By: Jhon Revesencio and Chris Autentico, Cofense Phishing Defense Center
Have you ever felt like you're dodging digital daggers in the online world? Well, you're not far off. Imagine a sneaky email landing in your inbox, disguised as a file deletion reminder or a too-good-to-be-true offer from a trusted file-sharing service. You click, thinking you’re preventing a potential threat to your organization—but BAM! It’s a trap. The Cofense Phishing Defense Center (PDC) has identified a clever cyber-attack distinguished by its hybrid approach of integrating both phishing techniques targeting Office365 (O365) credentials and malware delivery. The campaign uses a file deletion reminder as a pretext to employ credential phishing as well as the delivery of malware. Victims receive a message warning about an impending file deletion, prompting them to take immediate action. Additionally, what's more deceiving is that the email is coming from a legitimate file-sharing service, making this lure more effective against susceptible users. The email seen in Figure 1 initially appeared to be a reminder regarding file deletion from files.fm, a cloud storage and file-sharing service.
Figure 1: Email Body
Figure 2: Attachment download page
Upon clicking the hyperlinked document name in the initial email lure, users are redirected to a legitimate files.fm link where they can download the seemingly safe shared PDF file, which further strengthens a sense of security. The key deception lies in the next step: when users open the shared file, the phishing attack and malware delivery are triggered. This tactic cleverly exploits the trust associated with a reputable file-sharing service, making it easy for users to overlook potential cyber threats.
Figure 3: Opened PDF file
After the user opens the PDF file, Figure 3 shows the deceptive content within. It presents two seemingly benign hyperlinks: “Preview” and “Download,” both of which conceal threats/malicious attacks via hyperlinks, etc. This technique significantly increases the likelihood of a successful cyberattack, particularly targeting users who may not be well-versed in recognizing such threats. The most fascinating aspect of this cyberattack is that the “Preview” and “Download” hyperlinks are subjected to two different types of attacks, almost as if the threat actor intentionally designed the attack to trap the user, forcing them to choose which ‘poison’ they will fall for. Both options lead to the same outcome, with similar goals but different approaches to achieving them.
Figure 4: Fake Microsoft Login (Phish Page)
When users click the hyperlink “Preview," they’re directed to a page that looks like the typical Microsoft login screen, which is a familiar setup that threat actors often use to trick people into entering their credentials. The page initially appears to be trustworthy with the recognizable Microsoft branding and standard login prompts. But if the users pay attention, there are some signs that something’s off. The URL isn’t the official Microsoft domain, and the request to re-enter credentials for a shared document is unusual. Although these warning signs may seem minor, they serve as key indicators of a phishing scheme aimed at stealing user credentials.
Figure 5: Malware Download
Figure 5 highlights that when the users click the hyperlink “Download," it initiates the download of an executable file named 'SecuredOneDrive.ClientSetup.exe,' which, based on its name, appears to be associated with OneDrive client installation. However, it deceptively uses a Microsoft-related name to trick the users into believing it is a legitimate OneDrive installer. Similarly to the phishing attack, the file name in this instance uses Microsoft branded products such as “OneDrive” to help reinforce the idea that the file is ‘Safe’ or ‘Secure’. In doing so, the threat actor leverages a sort of psychosocial engineering that furthers the malicious narrative.
The infection chain leading from the malicious phishing email to either ConnectWise RAT or credential phishing is diagramed below in Figure 6.
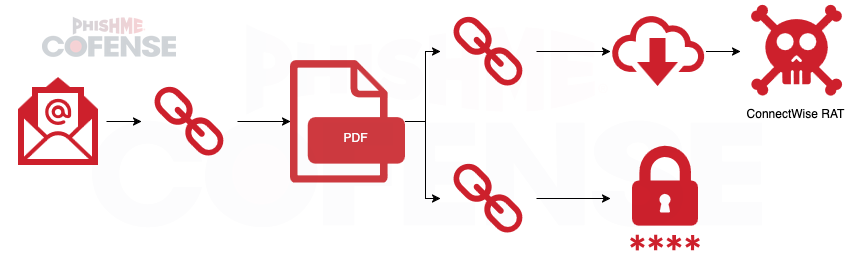
Figure 6: Infection Chain Leading to ConnectWise RAT or Credential Phishing
Technical Analysis
Figure 7: Execution
When the user tries to open the downloaded file, it automatically installs and executes itself. Figure 7 illustrates two active processes: the parent process, labeled as ScreenConnect.ClientService.exe, and its child process, identified as ScreenConnect.WindowsClient.exe. These processes are associated with the ConnectWise RAT malware family, which exploits the legitimate remote administration tool ConnectWise Control (formerly ScreenConnect). This tool has been used for legitimate remote support and access since at least 2016 but has been exploited by threat actors to establish unauthorized connections and facilitate lateral movement within target environments. In addition, the figure shows notable extracted strings related to the malware family.
Figure 8: ScreenConnect.ClientService.exe remote address
As shown in Figure 8, the process is connected to the remote address “139[.]178[.]89[.]76.” However, this IP address belongs to ConnectWise infrastructure for ScreenConnect and is not inherently malicious. The actual command and control (C2) endpoint are hXXp[://]instance-i4zsy0-relay[.]screenconnect[.]com:443, allowing the threat actor to remotely manage and execute commands on the infected system. Establishing a connection to a remote address is a common behavior exhibited by malware to perform data exfiltration, system manipulation, and further propagation within a network.
Figure 9.1: Created Service – General Settings
Figure 9.2: Created Service – Recovery Settings
ConnectWise ScreenConnect is a legitimate remote desktop software application that installs itself as a system service to maintain continuous functionality, as shown in Figures 9.1 and 9.2. This behavior is expected and does not inherently indicate malicious activity. However, threat actors can exploit this legitimate service for their persistence strategy and this tactic is commonly used by threat actors to control compromised systems, evade detection, and hinder removal efforts.
Figure 10: Created Registry
Another persistence technique employed by the malware involves modifying the system registry. As illustrated in Figure 10, the malware creates a registry entry under HKEY_LOCAL_MACHINE, a critical part of Windows that controls system-wide settings for all users. The “Start” value is configured to “0x00000002,” indicating that the service is set to start automatically during system boot. This registry modification allows the malware to reactivate with each system restart, serving as a reliable fallback mechanism. Even if the malware is manually terminated or removed by antivirus software, this technique significantly enhances its persistence on the compromised system.
This dual-threat approach emphasizes the need for vigilance in email communications. Users must be educated to recognize red flags, such as unexpected requests or unusual sender addresses. To combat such attacks effectively, organizations should prioritize user awareness and education about phishing threats. While automated systems are helpful, the human element is vital in identifying and reporting suspicious emails. By utilizing solutions like Cofense Managed Phishing Detection and Response (MPDR) through the Phishing Defense Center (PDC), businesses can strengthen their defenses and gain insights into real phishing threats, ultimately reducing the risk of costly breaches.
| Stage 1 - Observed Email Infection URL | Infection URL IP(s) |
|---|---|
| hXXps://www[.]files[.]fm/u/jv2stwauw7 | 172[.]67[.]75[.]107 104[.]26[.]0[.]31 104[.]26[.]1[.]31 |
| Stage 2 - Observed Malicious File(s) |
|---|
File Name: Mash_Media_Group_Ltd_-S8927302.pdf File Name: SecuredOnedrive.ClientSetup.exe File Name: ScreenConnect.WindowsClient.exe File Name: ScreenConnect.ClientService.exe |
| Stage 2 - Observed Payload URL(s) | Payload IP(s) |
|---|---|
| hXXps://femaxpipeworks[.]com/LgGxTNCi hXXps://apsxsecured[.]screenconnect[.]com/Bin/SecuredOnedrive[.]ClientSetup[.]exe?e=Access&y=Guest | 64[.]72[.]205[.]63 139[.]178[.]89[.]78 |
| Stage 2 - Observed Command & Control IP(s) |
|---|
| hXXp[://]instance-i4zsy0-relay[.]screenconnect[.]com:443 |