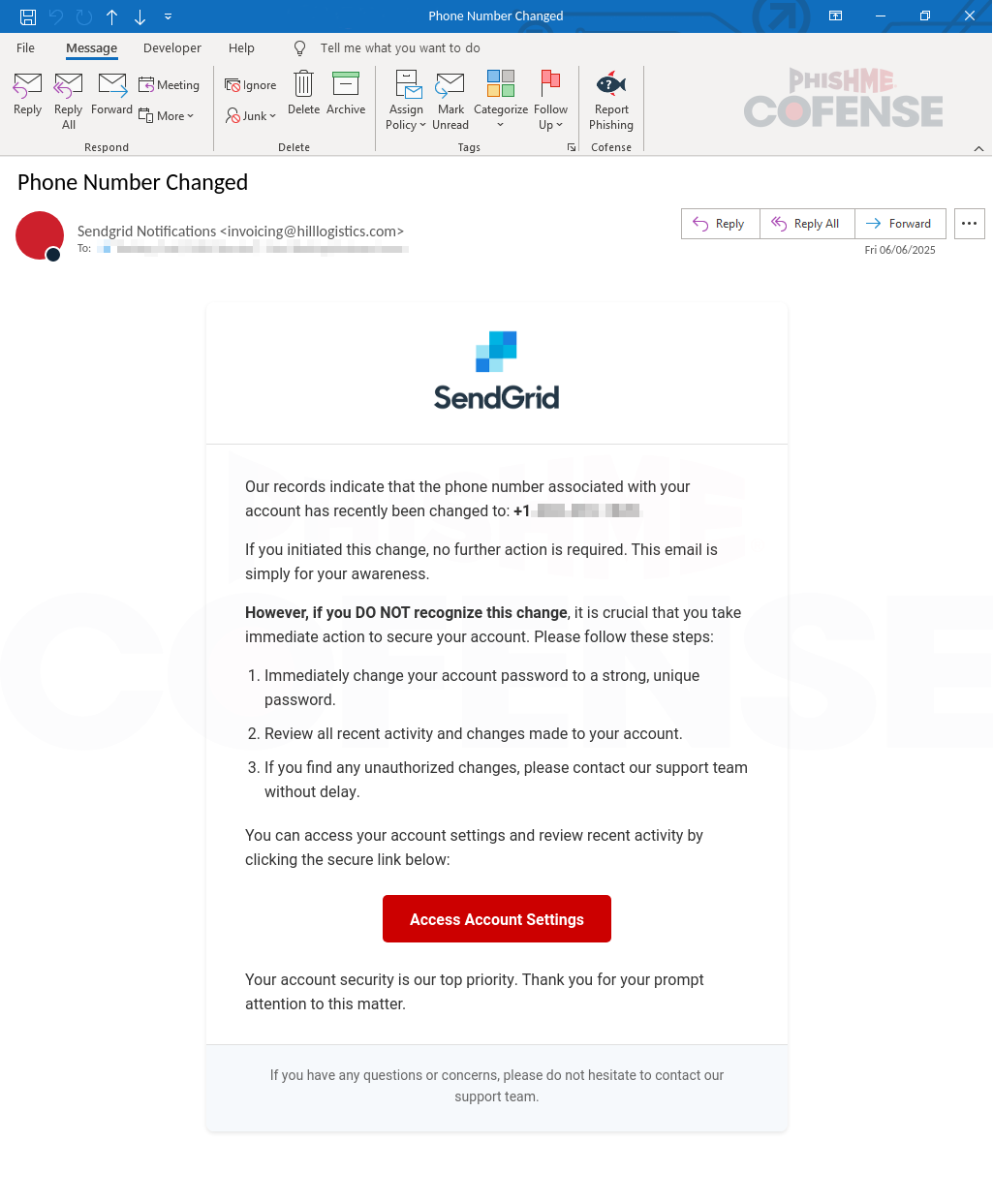
Figure 3: Email Body
The final themed phishing email follows a similar pattern to the first, but instead of notifying users about a new login location, it deceives them by claiming their phone number has been changed. This tactic is designed to promote a sense of urgency and panic, prompting users to take immediate action without careful consideration. Like the earlier emails, this email contains an embedded link in “Access Account Settings” directing users to a malicious website designed to steal sensitive information.
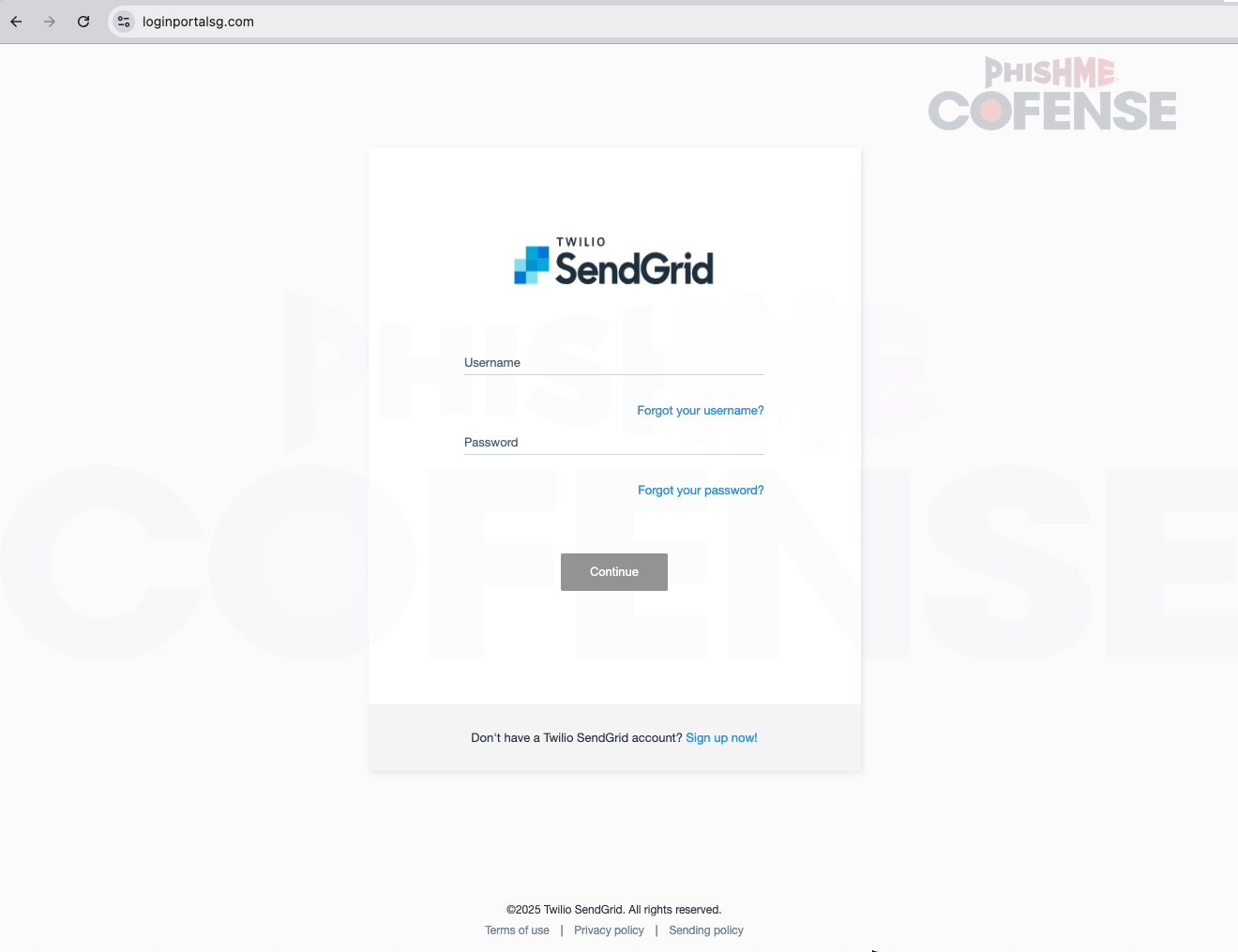
Figure 4: Phishing Page
When the button is clicked, the threat actors exploit the open redirect link url6849[.]destinpropertyexpert[.]com/ls/click?. The link structure accepts any URL as a parameter, and the server redirects the user to that specified address. Attackers commonly abuse this behavior to make their phishing links appear more legitimate by leveraging the trust associated with a legitimate domain. It provides an ideal cover for malicious activity, helping threat actors evade detection and bypass security controls by disguising harmful traffic as legitimate.
These links include encoded data and redirect users to a SendGrid phishing site shown in Figure 4. The landing page appears clean and closely mimics the legitimate SendGrid website, making it difficult to detect at first glance. However, the key takeaway is that the domain hXXps://loginportalsg[.]com is not a legitimate SendGrid website. Users should always verify the URL carefully before interacting with it or taking any action.
This analysis highlights how attackers employ varied techniques to steal user credentials, with each of the three phishing emails crafted differently to achieve the same end goal—harvesting sensitive information. By manipulating trust, creating urgency, and mimicking legitimate platforms, threat actors increase the chances of success. To counter these types of attacks, the PDC helps businesses strengthen their defenses and identify real-world phishing threats—minimizing the risk of data breaches, reputational harm, and business disruption. Schedule a demo today to learn more.
Stage 1 - Observed Email Infection URL: | Infection URL IP(s): |
hXXp://url1390[.]hilllogistics[.]com/ls/click?upn=u001[.]Yu9M7-2F-2FnrU2-2FRpzPaAEBgExVWKWoxNPKCFhhsWROf9XeYEMCh9e0QECnhcptrX2S2cV2aht923LdETaR5ijzYPlx9Y4mOQB-2BZCcetWLkr7d7I-2Faah37spQKY-2FEILc8FWRI62kYEJgL2tdy9pwwstWdtizVOhKOtwL-2FCshQKjTEx-2FeUXnmLIQH4HD04d3WJC5WbLQXbPUnEvSBa98L2b2xZRBpSFOQ1WlzpNZ54xH9x2s19bZS0kDcyfolo-2FvQ3Piyd0dHfVJJIivKm3th9BhFdklrRcTVQLjsqA333brunzirWty5u0MIHmODeVG4q8P47hYTNX6r-2FJZKG7QI-2FHnfmY8pr2Phj22w4DDacVRVU9L2X-2Bu4RipO-2FoFfJXX6Ke8fvAD2Aec2JHg-2BQp5-2Bb2YSDG-2BAETn5WcvkFH2yJEDsfzUBi1jHgQT4xtgNv1-2FSTtYoySAdLSE8I3Z-2FMAn5EQD7Cw4yxlgrvp3lz69oa7Mw0F92uoP4HQvDGHe5XC-2Fvt0yLuj-2FDq45cC38y3l7h4f7sw-3D-3DA9Ub_t7gAvOB6HMyU6RfuKePtJra5X2EdiORCrHyMQTm7hGCzxK-2BwJ7iZNyOIS5Ehbwru7yA5zp-2FMuYar-2Bdd7JeWa0HOD0acl5osm-2FGSW7-2B9n3xvRFx8KMgxocgt9jYT0H9OQJ6WnU2TAogxFDLsAnBvenVBN19-2BieBcDVPOMzvdyU8a3dUTjXhz0mposTjIGAncFGpwKwDjOhnq6ripN1i6reA-3D-3D
| 69.7.174.162
|
hXXp://url6849[.]destinpropertyexpert[.]com/ls/click?upn=u001[.]5kHtxVODF9oynRfMIg1bHYLnvZ4uwKfPxeqMAGcCyRwF7zVeV7TeWDa1YeA1WEqlv5YICvDuLTpVVcjWzC-2BpE3N6z8-2BMiEhT3YdSdYC7pqgGn8W6bMGma5T1-2Bo7ttkP28fXVNm3HnDZ3fjeOS43bzjsgM5ldRWhj-2FDC-2F7i-2Fi1XRXzWe97fQ0YU4rmyJ5J80HFkmcvSpfalp2UGySKiTGKWxSSDcZNkgIh1i6cyMmWyVY3s7Pq-2BZWA41gsjE07AjMIa9NkA-2BsiLL8KDyl45AivhbyAjaay5aHtPlIKmav-2B9fWBo-2Bx0VVcih-2BDr4xOAUXj-2FzUvJw5tfNOcpYzyt39b2EAjmnsJxMMTvUFglRunWcvMrNHy72p6nqjjEanWcg-2Btapgj7fNXAGTB8e0Yd2mgp4QuFoSke5t5UWJtaCWEYB2XjtNGqMKmxTT6MUnFOJnuoJW0yyIC4JrLaVhErDlKooiLUzo0o7rmMieLgOKU1khw8jBKzYlCUMt9qSnD16xxifB0qyozOGRg5x0aqN5qa5W-2Fw0awC1KLhH8Yk3Y9Lb-2FzR9q5OGzAkGZTefbGYcAydCj-2BC2v7K-2BfFR0f-2FfaEFdrCwor9fdbnRtYdFGMrlOlM-3DTHFf_t7gAvOB6HMyU6RfuKePtJra5X2EdiORCrHyMQTm7hGAyCjtWlUwJBEgDvmLVdQH7L49YrNvi8a3OdWrJrZLfy1KR4AG2-2BMHwSnB9PmT8O-2F7ye0Mj5LfQHrSKKtSYgEPz7sityaSg-2FCpNAWzmedfLOsg6oxAlY0erepcC9Y8gHooOB1BsoYcVn-2FbSMXP9uGkqEt5anzKss6wx-2FY2dpud6QQ-3D-3D
| 104.21.85.103 172.67.204.116
|
hXXps://u42632394[.]ct[.]sendgrid[.]net/ls/click?upn=u001[.]RTyH5NZxNIUh-2Fr7uRoQ0-2FcekI92sgoZ43P3aqN5SYTzUsTOOgoEyfKKq0ybvWfymrg7bVKyaEAVaf74ERHdn0XxX3TQKihdCqpY8qHt8jZ59mMTJPEgLLFD8fHNnm4KSlNDym-2Fwe4gJkc9F2UsHXBADaaPs53n3mfb260UhRi5wn1Oon9AURLGC0WVGwJLdW9ZH6oav3sfc7QpuVPEWEM23VWNngl0inG2G-2BxlwP9F0dlmNUtQmiD4vBVf81U-2Bbc9tL-2FxGwxbR-2FMhMqhyc5y0tRT9KZeAIRH-2BEPRw1Utb3XBOAj1cqyuG5jJmgXp7cuTSRsCfszQw5xhJp5LYgOKefP8zfUd6F7qZ8xsHm1k2aUL9s0LRhBIhp1ShE-2BlILU0XRavzbw8eu64DGPOjonzbCDaT6LpCliWBSGWNCxNzTQS7exlRTsN8af9HVo8ehGC02UgJX7lHN5-2BzqQv2VOM0AVx3BfbKXhx4napyCgdHUwXH-2BjHhNSoAB2OnmMlLV4-2ByFKmbS8sWHi9ZWvknFBeYg-3D-3Dr2MN_t7gAvOB6HMyU6RfuKePtJra5X2EdiORCrHyMQTm7hGASLVLP4bxIlHGXc6MwwzctBJVZ2u6NNtSOwi31J6jzklKcTbU9AxBuggAE-2FHqbpTBwf6B8o8ud1SqVcpWBf5BD1zzkmjAuo-2BxsDpWPAPWLjhoTPsAI92nQFPAfuU0gnUVsMkbmuIhqMgHpJNvTiCq4vAlk9ryzOg3ETDViAJWlAQ-3D-3D
| 3.220.122.174 54.158.174.185 3.231.179.208
|
Stage 2 - Observed Payload URL(s): | Payload IP(s): |
hXXps://loginportalsg[.]com/
| 185.208.156.46 |
hXXps://sendgrid[.]aws-us5[.]com/
| 185.208.156.46 |
All third-party trademarks referenced by Cofense, whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of endpoint protections are based on observations at a point in time, based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog, are registered trademarks or trademarks of Cofense Inc.