By: Kaleb Kirk and Kat George, Cofense Phishing Defense Center
QakBot is a form of malware commonly reported into the Cofense Phishing Defense Center (PDC). With that in mind, it is no surprise that analysts in the PDC are witness to myriad tactics implemented by attackers to manipulate or influence recipients into running the malware.
Recently, we observed emails delivering QakBot that use a familiar tactic, which is the use of old emails or email chains involving the target in an attempt to disguise the threat and, possibly, to lower recipient suspicions. A strange move for a malware type that’s so widely circulated given the additional effort involved.
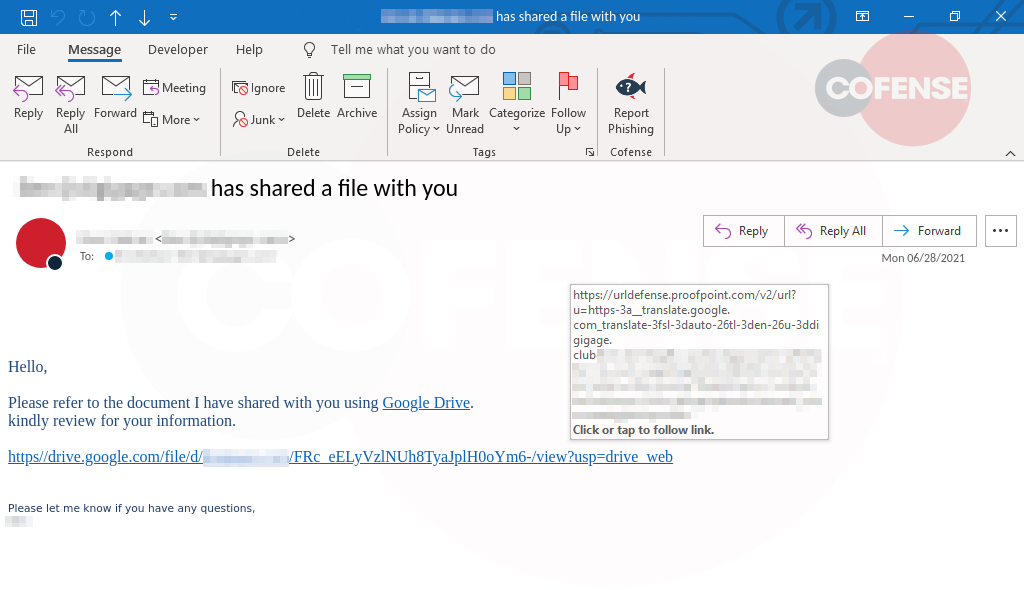
Figure 1: Email Body
Looking at the email in Figure 1, it does not really have any intricate design details to it. It can be assumed that the threat actor is using the revived email chain as the main source of influence against the target. The start of another email can be seen at the bottom of Figure 1, but it’s been cropped. One other thing to point out is that the threat actor does not bother to spoof the email of the person who was conversing with the target. They instead only choose to use their name. Once the recipient clicks the malicious URL, a ZIP with the same name as the last part of the URL’s pathing is downloaded. Within this ZIP file is only an XLS file.
Figure 2: XLS File
When it comes to appearance, the XLS file in Figure 2 is typical for malware utilizing macros and an XLS file. For starters, it has the classic labeling at the top calling this file a “protected” document. It also includes instructions for the recipient on how to click “Enable Editing” or “Enable Content.” Once enabled, a trusted service will be initiated by the infection, and it will reach out to three different payload URLs. These payloads will then download DLLs which will attempt to connect to C2s and, in turn, finish the connection chain for QakBot. One thing to notice is that, in some instances, the payload URLs that are reached out to after the content is enabled will potentially change after a certain amount of time. This can even occur if the initial URL in the email is the same. Despite this, it will only try to reach three different URLs.
Exploring different delivery tactics with emails is something that threat actors naturally must do to have any recurring success. While they perpetually devise new ways to trick recipients into interacting with emails where the environment is protected by a secure email gateway (SEG), the Cofense PDC constantly watches for such emails when they inevitably land in inboxes. The PDC is perfectly positioned to catch and analyze emails that wind up in such environments, and that are reported by well-conditioned users. Contact us to learn how to address the phish that SEGs miss.
| Indicators of Compromise | IP |
| hXXps://asc[.]meticulux[.]net/iatuvtleme/civlaaisesqtpemsai-pfalntlesuumtoitia- | 208.75.149.34 |
| hXXps://radolabs[.]in/AS8IJaDWA/nh.png | 103.53.42.97 |
| hXXps://masterdomoficial[.]com[.]br/8cntzcgI3T/nh.png | 108.179.252.230 |
| hXXps://geeksrn[.]com[.]br/nDRc2IJgN/nh.png | 69.49.241.29 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.