By: Harsh Patel, Cofense Phishing Defense Center
As organizations wrap up the first quarter of the year, many employees are gearing up for Q1 evaluations that highlight their progress or areas for improvement, while also planning for their goals in the upcoming Q2. These goals and achievements showcase a glimpse of what they can expect for their yearly reviews, bonuses, and future opportunities. Cybercriminals have been exploiting this anticipation by creating a themed phishing campaign camouflaged as official company-wide initiatives to follow toward the end of Q1.
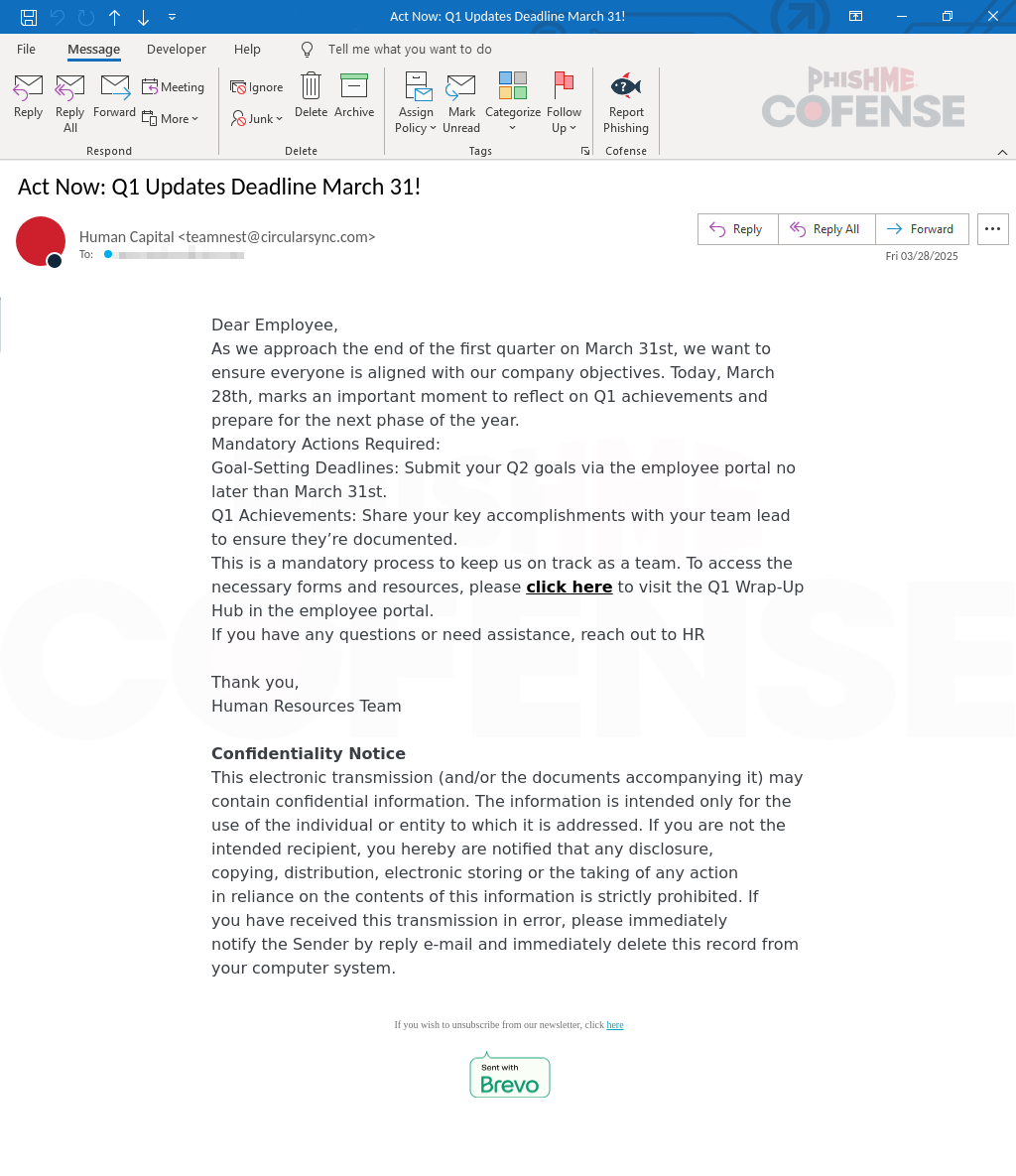
The Cofense Phishing Defense Center (PDC) has observed a similar call-to-action-themed phishing email meant to leverage authority, urgency, and familiarity to lure anticipating and unsuspecting employees into compromising their sensitive information. This highly targeted phishing attack contains detailed mandatory steps in the email to establish trust, as shown in Figure 1 below.
.png)
Figure 1: Email Body
At first glance, the user would see the email appearing to be delivered from the company's "Human Capital" department. Also known as the company's human resources, this department typically communicates information about benefits, performance reviews, or other HR-related matters. The email sender, the subject being "Act Now: Q1 Updates Deadline March 31!" and the email body mentioning a compliance deadline immediately instills a sense of importance. These subtle psychological cues create a compelling narrative that urges employees to engage without suspicion. The email body reinforces this by emphasizing the need for employees to stay "aligned with our company objectives" and listing "Mandatory Actions" like "Goal-Setting Deadline" and "Q1 Achievement." A malicious hyperlink saying "click here to visit Q1 Wrap-Up Hub in the employee portal" with a 3-day deadline is also included, further increasing the pressure of urgency.
.png)
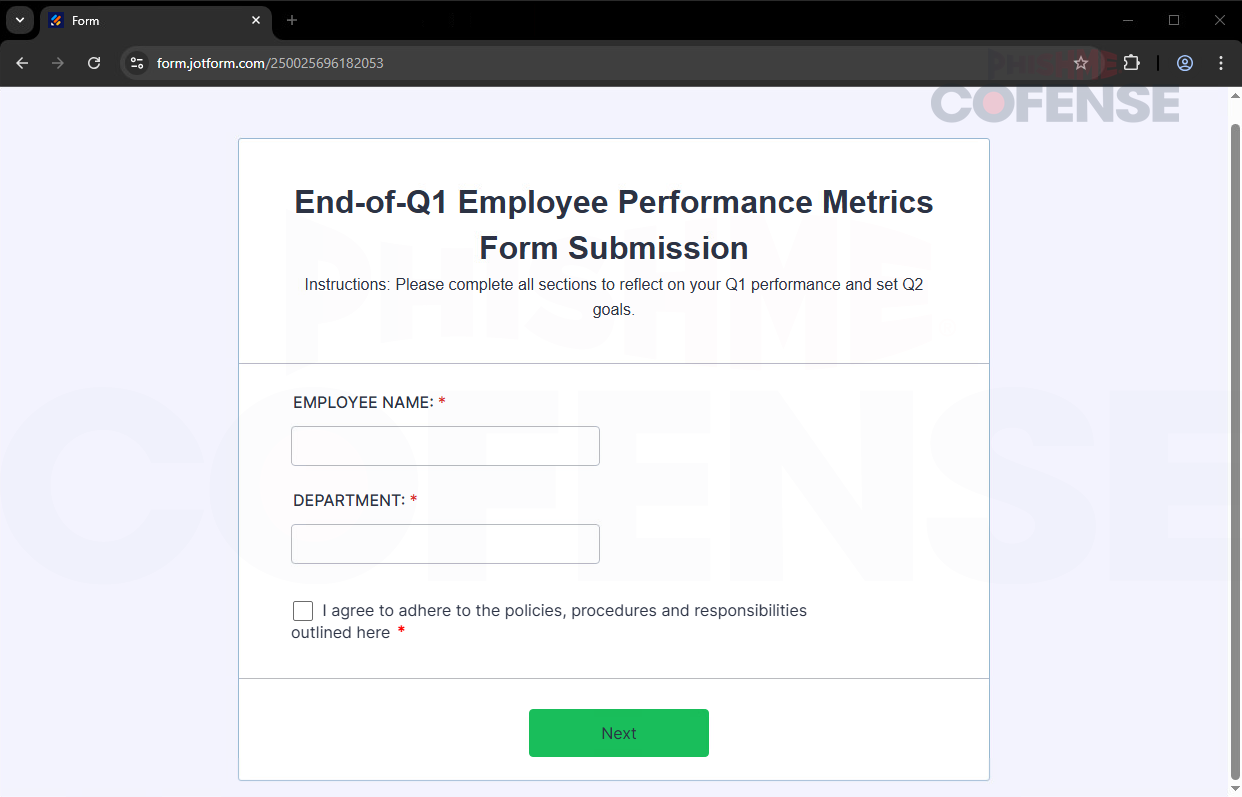
Figure 2: Initial Phishing Page
The malicious hyperlink, in the email, directs to a JotForm survey that requests sensitive information, which proves highly effective for several reasons, as illustrated in Figure 2 above. The malicious URL takes you to a pre-access authentication process to verify the employee name and department. Employees are familiar with having some sort of verification process prior to accessing sensitive documents. This allows the threat actor to gather more information about the user through social engineering, enabling them to craft tailored phishing emails in the future that reference the stolen specific details.
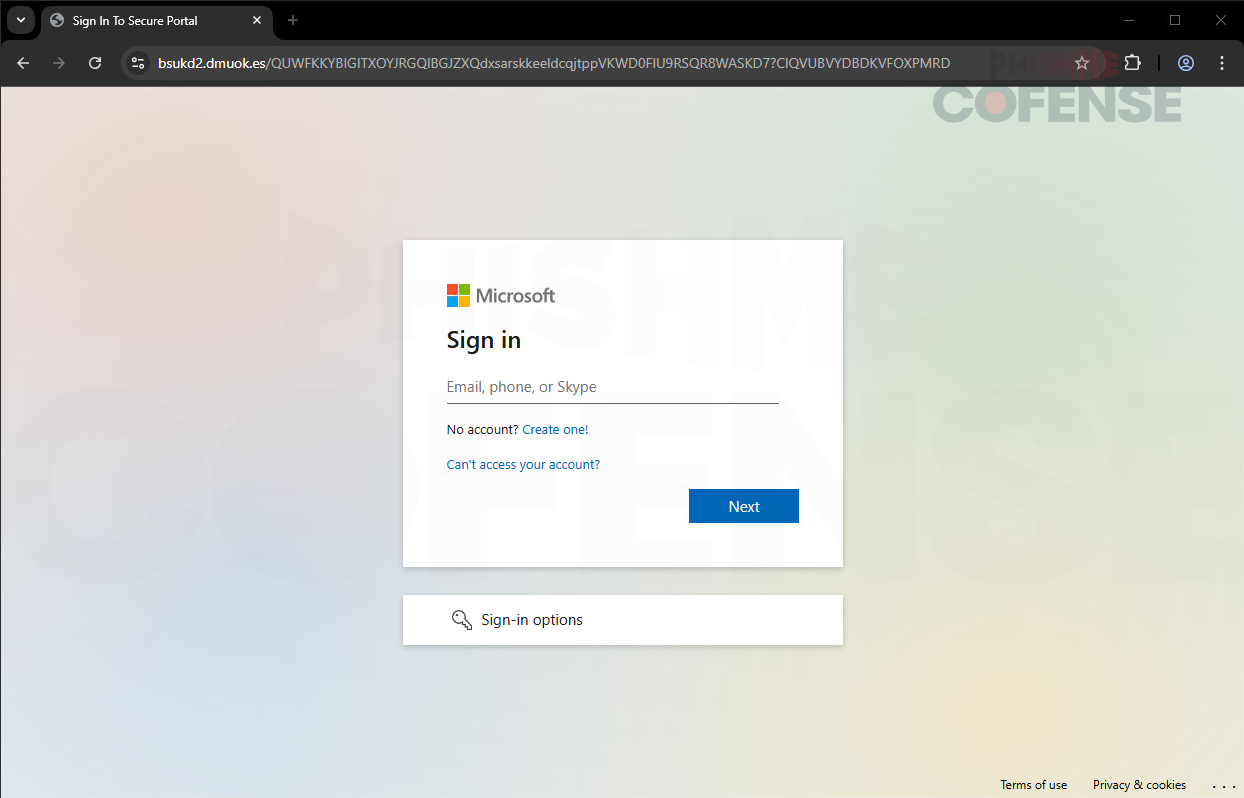
After submitting the information, the user is then redirected to a spoofed Microsoft login page that mimics the official page perfectly, as shown in Figure 3 below. If the user rushes to enter their company’s Microsoft credentials to submit their Q1 accomplishment and Q2 goals, the user unknowingly hands them over to the attackers. Compromises like these can result in account takeovers, internal data breaches, malware deployment, ransomware attacks, and reputation damage, ultimately leading to a loss of business.
.png)
Figure 3: Microsoft Phishing Page
To reduce the risk of compromise, companies can utilize email filtering systems, multi-factor authentication, continuous security awareness training, and realistic phishing simulations. These themed simulations can help employees identify red flags in emails to question, verify, and report. The Cofense Managed Phishing Detection and Response (MPDR) solution can help identify threats in real-time and bolster your company's defenses against evolving threats. This allows your organization to be more confident in its overall security posture, as one seemingly harmless email could lead to severe consequences when left unchecked.
Schedule a demo with our team of experts today to learn more.
| Stage 1 - Observed Email Infection URL:= | Infection URL IP(s): |
|---|---|
| hXXps://fmuas[.]r[.]ag[.]d[.]sendibm3[.]com/mk/cl/f/sh/SMK1E8tHeFuBm02jG51eTIgSrtto/ANtGc_Nfbczm | 1[.]179[.]112[.]195 1[.]179[.]112[.]196 1[.]179[.]112[.]197 |
| Stage 2 - Observed Payload URL(s): | Payload IP(s): |
|---|---|
| hXXps://ekamtahjzr8yjo05vmqiiwkvw20vqi7aixd1dzf04trrc0nki1gohjj06p[.]freyaxw[.]es/jhatlzqxtfgnuip ipjodaxzibkPQgAYJWXOFSMRWYAOLPZYHSMWZOBHNKDIPOTpqZAPLgrvIe12DfuEYMXwx33 hXXps://form[.]jotform[.]com/250025696182053 hXXps://bsukd2[.]dmuok[.]es/n9IzCybq | 151[.]101[.]130[.]133 151[.]101[.]66[.]133 13[.]77[.]50[.]115 151[.]101[.]2[.]133 151[.]101[.]194[.]133 |
All third-party trademarks referenced by Cofense whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding the circumvention of end-point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog, are registered trademarks or trademarks of Cofense Inc.