By Dylan Duncan
Phishing Attacks Exploit Russia’s Invasion of Ukraine, Multinational Organizations Targeted
As the conflict in Ukraine unfolds, Cofense Intelligence continues to monitor for phishing threats related to the conflict and has identified malicious campaigns that are using this current event as a lure to target end users. These campaigns are almost certainly opportunistic, as threat actors are weaponizing the conflict for financial gain by creating well-crafted credential phishing campaigns and donation scams. Threat actors using current events as themes within their email campaigns is quite common, and users should be universally vigilant against these threats. A variety of emails using this conflict as a lure have been reported to the Cofense Phishing Defense Center (PDC) directly from enterprise users’ inboxes. We have no evidence to suggest – based on IOCs, tactics, or campaign sophistication - that any of these campaigns were conducted by nation states directly involved in the war in Ukraine.
The overall volume of the phishing emails we have observed using the Russia/Ukraine conflict as a theme is low. However, some credential phishing and scam emails have made it into the inboxes of large multinational organizations in two separate industries. Each of the campaigns uncovered is focused on receiving cryptocurrency as a payout by directing the focus of the campaign toward cryptocurrency marketplace login credentials, or by requesting payment to a crypto wallet. In addition, some advance fee fraud emails have referenced the conflict as a social engineering effort. We know these have been sent by threat actors but have not seen them reported by enterprise end users.
Example 1: Sanctions-Themed-Emails Targeting Cryptocurrency Marketplace Credentials
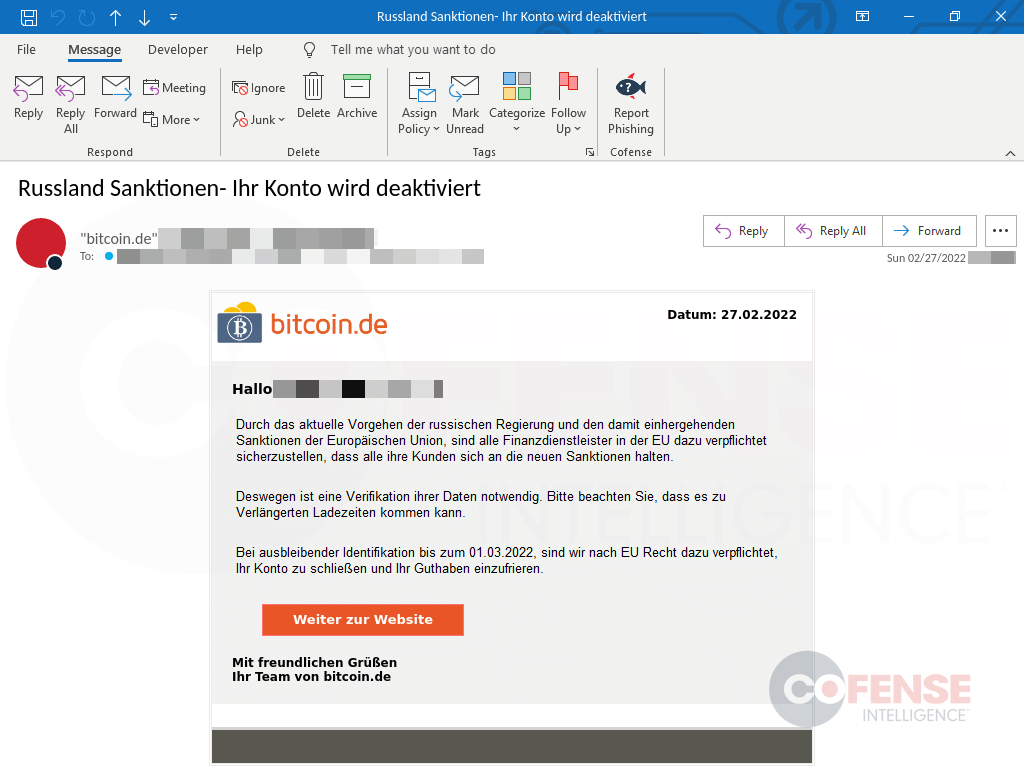
This phishing email used the subject of sanctions against Russia in targeting employees at a European financial service provider, as seen in Figures 1 and 2. The campaign spoofs the login page of popular German Bitcoin marketplace bitcoin.de, targeting login credentials with the likely intention of stealing cryptocurrency. Multiple variants of the email were discovered, but all used the sanctions against Russia to add social engineering pressure within the phishing campaign. The email was originally in German but has been translated to English for this report.
Example 2: Humanitarian-Aid-Themed Scam Seeks Cryptocurrency
The image in Figure 3 shows an example of an email scam spoofing the Ukraine Red Cross Society, aiming to scam donors into cryptocurrency donations to a private wallet. The scam claims that funds will be used for logistical and medical support of Ukraine armed forces and civilians. This scam is not particularly sophisticated in its construction and is more likely to impact individuals than organizations. However, as noted above, it has reached inboxes at a multinational company.
Example 3: Advance Fee Fraud
Threat actors often use world events as themes within advance-fee fraud operations, as part of unsophisticated social engineering efforts intended to convince victims of their sincerity. A number of recent emails using the Russia/Ukraine conflict as a theme have this objective. The image in Figure 4 shows the text of one such social engineering effort. We have not observed any of these emails actually reaching corporate inboxes, but they demonstrate how this conflict may be used by threat actors at any sophistication level.
Indicators of Compromise
Table 1: Related phishing URLs for the Russia and Ukraine-Conflict-Themed Crypto credential phishing campaign.
| Indicators of Compromise | Description |
| hxxp://gefanet[.]com/?2DsZFmK7MA | Phishing URL embedded in email |
| hxxp://pro-trux[.]com/?bEtW8e5IBm | Phishing URL embedded in email |
| hxxps://bit[.]ly/3piqMWI | Phishing URL embedded in email |
| hxxp://bobaylsworth[.]com/?0TtBfkonYL | Phishing URL embedded in email |
| hxxp://latahina[.]com/?MuXhL1T4U3 | Phishing URL embedded in email |
| hxxps://bitcoin[.]de-schutz-kundenkonto[.]com/btc/ | Spoofed Bitcoin[.]de login page |
| hxxps://bitcoin-kundenupdate[.]com/btc/ | Spoofed Bitcoin[.]de login page |
| hxxps://strato[.]de-kundenkontrolle-verifkation[.]com/panel/live[.]php | PHP panel to harvest login credentials |
| hxxps://strato[.]de-kundenkontrolle-verifkation[.]com/panel/auth[.]php | PHP panel to harvest login credentials |
Table 2: Crypto Wallet from the Ukraine Red Cross Society-spoofing scam email.
| Crypto Wallet |
| bc1qa8gafgj8807pergjctdlsxa2rd0hxpk0qupqge |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.