Found in Environments Protected By: Symantec
By Adam Martin, Cofense Phishing Defense Center
As self-testing via antigen and professional testing via PCR have become more common across many sectors of society, so has status-based phishing. Just as COVID-19 guidelines have evolved, so have threat actor phishing tactics. This recent Office365 credential harvesting campaign utilizes the topic of potential repercussions if the status form isn’t completed. A classic tactic of creating panic in the end user, this ploy threatens financial or other penalties if a certain urgent task isn’t completed.
The phishing email for this campaign plays on fear and conveys urgency. It uses a relevant topic -- COVID-19 – demanding completion of a form to disclose information, and it includes the threat of some form of reprisal for noncompliance. The email is tailored to the target organization, complete with branding. However, illustrated in Figure 1, the “Covid Form” button will direct the user outside of any authentic corporate environment. The initial “svc[.]dynamics[…]” link will redirect the user to an external domain once the button is pressed.
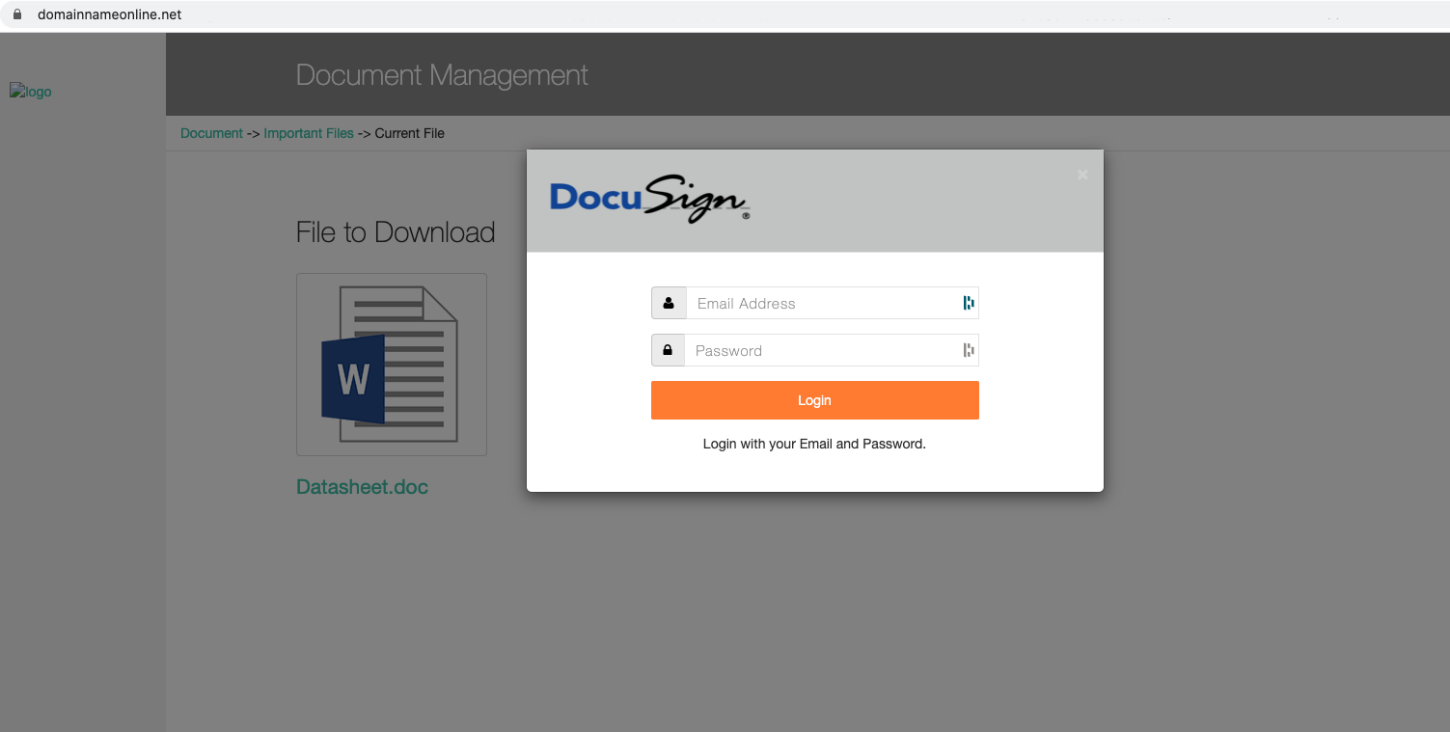
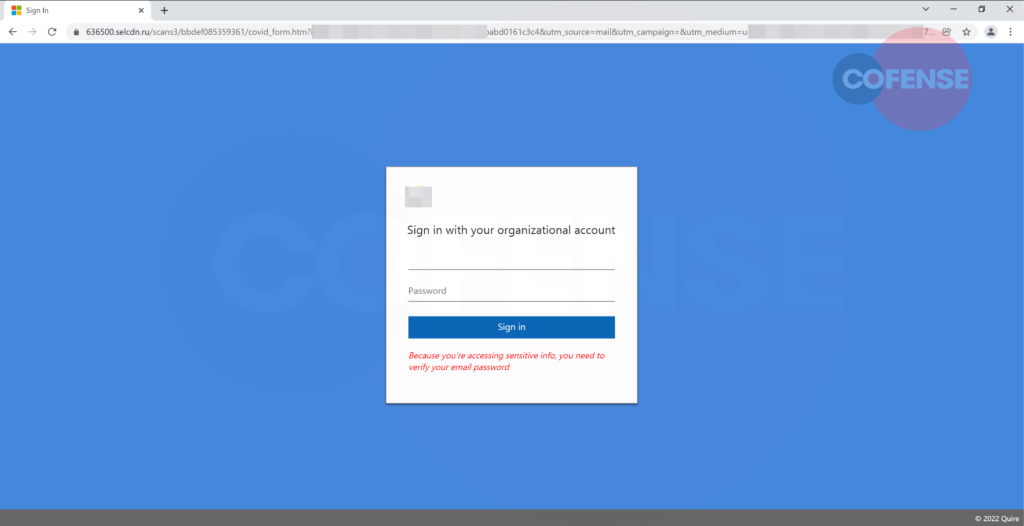
Figure 2: Phishing Page
The unsuspecting user, having clicked on the link, will be directed to the phishing page seen in Figure 2. As can be seen from the URL, this page is not a legitimate Microsoft website and the domain is being hosted from a Russian TLD (.ru). The information box is spoofed with target company branding along with the affiliation to Microsoft, shown in the tab logo. The most glaring giveaway is the URL base address, in tandem with the randomized look of the rest of the URL path.
The user is given the prompt to enter their password as “sensitive information” is being accessed. Once the password is entered, this information is exfiltrated to an external server. Another indicator of the illegitimacy of this service is the fact that there isn’t any typical email login option. We noted the absence of “have you forgotten your password,” “Contact” and any semblance of a help menu as would typically be seen with legitimate services. Regardless of the password entered, the page will return an error for incorrect password and run this error in a loop.
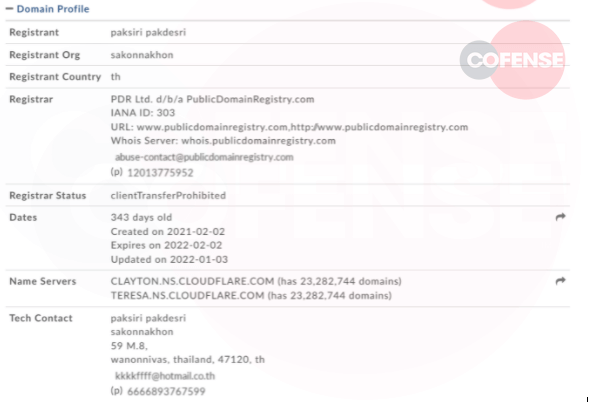
Figure 3: Whois Records
The sender address “Info@vtech-vt[.]net” found in Figure 1 and references in Figure 3 is relatively new. What also draws attention is the technical contact page. The contact address looks to be randomized, and the phone number is unusable.
As the world adapts to COVID, with different measures of detection and status declaration, so too adapts the world of credential phishing. As with most of the traffic seen here at the PDC, automated detection systems still underperform when compared to human analysis. With testing becoming more the norm, it is likely that phishing lures will exploit this trend. The driving factor behind the success of such a lure is the fact that a large number of employees are accessing or uploading these results for travel or other purposes. It’s not beyond the realm of possibility that a recipient would be panicked into revealing credentials if threatened with loss of access to work resources. Cofense continues to monitor these and disposition these threats. We can help your company, too.
| Indicators of Compromise | IP |
| hXXps://015e86e84bce4534a8a6f8e57cc4bd23[.]svc[.]dynamics[.]com/t/r/7HK qRHWPuvayNfeu9O0COW3Y3T6s9OwbRCRs3Zuq1N4 | 104[.]40[.]78[.]147 |
| hXXps://636500[.]selcdn[.]ru/scans3/bbdef085359361/covid_form.htm? ioxwrxnaerll&auth=&7589cf-3ac6-4e1c-9e2a- babd0161c3c4&utm_source=mail&utm_campaign=&utm_medium=u=589a04 49d04476c8af0f92bc7&id=ca92440317&e=c5cec25e50BgVtWAzsQmMcaL3z BjzlZ2TJR& | 92[.]53[.]68[.]201 92[.]53[.]68[.]203 92[.]53[.]68[.]202 92[.]53[.]68[.]205 92[.]53[.]68[.]204 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.