By: Madalynn Carr, Intelligence Team
Threat actors are constantly evolving and adapting by discovering new, unique ways to bypass email-based security controls. One key method they exploit is the abuse of URL shortening services (also known as URL shorteners or link shorteners).
These legitimate online tools allow users and businesses to make short aliases of longer URLs for a variety of reasons including aesthetics, easier sharing, gathering analytics, or improving perceived legitimacy.
Threat actors take advantage of the tools offered by link shortening services to deliver malware and credential phishing. Cofense Intelligence has identified the most commonly abused legitimate URL shortening services, as shown in Table 1.
Top URL Shortening Services | ||
T[.]ly | TinyURL[.]com | Rebrand[.]ly |
Is[.]gd | Goo[.]su | Qrco[.]de |
Table 1: Most common shortened URLs seen by Cofense Intelligence between July 2024 and June 2025.
This report will cover between July 2024 and June 2025 and will analyze both credential phishing and malware campaigns using these shortened URL services.
Key Points
- 28% of all campaigns using one of the commonly seen link shortening services delivered malware such as Pure Logs Stealer.
- Many shortened URL services are free or offer a free trial, allowing threat actors to easily create new accounts for new campaigns.
- Many shortened URL services offer free basic analytics when the user clicks on the link, allowing the threat actor to gain valuable information about the targets of their phishing attacks.
Overview
Shortened URL services can be utilized by threat actors for multiple reasons; however, the two main reasons are likely the analytics and click data they offer and the perceived legitimacy of these services. Nearly every shortened URL service mentioned in this report offers some sort of information regarding the recipient, whether it be just the number of times the URL was accessed, browser type, language, or date.
This is beneficial for threat actors because if the user opens the link, threat actors can gather important information to send further spear phishing campaigns specifically targeted at the user. This also lets the threat actor know that not only is the recipient’s email account actively being used, but also the recipient is susceptible to phishing campaigns.
Between July 2024 and June 2025, Cofense Intelligence witnessed many different URL shortening services used in phishing attempts. The top six shortened URL services Cofense Intelligence has witnessed can be seen in Figure 1.
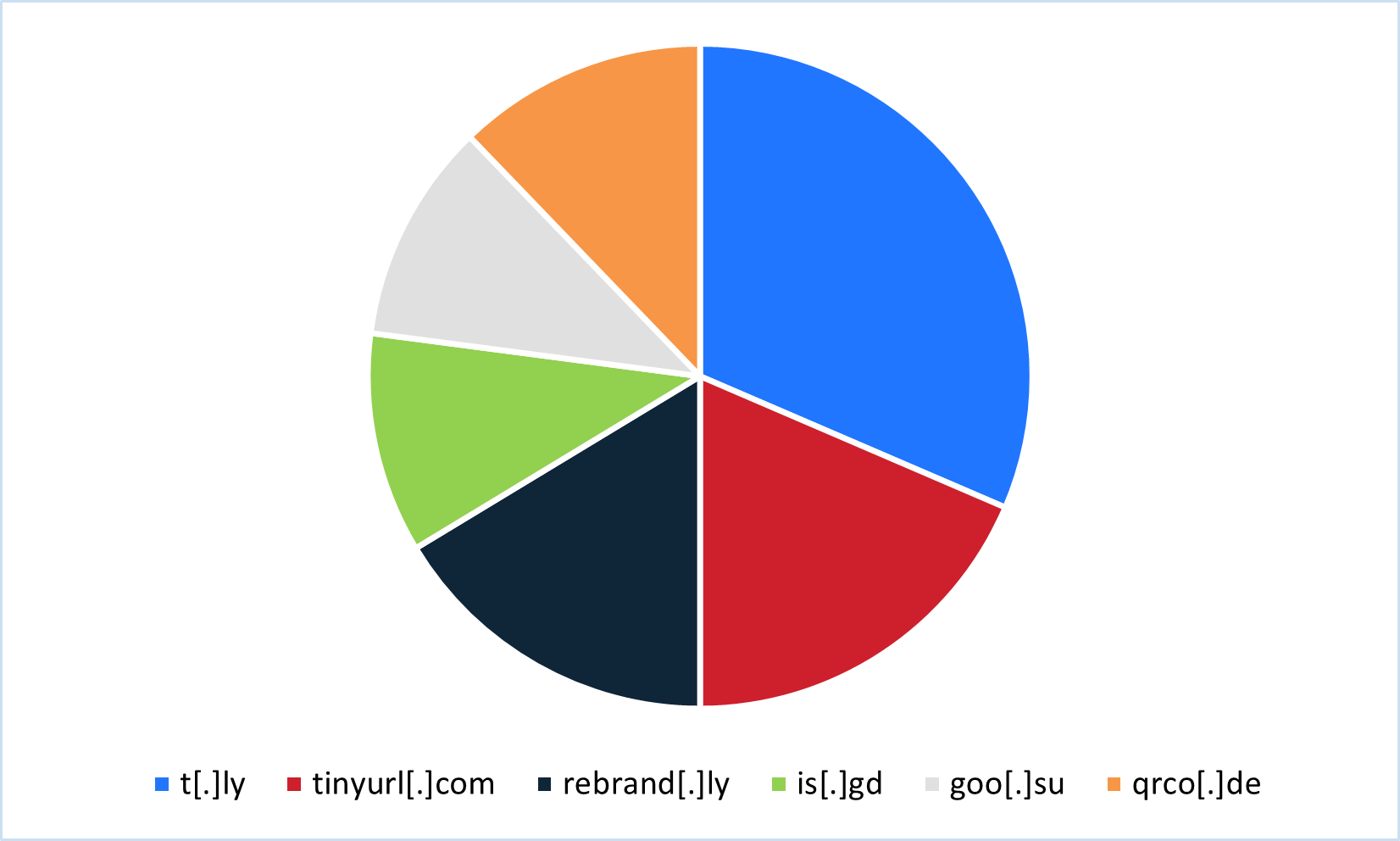
Figure 1: Top shortened URL services seen by Cofense Intelligence in use delivering malware or credential phishing between July 2024 and June 2025.
T[.]ly
T[.]ly is a free shortened URL service; it was the most popular shortened URL witnessed by Cofense Intelligence within the time period. A free version is available for threat actors; however, benefits are limited. Like many other link shortening services, t[.]ly provides an API, allowing threat actors to automatically create shortened links at scale. However, the API requires an account.
All the paid plans include a five-day free trial, allowing threat actors to abuse the trial system. A few notable perks include:
- Trackable QR codes
- Smart URLs (traffic routing)
Tracking QR codes is highly sought after due to the rise of QR codes in phishing campaigns. QR codes are often more difficult for automated analysis to track and harder for users to check the legitimacy of the destination URL before scanning the link. Smart URLs allow threat actors to redirect victims to different redirect URLs based on the browser user agent and geolocation.
T[.]ly has been most seen with credential phishing, as just under 15% of all campaigns containing this URL delivered malware. The malware primarily delivered via this shortened URL service are Information Stealers and a variety of Remote Access Trojans (RATs).
RATs are a malware type that contain multiple capabilities, with the primary distinction of providing threat actors with remote control of the infected device.
ConnectWise ScreenConnect, tracked by Cofense as ConnectWise RAT, has been seen using this URL in several campaigns spoofing the Social Security Administration.
Tinyurl[.]com
Tinyurl[.]com is another shortened URL service, which offers a free, no-account service. Like many other link shortening services, tinyurl[.]com offers an API, allowing threat actors to automatically create shortened links at scale, however, it does require an account.
The most notable capabilities useful to threat actors are:
- Setting expiration time on links
- Analytics for device language, location, browser, and time of click
The highlighted benefits are likely the most useful for threat actors. Expiration time on links can be useful, as this allows their campaigns to be inaccessible at a certain point, making it more difficult for analysis.
Analytics such as device language can also be useful for threat actors because it gives information about the user that they are targeting and allows the threat actor to know that not only are they susceptible to phishing emails, but the email itself is active.
If a threat actor is targeting a specific group or person in the company, a tactic widely known as spear phishing, this can give them more information about what to specify, such as geographic location, browser, and more.
Although Tinyurl[.]com is also primarily used for credential phishing, with only 17% of all campaigns containing this URL delivering malware, the choice of malware does not have an exact pattern.
Mispadu is the most popular malware family; however, other malware families, such as Remcos RAT and Lumma Stealer, have been seen being delivered via these shortened URLs.
Rebrand[.]ly
Rebrand[.]ly is another popular shortened URL service used by threat actors, likely due to the popularity of rebrand[.]ly within legitimate contexts. Rebrand[.]ly has been popular since 2015 and continues to be a common choice for individuals and organizations. This shortening URL service requires an account, even if the user is using the free version of the service.
However, the paid premium plans, which are offered, all have free trials, which are likely being used by threat actors. Like many other link shortening services, rebrand[.]ly offers an API, allowing threat actors to automatically create shortened links at scale. However, it does require an account.
The most notable capabilities useful to threat actors are:
- Setting link expiration
- Customizable QR codes
- Analytics for device language, location, browser, and time of click
- Traffic routing
- Password protection
Link expiration is often used by threat actors to prevent the original link from being blocked, as the longer the malicious website stays active, the more likely analysts are to flag it. Traffic routing is particularly important as this gives threat actors the ability to prevent analysis by redirecting to a legitimate site if analysis tools are detected or to send victims to phishing pages optimized for their device.
It can also be used to deliver malware tailored to the victim’s device. QR codes are also extremely useful for threat actors, as this gives threat actors more customization in the campaign, and QR codes are typically more difficult for many automated analysis tools.
Advanced analytics are beneficial, as this allows the threat actor to know that not only is the user susceptible to phishing, but also gives them information without typing in any credentials.
Password protection also aids threat actors in bypassing analysis because if the analyst does not know the password to the website, then no analysis can be done.
Compared to the other shortened URL services, rebrand[.]ly is used the most for credential phishing, with only 10% of all campaigns containing this URL delivering malware. The most common malware family delivered is Byakugan, an Information Stealer. However, there have been campaigns delivering ConnectWise RAT and Cobalt Strike.
Is[.]gd
Is[.]gd is a very simplistic free shortened URL service with no paid premium plans. Like many other link shortening services, rebrand[.]ly offers an API, allowing threat actors to automatically create shortened links at scale. Unlike other services, an account is not needed to use the API, enabling threat actors to quickly create shortened links at scale for free. It also offers free but limited capabilities in comparison to other services:
- Analytics for location, browser, operating system, and time of click
Analytics are extremely useful for threat actors, as they provide information regarding their targets without requiring the user to actually insert information.
An interesting aspect of this shortened URL is that, compared to the previous shortened URLs, this one is primarily used to deliver malware, compared to credential phishing, with 49% of all campaigns containing this URL delivering malware. Alongside this, nearly every campaign delivered Pure Logs Stealer, and recently Lone None Stealer, both Information Stealers.
This is often partnered with other shortened URLs later mentioned in this report, which makes it more likely to bypass automated analysis by SEGs.
Goo[.]su
Goo[.]su is a shortened URL service, which offers to shorten URLs without creating an account. Like many other link shortening services, goo[.]su offers an API, allowing threat actors to automatically create shortened links at scale. However, it does require an account.
A few capabilities to highlight include:
- QR code generation
- Password protection
- Analytics for location, browser, and time of click
The capabilities that this shortened URL service offers are extremely useful for threat actors. QR codes have been a consistent aspect of the threat landscape, and creating QR codes and deploying them into a phishing campaign can be useful for anti-analysis. As mentioned previously, QR codes have been a popular choice for threat actors, and pairing QR codes with a shortened URL helps threat actors to evade analysis.
Password protection on websites is also useful for anti-analysis. If an analyst does not have the original email containing the password, then the analyst cannot access the website, allowing the phishing campaign to continue. Advanced analytics are useful for threat actors, as they provide valuable information about the victim as long as the victim clicks the link.
This shortened URL service is seen delivering malware more than any other service, with 89% of all campaigns containing this URL delivering malware. It primarily delivers Pure Logs Stealer and Lone None Stealer, often together. This service is often paired with the previously mentioned is[.]gd link, with the initial often redirecting to goo[.]su, then redirecting to the download link.
Qrco[.]de
Qrco[.]de is unlike the other shortened URL services mentioned in this report, as this service was intended to be primarily used for QR codes rather than just shortened URLs. QR codes have been a constantly rising tactic in the threat landscape, and as mentioned previously in this report, are a common addition to many shortened URL services.
However, despite this, only 20% of all qrco[.]de campaigns contained a QR code, revealing that threat actors have been using this service primarily as a shortened URL service rather than a QR code. Qrco[.]de does require an account, and has a 14-day free trial, allowing threat actors to access analytics and create new accounts to create new campaigns. Like many other link shortening services, qrco[.]de offers an API, allowing threat actors to automatically create shortened links at scale. However, it does require an account.
The most important capabilities to highlight are:
- Analytics for location, browser, and time of click
- Bulk creation of QR codes
Advanced analytics are extremely important for threat actors since threat actors can gather information regarding the victim without the victim inputting any information on the malicious website. Creating QR codes, specifically in bulk, is useful for threat actors. Despite this fact, however, only a small percentage of campaigns actually had a QR code embedded in the email.
Qrco[.]de was primarily seen delivering credential phishing compared to malware, with nearly 96% of all campaigns delivering credential phishing. The only two malware families seen being delivered with this shortened URL service were ConnectWise RAT and jRAT.
Conclusion
Shortened URLs have been consistently used maliciously for years and are likely to continue to be used by threat actors. Although these services do attempt to suspend and deactivate malicious links, most of the time, a user has to submit the link, claiming it is used for malicious activity. This allows threat actors to abuse these services, abuse the free trials, gather analytics, and redirect to credential phishing pages for a significant amount of time before their links are taken down. Despite these issues, there are still ways to remediate this ongoing tactic.
Remediation
Handling shortened URLs can be tricky initially, as many shortened URLs are used legitimately by individuals and organizations. However, the most effective way of handling these URLs is often through employee training. Learning how to spot a malicious email is extremely important in the modern age and will aid in not clicking on any malicious URLs, including shortened ones.
Alongside this, as many of these shortened URL services offer QR code generators, it is important for employees not to scan QR codes from malicious emails. If a company uses only a selection of shortened URLs, another solution is to block less popular shortened URLs from getting into inboxes.
Regarding analysis, automated analysis could be set up to analyze multiple hops rather than just checking the first link’s location. One could also have systems set to show the final URL destination when a user hovers over the shortened URL. Some URL shortening services allow a user to add a special character at the end of the link to see where the link redirects without visiting the destination.
For example, t[.]ly has the ability where adding a “+” at the end gives any user access to analytics such as who has clicked on the link and where the link redirects. Is[.]gd has a similar service with a “-“ appended to a link. Tinyurl[.]com also has a toggle option available on their website that uses browser cookies to display expanded link previews.
Some URL shortening services have a specific page for looking at the expanded link. If this is unavailable, there are third party sources to look at the expanded link found on the internet.