By Kian Buckley-Maher, Cofense Phishing Defense Center
A phish recently noted by the Phishing Defence Center (PDC) utilizes the online form builder Wufoo, a tool commonly associated with easily created surveys and online registration forms. Threat actors have used Wufoo to create simplistic but effective credential-stealing vectors.
Phishing Email
The email in Figure 1 uses basic language informing the user that they need to save a copy and submit any further time requests, which enables the threat actor to gain credentials after any future mandatory password resets, a common feature seen in many organizations.
To instill a sense of urgency it states all requests for the subsequent two months need to be submitted through this method, so any users planning anything in the next few months will be compelled to download and input all the required information. As we head into the holiday season, these become even more timely. In addition, the user is requested to keep a copy of the form for any future time-off requests, as the requests are to be submitted during a two-month period. This also aligns with the typical 90-day password reset policies enabled in many organizations and as such the threat actors will ensure access to accounts even if the password reset has occurred.
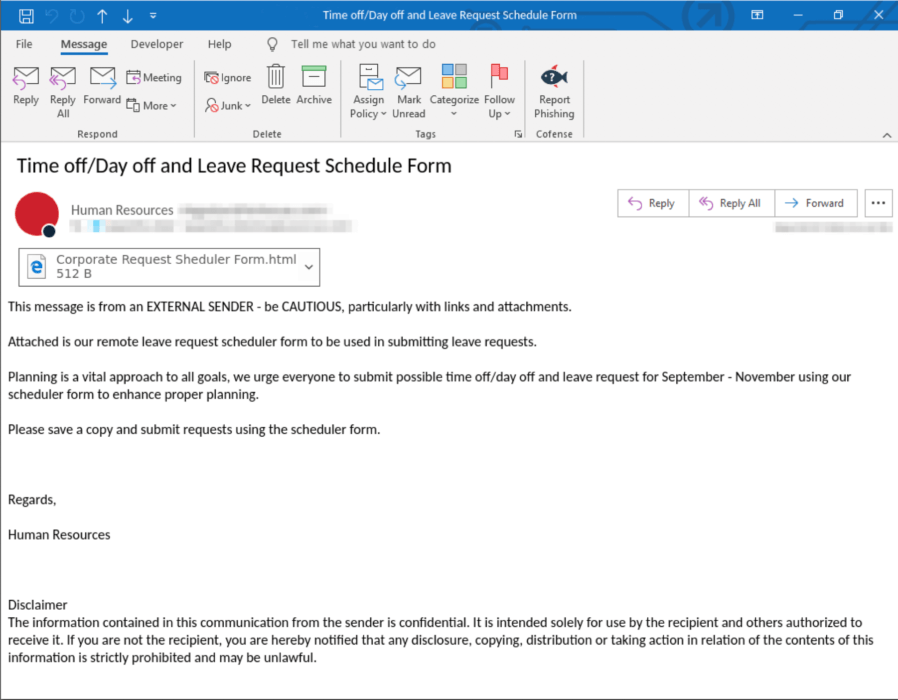 Figure 1: Email Image
Figure 1: Email Image
Looking at the header, we see the sender is utilizing a generic alias to impersonate Human Resources, a typical naming convention used by organizations for company-wide communications such as this one.
Phishing Page
As seen in Figure 2, the form itself contains very few identifiable markings such as branding or company logos; in most cases, threat actors use it in order to increase the potential of interaction from the recipient. The simplicity of this time request forms allows this phish to be used to reach further than most with little modification needed between phishing campaigns as it would be required for a more stylized and complex corporate communication.
After entering the required fields, the user is required to enter their email address in order to submit the form. Most organizations today utilize their self-service Payroll or HR portal to collect this information. This was most likely an indicator to the recipient that the email was suspicious and reported it via the Reporter button in Outlook.
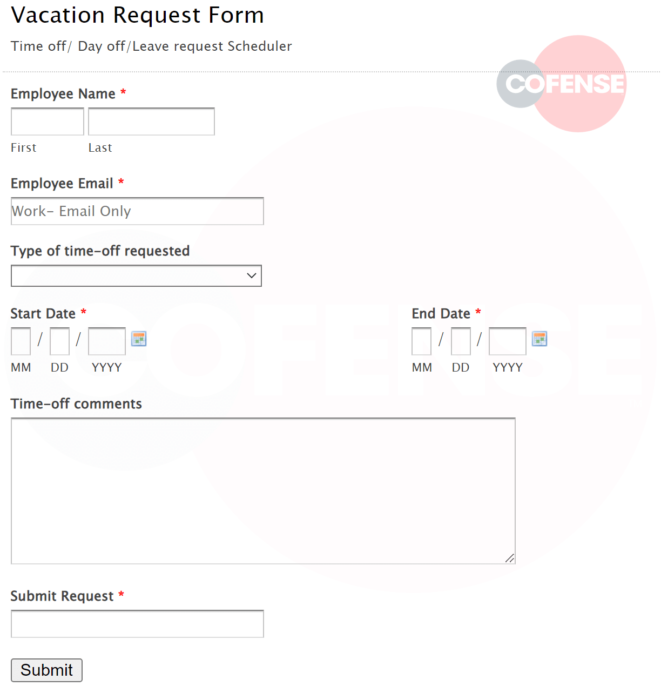 Figure 2: Main Phishing Page
Figure 2: Main Phishing Page
Once the user has provided all the required information, they will be presented with a page to input their account password to send the request, and the user's account credentials will be compromised.
Conclusion
The PDC continues to observe these kinds of phishing emails over the summer months, and as we look toward the end of the year and the upcoming holiday season, we expect these campaigns to increase once again.
Due to the nature of these campaigns and their relative simplicity, it can be expected that these will be successful in organizations without proper phishing training and adequate phishing defenses.
| Indicators of Compromise | IP |
| hXXps://xhrreview[.]wufoo[.]com/forms/m1cgigu51jrr9hf/ |